How to basic reverse
How to basic reverse
Basic Reverse Engineering using GDB
Reverse Engineering and Malware Analysis are now becoming fields of growing research. Here’s a jump start for all of you interested in Reverse Engineering.
I’ll be using the GNU Debugger (GDB) for this tutorial. There are other tools out there (which might make the task easier) like IDA, radare2 etc that can be used too!
In this tutorial, we will be reversing a C Program that uses the strcmp function to validate user input.
Here’s the snapshot of the code:
Let’s now fire up GDB using: gdb stringcmp
Before starting, we need to change the disassembly style to Intel (for a better readability);
set disassembly-flavor intel
Next, we shall see all the functions used in this binary;
Among all the functions, only main is what we have to concentrate at!
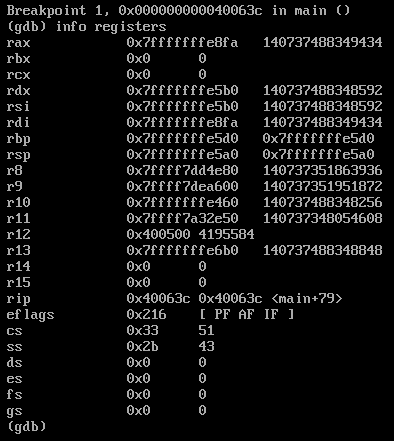
The assembly code for the main function will be dumped. We can see the strcmp function call at address 0x40063c (might be different in your case).
To examine the state of the program at that address, we need to set a breakpoint at the strcmp function call: b *0x40063c
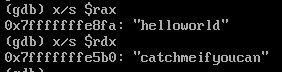
From the assembly, it can be noted that the user input (from the command line arguments is stored in the rax register). And the strcmp function compares the rax register with the rdx register, which must mean that the rdx register must contain the required string. On examining both the registers ( rax, rdx ). We get the required input!
On deleting the breakpoints and running the program via GDB, we see the Correct! response!
How to Shoot a Reverse Layup in Basketball
This article was co-authored by Ryan Tremblay. Ryan Tremblay is a Basketball Coach and the Owner of National Sports ID and STACK Basketball. With over 30 years of experience, Ryan specializes in basketball coaching, social media marketing, and website design. Ryan created the National Sports ID as a platform to verify the age/grade of youth athletes and STACK Basketball to inspire young athletes to grow into mature individuals and basketball players. Ryan was a First Team All-Decade basketball player in Bergen County and finished in the top 20 all-time leading scorers in the county’s history with 1,730 points. He went on to Caldwell University on a basketball scholarship where he was part of three championship teams. Ryan was a two-time All-Metropolitan, All-State, and All-Conference point guard and the all-time three-point leader in the school’s history, landing him in the Caldwell University Athletic Hall of Fame.
There are 7 references cited in this article, which can be found at the bottom of the page.
This article has been viewed 61,355 times.
The reverse layup and its variations, like the finger roll or teardrop, have been made famous by NBA all-stars like Michael Jordan, Scottie Pippin, and Stephen Curry. [1] X Research source To make this shot, you’ll need to drive across the court and shoot the ball underhand into the basket. [2] X Research source Though this may sound simple, the mechanics behind performing this move smoothly can take time and practice. After you learn how to do the reverse layup, there are ways you might improve your technique and variations you can use to make your reverse layup more versatile.
0x00 Preface
I don’t know why, please see
Android reverse-Android basic reverse (2)
Android reverse-Android basic reverse(5)
And the java series:
Content or question
1. How to write a login interface? √
2. Reverse analysis of login logic √
3. How to violently bypass a login interface? √
4. How to log in smartly √
5. How to add ads √
6. How to advertise
7. Case analysis
February 4, 2018 13:10:42
purpose
1. Review the writing of the login interface
2. Violent practice
3. Get practice
4. Smali code proficiency
5. Add ads to your app
6. The actual combat of secondary packaging and advertising
7. How to get advertising
0x01 Android programming-login interface
Description
This is a must to learn when learning programming, this time we will not access the database to operate. There is also no registration interface, just a simple login interface.
The demo still follows the previous changes. Well, anyway, I will, I will be lazy.
1. Change the layout
First, a box of username.

Then a login password box.

Then it’s a login button

Preview our interface

is so ugly, to make a simple adjustment, the overall code is as follows:
2. Bound controls
Well, in order to look like a login interface, I also changed the name.
So rebind.
3. Logic Writing
A knowledge point is involved here.
How to convert java String type to int type.
In short:
Can be converted
I suddenly thought of what to do if I don’t enter a number. Well, go and change the norms.
A line is added here and only numbers are allowed.
0x02 Decompilation analysis
Analysis, many times. Old rules
1. Android Killer
2. Find the main function
3. Key logical part
The key logic is how to judge the login part
We saw two if languages
The whole logic is to make one judgment first, and then another judgment. That is, the first if statement is satisfied, and then the second if statement is satisfied.
These smali codes are statements that we have analyzed many times before. There is nothing difficult, they are all simple.
0x03 Violent Aesthetics
Let’s try to crack.
method 1
Ideas
Since there is an if statement for judgment, I deleted the if statement. Programming now looks like this:
Then save for decompilation.
Installation test
Test success
Method 2
Ideas
Do not delete the if statement, but I change the logic of the if statement. For example, if it is equal, I change it to not equal and continue to run.
Specific operation
The first judgment statement is:
The meaning of if-eqz is to jump to cond_0 if it is 0
Now we modify it to:
The meaning of if-nez is, if it is not 0, jump to cond_0
The second judgment statement is:
The meaning of if-ne is if v0! =v1 just jump.
Now we change to:
The meaning of if-eq is to jump if they are equal.
The test is successful and I don’t want to record pictures anymore.
Method 3
Ideas
Since the last thing we have to go is the content of the second judgment, then we can use the goto statement to go directly in.
First set up a cond_1
then goto :cond_1
Test Results
Concluding remarks
There may be many ways to bypass, and I won’t show them all here.
0x04 elegant login
Ideas
Since it is a login, there must be a comparison. As long as I know what is used to compare, I output the things that need to be compared so that we can check if it is better.
Code analysis
It is obvious here that we compare v0 and v1, if yes, return 1 and if not, return 0
Define a v1 register, and then compare v0 and v1 to see if they are consistent. If they are consistent, continue to run down.
0x208 is in hexadecimal format. After conversion, we know what our password is, and then log in and output it. Of course, this is a visible password. If you access the database, it will become an invisible password. Then you can perform dynamic debugging to output the password.
0x05 How to place ads
What is advertising?
The great god once said that everything that has nothing to do with the game is advertising. What we generally say about advertising is something that is kind and annoying.
What is the purpose of placing ads?
The purpose of placing ads is mainly
(1) Do promotion
(2) Can make money
Analysis of the principle of embedded advertising
Use a carrier to carry the advertisement and then display it. The technology used is static layout or dynamic loading. Let’s take a look at the specific operation if the advertisement is implanted.
Advertising on the market
Youmi ads
Youmi ads, anyway, I was scammed for two full days. I didn’t succeed in doing anything, and I was tossed enough. Although I didn’t produce any results, I had a deep understanding of Youmi ads. Human things, so angry.
In the end, I just succeeded in this thing.

Why does this ghost appear, well, I don’t know.
There is too little information. Most of the blogs are official documents copied directly. The most outrageous thing is to take the official demo given by Youmi. Once the source code is posted, a blog will be finished. I don’t know what to say.
Climb the pit
Let me talk about the pit I encountered. I hope someone can save time when researching.
Seeing this ghost, there is nothing. Internet searches say that you need to change an SDK, but the official website only provides the latest SDK, maybe I didn’t find it.
Change sdk decisively.
And the official demo cannot be imported into Android Studio, which is also the problem.
Solution:
Add this sentence in Androidmanifest.xml, which may be useful.
But the most reliable way is to change the SDK.
Where can I find the sdk? I do not know either.
See if you can give it to Youmi customer service.
Anyway, I pulled it from other apks. YoumiSdk_v7.4.0_2017-05-18 this version.
At 21:45:28 on February 5, 2018, I wanted to give up, but suddenly I saw a picture.

I think I might have to work hard. Do it again.
The following is a re-enactment record.
Re-engage
1. Create a new demo
2. Add arr package
By the way, there is one more thing that youmi is an arr package or not a jar package.
to see the difference
*.jar: It only contains class files and manifest files, not resource files, such as pictures and other files in res.
*.aar: contains all resources, class and res resource files all contain
continue our operation
3. Add dependencies

In the third step, copy and paste the arr package name
I’m here to complain, the official document can really be illustrated with text. Oops
4. Application ID

apply for such a ghost.
5. Initialization information
There was a problem without mercy.

Change to arr version and continue.
Remember to change the configuration file
Sure enough, I changed an arr package and it was right. It was too unfriendly.
We then initialize.

The official document at this step is very clear, partial praise.
6. Set the channel number
Yeah, set it up
7. Permission configuration.
Advertising, it can be run only when the permission scan is configured.
One thing should be done synchronously.
should make a record synchronously on my notebook.
Add v4 package
The v4 here: xx.x.x must be consistent with the above, just look at the picture:
Write a call

such a ghost appeared, and it was this ghost. I got it at 5 o’clock in the evening and I didn’t know what happened.
I searched it myself and said that DNS resolution failed
then consulted customer service

Well, it has nothing to do with me.
Try other ad types
The same returns code 1. annoying. Submitted for review.
February 6, 2018 12:38:11
Domob Advertising
Do it yourself, I’m tired
Tencent
Concluding remarks
I wrote at least 4 demos, and now I have access to the SDK, which is really familiar to me. If you lose your horse, you know good fortune. How to use it is also very skilled.
If you want to go to the advertisement, first observe the Activity, then directly look at the official document, and then do the opposite.
0x06 How to re-implant ads
Basically a search is a method: (maybe there is some black technology that has not been announced in the world),
There is also a second package with rice.
0x07 conclusion
In view of the space, switch to Android reverse-Android basic reverse (6-2)
reward:
1. Review the writing of the login interface
2. Simple bypass summary
3. Simple analysis of smali code
4. After climbing the ad access pit for two days, I have a deep understanding of Android access sdk
Remaining problem
1. How to remove ads
2. There is also a demo button logic added before
FYI: Reverse Crunches Deserve a Spot in Your Core Routine
Jen Polzak is a certified personal trainer who has been in the fitness industry for over a decade, specializing in nutrition coaching, post-rehabilitation exercises, and weight loss.
Javier Díez / Stocksy
In This Article
As someone who isn’t exactly the «gym-going» type, I always find myself at a loss when discussing exercise moves and fitness routines. Such was the case when the term «reverse crunches» came across my computer screen. I didn’t know how they were different from regular crunches, if I should be doing them, or if they were another seemingly pointless move that would do little for my body. Of course, we’re all always trying to look our best and tone up when we can, but I like to know if an exercise has other perks as well. Does it help with back pain? Anxiety? Flexibility?
We spoke to a fitness expert to get the lowdown. Turns out, reverse crunches are powerful and boast enough benefits that they’ve become mainstays in my rather limited exercise routine.
Read on for everything you need to know about reverse crunches and why you should consider adding them to your workout routine.
Meet the Expert
Tatiana Boncompagni is a NASM-certified personal trainer and the founder of Eat Sunny.
What Is a Reverse Crunch?
» data-caption=»» data-expand=»300″ data-tracking-container=»true» />
Mihajlo Ckovric / Stocksy
«The reverse crunch is a classic core-strengthening move that targets the lower abdominals,» says Boncompagni. «Unlike regular crunches, which are performed with the feet on the floor and work more of the upper abs, reverse crunches are done with legs lifted off the floor.»
Benefits of Reverse Crunches
Boncompagni shared several key benefits of this core exercise.
They target those pesky lower abs.
Reverse crunches earn a spot in many core routines because they target the lower abs, which are notoriously difficult to strengthen and tone. «They work the rectus abdominis,» Boncompagni continues, «which are the muscles on the front of the abs—what people often refer to as your ‘six-pack muscles.’ They really focus on the lower portion of these muscles, which can be harder to train, so it’s a great exercise to include in your ab routine.» Though you certainly don’t need to concern yourself with achieving chiseled abs, having a strong core is critical for optimal health, injury prevention, posture, and movement efficiency, so it’s important to make sure you’re strengthening your lower abs, too.
They can improve your posture.
Reverse crunches also activate your deep core muscles, such as the transversus abdominis, which helps you maintain healthy posture, especially when sitting for long periods of time.
They strengthen your mind-body connection.
«Because this move really requires you to focus on the squeeze of the abdominals and working from the lower abs, it is totally mental and builds the neurons between your brain and your body,» Boncompagni says. «So, while I’m training my abs, I’m also training my mind, and I have a greater mind-body connection.»
They are safe for your neck and back.
A common complaint with standard crunches and many abs exercises is that they bother the neck. And with good reason—they involve flexing the neck, and many people make the mistake of interlacing their hands behind their head and pulling too much on their head, further straining the neck. Reverse crunches don’t involve neck flexion and are safer for the spine overall.
They don’t require any equipment.
You can definitely spice up reverse crunches with variations like using resistance bands and ankle weights, but a real perk of the exercise is that it can be done anytime, anywhere, with just your body and the floor (though a good mat is recommended). Any exercise that avoids the gym wins my support.
They help you feel more confident in your body.
One of the greatest benefits of exercising is that it helps us feel more confident and powerful in our bodies. Boncompagni says reverse crunches will do just that. «I love how exercises like this help me build a better relationship with my body, They truly make me feel more embodied, more in my skin, and, therefore, more confident,» she notes. «It’s so magical. It impacts the way I walk, the way I hold myself, and the way I feel in my skin.»
How Do I Do Them Properly?
Boncompagni walked us through how to perform a perfect reverse crunch. Work up to completing two or three sets of 20 reps.
«It’s important that your back is protected from the floor, so these are best done on a bench or mat with a lot of cushioning support,» advises Boncompagni. «Also, make sure your back remains flat on the mat.»
When Can I Expect to See Results?
» data-caption=»» data-expand=»300″ data-tracking-container=»true» />
Klaus Vedfelt / Getty Images
«In my personal experience, it takes three weeks to a month of consistent effort in the gym to see a difference in the mirror or how your clothes are fitting,» says Boncompagni. Keep in mind, nutrition is also important when it comes to seeing results. But, more important than «seeing» results aesthetically is starting to feel the benefits of a stronger core.
Boncompagni adds that if you really want to see and feel a difference in your abs, reverse crunches aren’t enough. «The best approach is to combine reverse crunches with other moves that target those core muscles—I’m talking planks, pikes, etc.—in addition to weight training, running, yoga, or any other form of exercise that you enjoy that also helps strengthen the core,» she suggests.
Do Reverse Crunches Boost My Overall Health?
» data-caption=»» data-expand=»300″ data-tracking-container=»true» />
Ivan Gener / Stocksy
«This move has benefits far beyond toning. Reverse crunches are great for anyone to do, but conditioning your core, including your lower abs, is especially helpful if you suffer from chronic back pain related to muscular imbalance or poor posture,» says Boncompagni. «Because so many of us are not getting enough movement in our days, we might be disengaging our abs as we work at a desk, which will lead to worsening posture, more back problems, and make us more vulnerable to injuries.»
That being said, if you experience persistent back or hip pain when performing reverse crunches, it’s important to see a physical therapist to address muscle imbalances or other limiting factors.
Level Up Reverse Crunches
Once you’ve mastered basic reverse crunches, you can kick it up a notch by trying one of several common variations, such as lifting your shoulder blades off the floor simultaneously. «The key thing with all of these variations is to really slow down the exercise so you aren’t relying on momentum to do the work,» says Boncompagni. «Whether or not you are also lifting your shoulder blades off the floor with each rep, the magic happens when you focus on squeezing from the lower abs to lift the legs and hips.»
Seated
This version engages your lower back, abs, and hip flexors, putting nearly your whole core to the test.
With Resistance Band
This variation adds resistance to ramp up the intensity of the exercise.
Oblique
You’ll target your obliques with this variation for an even more all-encompassing core exercise.
Huxel Bliven KC, Anderson BE. Core stability training for injury prevention. Sports Health. 2013;5(6):514-522.
Rasouli O, Arab AM, Amiri M, Jaberzadeh S. Ultrasound measurement of deep abdominal muscle activity in sitting positions with different stability levels in subjects with and without chronic low back pain. Man Ther. 2011;16(4):388-393.
Zamani Sani SH, Fathirezaie Z, Brand S, et al. Physical activity and self-esteem: testing direct and indirect relationships associated with psychological and physical mechanisms. Neuropsychiatr Dis Treat. 2016;12:2617-2625.
How to Reverse Engineer Software (Windows) the Right Way
In this article, we discuss the knowledge base needed to perform reverse engineering, basic principles of reverse engineering a piece of Windows software, disassemblers, and tools. We also provide a step-by-step example of reverse engineering an application.
Network Security Team
Security Research Leader
What is software reverse engineering?
Reverse engineering is the process of uncovering principles behind a piece of hardware or software, such as its architecture and internal structure. The question that drives reverse engineering is How does it work?
Obviously, if you have documentation, the whole process becomes much simpler. But it often happens that there’s no documentation and you need to find another way to learn how a piece of software works.
When might you need to reverse engineer a piece of software and how might doing so help you?
There are many uses of reverse engineering in the field of computer science, including:
The legality of reverse engineering depends on its purpose and how the software will be used. All the purposes mentioned above are completely legitimate, assuming you’ve obtained a copy of the software legally. But if you intend to, for example, reverse engineer a certain feature of a closed application and then implement it in another application, you’ll probably get into trouble.
Regarding legal documentation, reverse engineering is often prohibited by end-user license agreements (EULAs). But the US Digital Millennium Copyright Act specifies that reversing a piece of software is legal if it’’ done to improve compatibility with other products.
Legal requirements vary from country to country, so take your time to research them before you start.
Now let’s see how to reverse engineer software.
What do we need for reverse engineering?
To start reverse engineering software, you need:
Let’s consider a generic example that isn’t connected to software. Let’s say you have a watch and you want to find out if it’s mechanical, quartz, or automatic.
Having knowledge of the field means you should know that there are three types of watches. Additionally, you should know that if there’s a battery, it’s located inside the watch, and you can see it if you open it up. You should also have basic knowledge of a watch’s internal structure, what the battery looks like, and what tools you need to open a watch case. Having the tools to apply your knowledge means that you need to have a screwdriver or other dedicated tool that will give you the chance to open the watch.
Just like reverse engineering a watch requires a specific skill set and tools, reverse engineering software requires its own field-specific knowledge and tools.
Theoretical Knowledge. Software Reverse Engineering Process
For different software reverse engineering tasks, you need different types of knowledge. Of course, there’s common knowledge that will help you in most reverse engineering tasks: knowledge of common application structures, programming languages, compilers, and so on. However, without special theoretical knowledge, you can’t solve specific reverse engineering tasks.
You need knowledge of.
reverse engineer any network applications
principles of inter-process communications, the structure of networks, connections, network packets, etc.
reverse cryptographic algorithms
cryptography and the most popular algorithms used in the field
research file structures
basic file concepts and how different systems or components work with files
Special techniques can save a lot of time while reversing special types of software. In the case of file interactions, making a test that writes unique type values to a file while logging the offsets and data size to the actual storage file may help you find common patterns in offsets. This will give you a hint about the internal structures of these files.
When starting the process of reverse engineering, software developers generally use a disassembler in order to find algorithms and program logic in place. There are many different executable file formats, compilers (which give different outputs), and operating systems. This diversity of technologies precludes the use of one single technology for reversing all types of software.
To understand the decompiled code, you need some knowledge of the assembler language, function calling conventions, stack structure, stack frames concept, etc.
Knowing the assembler output for different code samples may help you in uncovering the original functionality. Let’s consider some reverse engineering examples for the Windows x86 platform.
Let’s say we have the following code:
If we compile this code to an executable file, we’ll see this in the disassembler:
As we can see, the regular cycle turned into assembly code with comparisons and jumps. Notice that the assembly code doesn’t use the regular assembly loop with the counter in the ecx register. In addition, local variables here are referred to as [ebp-14h] and [ebp-8] accordingly.
Let’s see what will happen if we compile this code using the release build:
This piece of code doesn’t look anything like the previous. This is because of how the code was optimized. Technically, the loop was removed, since it’s not doing anything valuable other than incrementing the count variable to 10. So the optimizer decided just to keep the final value of the count variable and place the value directly as an argument for the count output operator.
The compilers that we use nowadays are very good at optimizing code. That’s why when reverse engineering, it’s better to understand the idea behind the code (the principles of the code) rather than to try getting the original code itself. If you understand the idea behind the code, you can just write your own prototype that fits the original task.
It will be very useful to know what assembly code you’ll get if you compile different operators, structures, and other language constructions. Understanding resultant assembly code is a good way to start the C++ reverse engineering process, but we won’t get into technical details of it here.
Useful tools for reverse engineering Windows software
We’ve already described several reverse engineering tools, including ProcessMonitor and ProcessExplorer, in our application architecture research. These tools are absolutely indispensable for reverse engineering.
In this section, we’ll review the most popular disassemblers and a few more tools that we use for our reverse engineering projects.
You can get more details and usage examples in our article on best software reverse engineering tools.
Disassemblers
A disassembler is a program that translates an executable file to assembly language. The most popular one is IDA Pro
IDA Pro is a convenient and powerful tool for disassembly. It has a huge number of instruments that allow you to quickly disassemble a piece of software. It can show the function call tree, parse import and export of the executable, and show information about them. It can even show the code in C. Also, it supports multiple CPU architectures, so it’s possible to use IDA Pro to reverse engineer code for ARM, AVR, M68k, and many other architectures.
The Radare disassembler is an alternative to IDA. It basically has all the IDA features without being as robust and stable. But it’s free and open source. Radare itself is a console tool, but it has a Cutter frontend, which makes it a true alternative to IDA.
Windows Sysinternals
Windows Sysinternals utilities are generally used for management, diagnostics, troubleshooting, and monitoring of the Microsoft Windows environment. But they’re also suitable for reverse engineering Windows software.
TCPView is a network sniffer that shows all information about TCP/UDP packets from all processes. This tool is useful for reversing network protocols.
PortMon is a physical system port monitor. It monitors serial and parallel ports and all traffic that goes through them.
WinObj shows all global objects in the system in a hierarchical structure. This tool can be useful when reversing an application that works with synchronization primitives such as mutexes and semaphores and also when reverse engineering kernel mode drivers.
Network monitoring tools
Wireshark is one of the most powerful network sniffers. It not only allows you to capture network traffic but also contains parsers for various network protocols, starting from really low-level like Ethernet, TCP, and IP to application-specific protocols like WebSockets and XMPP.
Fiddler is a web proxy that records traffic from browsers and allows you to analyze HTTP/HTTPS requests. Unlike Wireshark, it shows HTTP sessions instead of separate network packets. Fiddler also allows you to analyze compressed data sent over HTTP and analyze JSON and XML data when monitoring SOAP, REST, and AJAX requests.
API Monitor is a useful tool for discovering which APIs are called by an application and what behavior the application expects from those APIs. This tool has a powerful database and lets you see calls to a huge number of API functions of not only kernel32 and ntdll but also COM, managed environment, and others. Also, API Monitor provides convenient filtering mechanisms.
Debuggers
A debugger is invaluable for any developer to see what a program is doing right now. You get the same benefit from debugging when reversing applications as you get from debugging live applications.
The most popular debuggers are OllyDbg, WinDbg, and Windbg Preview.
OllyDbg (and its successor x64dbg) is probably the best debugger when it comes to software reverse engineering. It was specifically developed for the needs of reversing, and has all the tools needed for that purpose:
The ability to parse API functions and their parameters makes it easy to reverse interactions with a system. The stack view provides a lot of information about the call stack. One more important advantage is that you may use OllyDbg with debug-protected applications, when usual reverse engineering debuggers just can’t do anything.
Despite its simple interface, WinDbg has powerful tools for debugging. It has a built-in disassembler, various commands that allow you to know almost everything about the process/system you’re debugging, and the ability to do kernel-mode debugging, which is probably the most valuable feature. It’s a big advantage for reversing drivers, kernel-mode drivers in particular.
Windbg Preview is a new version of Windbg developed by Microsoft. It’s distributed via the Windows Store only. It has all the features of the classic Windbg coupled with a new UI and several new features. One of these new features is Time Travel Debugging, which allows you to record some period of program execution and then replay it as many times as you need. This way, you can execute the interesting parts of the code by stepping, without being afraid to run some code accidentally and lose the context or all the data.
Real-life software reverse engineering example
Now we’ll see an example of how to do reverse engineering for a piece of software. Let’s imagine you have a suspicious executable file. You need to find out what this program does and if it’s safe for users.
Considering the scenario, it’s a good idea not to run this executable on your work computer but to use a virtual machine instead. Let’s start the application in our virtual machine.
Process creates a service
As we can see, this file creates a Windows service named TestDriver. It has the type kernel, so we know it’s a driver. But where does it take the driver file from in order to run? We can use ProcessMonitor from Sysinternals Suite to find out. When we open ProcessMonitor, we can set up filters to show us only the file activity from the process we’re interested in. Its activity log looks like this:
The driver file is created by the process that we’re reversing, and this process puts this file in the user’s temp directory. There’s no need to look for the file in the temp folder since we see that the process deletes it right after use. So what does the process do with this file? If it unpacks the file, we may try to find it in the process’s resource section, since this is a common place to store such data. Let’s look there. We’ll use another tool – Resource Hacker – to examine the resources. Let’s run it:
Examine resources with Resource Hacker
Bingo! As we can see from the found resource content, this is probably the Windows executable file, since it starts with an MZ signature and has the string “This program cannot be run in DOS mode.” Let’s check if it’s our driver file. For that purpose, we extract the resource using Resource Hacker and open it in the disassembler.
As we know, DriverEntry is the entry point for kernel-mode drivers in Windows systems. We can continue our research, as it looks like we’ve found the right driver.
How to reverse engineer a driver
Some lines are omitted here for the sake of simplicity.
In the second listing, we see that ZwCreateFile is indeed called, which makes us pretty sure that the driver creates the file – and we know where this file is located after it’s created.
From the third and fourth listings, we can see that the driver takes the unicode string and writes it to the buffer (this happens in the sub_11150 function), and the buffer will be written to the file using the ZwWriteFile function. At the end, the driver closes the file using the ZwClose API.
Let’s summarize. We found out that the original program extracts the driver file from its resources, puts it in the temp folder of the current user, creates the Windows service for this driver, and runs it. After that, the program stops and deletes the service and the original driver file from the temp directory. From this behavior and from analyzing the disassembly, it appears that the driver doesn’t do anything except create a file on the C drive named hello.txt and write the string “Hello from driver”.
Now we need to check if we’re correct. Let’s run the program and check the C drive:
Wonderful! We’ve reverse engineered this simple computer program and now we know that it’s safe to use.
We could have achieved this result in many different ways – using debugging or API Mon, writing tests, etc. You can find your own ways to reverse engineer software that work for you.
Conclusion
Windows software reverse engineering requires a solid educational background and reverse programming experience. In order to perform reverse engineering, you need to combine skills in disassembling, network monitoring, debugging, API integration, several program languages, compilers, etc. You also have to be very careful when reversing software in order not to break copyright laws or harm your system.
At Apriorit, we have an experienced team of reverse engineers. If you want to apply reverse engineering skills to your project, feel free to contact us!
Read more about how reverse engineering can augment your project below!









:max_bytes(150000):strip_icc()/hallie-2-c10888b0350644d7b625adcf133aeb9a.jpg)
:max_bytes(150000):strip_icc()/jen-polzak-0c2ff49735874e69a9acf0b2c25440f8.jpg)
:max_bytes(150000):strip_icc()/karli-08ccbde0d5574a829d3c0248789b6738.jpg)
:max_bytes(150000):strip_icc()/Stocksy_txp12eb29e7XC7300_Medium_2218184-7b8416b8e00546529563f511a380d9fc.jpg)
:max_bytes(150000):strip_icc()/reverse-crunch-5c81731f4cedfd000190b129.gif)


















