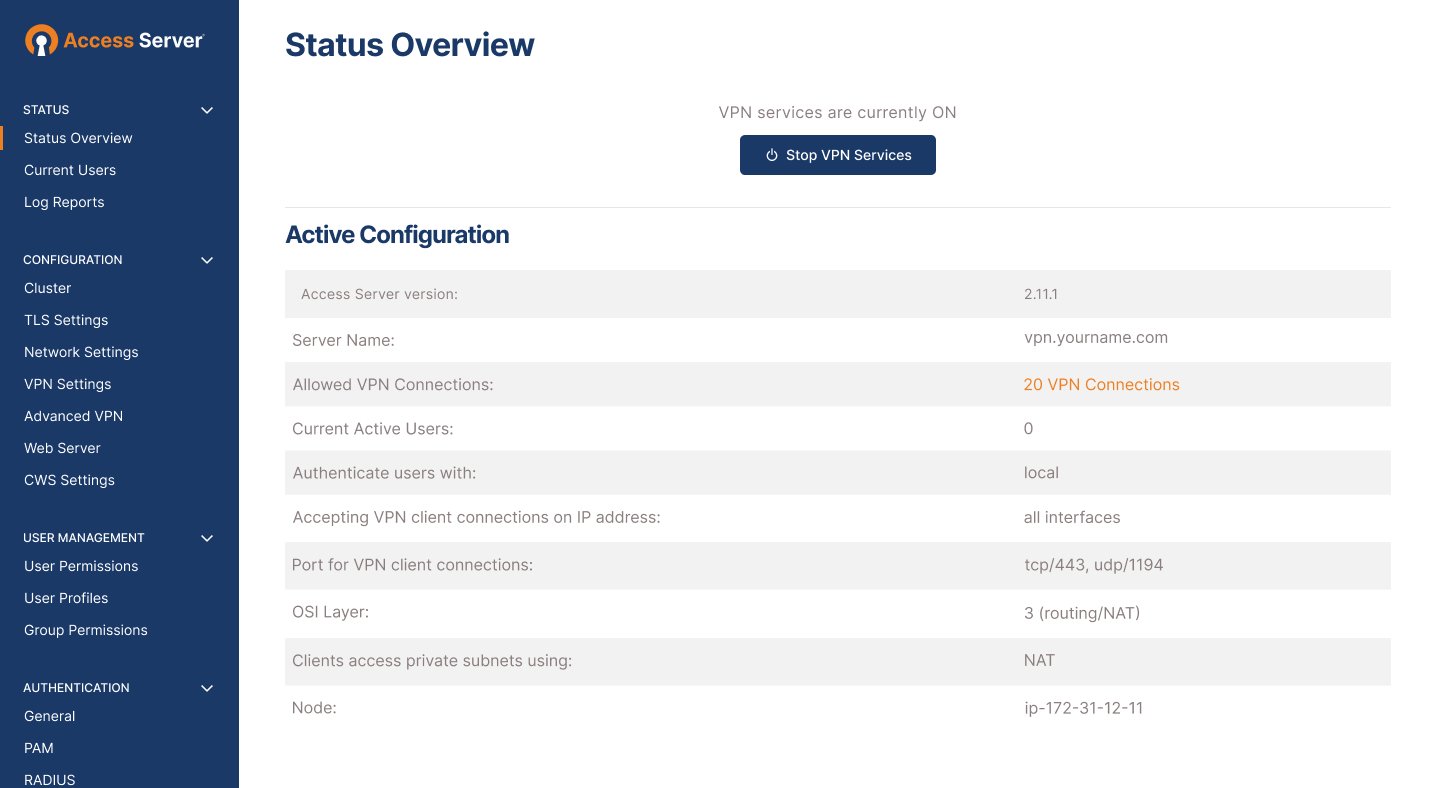
How to connect to openvpn
How to connect to openvpn
Connecting to Access Server with Linux
Client software choice
Connecting to OpenVPN Access Server from Linux requires a client program. It will capture the traffic you wish to send through the OpenVPN tunnel, encrypting it and passing it to the OpenVPN server. And of course, the reverse, to decrypt the return traffic.
Linux Packages Discussed
| OpenVPN Access Server | openvpn-as |
| OpenVPN 3 Linux Client | openvpn3 |
| OpenVPN open source | openvpn |
OpenVPN 3 Linux Client
The OpenVPN 3 Linux project is a new client built on top of the OpenVPN 3 Core Library. This client is the official OpenVPN Linux Client program. You can find an overview of the features, frequently asked questions, and instructions on installing the openvpn3 package on our OpenVPN 3 for Linux site.
After following the instructions there to install the client, you’ll need a connection profile. This is a file generated by your OpenVPN Access Server installation for your specific user account. It contains the required certificates and connection settings. Go to the Client web interface of your Access Server (the main address, not the /admin portion). Log in with your user credentials. You will be shown a list of files available to download. Pick the user-locked profile or the auto-login profile, and you will be sent a client.ovpn file. Save this file to your Linux operating system.
Once you’ve moved the file to your Linux system, you can import it.
You can start a new VPN session:
You can manage a running VPN session:
And so on. More details can be found here: OpenVPN3Linux.
OpenVPN open source OpenVPN CLI program
The open source project client program can also connect to the Access Server. The package is available in most distributions and is known simply as openvpn. It supports the option to connect to multiple OpenVPN servers simultaneously, and it comes with a service component that can automatically and silently start any auto-login profiles it finds in the /etc/openvpn folder, even before a user has logged in. This service component can be set to automatically start at boot time with the tools available in your Linux distribution if supported. On Ubuntu and Debian, when you install the openvpn package, it is automatically configured to start at boot time.
To install the OpenVPN client on Linux, it is possible in many cases to just use the version that is in the software repository for the Linux distribution itself. If you run into any connectivity problems when using outdated software, it may be due to a possible lack of support for higher TLS versions in older versions of OpenVPN. Follow the instructions found on the open source openvpn community wiki if you wish to install the OpenVPN client on your Linux system.
After installing, you will need a connection profile. This is a file generated by your OpenVPN Access Server installation for your specific user account. It contains the required certificates and connection settings. Go to the Client web interface of your Access Server (the main address, not the /admin portion). Log in with your user credentials. You will be shown a list of files available to you for download. Pick the user-locked profile or the auto-login profile, and you will be sent a client.ovpn file. Save this file to your Linux operating system somewhere. OpenVPN Access Server supports server-locked, user-locked, and auto-login profiles, but the OpenVPN command line client is only able to connect with user-locked or auto-login connection profiles.
We are assuming you are going to start the connection through either the command line as a root user, or via the service daemon. If you want unprivileged users to be able to make a connection, take a look at the community wiki for more information on how to implement that. Here we are going to focus on the simplest implementation; run the connection as root user directly, or via the service daemon.
Start a connection with an auto-login profile manually:
Start a connection with a user-locked profile manually:
If you use Google Authenticator or another extra factor authentication, add the auth-retry parameter:
To start an auto-login connection via the service daemon, place client.ovpn in /etc/openvpn/ and rename the file. It must end with .conf as file extension. Ensure the service daemon is enabled to run after a reboot, and then simply reboot the system. The auto-login type profile will be picked up automatically and the connection will start itself. You can verify this by checking the output of the ifconfig command; you should see a tun0 network adapter in the list.
One major feature that is missing with the command line client is the ability to automatically implement DNS servers that are pushed by the VPN server. It is possible, but it requires you to install a DNS management program such as resolvconf or openresolv, and it may or may not clash with existing network management software in your OS. The idea here, however, is that you use a script that runs when the connection goes up, and when it goes down, that uses resolvconf or openresolv to implement the DNS servers for you. The reason why this client is not able to manage it completely by itself is mainly because in an operating system like Windows, Macintosh, Android, or iOS, there is already an established single method of handling DNS management. It is therefore easy for us to create a software client for those operating systems that already knows how to handle DNS. But Linux is available in so many variations and also supports different programs and methods of implementing DNS servers, and so it was only reasonable to leave built-in DNS support out of the OpenVPN program and instead to provide, where possible, a script that handles DNS implementation. Such a script could even be written by yourself to do whatever tasks are necessary to implement the DNS servers in your unique situation.
Fortunately on Ubuntu and Debian, for example, there is the /etc/openvpn/update-resolv-conf script that comes with the openvpn package that handles DNS implementation for these operating systems. You need only to activate the use of these by following the instructions:
Open your client.ovpn file in a text editor:
At the very bottom simply add these lines:
The first line enables the use of external scripts to handle the DNS implementation tasks. The up and down lines are there to implement DNS servers pushed by the VPN server when the connection goes up, and afterwards to undo it, when the connection goes down.
Ubuntu network management program
How To Connect To A VPN Server With OpenVPN Connect
Introduction
This guide covers how to connect to a server with the OpenVPN Connect app.
With OpenVPN Connect v3, you can connect to:
OpenVPN Connect v3 downloads
You can download the install files for OpenVPN Connect v3 for Windows, macOS, Android, and iOS here: OpenVPN Connect Client—our official VPN client.
For the Linux operating system, there is a command-line client available.
You can also download the app for your OpenVPN Access Server or OpenVPN cloud connection:
Launching OpenVPN Connect v3
After downloading OpenVPN Connect, install the program on your device.
After installing the program on your respective OS, you receive some one-time messages about onboarding, the license agreement, and deprecated functions the first time you launch it.
Connecting to OpenVPN Access Server
To connect to an OpenVPN Access Server with a Windows or macOS computer, we recommend a direct download. You can do this by signing in to your OpenVPN Access Server’s client web UI. When you download and install the OpenVPN Connect v3 client from the client web UI, it is pre-installed with the necessary configuration profile. You or your user can start the connection immediately after installation.
If you prefer to download the Connect app directly from our site, follow the instructions below to import a configuration profile.
To connect with an already installed client, simply import a configuration profile directly from your server or use a file on your computer.
Connecting to OpenVPN Cloud
Download the client from our website, then use the instructions below to import a configuration profile directly from the server. When a new user gets an invite to OpenVPN Cloud, they can follow the instructions in their email to connect.
Import a configuration profile from the server
You can import a configuration profile directly from a server for our official business VPN products, OpenVPN Access Server and OpenVPN Cloud. To do this, open the program and click on the + icon on the main screen.
In the Import Profile window, enter the address of your server. For Access Server, this could be https://vpn.yourcompany.com/. For OpenVPN Cloud, this is your cloud tenant ID with ‘openvpn.com’ such as https://yourcompany.openvpn.com/.
Note: When you create a new user from your OpenVPN Cloud portal, they receive an email invitation with instructions for downloading the client and connecting with their assigned username and a temporary password.
Click Next, and you will be prompted to sign in with your credentials. If you receive a certificate error message, this is because your Access Server uses a self-signed certificate. We recommend installing a valid SSL web certificate and using a fully qualified domain name.
A new cloud user authenticating with a temporary password, is prompted to create a new password within OpenVPN Connect.
After successful authentication, the new profile is added to the list of profiles on your main screen. You can now easily connect and disconnect at any time.
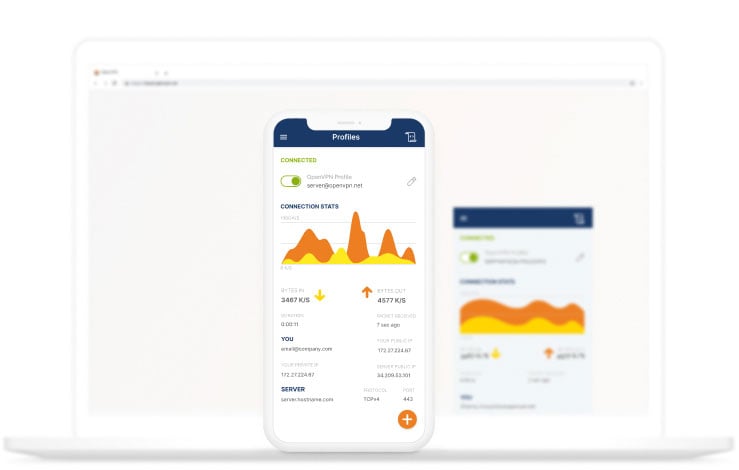
Starting a connection
On OpenVPN Connect’s main screen, any configuration profile already loaded displays.
By clicking on the toggle next to a profile, you can start or stop a connection at any time. Once the connection establishes, statistics and information about the connection display.
You can easily disconnect at any time and return to the main screen.
Connecting to OpenVPN open source
If you are connecting to an OpenVPN open-source-based server, you may download the client from our website and use the instructions below to import a configuration profile from a file on your computer.
Import a configuration profile from a file
Importing a configuration profile from a file works for almost any OpenVPN server. You simply need the necessary file(s) saved to your device. Start by clicking on the + icon, then choose File.
Either drag the profile file to the window or point the program to it by clicking on Browse and then Open.
Make sure to click on Add, and the profile displays on the main screen, where you can easily connect or disconnect.
How do I connect a VPN client device to OpenVPN Access Server?
This FAQ provides you with information on how to connect VPN clients to OpenVPN Access Server.
How to connect using the Client UI to download the app or a config file
OpenVPN Access Server hosts a Client UI that your users can use to download clients and configuration files that are specific to your VPN server.
How to import a profile using the OpenVPN Connect app
If you don’t already have the OpenVPN Connect app installed, you can download a version for your operating system from our website for free: OpenVPN Connect | Our Official VPN Client.
After you have installed the OpenVPN Connect app, follow these steps:
General compatibility guide
OpenVPN Access Server is compatible with the OpenVPN protocol — an open source standardized protocol. Therefore, most devices that support the OpenVPN protocol can connect to Access Server. However, due to the enormous flexibility of OpenVPN software, it is possible that certain configuration choices can block or disable some options on a client device, which can prevent a successful connection.
The operating systems that are supported by the official OpenVPN Connect app are Windows, macOS, Linux, Android, and iOS. These operating systems are also supported by most open source and third-party commercial OpenVPN client programs and devices.
Conclusion
OpenVPN Access Server is compatible with most VPN clients that use the OpenVPN protocol. OpenVPN provides a free VPN client, OpenVPN Connect, to easily connect with your VPN server. Each implementation of Access Server also provides a Client UI, from which users can download pre-configured OpenVPN Connect apps and configuration files.
Quick Start Guide
QUICK START / ACCESS SERVER
OpenVPN Access Server Quick Start Guide
Setting up OpenVPN Access Server on Linux
Follow this high level overview to set up OpenVPN Server and OpenVPN Access Server Admin Web UI. For more details, refer to the Admin Web UI User Manual.
OpenVPN Access Server fits seamlessly with Linux. Our latest releases come through our software repository. It provides you with the following three components:
OpenVPN Server
The VPN server is the underlying component in OpenVPN Access Server.
Admin Web UI
The online admin web interface provides an easy UI for managing the server.
OpenVPN Connect
This is the client app to connect users to the VPN. Your server comes with a web-based Client UI with pre-configured apps available for download. You can also download a configuration file.
Choosing Your Platform
You can host a server on-premise, with a virtual machine, or through a cloud service provider. The first step is to choose the appropriate platform on our downloads page. Then you’ll launch your new VPN server.
We provide specific quick start guides for each option. These make it easy for you to get your VPN up and running.
Linux OS
Copy and paste the repository commands and execute with root privileges
Virtual machine
Select one of our pre-configured appliances
Cloud service provider
Select the OpenVPN instance from their marketplace
Obtain Admin Web UI login details
Once you install OpenVPN Access Server on your selected platform from above, you can configure your VPN using the web-based Admin Web UI. In the last step of the installation process, a randomly generated password for the openvpn administrative account will be shown on the console.
Then connect to the Admin Web UI with that username and password. The URL will be along the pattern of https://[youripaddress]/admin/
Replace “[youripaddress]” with the static IP address of your server.
Note: Access Server versions older than 2.10 don’t automatically generate a password. On older versions, set the password manually by typing passwd openvpn on the command line.
Next Steps
Once you’ve signed in to your web-based Admin Web UI, you can configure your VPN. These next steps will guide you through setting up a custom hostname, configuring network settings, adding users, and additional security steps.
Interfaces
The Admin Web UI
The Admin Web UI provides an intuitive tool to manage settings for your VPN server. Refer to the OpenVPN Access Server User Manual for details about the configuration options and functionality within the tool.
OpenVPN Connect
OpenVPN Connect is our free, full-featured VPN Client.
To download a pre-configured app via web browser, simply navigate to the IP address or hostname of your VPN server: https://[youripaddress]
You may also download OpenVPN Connect directly here, and import the config file.
How to setup a VPN Connection with OpenVPN
I admit, at the beginning, The thought of building a VPN for Home sounds about obscure.
Those are just a few of the reasons why I think a VPN to your home is a good Idea.
It is very easy to set up.
Well… for several reasons. I think that the first, is none of the tutorials I have seen do not address the client side example of the connection (through the NetworkManager GUI). Second there are a few tips and tricks to make it easier to maintain and produce a more advanced configuration (like PAM).
I assume that your Raspberry Pi is already installed with CentOS and EPEL.
In this tutorial we are working with the assumption that your internet connection does not consist a static IP and that you do own a public domain.
For this scenario the following document will provide several alternatives that will help you get the job done.
Static / Dynamic IP
In case your ISP has provided a static IP address to your account then you are in a good position. You can go to one of the known domain provides such as :
And buy a nice domain for about 3–12 dollars a year.
If you are using a Dynamic IP address then you can use one of the following dynamic DNS provides :
Once you create an account you need to setup a client/cron to keep your DNS record update 2 date.
(I advise you (if you can) to look at your router settings. Most routers today come with a variety of clients for well known dynamic DNS provides in order to skip the client installation).
For This tutorial I will use example.duckdns.org as the domain for the certificate this is how I did it :
Server Side
Installing the Server
We are now installing OpenVPN 2.4 with easy-rsa 3
When the installation is complete, check the openvpn and easy-rsa version.
The certificates in OpenVPN are not complicated to setup but they do require some attention.
There are 2 types of certificates we can generate, each has its own advantages and disadvantages so we will go through both options (you can choose whichever you like.
Private Certificate (easy-rsa)
You will have to know and get yourself familier with SSL/TLS which in most cases a necessity and not a requirement by the Server Admin (you)
Configure Easy-RSA 3
In this step, we will configure easy-rsa 3 by creating new ‘vars’ file. The ‘vars’ file contains the Easy-RSA 3 settings.
Go to the ‘/etc/openvpn/’ directory and copy the ‘easy-rsa’ script.
Now go to the ‘easy-rsa/3/’ directory and create new vars file using your favorite EDITOR (I prefer VIM)
Paste the vars easy-rsa 3 configuration below.
Build OpenVPN Certificates and Keys
In this step, we will build the OpenVPN keys based on the easy-rsa 3 ‘vars’ file that we’ve created. We will build the
Now make the ‘vars’ file executable by changing the permission of the file.
The vars file for Easy-RSA 3 setting has been created.
Before building any keys, we need to initialize the PKI directory and build the CA key.
Initiate the PKI directory and build the CA key using the command below.
Now type the password for your CA key and you will get your ‘ca.crt’ and ‘ca.key’ files under the ‘pki’ directory.
Build Server Key
Now we want to build the server key, and we will build the server key named ‘my-server’.
Build the server key ‘my-server’ using the command below.
When you are prompted for a common name (CN) then input your public fully qualified domain name (FQDN) : example.duckdns.org (from the duckdns.org record in our example)
Sign the ‘my-server’ key using our CA certificate.
You will be asked for the ‘CA’ password, type the password and press Enter. And you will get the ‘hakase-server.crt’ certificate file under the ‘pki/issued/’ directory.
Verify the certificate file using the OpenSSL command and make sure there is no error.
All server certificate keys have been created. The server private key is located at the ‘pki/private/my-server.key’, and the server certificate on the ‘pki/issued/my-server.crt’.
Build Diffie-Hellman Key
This action will take a lot of time, depending on the key length that we chose and the available entropy on the server. We will be using the length key that we define on the ‘vars’ file.
Generate the Diffie-Hellman key using command below.
The DH key has been generated, located at the ‘pki’ directory.
Generate the CRL Key
The CRL (Certificate Revoking List) key will be used for revoking the client key. If you have multiple client certificates on your vpn server, and you want to revoke some key, you just need to revoke using the easy-rsa command.
Copy Certificates Files
All certificates have been generated, now copy the certificate files and PEM files.
Copy Server Key and Certificate.
Copy DH and CRL Key.
Configure the OpenVPN Server
In this step, we will create new configuration ‘server.conf’ for the openvpn server.
Go to the ‘/etc/openvpn/’ directory and create new configuration file ‘server.conf’ using your favorite EDITOR (vim).
Paste the following OpenVPN server configuration there.
With your favorite editor edit the file to look like so :
The configuration for OpenVPN has been created.
Firewall And NAT Configuration
In this step, we will enable Port-forwarding kernel module and configure routing ‘Firewalld’ for OpenVPN.
Enable the port-forwarding kernel module by running following commands:
Next, configure routing using the Firewalld for OpenVPN.
To see your zone you can run the following command :
This will give us the zone we need for our services configuration.
Add the ‘openvpn’ service to the firewalld list service and add the ‘tun0’ interface to the firewalld trusted zone.
Enable ‘MASQUERADE’ on the ‘trusted’ zone firewalld.
Enable NAT for OpenVPN internal IP address ‘10.10.1.0/24’ to the external IP address ‘SERVERIP’.
If you need to make changes the configuration are been kept at the file “direct.xml”
The “172.26.15.0/24 are taking from the server configuration and is the VPN network the Server will use for Client / Server communication.
And reload firewall.
Test the setting with the following command:
The output should look like :
And make sure the service is running without errors:
The Port-forwarding and the Firewalld routing has been completed, now start the openvpn service and enable it to launch automatically every time at system boot.
For RHEL/CENTOS 8
Now that your Server is setup we can continue with the client configuration
Client Side
In this Client Section I will go through 3 types of configuration
Everything we do in the GUI can be easily exported to a simple *.ovpn file which can be used in the CLI.
OVPN File
I want to talk about this file type for several reasons.
Private CA.
First we will want to generate a private Key + Certificate using our Private CA and for that both easy-rsa and openssl have a very easy way of doing that.(I will focus on easy-rsa for this example)
Now sign the ‘client01’ key using our CA certificate as below.
Type ‘yes’ to confirm the client certificate request, then type the CA password.
The client certificate named ‘client01’ has been generated, verify the client certificate using the openssl command.
Copy client01 Key and Certificate.
Client Machine
On the Client Machine we have 2 options we can use in regards to the OpenVPN client but as stated before the first action item is to create the ovpn file.
Here is an example of the ovpn file :
You can extend the verb option to a bigger number (up to 7) in order to receive a better verbosity in case the connection is not working.
Client CLI
This option is very simple and easy to apply and we can set it up to connect to the VPN at boot.
Copy the Client01.ovpn file to /etc/openvpn/client
Now change the directory to the /etc/openvpn/client
Now run the openvpn command and start the vpn
Now we can test the VPN connection by pinging the default gateway of the VPN network:
You should receive a reply and everything is setup correctly
Now if we want to make sure the vpn client is running at startup we need to enable it using the systemctl tool:
Systemctl enable openvpn@client
Client GUI
The GUI configuration are very simples
We are all done
Client Pubilc Certificate
Sense we configured the VPN Server which uses the public certificates with a username/password challenge response then we need to make we select it when we configure the GUI VPN connection:
Select the challenge response and pub the public CA (you can download it from letsencrypt site or take it from the VPN server :
click “Save” and you are do
try to connect to the VPN using the VPN option in your networkManagere GUI