How to create key file
How to create key file
.KEY File Extension
Software License Key File
What is a KEY file?
Typically, the software developer distributes a KEY file to a user after they purchase the software to register an application offline. The user may then need to place the file in a specific directory or open it with the application to register the software.
NOTE: Windows applications primarily use KEY files, but programs on other operating systems may also use the files.
How to open a KEY file
Programs that open or reference KEY files
LightWave 3D License File
What is a KEY file?
A KEY file is a software registration file used by NewTek LightWave 3D, a professional 3D rendering application. It stores a 16-digit license key, enabling users to activate a legal copy of the software.
LightWave 3D is a computer graphics application that renders static and animated 3D images. Professionals use the software in various fields, including television, film, video game development, building visualizations, and product design.
You will most likely only encounter a software registration KEY file when purchasing and activating LightWave 3D. For example, after purchasing LightWave 3D online, NewTek displays instructions to download LightWave 3D and provides a license.key file to register the application to your computer.
However, NewTek replaced KEY files with LWK files when it released version 11 of LightWave 3D. Therefore, to register the trial version of LightWave 3D (11.0.3 or later), place the license.lwk file in the «licenses» folder in the LightWave installation directory to register the software.
Common KEY Filenames
How to open a KEY file
KEY files are not meant to be opened. Instead, you can place the KEY file in the «licenses» folder in the LightWave installation directory to register the software.
For example, to register LightWave 10, place the KEY file in the following directory:
Although KEY files are not meant to be opened, you can open them with a plain text editor to view the license key.
Programs that open or reference KEY files
Apple Keynote Presentation
What is a KEY file?
A KEY file is a presentation created by Apple Keynote, a macOS and iOS presentation application. It contains slides that may include text, images, shapes, charts, tables, transitions, audio, video, and notes. KEY files may save various types of presentations, including financial proposals, research findings, and book report summaries.
Keynote is one of Apple’s three productivity apps that make up iWork, along with Pages and Numbers. These applications are Apple’s versions of the more popular PowerPoint, Word, and Excel programs, which are developed by Microsoft and available in the Office suite. The iWork apps are developed for macOS and iOS but can also be accessed using a browser on a Mac or PC through iCloud.
KEY files are generally used for storing presentations for academic, business, or personal purposes that Keynote can display. For example, you can create a KEY file to save a presentation filled with photos from your summer vacation, tables and charts of data detailing a business proposal, book report information for a class, and more.
Keynote comes with many templates to get you a jumpstart on your presentation, or you can start from scratch with blank slides. Then, when you finish creating your presentation, you can share it directly from your device or through Keynote Live to stream the presentation online.
How to create a KEY file
To create a KEY file with Keynote, select File → Save in the application. Keynote then creates a KEY file and saves your presentation’s contents in the file. After saving the presentation, you can close it and reopen it later for further editing.
How to open a KEY file
In macOS and iOS, you can open KEY files with Apple Keynote. To open a KEY file with Keynote on a Mac, select File → Open. in Keynote. If you are looking to only view the KEY presentation, you can open it with Apple Preview, and each slide is presented as a static image.
You can also upload KEY files to the iCloud version of Keynote in your web browser (requires an Apple ID). This is helpful for Windows users who don’t have access to the Mac or iOS versions of Keynote. In the iCloud application, you can view, edit, save, and download KEY presentations.
How do I open KEY files in Windows and Linux without an Apple ID?
How to convert a KEY file
How to Create SSH Keys with PuTTY on Windows
DigitalOcean Droplets are Linux-based virtual machines (VMs) that run on top of virtualized hardware. Each Droplet you create is a new server you can use, either standalone or as part of a larger, cloud-based infrastructure.
To create and use SSH keys on Windows, you need to download and install both PuTTY, the utility used to connect to remote servers through SSH, and PuTTYgen, a utility used to create SSH keys.
You can customize the Parameters at the bottom if you like, but the default values are appropriate in most situations. However, Fedora 33’s new encryption requirements will not accept the default RSA algorithm, so choose ECDSA or another supported algorithm when creating a key for use with Fedora 33.
When you’re ready, click the Generate button on the right-hand side.
You might be prompted to “generate some randomness by moving the mouse over the blank area”. This randomness, known as entropy, is used to create keys in a secure fashion so that other people can’t reproduce them.
When the key is generated, you’ll see the public key displayed in a text box. Copy this into your clipboard now if you plan to add it to your DigitalOcean account or to servers. Be sure to scroll within the text area so you copy the entire key.
Next, you’ll be prompted to enter a passphrase for your SSH key. This improves security by preventing someone who gains access to your private key from using it without also knowing the passphrase. You’ll need to provide your passphrase every time you use this key (unless you use SSH agent software that stores the decrypted key).
If you have not entered a passphrase, you will be asked to confirm that you want to save the key without one. We strongly recommend using a passphrase, but you can press ENTER to bypass this prompt.
Working with PuTTY’s Public Key Format
You can click Save public key as well, but take note: The format PuTTYGen uses when it saves the public key is incompatible with the OpenSSH authorized_keys files used for SSH key authentication on Linux servers.
If you need to see the public key in the right format after the private key has been saved:
The public key is redisplayed again in the appropriate format.
Now that you have your generated key pair saved on your computer and ready to use, you can:
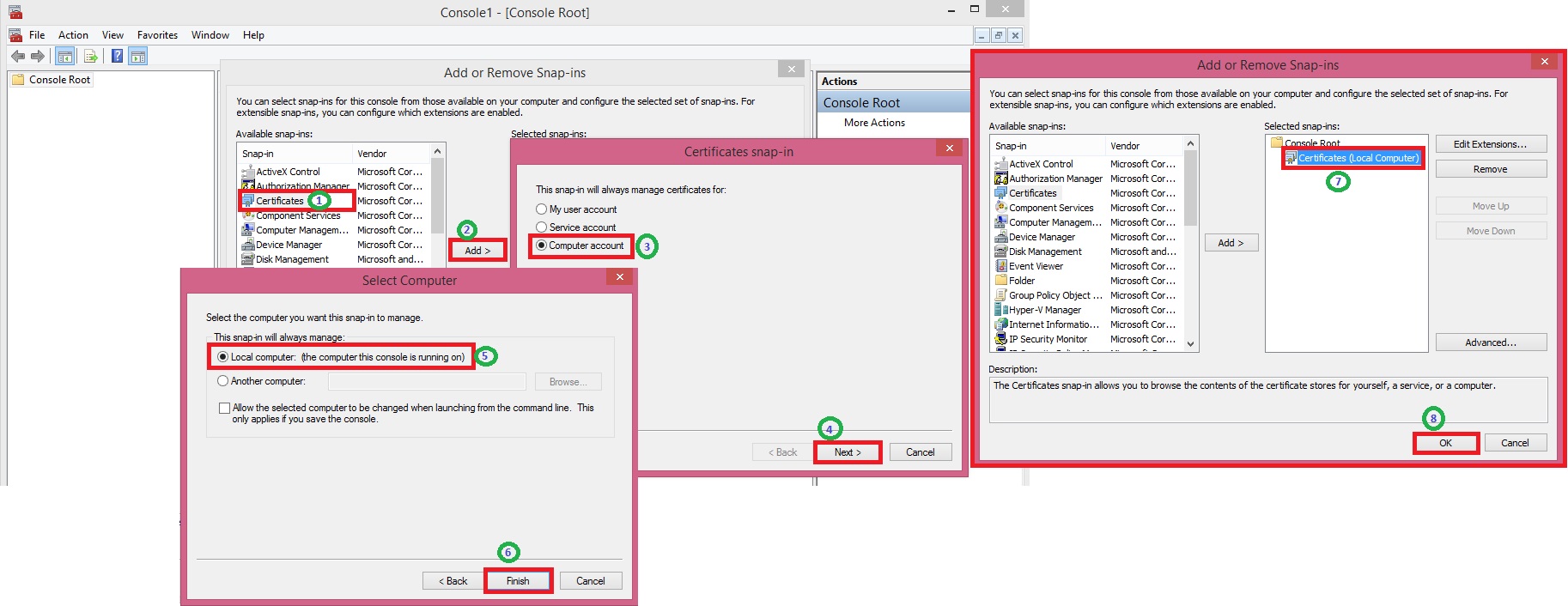
How to create a root CA and a private key file by using the makecert.exe utility
We will follow below step to create a certificate for Microsoft Dynamics Server. Then we will implement the same for login from WAN to access Navision using Windows and Web Clients.
Now we will use the Certificates snap-in to install the root CA on the computer running Microsoft Dynamics NAV Server
The RootNavServiceCA certificate is now visible in the list of trusted root CAs.
In next step we will now create a certificate revocation list for the root certification authority and then install the certificate revocation list on the computer running Microsoft Dynamics NAV Server.
A certificate revocation list is required because WCF applications check the revocation list when validating certificates.
Detailed steps: Create and manage SSH keys for authentication to a Linux VM in Azure
Applies to: вњ”пёЏ Linux VMs вњ”пёЏ Flexible scale sets
With a secure shell (SSH) key pair, you can create a Linux virtual machine that uses SSH keys for authentication. This article shows you how to create and use an SSH RSA public-private key file pair for SSH client connections.
To create SSH keys and use them to connect to a Linux VM from a Windows computer, see How to use SSH keys with Windows on Azure. You can also use the Azure portal to create and manage SSH keys for creating VMs in the portal.
Overview of SSH and keys
SSH is an encrypted connection protocol that provides secure sign-ins over unsecured connections. Although SSH provides an encrypted connection, using passwords with SSH connections still leaves the VM vulnerable to brute-force attacks. We recommend connecting to a VM over SSH using a public-private key pair, also known as SSH keys.
The public key is placed on your VM.
The private key remains on your local system. Protect this private key. Do not share it.
When you use an SSH client to connect to your VM (which has the public key), the remote VM tests the client to make sure it has the correct private key. If the client has the private key, it’s granted access to the VM.
Depending on your organization’s security policies, you can reuse a single public-private key pair to access multiple Azure VMs and services. You do not need a separate pair of keys for each VM or service you wish to access.
Your public key can be shared with anyone, but only you (or your local security infrastructure) should have access to your private key.
Supported SSH key formats
Azure currently supports SSH protocol 2 (SSH-2) RSA public-private key pairs with a minimum length of 2048 bits. Other key formats such as ED25519 and ECDSA are not supported.
SSH keys use and benefits
/.ssh/authorized_keys folder on the VM. SSH keys in
/.ssh/authorized_keys are used to challenge the client to match the corresponding private key on an SSH connection. In an Azure Linux VM that uses SSH keys for authentication, Azure configures the SSHD server to not allow password sign-in, only SSH keys. By creating an Azure Linux VM with SSH keys, you can help secure the VM deployment and save yourself the typical post-deployment configuration step of disabling passwords in the sshd_config file.
If you do not wish to use SSH keys, you can set up your Linux VM to use password authentication. If your VM is not exposed to the Internet, using passwords may be sufficient. However, you still need to manage your passwords for each Linux VM and maintain healthy password policies and practices, such as minimum password length and regular updates.
Generate keys with ssh-keygen
SSH keys are by default kept in the
/.ssh directory. If you do not have a
/.ssh directory, the ssh-keygen command creates it for you with the correct permissions. An SSH key is created as a resource and stored in Azure for later use.
You can also create keys with the Azure CLI with the az sshkey create command, as described in Generate and store SSH keys.
Basic example
The following ssh-keygen command generates 4096-bit SSH RSA public and private key files by default in the
/.ssh directory. If an SSH key pair exists in the current location, those files are overwritten.
Detailed example
The following example shows additional command options to create an SSH RSA key pair. If an SSH key pair exists in the current location, those files are overwritten.
Command explained
ssh-keygen = the program used to create the keys
-m PEM = format the key as PEM
-t rsa = type of key to create, in this case in the RSA format
-b 4096 = the number of bits in the key, in this case 4096
-C «azureuser@myserver» = a comment appended to the end of the public key file to easily identify it. Normally an email address is used as the comment, but use whatever works best for your infrastructure.
-N mypassphrase = an additional passphrase used to access the private key file.
Example of ssh-keygen
Saved key files
Enter file in which to save the key (/home/azureuser/.ssh/id_rsa):
The key pair name for this article. Having a key pair named id_rsa is the default; some tools might expect the id_rsa private key file name, so having one is a good idea. The directory
/.ssh/ is the default location for SSH key pairs and the SSH config file. If not specified with a full path, ssh-keygen creates the keys in the current working directory, not the default
List of the
Key passphrase
Enter passphrase (empty for no passphrase):
It is strongly recommended to add a passphrase to your private key. Without a passphrase to protect the key file, anyone with the file can use it to sign in to any server that has the corresponding public key. Adding a passphrase offers more protection in case someone is able to gain access to your private key file, giving you time to change the keys.
Generate keys automatically during deployment
/.ssh directory. Note that this command option does not overwrite keys if they already exist in that location.
Provide SSH public key when deploying a VM
If you’re not familiar with the format of an SSH public key, you can see your public key by running cat as follows, replacing
/.ssh/id_rsa.pub with your own public key file location:
Output is similar to the following (here redacted):
If you copy and paste the contents of the public key file into the Azure portal or a Resource Manager template, make sure you don’t copy any additional whitespace or introduce additional line breaks. For example, if you use macOS, you can pipe the public key file (by default,
/.ssh/id_rsa.pub ) to pbcopy to copy the contents (there are other Linux programs that do the same thing, such as xclip ).
If you prefer to use a public key that is in a multiline format, you can generate an RFC4716 formatted key in a pem container from the public key you previously created.
To create a RFC4716 formatted key from an existing SSH public key:
SSH to your VM with an SSH client
With the public key deployed on your Azure VM, and the private key on your local system, SSH to your VM using the IP address or DNS name of your VM. Replace azureuser and myvm.westus.cloudapp.azure.com in the following command with the administrator user name and the fully qualified domain name (or IP address):
If you provided a passphrase when you created your key pair, enter the passphrase when prompted during the sign-in process. (The server is added to your
/.ssh/known_hosts folder, and you won’t be asked to connect again until the public key on your Azure VM changes or the server name is removed from
If the VM is using the just-in-time access policy, you need to request access before you can connect to the VM. For more information about the just-in-time policy, see Manage virtual machine access using the just in time policy.
Use ssh-agent to store your private key passphrase
Verify and use ssh-agent and ssh-add to inform the SSH system about the key files so that you do not need to use the passphrase interactively.
Use ssh-copy-id to copy the key to an existing VM
Create and configure an SSH config file
You can create and configure an SSH config file (
/.ssh/config ) to speed up log-ins and to optimize your SSH client behavior.
The following example shows a simple configuration that you can use to quickly sign in as a user to a specific VM using the default SSH private key.
Create the file.
Edit the file to add the new SSH configuration
Add configuration settings appropriate for your host VM. In this example, the VM name is myvm and the account name is azureuser.
You can add configurations for additional hosts to enable each to use its own dedicated key pair. See SSH config file for more advanced configuration options.
Now that you have an SSH key pair and a configured SSH config file, you are able to sign in to your Linux VM quickly and securely. When you run the following command, SSH locates and loads any settings from the Host myvm block in the SSH config file.
The first time you sign in to a server using an SSH key, the command prompts you for the passphrase for that key file.
Next steps
Next up is to create Azure Linux VMs using the new SSH public key. Azure VMs that are created with an SSH public key as the sign-in are better secured than VMs created with the default sign-in method, passwords.
Iguana Documentation
Introduction
Iguana only supports OpenSSL SSH-2 private keys and certificates in PEM format, these must not be password protected. Iguana accepts the older “Traditional” (or “SSLeay”) PKCS#5 format (as defined in RFC2890) or in the newer PKCS#8 format (as defined in RFC5958).
Note: For production systems you will need to get SSL certificates from a Certificate Authority, see Using SSL security, certificates and verify peer etc for more information.
Task [top]
How to create self-certified SSL certificate and public/private key files.
Accepted formats [top]
If you are in hurry (and don’t need explanations), then you can just skip this section.
However if you are having a problem with Iguana not accepting your private key, then you should open the key file in a text editor and check if it matches one of two accepted formats.
Iguana will accept these two PKCS formats:
Note: Iguana will not accept SSH format defined in RFC4716, even though the format looks similar:
OpenSSL: Create a public/private key file pair [top]
This section shows you how to create a public/private key file using OpenSSL.
To generate a public/private key file on a Windows system:
To generate a public/private key file on a POSIX system:
Tip: Iguana requires PEM format keys. The ssh-keygen utility recently changed to using the (more secure) openssh private key format by default – whereas previously the default was PEM format. To generate PEM format we added the “-m PEM” option to the old command.
The public & private key files are saved in the new directory you created earlier. An example of a private key file is shown below:
You can copy the key from above. This key is to be used for testing purposes only.
Note: In this example, the 4096 parameter to the openssl genrsa command indicates that the generated key is 4096 bits long. A key that is 4096 bits or longer is considered more secure. A shorter key will be less secure, but will require less computation to use.
OpenSSL: Create a certificate [top]
This section shows you how to create a self-signed certificate file using OpenSSL.
Note: Iguana offers support for x509 compatible certificates in pem format, certificates must not be password protected.
To generate a self-signed certificate file on a Windows system:
To generate a self-signed certificate file on a POSIX system:
The self-signed certificate file is created and saved in the directory you specified earlier. An example of the certificate format is shown below:
You can copy the certificate from above. This certificate is to be used for testing purposes only.
Note: Remember that this newly created certificate file should be used for test purposes only. Normally, you would need to create a certificate request and send it to a certificate authority (CA). The CA would then sign the certificate and give it back to you upon payment, thus providing you with authentication according to their outlined policies.
PuTTYgen: Create a public/private key file pair [top]
These instructions use screenshots from Windows 7, but the process is the same in other Windows versions.
To generate a public/private key file:
The standard install of puttygen.exe is in C:\Program Files\PuTTY — but it is a standalone executable and can be run from anywhere.
PuTTYgen defaults to the desired RSA (SSH-2 RSA) key.
Other key formats like the “ssh.com” export format is not compatible with Iguana.
Make sure to scroll down to ensure you get the whole key.
How it works [top]
In order to enable HTTPS support for use with Iguana, you must first generate valid public key/private key certificates. These digital certificates are used to authenticate the sender. Keys are typically generated in pairs, with one being public and the other being private. The private key must be kept secret to ensure security. It is used to encrypt outgoing messages and decrypt incoming messages. A public key is the one that is released to the public. It allows anyone to use it for encrypting messages to be sent to the user, as well as for decrypting messages received from the user.
f you use OpenSSL to generate certificates, the private key will contain public key information, therefore the public key does not have to be generated separately. You will need to have OpenSSL installed on your machine. You can download OpenSSL for Windows or Linux from: http://www.openssl.org.
On Windows you can use the PuTTYgen program to generate public and private keys, however it does not generate certificates. You can download PuTTYgen for Windows: http://www.chiark.greenend.org.uk/
In addition to having a public/private key certificate, you must also obtain a certificate file from a certificate authority (CA), such as Verisign, which issues digital certificates for use by other parties. There are many commercial CAs that charge for their services, while other institutions may have their own CAs. To ensure that the web server (with HTTPS support enabled) functions as expected, you can create a self-signed certificate for use during the initial testing phase.
Источники информации:
- http://docs.digitalocean.com/products/droplets/how-to/add-ssh-keys/create-with-putty/
- http://ksdconsultancy.blog/2015/08/07/how-to-create-a-root-ca-and-a-private-key-file-by-using-the-makecert-exe-utility/
- http://docs.microsoft.com/en-us/azure/virtual-machines/linux/create-ssh-keys-detailed
- http://help.interfaceware.com/v6/how-to-create-self-certified-ssl-certificate-and-publicprivate-key-files