How to get access to
How to get access to
How to Get Instagram Access Token in 1 Minute
What is Instagram Access Token – Brief Description
Authenticated requests need Instagram Access token. Access Token is an opaque string that identifies a user, app, or page. It can be used by the app to make graph API calls and is unique to each user.
Instagram Access Token is essential for the usage of most Instagram based apps.
Step-by-Step Guide for Getting Instagram Access Token
In the beginning, make sure you’ve got the following:
Then proceed to the first step.
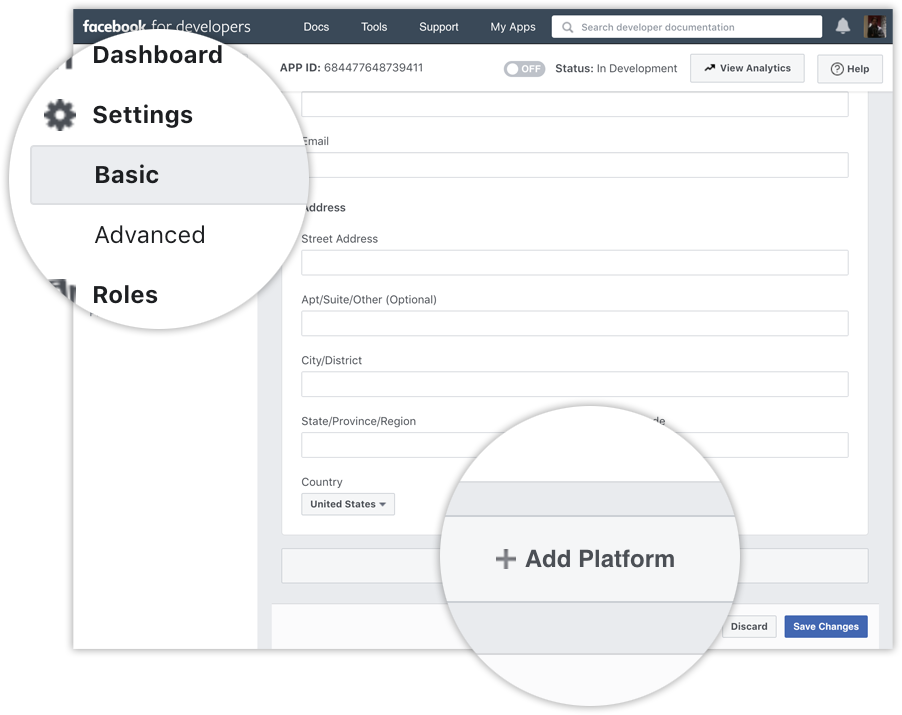
Step 1: create your Facebook App
You need to go to developers.facebook.com, then click My Apps, and create a new app. After the app is created, click Settings > Basic, scroll the bottom of page, and select Add Platform.
Then choose website, add its URL, and save the changes. Keep in mind that the platform can be changed later in case you need.
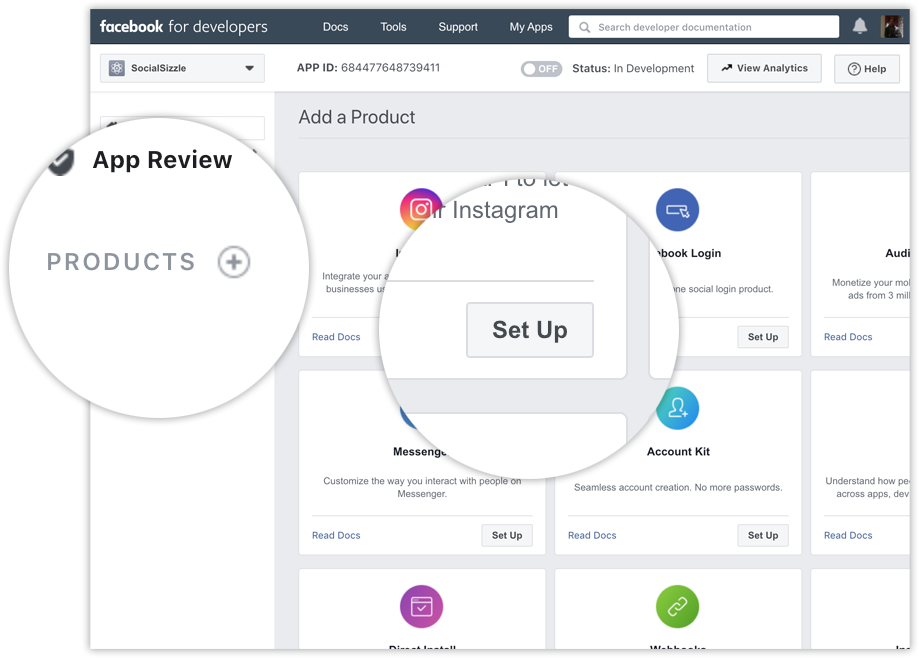
Step 2: build Instagram Basic Display
To do it, click the Products button, locate the Instagram product, and click Set Up to add it to your app.
Complete every section in the appeared form, using the following guidelines:
Now you can proceed to the next step.
Step 3: add an Instagram test user
Go to Roles > Roles and scroll down to the Instagram Testers section. Then click Add Instagram Testers and enter your Instagram account’s username and send the invitation. After that, you’ll need to open a new browser, go to www.instagram.com and sign into your Instagram account that you just invited. There navigate to Edit Profile > Apps and Websites > Tester Invites and accept the invitation.
Now your Instagram account is eligible to be accessed by your Facebook app while it is in Development Mode.
Step 4: Authenticate the Test User
Build the Authorization Window URL below, replacing app-id with your Instagram app’s ID (which can be found here: App Dashboard > Products > Instagram > Basic Display > Instagram App ID) and redirect-url with your website URL that you’ve provided before in step 2. Remember that the URL must be exactly the same.
Then you’ll need to open the browser window and load the Authorization Window URL. It should appear and display your Instagram user’s name, the app’s name, and a description of the permissions your app is requesting. To authenticate your Instagram test user you’ll need to sign into the Authorization Window, then click Authorize to grant your app access to your profile data. This page will redirect you to to the redirect URI you included in the previous step and append an Authorization Code.
Step 5: exchange your code for Instagram access token
Here you’ll need to open your command line tool or any other app supporting cURL requests and send the following POST request to the API.
Replace with your Instagram app ID, Instagram app secret, your redirect URI, and the code sent to you buy Facebook. Make sure your redirect URL exactly matches the one from the previous step.
After that, the API will return a JSON encoded object containing a short-lived Instagram User Access Token, valid for 1 hour, and your Instagram test user’s ID:
You’ll simply need to copy the access token and user ID so that they could be used in the next step.
Step 6: Query the User Node
All is left now is to query the User node for your user ID and username. Simply replace
Then the API will respond with your Instagram user ID and username:
Now you know how to get the Instagram access token and perform a basic query.
You Don’t Feel Secure?
If you embed Instagram to your site, you might have another question about your newly achieved Instagram plugin and its security: “What if someone will get my Access Token?”. Simply – nothing terrible. Here’s why.
If someone gets your Access Token then don’t worry.
You can’t do anything with Instagram Access Token except browsing photos. This token doesn’t give any access to your personal data. Moreover, it doesn’t allow making any action from your name.
Keep going and share your Instagram feed on the website!
Still Have Questions about Authorization Process?
Feel free to contact us by submitting a ticket in Elfsight Support Center. We are ready to help you with any emergent issue. By the way, stay tuned to our blog and get more useful articles and plugins’ guides!
TheCodeBuzz
Best Practices for Software Development
Recently I happen to try to figure out, How to get access token from httpContext for the current request. I wanted to read the token value from HttpContext.
Below is a simple technique explained which I used to get the access token from HttpContext.
As explained, the below piece of code is from the same sample which we learned in the JWT Authentication article,
Get Access token from HttpContext – Identity tokens Access
Access tokens enable clients to securely call protected web APIs and help perform authentication and authorization while providing access to the requested resources.
In the below example we have used “access_token” to access the JWT Bearer token.
Here in the Controller method to fetch the token,
Here is JWT Bearer token passed through HTTP request used,
Here is how we can read the above token as below in the method,
Using HTTPContextAccessor to extract Authorization header
If you need to access authentication headers or any HttpContext metadata in custom components or services or modules then please use HTTPContextAccessor as below,
Using Middleware to extract Authorization header
One can use Custom or Inline middleware also to read the HTTPContext details.
If you want to access HttpContext with intention of doing more meaningful stuff then the Adding Custom Middleware ASP.NET Core approach is more preferable.
Example: Custom Middleware
References
Do you have any comments or ideas or any better suggestions to share?
Please sound off your comments below.
Get access on behalf of a user
To use Microsoft Graph to read and write resources on behalf of a user, your app must get an access token from the Microsoft identity platform and attach the token to requests it sends to Microsoft Graph. The exact authentication flow to use to get access tokens will depend on the kind of app you're developing and whether you want to use OpenID Connect to sign the user into your app. One common flow used by native and mobile apps and also by some Web apps is the OAuth 2.0 authorization code grant flow. This article walks through an example using this flow.
Authentication and authorization steps
The following are the basic steps to use the OAuth 2.0 authorization code grant flow to get an access token from the Microsoft identity platform endpoint:
1. Register your app
To use the Microsoft identity platform endpoint, you must register your app using the Azure app registration portal. You can use either a Microsoft account or a work or school account to register an app.
To configure an app to use the OAuth 2.0 authorization code grant flow, save the following values when registering the app:
For steps on how to configure an app in the Azure portal, see Register your app.
2. Get authorization
The first step to getting an access token for many OpenID Connect (OIDC) and OAuth 2.0 flows is to redirect the user to the Microsoft identity platform /authorize endpoint. Azure AD will sign the user in and request their consent for the permissions your app requests. In the authorization code grant flow, after consent is obtained, Azure AD will return an authorization_code to your app that it can redeem at the Microsoft identity platform /token endpoint for an access token.
Authorization request
The following shows an example request to the /authorize endpoint.
With the Microsoft identity platform endpoint, permissions are requested using the scope parameter. In this example, the Microsoft Graph permissions requested are User.Read and Mail.Read, which will allow the app to read the profile and mail of the signed-in user. The offline_access permission is a standard OIDC scope that is requested so that the app can get a refresh token. The app can use the refresh token to get a new access token when the current one expires.
Microsoft Graph exposes two kinds of permissions: application and delegated. For apps that run with a signed-in user, you request delegated permissions in the scope parameter. These permissions delegate the privileges of the signed-in user to your app, allowing it to act as the signed-in user when making calls to Microsoft Graph. For more detailed information about the permissions available through Microsoft Graph, see the Permissions reference.
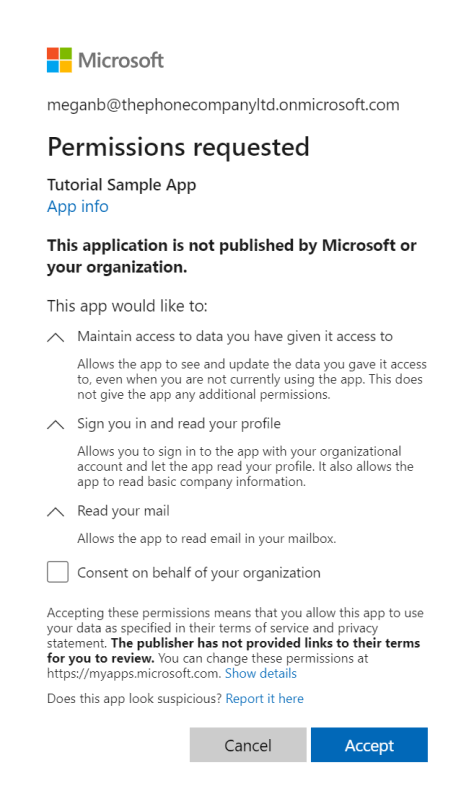
Consent experience
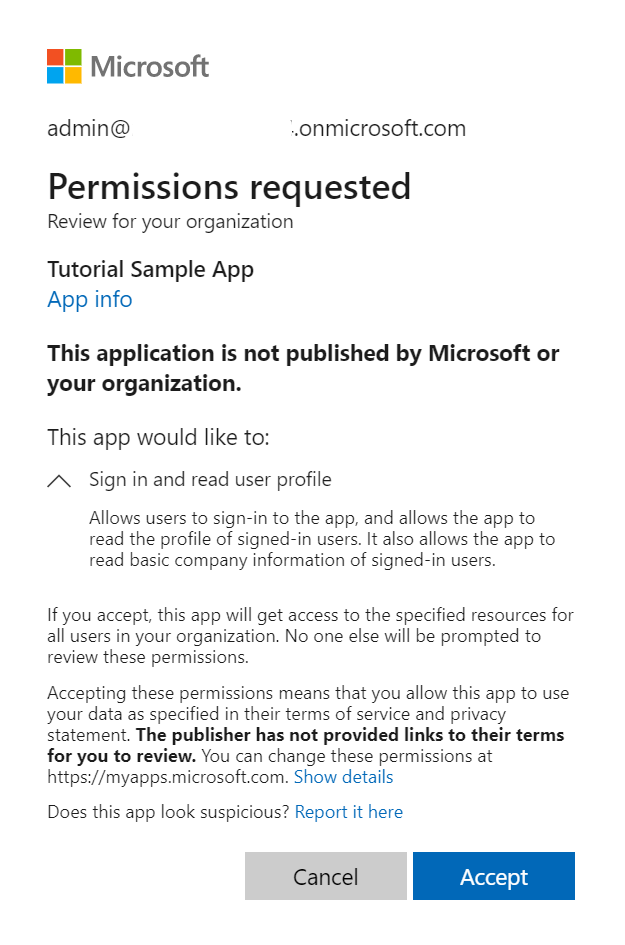
After sending an authorization request, the user will be asked to enter their credentials to authenticate with Microsoft. The Microsoft identity platform v2.0 endpoint will also ensure that the user has consented to the permissions indicated in the scope query parameter. If the user hasn't consented to any of those permissions and if an administrator hasn't previously consented on behalf of all users in the organization, they'll be asked to consent to the required permissions.
The following screenshot is an example of the consent dialog box presented for a Microsoft account user.
Try If you have a Microsoft account or an Azure AD work or school account, you can try this for yourself by clicking the following link. After signing in, your browser should be redirected to https://localhost/myapp/ with a code in the address bar.
Authorization response
| Parameter | Description |
|---|---|
| code | The authorization_code that the app requested. The app can use the authorization code to request an access token for the target resource. Authorization_codes are short lived, typically they expire after about 10 minutes. |
| state | If a state parameter is included in the request, the same value should appear in the response. The app should verify that the state values in the request and response are identical. This check helps to detect Cross-Site Request Forgery (CSRF) attacks against the client. |
| session_state | A unique value that identifies the current user session. This value is a GUID, but should be treated as an opaque value that is passed without examination. |
3. Get a token
Your app uses the authorization code received in the previous step to request an access token by sending a POST request to the /token endpoint.
Token request
Token response
Although the access token is opaque to your app, the response contains a list of the permissions that the access token is good for in the scope parameter.
| Parameter | Description |
|---|---|
| token_type | Indicates the token type value. The only type that Azure AD supports is Bearer. |
| scope | A space separated list of the Microsoft Graph permissions that the access_token is valid for. |
| expires_in | How long the access token is valid (in seconds). |
| access_token | The requested access token. Your app can use this token to call Microsoft Graph. |
| refresh_token | An OAuth 2.0 refresh token. Your app can use this token to acquire additional access tokens after the current access token expires. Refresh tokens are long-lived, and can be used to retain access to resources for extended periods of time. For more detail, refer to the v2.0 token reference. |
4. Use the access token to call Microsoft Graph
After you have an access token, you can use it to call Microsoft Graph by including it in the Authorization header of a request. The following request gets the profile of the signed-in user.
A successful response will look similar to the following (some response headers have been removed).
5. Use the refresh token to get a new access token
Request
Response
A successful token response will look similar to the following.
| Parameter | Description |
|---|---|
| access_token | The requested access token. The app can use this token in calls to Microsoft Graph. |
| token_type | Indicates the token type value. The only type that Azure AD supports is Bearer |
| expires_in | How long the access token is valid (in seconds). |
| scope | The permissions (scopes) that the access_token is valid for. |
| refresh_token | A new OAuth 2.0 refresh token. Replace the old refresh token with this newly acquired refresh token to ensure your refresh tokens remain valid for as long as possible. |
Supported app scenarios and additional resources
You can call Microsoft Graph on behalf of a user from the following types of apps:
For more information about supported app scenarios with the Microsoft identity platform endpoint, see App scenarios and authentication flows.
Note: Calling Microsoft Graph from a standalone web API is not currently supported by the Microsoft identity platform endpoint. For this scenario, you need to use the Azure AD endpoint.
For more information about getting access to Microsoft Graph on behalf of a user from the Microsoft identity platform endpoint:
Endpoint considerations
Microsoft continues to support the Azure AD endpoint. There are several differences between using the Microsoft identity platform endpoint and the Azure AD endpoint. When using the Azure AD endpoint:
For more information about getting access to Microsoft Graph on behalf of a user, see the following resources.
How to get full access to windows 10?
2 Answers 2
There is no such way.
(In particular, because all file access goes through the OS – that's literally the job of an OS – it means the OS is always in position to deny a request it dosen't like.)
If you're just trying to recover your files, then a Linux liveCD will do the job because the default mode for its 'ntfs-3g' driver is to completely ignore NTFS file permissions.
If you're selecting an OS for your future PC, then Linux might also be suitable – not only its permission model is simpler, it is possible to have a blanket bypass using cap_dac_override, which the 'root' account has by default. Various BSDs and Solaris similarly have a 'root' account with unlimited access.
Unfortunately in your case, even though Windows sort of has a bypass mode in the form of SeBackupPrivilege, programs still have to opt in to use it whenever they open a file. Even if granted to the user, it still won't apply to all apps automatically.
But at some point, literally all requests go through the OS. So the only guaranteed way to make sure the OS won't deny some requests is to use an OS that doesn't have such any functionality to begin with.
So maybe also consider Windows 98 or Mac OS Classic or Amiga Workbench – they did not have any file protections at all. (Well, except for the 'read-only' bit.) Yes, they won't run any of your apps either, but they do make for a distraction-free environment.
Get access without a user
Some apps call Microsoft Graph with their own identity and not on behalf of a user. In many cases, these apps are background services or daemons that run on a server without the presence of a signed-in user. An example of such an app might be an email archival service that wakes up and runs overnight. In some cases, apps that have a signed-in user present may also need to call Microsoft Graph under their own identity. For example, an app may need to use functionality that requires more elevated privileges in an organization than the signed-in user may have.
Apps that call Microsoft Graph with their own identity use the OAuth 2.0 client credentials grant flow to get access tokens from Azure AD. This article describes the basic steps to configure a service and use the OAuth client credentials grant flow to get an access token.
Authentication and authorization steps
Follow these basic steps to configure a service and get a token from the Microsoft identity platform endpoint. Your service can use the token to call Microsoft Graph under its own identity.
1. Register your app
To authenticate with the Microsoft identity platform endpoint, you must first register your app at the Azure app registration portal. You can use either a Microsoft account or a work or school account to register your app.
For a service that will call Microsoft Graph under its own identity, you need to register your app for the Web platform and copy the following values:
For steps on how to configure an app using the Azure app registration portal, see Register your app.
With the OAuth 2.0 client credentials grant flow, your app authenticates directly at the Microsoft identity platform /token endpoint using the application ID assigned by Azure AD and the client secret that you create using the portal.
2. Configure permissions for Microsoft Graph
Microsoft Graph exposes application permissions for apps that call Microsoft Graph under their own identity (Microsoft Graph also exposes delegated permissions for apps that call Microsoft Graph on behalf of a user).
You pre-configure the application permissions your app needs when you register your app. Application permissions always require administrator consent. An administrator can consent to these permissions either using the Azure portal when your app is installed in their organization, or you can provide a sign-up experience in your app through which administrators can consent to the permissions you configured. Once administrator consent is recorded by Azure AD, your app can request tokens without having to request consent again. For more detailed information about the permissions available with Microsoft Graph, see the Permissions reference
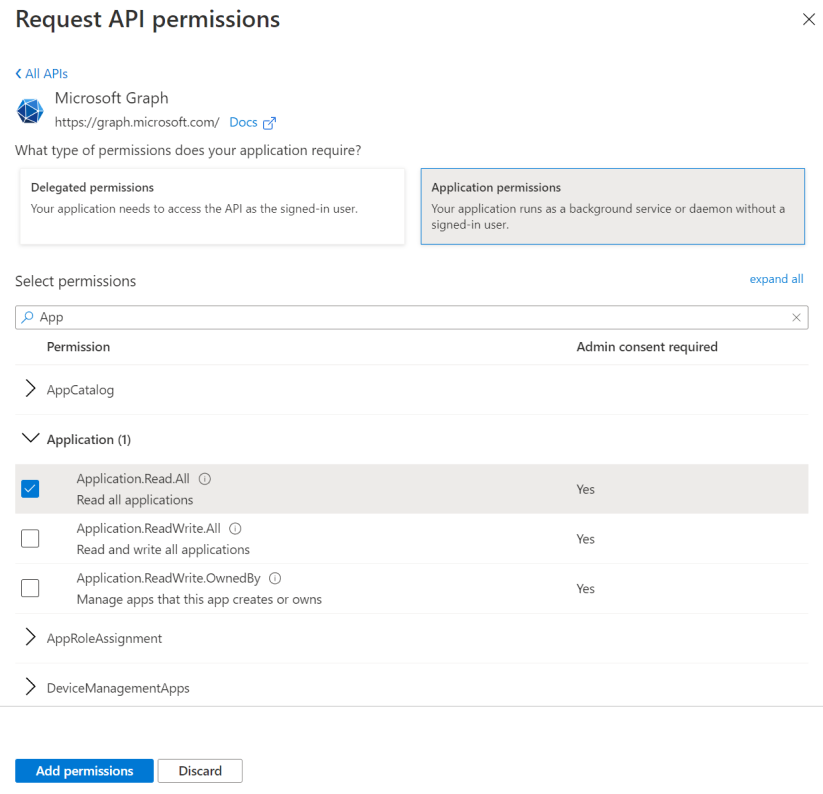
To configure application permissions for your app in the Azure app registrations portal, under an application's API permissions page, choose Add a permission, select Microsoft Graph, and then choose the permissions your app requires under Application permissions.
The following screenshot shows the Select Permissions dialog box for Microsoft Graph application permissions.
Configure the least privileged set of permissions required by your app to improve its security. For more information, see Enhance security with the principle of least privilege.
3. Get administrator consent
You can rely on an administrator to grant the permissions your app needs at the Azure portal; however, often, a better option is to provide a sign-up experience for administrators by using the Microsoft identity platform /adminconsent endpoint.
When you change the configured permissions, you must also repeat the admin consent process. Changes made in the app registration portal will not be reflected until consent has been reapplied by the tenant's administrator.
Request
Administrator consent experience
With requests to the /adminconsent endpoint, Azure AD enforces that only a tenant administrator can sign in to complete the request. The administrator will be asked to approve all the application permissions that you've requested for your app in the app registration portal.
The following screenshot is an example of the consent dialog that Azure AD presents to the administrator:
Response
If the administrator approves the permissions for your application, the successful response looks like this:
| Parameter | Description |
|---|---|
| tenant | The directory tenant that granted your application the permissions that it requested, in GUID format. |
| state | A value that is included in the request that also is returned in the token response. It can be a string of any content that you want. The state is used to encode information about the user's state in the app before the authentication request occurred, such as the page or view they were on. |
| admin_consent | Set to true. |
Try: You can try this for yourself by pasting the following request in a browser. If you sign in as a global administrator for an Azure AD tenant, you will be presented with the administrator consent dialog box for the app. (This will be a different app than that in the consent dialog box screenshot shown earlier.)
4. Get an access token
In the OAuth 2.0 client credentials grant flow, you use the application ID and client secret values that you saved when you registered your app to request an access token directly from the Microsoft identity platform /token endpoint.
You specify the pre-configured permissions by passing https://graph.microsoft.com/.default as the value for the scope parameter in the token request. See the scope parameter description in the token request below for details.
Token request
You send a POST request to the /token identity platform endpoint to acquire an access token:
Token response
A successful response looks like this:
5. Use the access token to call Microsoft Graph
After you have an access token, you can use it to call Microsoft Graph by including it in the Authorization header of a request. The following request gets the profile of a specific user. Your app must have the User.Read.All permission to call this API.
A successful response will look like this (some response headers have been removed):
Supported app scenarios and resources
Apps that call Microsoft Graph under their own identity fall into one of two categories:
Apps that call Microsoft Graph with their own identity use the OAuth 2.0 client credentials grant to authenticate with Azure AD and get a token. For the Microsoft identity platform endpoint, you can explore this scenario further with the following resources:
Endpoint considerations
Microsoft continues to support the Azure AD endpoint. There are several differences between using the Microsoft identity platform endpoint and the Azure AD endpoint. When using the Azure AD endpoint:
You can explore this scenario further with the following resources: