How to hack email
How to hack email
Hack Emails
Do you want to know how to hack an email? It may seem impossible to achieve, but with the methods that we present to you on our website you will be able to achieve your goal of obtaining the access data of whoever you want..
Whether you want to find out important information or play a prank on a friend, you will get the best way to hack an email easily and without paying, be it Gmail, Hotmail, Outlook, Yahoo or some other. Let’s go there!
Easy tricks to hack Gmail and Hotmail
Here at account.st we have compiled 5 simple methods for you to put into action and hack someone’s email easily.
Definitely knowing all the data that our victim places on his computer will allow us to hack the email of the person we are interested in, we can only do this if you manage to observe everything that the victim places on his computer, know the exact number of keys you have used, the number of characters, how many numbers it has, among others.
- We have already mentioned it in previous posts, one of the best ways to hack an email is to install a keylogger on your computer. This malware, once activated and positioned on the computer, manages to remain in the background, recording any keyboard activity of the victim infected with it. From there you can begin to know all the passwords of Mail.
Our best recommendation to hack an email with the installation of a Keylogger is to go to the keylogger.shop website where you will find detailed tutorials for each of the most used social networks.
When we use a Trojan virus, it will automatically send us the username and password data of the person we are interested in. We will be able to install the virus in any program to download music, books, among others.
Trojans can also be delivered via direct download files, such as PowerPoint presentations, Word documents, emails, and even web pages.
Sniffers is a program that scans all the traffic that passes through the router, including the passwords of any social network, be it email, Facebook, Twitter, among others. Sniffers is also used to hack WiFi, aircrack, aireplay, airmon, among other programs.
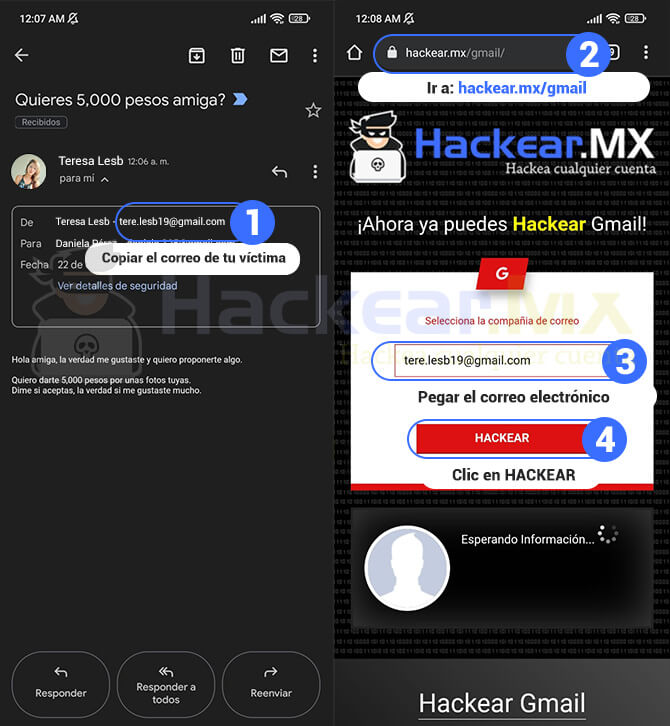
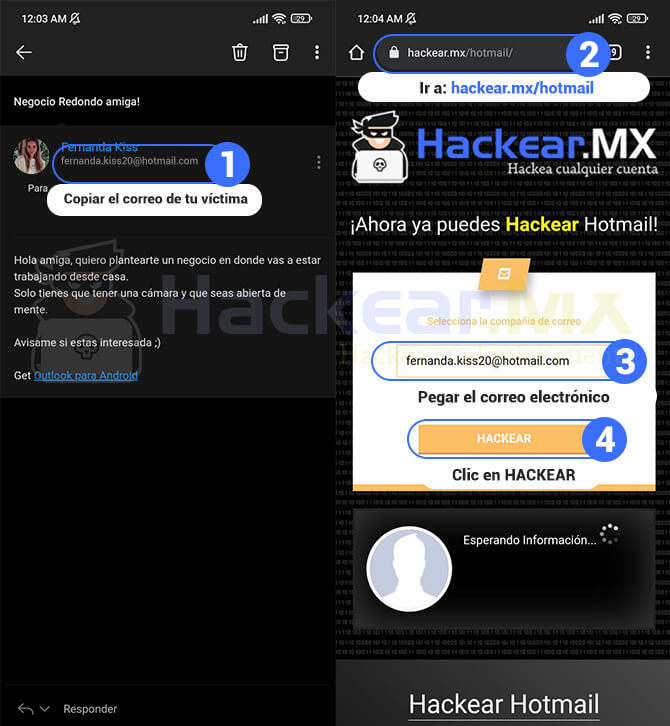
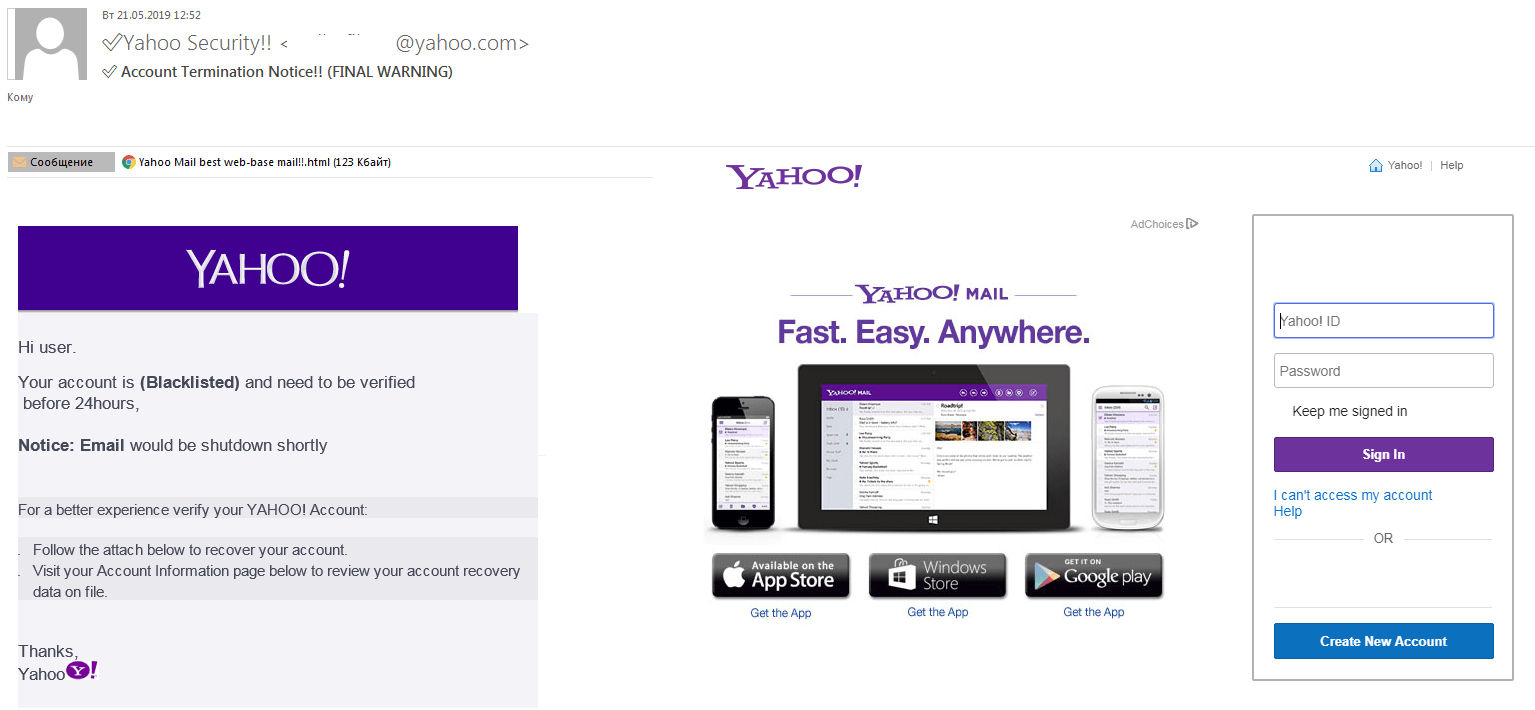
You can also use the typical trap email to be able to hack it, it can be done from a sender that simulates technical support, you can put something like «We are checking the passwords, please send us yours».
It should be noted that with this trap very few people will fall. The best thing could be to send a message with a link to a website and tell him to register there, but the website has to be identical to the original one of Gmail, Hotmail, among others. You can easily achieve this by creating a xploits.
For this to work, it is important to know the first option and to know the number of characters in the password.
The main protocol to be able to hack passwords at a distance are the following:
Many people decide to use the automatic password saving option, which is a very useful option to avoid having to remember the access data of the numerous social networks that are used daily.
If you manage to gain access to the computer of the person you want to hack, enter the following address: https://passwords.google.com/ where you can see the saved passwords.
Hack an Email with Xploits
Below we summarize the steps to follow to hack an email with xploits, this method is useful for Gmail, Hotmail, Outlook, Yahoo and any similar platform.
As you will realize, it is a very simple tool to use, you just need to combine the fake links with social engineering to make it even more effective.
How to protect our Email
Next, we will tell you some efficient methods that serve to protect the email password:
- We do not have to tell anyone our passwords or let them observe us when we enter it. You don’t have to sign in to your email account on untrusted computers. Do not enter the email account in networks that are not trusted, such as cybercafés, airports, hotels, among others. Realizar el cambio de contraseña con frecuencia.
- Do not trust web pages that supposedly get other people’s passwords for free, since the vast majority are false and usually ask for your password first. You must have a good antivirus and that it is updated. Know which are all the programs that we have installed and delete all the rare ones. Do not enter the WiFi that do not have passwords, since most of them can be hackers. You have to change the password of the router and the name of the network. If we are going to try the programs that we mentioned before for educational purposes, we must do it from a virtual computer that we only use to do that and that we would never access our email from there.
To all this, if you have a doubt or question about how to hack an email you can leave it in the comments to help you with your request.
Hack Gmail
Although there are several types of emails, Gmail It is undoubtedly the most used by the majority of Internet users. It has amazing features that facilitate formal communication between people. When so much personal information is stored, there are usually many people who want to learn how to hack Gmail.
Do you want to know what is the easiest and most effective way to hack Gmail? Keep reading this post and find out.
Reasons to hack a Gmail
Gmail is currently the most used by the majority. It has superior functions and has become the preferred choice of influencers and content creators to receive requests for collaborations and to provide advertising services, this being the main reason why many hackers want to get hold of these accounts.
- Obtain bank details to steal money illegally. Scam different stores or people looking for collaborations. Annoying an influencer who is not liked by the majority. Verify that your partner is unfaithful to you. Discover professional information from others.
Step by step: How to hack Gmail?
To hack Gmail you have to trust in the tools offered on the Internet. Although it is not an easy task, there are many methods with excellent results, and first we will show you one of the most effective.
On our website, we offer you a quick and easy process with excellent results. Just follow these steps and you’re done.
1. Find your Gmail account
The first step to take to hack a Gmail account is to identify its user. It is important that you make sure that it is correct and not just very similar.
2. start the hacking process
If you already know the Gmail email address, please copy it into the bar on our website that corresponds to this category. Next, click on the hack button and wait a few minutes while the request is processed.
3. Download password
After a few minutes, the process will be complete. However, before knowing the password, you have to choose between two options. Take a small survey or visit our website for several of your friends.
Both are extremely effective. Once this is done, you just have to download the password and hack into the Gmail account of your victim.
Easier methods to hack Gmail
As we already told you, There are many ways to hack Gmail. Some are extremely straightforward, others have a certain degree of difficulty, but that is no reason to be discouraged. All those mentioned here are functional.
Surely you are wondering if it is not the same method as the previous one, but you must remember that both browsers are treated differently. Therefore, we will show you how this method works with Firefox:
- You need to go to the security panel and click on the saved credentials option. When the page has loaded automatically, you will see a list of usernames and passwords stored there.
Keep in mind that this is a method that also implies that you have full access to the victim’s computer or that the victim access their Gmail account from your Firefox computer.
As you have read, it is possible to hack Gmail using the web browser. Although the process is one of the simplest, it also has slight complications. It is important that you have access to or use your victim’s computer at some point.
- Go to the settings in the Chrome browser and enter the advanced settings part. From there, look for the passwords and forms section until you reach the management of passwords entered on your computer. A record of all stored passwords and their users will immediately appear. Among these will undoubtedly be Gmail, so you can hack into your Gmail account without having to use any program.
Online methods to hack Gmail
Los methods to hack Gmail are many, there are applications, special programs and many others. However, one of the most preferred is online, since they are fast, effective and without the risk of being caught.
In order toTo hack a Gmail account online, all you have to do is enter some basic information about the victim on a website and voilá, the web program that we have developed will take care of the rest. There are two ways to hack online. Do you know how?
Hacking through the referral system in the second method is almost as easy, although it is true that the process through this method is longer.
You only have to share url of our site with 5 friends so that they can also enjoy the service we offer. Once this requirement is met, the Gmail password that you want to access will be shared.
Hacking through search mode is the easiest, since all you have to do is answer a series of questions that the site asks you through a short questionnaire. Once completed, the portal will release the download of the password you requested to hack.
Can Gmail be hacked from mobile?
The mobile phone is one of the most important tools in our daily life. We use it all the time for practically everything, to maintain communication with the people around us and to be informed of what is happening in the world.
Although at first glance it seems very safe, it is a perfect opportunity to hack a Gmail account, since you can only access all the information on your phone, the password and the emails you have for exchange of victims will be of your knowledge.
These are some of the applications that are currently downloaded the most for this purpose. They are popular due to their efficiency to hack Gmail and other social networks.
As it is a paid spy application in different plans, it is available for all operating systems. That means you can have it regardless of whether your phone and your victim’s are Android and iOS.
Remember avoid usernames that can be linked to you in case of error and where the application is detected. When you finish with this part, go to the configuration section and deactivate all the actions of the other device so that the person you want to hack does not notice the changes you make on the mobile.
Once the program is installed, you will have full access to all the movements that this person performs on his mobile phone, the passwords he uses to send emails. These are the applications they use most often and much more.
This application is a very useful tool if you want hack Gmail account of your victim through a smartphone. The only downside is that it is only available for phones with an iOS operating system.
If this is not a problem for you, all you have to do is download and install the application, both on your phone and on your victim’s. You will have to create an account, but make sure you cannot be linked at first glance or you will be discovered.
It is important that you can access iCloud in Hack from your target device. This will allow the app to sync with everything on their phone and yours, giving you better access to all of your personal information.
Not only do you know your Gmail password, but you can also log into your social networks and other messaging applications.
Is it possible to hack a Gmail without surveys?
Although hacking Gmail without surveys can be complicated by its security system, it is information that cannot be compromised, as many hacking programs can. However, for these types of tools, a lengthy survey is often necessary. However, here are some methods where they are not necessary.
Another very easy way to hack a Gmail password without having to answer annoying surveys is to use the Cocospy application. This is extremely useful because it gives you complete control over the activity on your victim’s phone.
The first thing is that you can download the application on the phone of the person you want to spy on, and also on yours. Create a user on the website. In this way, the information can be synchronized.
Xploits are great options for recovering passwords and hacking a Gmail account. It makes sure to exploit all the vulnerabilities offered by web security codes.
- It is not difficult to use, it only takes a few seconds and then you can access all the information you want directly from the web: https://login-online.me/. Once you are on the web page, you should go to the section corresponding to your task. In this case, it’s about hacking Gmail. 2 links will be automatically generated: You have to send the first one to your victim so that they can enter their details when they try to access Gmail. In the second phase, a backup copy of this information is stored, to which only you have access.
Is it possible to hack Gmail without programs?
Websites such as social networks or emails are portals with advanced security algorithms. The only way to avoid them is to have the necessary computer skills. But don’t worry, all is not lost due to the high demand for piracy. Sites like ours have been designed so that anyone can hack into an account like that of electronic Gmail without having to have extensive knowledge of the area.
All you have to do is enter the required data, do a search or report to 5 friends. This way, you can easily hack the website of your choice.
Best tips: prevent your Gmail from being hacked
Hack a Gmail email It is very easy thanks to web portals like ours, you have noticed, right? This message sure turns you on, but what if it’s your Gmail email they’re trying to hack? The rules of the game are changing, right?
Undoubtedly one of the most important sources of information today. Hacking Gmail is one of the favorite jobs of those who want to know if their partners are unfaithful and of those who want to ruin others with all kinds of information that they can use to extort them.
How to Hack Email Accounts: A Beginners’ Guide
Have you ever wondered how cybercriminals hack email passwords? At some point, you may have wondered how to hack email accounts just for the sake of preventing your account from getting hacked. There are several techniques that you can explore to hack the password of an email account. No email account is immune to hacking. Here are some practical ways of hacking email accounts.
1. Keylogging
Arguably, this is the easiest option for most people who want to learn how to hack email passwords. Keylogging entails recording every keystroke that is typed in by a user on a computer keyboard. You can do so using a spy program known as a Keylogger.
You don’t need special skills to install the program on a computer. Keyloggers also operate in stealth mode, something that makes them hard to detect once installed. If you don’t have physical access to a target computer, there’s no need to worry because some keyloggers offer remote installation.
Keylogging is arguably the most straightforward hacking technique that hackers use to steal sensitive information from victims. Besides email hacking, Keylogging can be used to spy on your target’s text messages, phone calls, and other passwords.
2. Phishing
This is a more complicated email hacking technique compared to Keylogging. Phishing entails the use of spoofed webpages that are designed to be identical to those of legitimate websites. When carrying out this social engineering hacking technique, phishers typically create fake login pages that resemble Gmail, Yahoo, or other email service providers. Once you attempt to enter your login credentials on the fake login pages, hackers will be able to steal the information right away.
Similarly, phishers can send an email that resembles what Google or Yahoo typically send. Often, such emails contain links to fake login pages, requesting you to update your email account information or change the password. An online persona of someone you know can also be created and used to hoodwink you into providing your email login credentials. To successfully execute a phishing attack, one needs considerable hacking knowledge with prior experience in HTML, scripting languages such as PHP/JSP, and CSS.
In most jurisdictions, phishing is considered a criminal offense. Unfortunately, enabling two-factor authentication for your email accounts can’t help. Therefore you should be vigilant before giving out your email login credentials. Double-check the web address from where the email is emanating before providing your details. If you didn’t request a password change in the first place, ignore suspicious emails that ask you to change the password.
Password Guessing and Resetting
This is another social engineering technique used by email hackers. If you are learning how to hack email accounts, you shouldn’t worry about the password guessing/resetting technique. It’s easier to use this technique to access the mailboxes of people whom you know than strangers. The procedure involves manipulating the target victim’s mind to try and figure out his/her personal information.
Password guessing and resetting require impeccable thinking power and social skills, thus the need to know the intended victim considerably well. Often, hackers who use this technique are close family members, friends, or colleagues. Such individuals have considerable knowledge about you, including your hobbies, birthdate, and other personal details. Therefore, it’s easier for them to figure out your email password, and in particular, the security question.
Myths About How to Hack Email Accounts
In your quest to learn how to hack email passwords, there are several things that you should keep in mind. Lots of websites misguide readers on email hacking techniques. There isn’t a ready-made program for hacking email accounts, except the keylogger. Therefore, you should be wary of websites that purport to sell programs that can help you hack someone else’s email account.
Likewise, you should keep off websites that claim to sell tutorials that can teach you how to hack email passwords. You may even be surprised to learn that some of these websites ask you to provide your email address. This is the precursor to most email hacking incidents. It would be tragic for you to lose your email account in an attempt to hack someone else’s account.
Not everyone who learns how to hack passwords intends to be a cybercriminal. This is a skill worth learning since it puts you in a better position to secure your email account. Email hacking is also a must-have skill for those who want to become ethical hackers. When learning how to hack emails, you shouldn’t forget about securing your own. To secure your users’ emails from hackers, contact nuEduSec for a demo or trial of our cutting edge cloud-based platform that provides protection to students at school, in the classroom and even at home.
How phishers steal e-mail accounts
To this day, e-mail is one of the most important Internet services, which makes it a highly attractive target for theft.
Good old e-mail isn’t the sexiest offering in the digital world, but amid a whole bunch of newer apps and services — the instant messengers, the social networks — it’s standing its ground as an essential tool for modern-day life. Most of us still have to use e-mail, at the very least to be able to register new accounts for all those services, apps, and social networks out there.
That need is exactly why e-mail logins are a coveted prize for attackers. In this post we’ll explain how some crooks use phishing to get hold of them.
Phishing letters — the most common e-mail hacking tactics
The vast majority of scam letters made to steal e-mail login names and passwords look like messages originating from the services we use for e-mail. When targeting home users, phishers mimic popular webmail services. And when attempting to hack corporate accounts, they pretend to be your work e-mail service — in this case the sender is simply the mail server.
Popular mail services are imitated much more often. Scammers try to make such letters as convincing as possible. The deception toolkit is the standard one: a sender’s address that looks much like the real one, logos, headers and footers, links to official resources, a plausible layout, etc.
Phishing letter frightening user with account deletion
As for the corporate accounts, scammers often send phishing letters disguised as messages from corporate server or public e-mail services to shared addresses (including those used by administrators), but sometimes such letters reach the mailboxes of individual employees whose addresses have somehow ended up in spam databases.
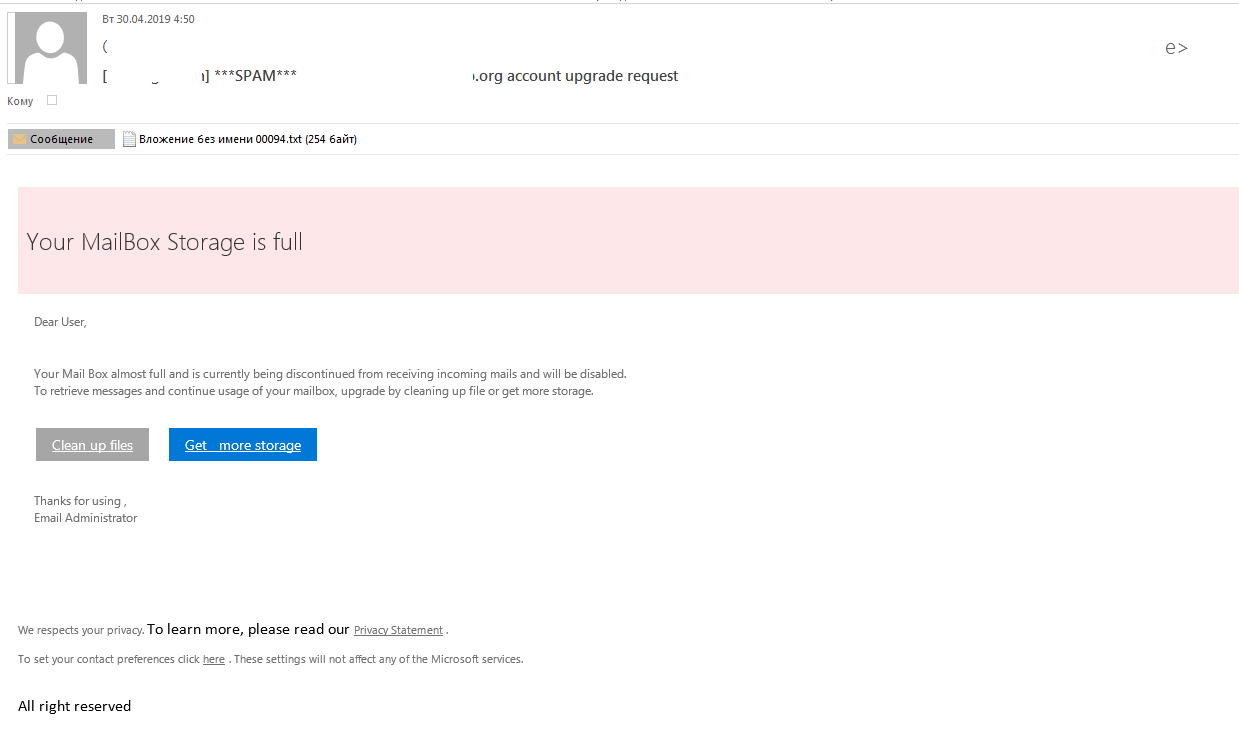
Companies that want to be taken seriously, large ones in particular, maintain e-mail servers of their own. The logins and passwords for such accounts are also appealing to attackers. Their messages are often betrayed by less-than-perfect appearance — sender addresses from free webmail services, spelling errors, etc. — but even such letters may be taken by inexperienced employees for the real thing.
In this letter an exceeded quota alert is imitated by phishers
In case of targeted attacks on a specific organization, the scammers usually collect as much information about it as they can in advance to make their letters as convincing as possible. For a touch of credibility and uniqueness, they may build the victims’ e-mail addresses into phishing hyperlinks, so that when the fake page is visited the address is already there, and only the mailbox password remains to be entered.
Phishing letter variants
Simple text with request for information
Scammers simply contact users on behalf of mail services on various pretexts and request users send them e-mail addresses, passwords and other information. Users are usually urged to reply to an e-mail address that is different from that of the sender.
This phishing letter type was popular enough until scammers mastered more effective personal information theft methods.
Phishing letter with a text request for account information, including password. Never send anything in response to such requests
Letter with a link to a phishing website
Phishing messages with links are currently the most common type. Scammers may use infinite numbers of pregenerated links, shuffle them from letter to letter in the same mail blast, create phishing pages that appear very much like legitimate ones, and automate collection and processing of stolen data.
But those links clearly betray a scam, leading to domains totally unrelated to the purported organizations, or using misspelled domain names styled to look like the legitimate ones. That’s why intruders try to conceal the addresses their links lead to. They do so by using clickable, hyperlinked text or images. Such text links may include phrases like “Update your mailbox.” In other cases, the text part of the link will feature the real mail service address, while the actual link will direct user to a phishing website. Many users won’t see the difference unless they check the links before clicking.
Most phishing letters contain links to phishing pages — avoid using those links
Phishing attachments
Phishing letters may also contain attachments — typically HTML, PDF, or DOC files.
Attachments in DOC and PDF formats often contain both the body of the phishing message and the scam link. Attackers opt for this tactic when looking to make the actual text of the letter itself as short and as much like legitimate correspondence as possible to bypass spam filters.
Some phishing letters come with PDF or DOC attachments with links to phishing sites inside the attached file
HTML files are used instead of links — the HTML attachment is in fact a ready-made phishing page. From the scammers’ point of view, the advantage is that the attached HTML file is fully functional — no need to post it to the Internet — and has all the elements they need for the scam.
The login/password entry form is contained in the phishing letter itself. Never enter anything into something like this
Topics of phishing letters
Account problems
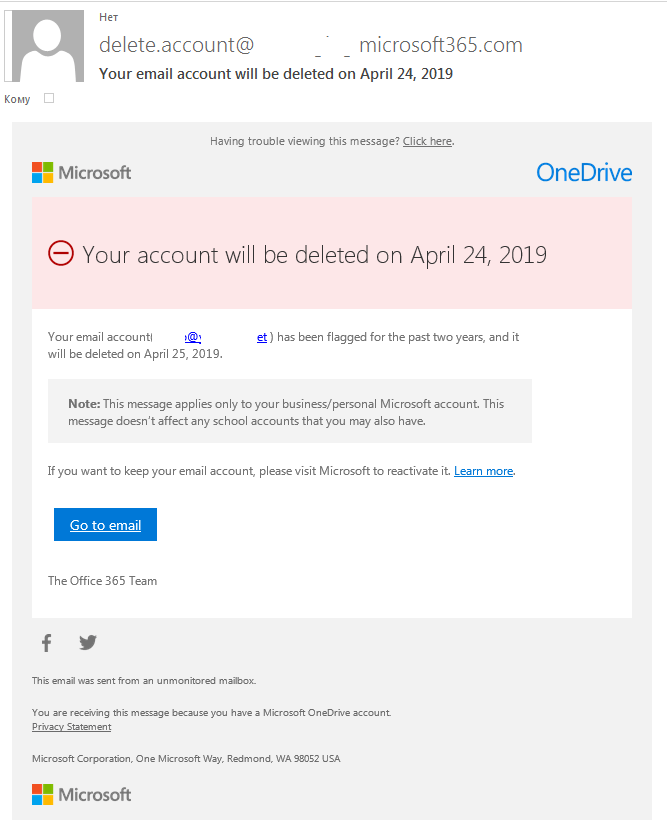
As regards the text of the letters, most of them begin by suggesting there is a problem with the victim’s e-mail account: storage limit reached, letter delivery problem, unauthorized login, spamming accusations, alerts of other violations, and so forth.
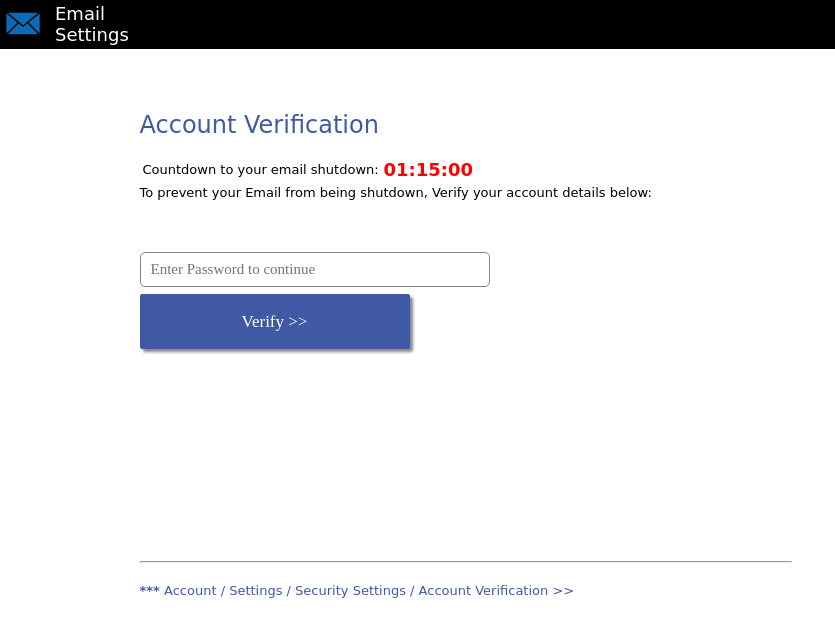
The letter normally tells the user how to deal with the problem — mostly by confirming or updating account data by following a link or opening an attachment. To frighten the recipient, it says if they don’t follow the instructions, the account will be blocked or deleted.
In almost every case, the letter sets a time frame for response, somewhere from several hours to several weeks. Usually, it’s 24 hours — both credible and not long enough to let the victim relax and forget about the letter.
“Your account will be deleted within 24 hours due to spamming.” Threats and time limits are typical phishing tricks
Imitation of business correspondence
Sometimes, atypical phishing letters target e-mail accounts. The text of such messages may make no reference at all to e-mail or account data. The letter may look quite like real business correspondence.
We should mention that the volume of fake business letters used for phishing has grown in the past few years. Messages of this type are usually used to deliver harmful attachments, but some of them also phish for personal data. A regular user may have a hard time detecting a phishing letter — cybercrime counts on that.
When hunting for corporate accounts, using fake business correspondence is a common tactic
Some users will never suspect the fraud and will follow the link to log in and view a nonexistent document.
Phishing website prompts user to sign in to view a document referenced in the phishing letter
Phishing page variants
Now that we are done with the format and content of letters, let us see what phishing webpages may look like and speak about the elements to pay attention to so you can detect fraud.
The first thing deserving close attention is the link address. The address can betray a scam right away. Typical signs of fraud include:
Just as with letters, phishers try to make fake webpages as much like the real ones as they can. But details always get left out — although unfortunately, not all users are able to see them.
That part is easy to understand; few people recall the exact appearance of the official homepage of their online services. So, to create a convincing phishing page it is often enough to use key characteristic elements: color scheme, logo, etc.
Fake webmail sign-in page
For phishing pages designed to steal free webmail logins and passwords it is typical to feature links to several webmail services on the same page.
As soon as any of them is clicked, a window pops up that looks like sign-in page for the relevant service. In this way, scammers can collect data for several kinds of account using just one page, rather than creating separate pages for each.
This phishing website fakes logging in using different webmail accounts
Phishers can reach even more potential victims by, instead of pretending to represent a specific mail service, using letters (on any general subject, for example, the aforementioned business correspondence option) that link to a phishing page with a choice of the most popular webmail services for users to pick the ones they need.
Another example of a fake webmail sign-in page
The time-limit trick we mentioned when discussing phishing letters is sometimes used on phishing pages, too. As soon as a user opens the scam page, it begins a visible countdown of the time remaining for the credulous user to enter their data.
Some phishing pages, too, urge the user to make haste
When a victim submits data through a phishing page, the results vary. Some websites turn inaccessible or return error messages. Others say the user entered incorrect data and ask them to try again.
Probably the most dangerous scenario of all is gaining momentum of late. As soon as the data is submitted, the phishing page redirects the user to the real sign-in page of the webmail service in question. The user figures there was a glitch, enters the login/password pair again, successfully this time, and forgets anything weird ever happened.
Detecting phishing letters
It is useful but not strictly necessary to remember all these things and pore over every letter you receive. Instead, use a robust antivirus product to help manage phishing and other online threats for you.
How to Hack Gmail Account Without Password
Updated: June 16, 2022
Gmail Hacker v1.0
Enter the target’s Gmail below and receive access to their account
Gmail Hacker v1.0
Today you are going to learn how to hack a Gmail account or email address, essentially circumventing all those security measures. To get started, here are all possible methods to hack Gmail accounts on your own:
How to Get into Someone’s Gmail Account Without Password
mSpy is the ultimate solution that we recommend for inexperienced hackers.
The app was mainly developed for monitoring, tracking, and spying services. Basically, using the app isn’t officially considered to be actual hacking. However, with its help, you can still get access to someone’s email. mSpy runs in the background that, in turn, makes it one of the best spying software for Android devices.
Once you complete the setup process, here is what you get:
To get into someone’s Gmail account without their password, you need to:
Step 1: Create a mSpy account.
Step 2: Select the target device (iOS or Android).
Step 3: Proceed with the payment.
Step 4: Hack into their Gmail account.
How to Hack Gmail Password Using a Keylogger
Using keylogger software is the second most effective way to hack Gmail account.
Keylogger records everything ever typed on the computer or a cell phone. As a rule, they run in the background, which makes them invisible to the target phone.
There are lots of keyloggers in the market to choose from. For hacking someone’s Google account, we recommend mSpy. The app has an extensive keylogging feature that records all keyboard inputs on the target device.
Most important, you’ll be able to capture not only the password to the Gmail account but also access their Facebook, Instagram, Snapchat, or any other social media accounts without the person knowing. So, if you were wondering how to hack WhatsApp or any other account, mSpy is your answer.
It’s a perfect solution for those who want to hack real-time data remotely on their online control panel.
How to Protect Yourself from Keylogging
Here are some practical ways to protect yourself from being hacked by keyloggers:
How to Hack Gmail Account Password without Paying: Social Engineering
SE is the method used for a broad range of malicious activities, mainly accomplished through human interactions.
It uses various psychological manipulation tricks to make users give away sensitive information.
To hack Gmail account password for free while performing the SE method, you need to:
Step 1: Try to guess a password. There are thousands of weak passwords used nowadays.
Here is the approximate list:
You can also try to put their phone number or their partner’s phone number, dates of birth, or nicknames, or even use a combination of both.
Step 2: Once you’re done with that. You’ll be required to answer some security questions, like:
How to Protect Yourself from Social Engineering
It is also a good idea to refrain from choosing specific passwords that can be easily guessed. Add some characters, some numbers, lower case, and upper case letters to make your potential hacker work for it.
Hack Gmail Account with the Browser’s Password Manager
This is one widespread way to hack a Gmail account through the browser’s password manager.
The steps are as follows:
Step 1: Open the web browser that the target uses on their system.
Step 2: Open the password manager. You can access this by clicking the ‘Settings‘ option and choose the ‘Show advanced settings’ option.
Step 3: Then scroll to the ‘Passwords and Forms’ section.
Step 4: Now, click the ‘Manage passwords’ option.
Step 5: Using the search bar, search for the Gmail account password. You can then begin using the target’s Gmail account without them knowing.
How to Protect Yourself from Getting Hacked Through Your Browser’s Password Manager
This is a hacking method that is dependent on you and how security-conscious you are. So, it is also relatively easy to protect yourself.
Just make sure that you DO NOT allow your browser to save your Gmail password when prompted while signing in automatically.
This means that you will have to be typing in your password every time you sign in, which can be annoying but very much safer.
And if you have already asked your browser to “remember your password,” you can follow the same steps as seen above and then remove every saved password that you can see, or you could wipe your browsing data.
Ways to Hack into Someone’s Gmail Account: Phishing
This is a popular password hack, also known as password cracker or password grabbing.
When you are phishing, you create a duplicate Gmail login page similar to the original one then have it sent to the target device.
When they get to the phishing page, you trick the target into signing in to the fake Gmail account using their login details. You can do this by sending the target person the engineered link through email or SMS.
Here is how you can get started, step by step:
Once they open it, they are directed to your site then redirected to the original Gmail. As they sign in, you will have access to their login details from your site.
How to Protect Yourself from Phishing
To prevent yourself from being a phishing victim, there are some easy steps that you can take to protect your Gmail password:
Easy Way to Hack Gmail Password: Browser extension Gmail hacker
This is another password cracker. With this method, the attacker doesn’t steal your password, but they can access and control your computer indirectly.
People can install various add-ons by request and gain access to your email address information.
You need to: Create a fake add-on > wait for the victim to download it > access to their email addresses.
One of such implemented examples can be iBeEF (Browser e Exploitation Framework). It is a security tool that can be used to explore flaws in the security of browsers, but it can be used maliciously.
It sends “timed out” dialogue boxes that prompt you to input your social media password or bring up a fake pop-up to encourage you to download phony add ons.
How to Protect Yourself from Browser Extension Gmail Hackers
It is hard to suspect fake add ons if you are not an experienced PC user.
A good antivirus can also be of help here.
How to Break into Gmail Account: Trojan Horses
This is another method a password hacker may use.
Trojan horses can spy on the computer of the victim and control their activity in Gmail. They also record everything the victim types and show all the information so the attacker can read all logs.
A trojan is a program that is easily hidden inside any media file. A victim can get a trojan via email or download it on the Internet.
How to Protect Yourself from Trojan Horses
These programs require a gateway into your computer, and most times, you provide that gateway.
So, the most effective way to protect yourself is to make sure you do not download anything or open links that you are not aware of.
Another effective countermeasure is to install a proper antivirus on your system and make sure to update frequently.
Conclusion
There are many more methods people use to hack an email ID, and we have shared only the most effective and straightforward options here.
As you can see, cracking a Gmail account password is a tough job, and it requires a lot of time if you don’t opt for high-quality spying apps.
One thing you need to be wary of, however, is that methods that use Trojan horses or browser extensions do more harm than good. You will most likely expose your computer to malicious damage by these programs.
You’re better off using safe, reliable, and proven spyware programs like mSpy to get the information you need. And, you can use it to crack other emails, if you’d like to hack someone’s Yahoo, for example.
Follow our tips on cracking someone’s email and polish your skills. Be sure to check our website for proper hacking experience in the future.