How to hack to website
How to hack to website
How to Hack a Website: Hacking Websites Online Example
Updated June 25, 2022
More people have access to the internet than ever before. This has prompted many organizations to develop web-based applications that users can use online to interact with the organization. Poorly written code for web applications can be exploited to gain unauthorized access to sensitive data and web servers.
In this tutorial you will learn how to hack websites, and we will introduce you to web application hacking techniques and the counter measures you can put in place to protect against such attacks.
Topics covered in this tutorial
What is a web application? What are Web Threats?
A web application (aka website) is an application based on the client-server model. The server provides the database access and the business logic. It is hosted on a web server. The client application runs on the client web browser. Web applications are usually written in languages such as Java, C#, and VB.Net, PHP, ColdFusion Markup Language, etc. the database engines used in web applications include MySQL, MS SQL Server, PostgreSQL, SQLite, etc.
Most web applications are hosted on public servers accessible via the Internet. This makes them vulnerable to attacks due to easy accessibility. The following are common web application threats.
How to protect your Website against hacks?
An organization can adopt the following policy to protect itself against web server attacks.
Website hacking tricks: Hack a Website online
In this website hacking practical scenario, we are going to hijack the user session of the web application located at www.techpanda.org. We will use cross site scripting to read the cookie session id then use it to impersonate a legitimate user session.
The assumption made is that the attacker has access to the web application and he would like to hijack the sessions of other users that use the same application. The goal of this attack could be to gain admin access to the web application assuming the attacker’s access account is a limited one.
Getting started
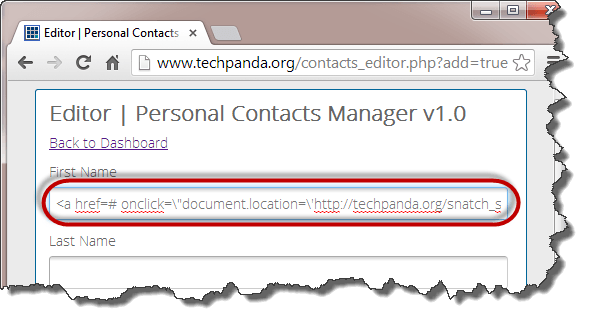
HERE,
The above code uses JavaScript. It adds a hyperlink with an onclick event. When the unsuspecting user clicks the link, the event retrieves the PHP cookie session ID and sends it to the snatch_sess_id.php page together with the session id in the URL
Note: the script could be sending the value to some remote server where the PHPSESSID is stored then the user redirected back to the website as if nothing happened.
Note: the value you get may be different from the one in this webpage hacking tutorial, but the concept is the same
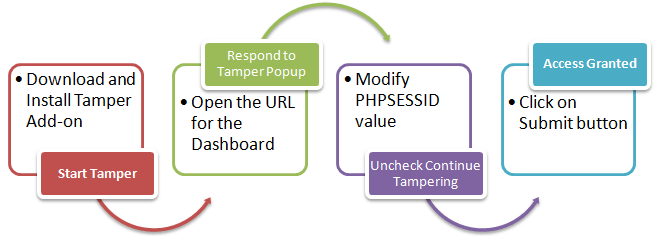
Session Impersonation using Firefox and Tamper Data add-on
The flowchart below shows the steps that you must take to complete this exercise.
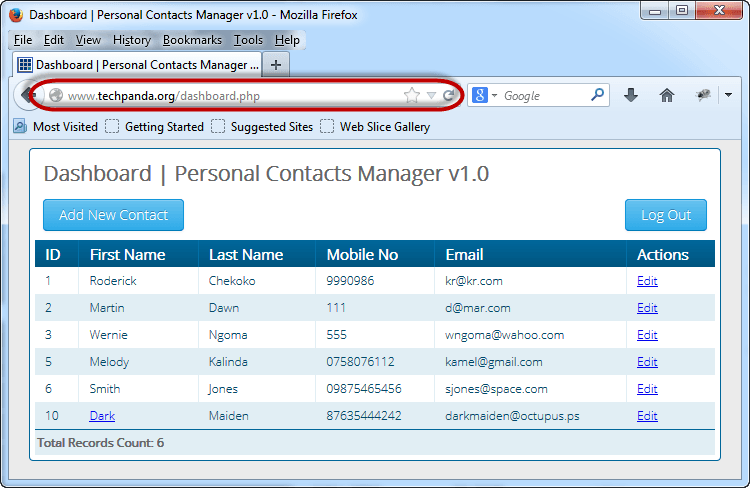
Note: we did not login, we impersonated a login session using the PHPSESSID value we retrieved using cross site scripting
How to hack a Website or websites database
For more basic knowledge about SQL injection visit:
The above tutorial consists of both types of SQL injection i.e. Manual and automatic through softwares. I will explain SQL injection in more detail with practical example in Next class.
Cross site scripting (XSS) occurs when a user inputs malicious data into a website, which causes the application to do something it wasn’t intended to do. XSS attacks are very popular and some of the biggest websites have been affected by them including the FBI, CNN, Ebay, Apple, Microsft, and AOL.
Some website features commonly vulnerable to XSS attacks are:
• Search Engines
• Login Forms
• Comment Fields
Cross-site scripting holes are web application vulnerabilities that allow attackers to bypass client-side security mechanisms normally imposed on web content by modern browsers. By finding ways of injecting malicious scripts into web pages, an attacker can gain elevated access privileges to sensitive page content, session cookies, and a variety of other information maintained by the browser on behalf of the user. Cross-site scripting attacks are therefore a special case of code injection.
I will explain this in detail in later hacking classes. So keep reading..
3. REMOTE FILE INCLUSION
Remote file inclusion is the most often found vulnerability on the website.
Remote File Inclusion (RFI) occurs when a remote file, usually a shell (a graphical interface for browsing remote files and running your own code on a server), is included into a website which allows the hacker to execute server side commands as the current logged on user, and have access to files on the server. With this power the hacker can continue on to use local
exploits to escalate his privileges and take over the whole system.
RFI can lead to following serious things on website :
4. LOCAL FILE INCLUSION
Local File Inclusion (LFI) is when you have the ability to browse through the server by means of directory transversal. One of the most common uses of LFI is to discover the /etc/passwd file. This file contains the user information of a Linux system. Hackers find sites vulnerable to LFI the same way I discussed for RFI’s.
Let’s say a hacker found a vulnerable site, www.target-site.com/index.php?p=about, by means of directory transversal he would try to browse to the /etc/passwd file:
I will explain it in detail with practical websites example in latter sequential classes on Website Hacking.
Simply called distributed denial of service attack. A denial-of-service attack (DoS attack) or distributed denial-of-service attack (DDoS attack) is an attempt to make a computer resource unavailable to its intended users. Although the means to carry out, motives for, and targets of a DoS attack may vary, it generally consists of the concerted efforts of a person or people to prevent an Internet site or service from functioning efficiently or at all, temporarily or indefinitely. In DDOS attack we consumes the bandwidth and resources of any website and make it unavailable to its legitimate users.
For more detailed hack on DDOS visit:
Its not a new category it comprises of above five categories but i mentioned it separately because there are several exploits which cannot be covered in the above five categories. So i will explain them individually with examples. The basic idea behind this is that find the vulnerability in the website and exploit it to get the admin or moderator privileges so that you can manipulate the things easily.
I hope you all now have a overview of that what is Website Hacking. In consecutive future classes i will explain all of these techniques in details. So guys keep reading..
IF YOU HAVE ANY QUERIES ASK IN COMMENTS…
Website Hacking Techniques Most Commonly Used By Hackers
Updated on: March 29, 2020
Do you use the internet? Guess is you do. Then you must have come across news such as hackers stealing data and bringing down services & websites. Here are some website hacking techniques hackers generally use.
These stats are startling, to say the least.
This does not mean website owners are reckless. No, they do take precautions. It’s only that – this is not enough! All websites and internet services have minute vulnerabilities that could be abused by this or that website hacking technique. Unless you identify and patch these vulnerabilities on time, you remain unsecured.
After every hack, I’ve seen many wonder – “If only I knew better of these hackers and the website hacking techniques, I might have successfully dodged it.“
While this has some truth to it, it isn’t entirely true.
That being said, of course, peeking into the minds of hackers helps. But without proper security equipment, you are only as good as a weaponless soldier.
So, with this blog post, we have created a window for you to look into the operations of a hacker and understand common web threats and the hacking techniques behind them.
Below are the nine most common website hacking techniques used by attackers.
Top Website Hacking Techniques
1. Social engineering (Phishing, Baiting)
Phishing is a method where the attacker replicates the original website and then leads a victim to use this fake website rather than the original one. Once the victim enters their credentials into this website, all details are sent to the attacker. This method can be used to obtain payment information such as credit card data or personal information such as login credentials to important accounts and websites.
Another type of social engineering is the ‘bait and switch’ attack. In this hacking technique, attackers buy advertising spots on trustworthy and popular websites and put up seemingly legit ads. Once the ads are launched, users click on it only to find themselves inside a website that is filled with malware. These malware gets installed on the victim’s system and then the attacker has a free run within their system
2. DDoS attacks
Distributed Denial of Service (DDoS) is mainly used to bring down websites by crashing their servers. Attackers flood the servers of the targeted website with the help of zombie computers or botnets. This overwhelms the resources of the servers and it crashes. In several cases, this attack was also used to steal user information by freezing the user forms. The recent DDoS attack on GitHub is an excellent example of how severe these attacks can be.
3. Code injection attacks
Code injection is the general term used for attacks that include injecting malicious codes into systems. Whenever there is improper handling of input data, it becomes vulnerable to code injection attacks.
These attacks are possible when input or output data is not properly validated. Once an attacker is able to inject their code into the system, they can compromise the integrity and security of the system. These attacks can also be used as a way to launch further attacks since the system is already infected and thus vulnerable.
4. SQL Injection
This attack majorly exploits vulnerabilities in a website’s SQL libraries or databases. In case a website has any such vulnerability, hackers can use simple SQL codes to obtain information and data from the databases. These simple codes trick the system into considering them as legit queries and then give access to its database.
5. XSS attacks
Also known as Cross-Site Scripting attacks, in this type of attack, hackers inject malicious code into a legit website. When a visitor enters the website and uses their credentials, all data is stored within the website, which the attacker can access anytime. These attacks can be effectively used to steal user data and private information.
There are two types of XSS attacks, stored XSS attacks and reflected XSS attacks. In stored attacks, the infected script is permanently kept in the server. And the attacker can retrieve it anytime. In reflected attacks, the scripts are bounced off web servers in the form of warnings or search results. Since this makes the request look authentic the website processes them and gets infected
6. Exploiting plugin vulnerabilities
If you use WordPress then you must be familiar with plugins (extensions & modules in case of Magento & Drupal respectively). Plugins are considered as the most vulnerable parts of a website. Any outdated or unsecured third-party plugins can be exploited by attackers to take control of your website or bring it down altogether. The best way to stay safe is to always use plugins from trusted sources and always keep your plugins updated
7. Brute force
In this hacking technique, the attackers try multiple combinations of the password until one of the combination matches. This method is simple to execute but requires huge computing power to implement. Longer the password, tougher it is to guess using brute force. Sometimes, attackers also use dictionaries to speed up the process
8. DNS Spoofing
By using DNS spoofing attacks, attackers can force victims to land on a fake website. This is done by changing the IP addresses stored in the DNS server to an address that leads to the attacker’s website. DNS cache poisoning is the process by which the local DNS server, with the infected server. Once the victim lands on the fake website, the attacker can infect the victim’s system with malware and use other website hacking techniques to cause further damage.
9. Cookie theft
As harmless as it sounds, this attack can effectively steal all your important data. During browsing sessions, websites stores tons of cookies on your computer. These cookies contain a lot of sensitive information, including your login credentials such as your passwords or even your payment data. If the attackers get their hands on these cookies, they can either steal all this information or use it to impersonate you online.
The above attacks are generally used against some vulnerability which the attackers exploit. That is why it is crucial to keep updating your software & other systems.
Once a vulnerability is discovered it is necessary to patch it up before an attacker exploits it to cause harm. Ethical hackers and security researchers around the globe try to discover such security gaps to ensure they are fixed. Astra’s VAPT (Vulnerability Assessment & Penetration Testing) does exactly that.
Moreover, you can look up known vulnerabilities in the system/software you are using by following this website: cve.mitre.org
Steps to protect yourself from getting hacked
Now we know the various ways attackers can harm you or your website. This will help us in understanding how attackers work and thus enable us to take more effective steps to protect ourselves from such attackers. Below are some basic steps to protect your data from some common website hacking techniques:
Websites are always vulnerable to such attacks and one needs to be vigilant round the clock. To monitor your website’s security, Astra’s security firewall is the best option for you.
With their constant monitoring of your website and an intuitive dashboard, you will always be aware of any attempts to sabotage your website.
If you liked this post, go ahead and share this with your friends 🙂
Hack the web! Как проверить сайт на уязвимости и как их эксплуатируют
Партнер
Содержание статьи
На январь 2020 года в интернете насчитывается 1,74 миллиарда сайтов, и многие из них уязвимы. Десять лет назад исследование Web Application Security Consortium показало, что минимум 13% сайтов можно взломать автоматически. А в недавнем исследовании Positive Technologies сообщается об уязвимости 19% протестированных веб-приложений. Поистине огромный простор для действий злоумышленников!
Общие принципы взлома сайтов
По структуре сайты делятся на три больших класса:
Встречаются еще самодельные CMS, созданные для конкретного сайта, но это сейчас стало редкостью — позволить себе поддержку своей системы могут только самые крупные ресурсы, и оправдать связанные с этим затраты непросто.
В основе большинства современных сайтов — готовые движки. Например, Xakep.ru не исключение: он работает на популярной системе WordPress (по крайней мере сейчас, в 2020 году).
С точки зрения атакующего, движки сайтов ничем не отличаются от других сервисов и служб. Их исходный код обычно находится в общем доступе, и любой исследователь может проанализировать его на ошибки, в том числе бреши в безопасности. Поэтому сайты на CMS редко становятся жертвами целевой атаки. Чаще их ломают массово.
Такой взлом автоматизирован и обычно протекает по следующей схеме: злоумышленник находит уязвимость (самостоятельно или просто гуглит что-то свежее). Затем он делает эксплоит или берет готовый и пишет специализированный бот. Этот бот ищет указанную дыру на всех сайтах подряд в заданном диапазоне и пытается эксплуатировать ее.
Казалось бы, для защиты от автоматических атак надо всего-то поддерживать программное обеспечение в актуальном состоянии, но в реальности CMS обрастает разными дополнениями, и уследить за всеми становится сложно.
При пентесте стоит несколько иная задача — проверить конкретный сайт на уязвимости. Об этом мы и поговорим.
WARNING
Статья предназначена для «белых хакеров», профессиональных пентестеров и руководителей службы информационной безопасности (CISO). Ни автор, ни редакция не несут ответственности за любой возможный вред, причиненный этим материалом.
Разведка
Прежде чем пытаться атаковать цель, нужно собрать информацию о ней. Для этого хорошо подходит инструмент WhatWeb. Эта утилита предоставляет подробную информацию о CMS жертвы и использованных ей веб-инструментах.
Вот пример запуска и собранных ответов:
Здесь мы видим, что это сайт британской компании, сделанный на WordPress, используется PHP v. 7.1.33 и jQuery 1.9.0, 2.2.3. Неплохо для начала!
Если у тебя нет VPN или ты просто не хочешь заморачиваться с установкой, обрати внимание на онлайновую версию WhatWeb.

Кстати, при работе с заграничными сайтами она дает большую скорость.
Если тебе достаточно определить только название CMS, то для этого есть отдельные сервисы, даже русскоязычные.
Продолжение доступно только участникам
Вариант 1. Присоединись к сообществу «Xakep.ru», чтобы читать все материалы на сайте
Членство в сообществе в течение указанного срока откроет тебе доступ ко ВСЕМ материалам «Хакера», позволит скачивать выпуски в PDF, отключит рекламу на сайте и увеличит личную накопительную скидку! Подробнее
Hack This Site In 7 Steps – How to Hack?
December 15, 2021 | By Admin
Types of Hackers
Some of the common types of hackers are as follows:
1. Ethical hackers
These hackers are also known as white hat hackers who do not illegally break into a computer’s network. Instead, they perform several tests to check the efficiency of their company’s security systems. Ethical hacking is done without any personal or profit motive. Computer security software manufacturers are those who mostly carry out this particular attack. They are considered to be the only line of defense between a black hat hacker and a company.
2. Black hat hackers
Unlike the white hat hackers, these black hat hackers execute just the opposite in both methodology and intention. After gaining access to a network, they only focus on corrupting data for their gain. They then share the information with other hackers to take advantage of the same vulnerabilities.
3. Blue hat hackers
Security companies call them to check for vulnerabilities in their system. Before launching a new product, companies will hire these rouge hackers for testing their systems.
4. Grey Hat Hackers
These hackers possess the properties of both black and white hat hackers. They generally scan the internet to observe flaws in a network. Next, they will hack into them and show the flaws to their administrator, thus seeking adequate compensation.
5. Intelligence Agencies
These hackers safeguard the national systems from foreign threats.
6. Organized Crime
This is a particular group of black hat hackers who try to find their gain by exposing computer systems.
7. Hacktivists
These hackers hack to advance social causes like politics, religion, or personal beliefs. Their main aim is to embarrass the victim or to deface a website. They come under two categories: the right to information and cyber terrorism. The former category refers to the concept of taking confidential information and exposing it to the public because they believe all information is free. The latter category aims at causing widespread fear by destroying a system’s operation and then making it useless to advance political motives.
The following tips will give you a brief idea of how to become a hacker:
UNIX is a multi-tasking and multi-user computer operating system that has been specifically designed to provide good security to the systems.
It is important to learn other modern computer programming languages such as Perl, PHP, JAVA, and Python.
Windows operating system is considered to be one of the most commonly compromised systems, hence it is always good to learn how to hack Microsoft systems, which are closed-source systems.
It is important that you thoroughly understand TCP/IP and UDP protocol to exploit the vulnerabilities on the world wide web.
From these articles, you will gain insight into hacking and how to develop the attitude to be a hacker.
As the most powerful language in computer programming, this programming language will help you divide the task into smaller pieces and these pieces can be expressed by a sequence of commands.
The technology of cryptography and encryption is extremely important for the internet and networking. Cryptography is increasingly used in ATM cards, e-commerce, and computer passwords. While hacking, these encrypted codes will have to be broken, and this is called decryption.
By initially experimenting on your computers, you will be able to rectify things if you have done any mistakes.
How to Hack a Website?
Website hacking can take place by:
Hacking Website using Online SQL Injection
The following steps are followed to hack a website using SQL injection:
Open google.com by using your system’s Firefox and type in inurl:.php?id= You will see a list of websites with dork PHP. Click on any of them.
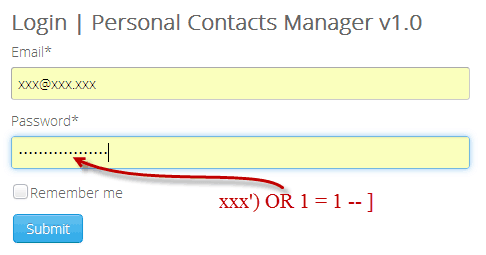
Insert an apostrophe at the end of the URL to check if the website is vulnerable. If it says, «you have an error in your SQL syntax«, then it indicates that the website is most likely to be vulnerable and hence proceed.
Remove the apostrophe and add order by 2—to see how many columns the website has and perhaps the most important work you have to do here. Keep testing with 3—, 4—, 5— till you receive a message like «unknown column».
Delete the ‘12 order by‘ and replace with null union all select 1,2,3,4,5,6,7,8,9,10— After the page loads, you will see a few numbers. Pick the top one. For instance, if it is 7 then replace 7 in the URL with @@Version. It will show 5.092 community which is great as it means that the database version is over 5 (fundamentally meaning it can be hacked).
Now replace @@version with group_concat(table_name) and after the last number, add from information_schema.tables where table_schema=database()—
Replace both tables in the URL with a column. You will get all the information the website has. Obtain those interesting to you, for example, username, full name, etc. Replace column_name with username,0x3a,pass and replace all the information tags with users—. You will get all the usernames and passwords associated with the website. If it says ‘unknown username and blank list’, it means you have the wrong table, and you will have to go back and look for a different table. It could also mean that you can select another way to hack a website, like the product.
Here, the usernames are displayed first because it comes before the pass in the URL.
To log in you will have to google admin page finder and then click on the first link. Follow the instructions and get your own admin page finder login. Following this, log in with any of the logins you have secured. Click on profile after it logs in and you will find all the details needed.
If you possess basic HTML and JavaScript knowledge, you might just be able to access websites that are password protected. This last method will present to you easy steps on how to hack an account on any website less secured websites of your choice through HTML. Remember that this method only works for websites with very low-security details.
Open the website you need to hack. In its sign-in form, enter the wrong username and wrong password combination. You will find an error popup saying the wrong username and password.
Right-click on that error page> and go to view source.
Open and view the source code. There you will see the HTML coding with JavaScript.
Carefully delete the JavaScript that validates your information on the server. This website can be successfully hacked based on how efficiently you delete the javascript code validating your account information.
Go to file>save as>and save it anywhere on your hard disk with ext.html
Reopen your target web i.e. ‘chan.html’ file that you earlier saved on your hard disk. You will see a few changes on the current page as compared to the original one. This indeed proves that you are on the right path.
Provide any username and password. You have thus successfully cracked a website and entered the account.
Note: All the above steps are for educational purposes. we do not encourage or endorse any type of hacking.