How to play gpo
How to play gpo
Use Group Policy to remotely install software
This article describes how to use Group Policy to automatically distribute programs to client computers or users.
Applies to: В Windows Server 2012 R2
Original KB number: В 816102
Summary
You can use Group Policy to distribute computer programs by using the following methods:
You can assign a program distribution to users or computers. If you assign the program to a user, it’s installed when the user logs on to the computer. When the user first runs the program, the installation is completed. If you assign the program to a computer, it’s installed when the computer starts, and it’s available to all users who log on to the computer. When a user first runs the program, the installation is completed.
You can publish a program distribution to users. When the user logs on to the computer, the published program is displayed in the Add or Remove Programs dialog box, and it can be installed from there.
Windows Server 2003 Group Policy automated-program installation requires client computers that are running Microsoft Windows 2000 or a later version.
Create a distribution point
To publish or assign a computer program, create a distribution point on the publishing server by following these steps:
Create a Group Policy Object
To create a Group Policy Object (GPO) to use to distribute the software package, follow these steps:
Assign a package
To assign a program to computers that are running Windows Server 2003, Windows 2000, or Windows XP Professional, or to users who are logging on to one of these workstations, follow these steps:
Start the Active Directory Users and Computers snap-in by clicking Start, pointing to Administrative Tools, and then clicking Active Directory Users and Computers.
In the console tree, right-click your domain, and then click Properties.
Click the Group Policy tab, select the policy that you want, and then click Edit.
Under Computer Configuration, expand Software Settings.
Right-click Software installation, point to New, and then click Package.
Don’t use the Browse button to access the location. Make sure that you use the UNC path of the shared installer package.
Click Open.
Click Assigned, and then click OK. The package is listed in the right-pane of the Group Policy window.
Close the Group Policy snap-in, click OK, and then close the Active Directory Users and Computers snap-in.
When the client computer starts, the managed software package is automatically installed.
Publish a package
To publish a package to computer users and make it available for installation from the Add or Remove Programs list in Control Panel, follow these steps:
Start the Active Directory Users and Computers snap-in by clicking Start, pointing to Administrative Tools, and then clicking Active Directory Users and Computers.
In the console tree, right-click your domain, and then click Properties.
Click the Group Policy tab, click the policy that you want, and then click Edit.
Under User Configuration, expand Software Settings.
Right-click Software installation, point to New, and then click Package.
Don’t use the Browse button to access the location. Make sure that you use the UNC path of the shared installer package.
Click Open.
Click Publish, and then click OK.
The package is listed in the right-pane of the Group Policy window.
Close the Group Policy snap-in, click OK, and then close the Active Directory Users and Computers snap-in.
Test the package.
Because there are several versions of Windows, the following steps may be different on your computer. If they are, see your product documentation to complete these steps.
Redeploy a package
In some cases, you may want to redeploy a software package (for example, if you upgrade or change the package). To redeploy a package, follow these steps:
Start the Active Directory Users and Computers snap-in by clicking Start, pointing to Administrative Tools, and then clicking Active Directory Users and Computers.
In the console tree, right-click your domain, and then click Properties.
Click the Group Policy tab, click the Group Policy Object that you used to deploy the package, and then click Edit.
Expand the Software Settings container that contains the software installation item that you used to deploy the package.
Click the software installation container that contains the package.
In the right-pane of the Group Policy window, right-click the program, point to All Tasks, and then click Redeploy application. You will receive the following message:
Redeploying this application will reinstall the application everywhere it is already installed. Do you want to continue?
Click Yes.
Quit the Group Policy snap-in, click OK, and then close the Active Directory Users and Computers snap-in.
Remove a package
To remove a published or assigned package, follow these steps:
Troubleshoot
Published packages are displayed on a client computer after you use a Group Policy to remove them.
This situation can occur when a user has installed the program but hasn’t used it. When the user first starts the published program, the installation is finished. Group Policy then removes the program.
How to apply a Group Policy Object to individual users or computers
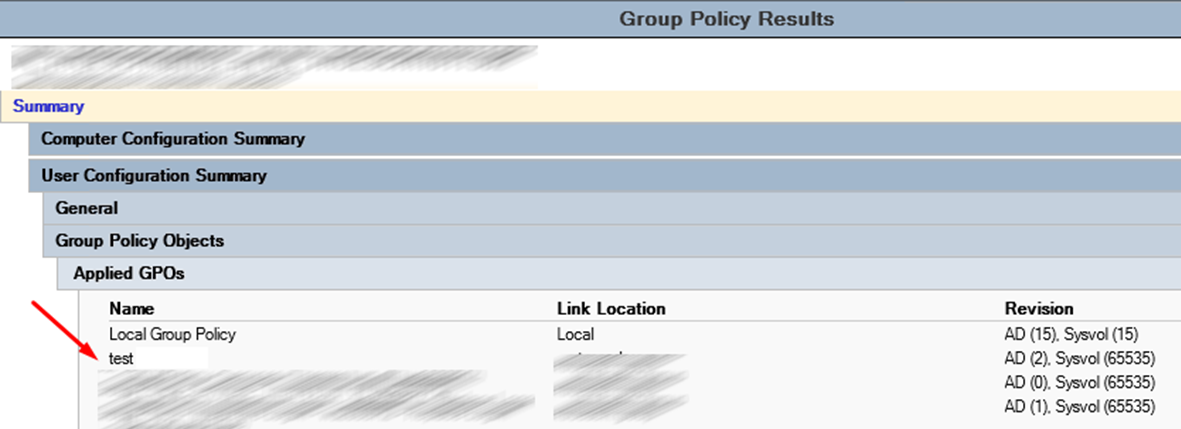
Привет, Хабр! Речь пойдет про групповые политики и Security Filtering. В зависимости от размера вашего домена, его логической структуры и количества OU, инструмент Security Filtering может быть вам очень полезным.
Используя Security Filtering вы можете применить политику к пользователям или к ПК которые расположены разных OU, разместив вашу политику в корне домена и применив фильтр.
Типовая задача для фильтрации это монтирование сетевых папок и принтеров. Но на принтерах и папках все только начинается и заканчивается вашей фантазией.
Читайте под катом, как применять групповые политики к отдельным пользователям/группам, и на что обратить внимание если при использовании Security Filtering ваши политики не работают.
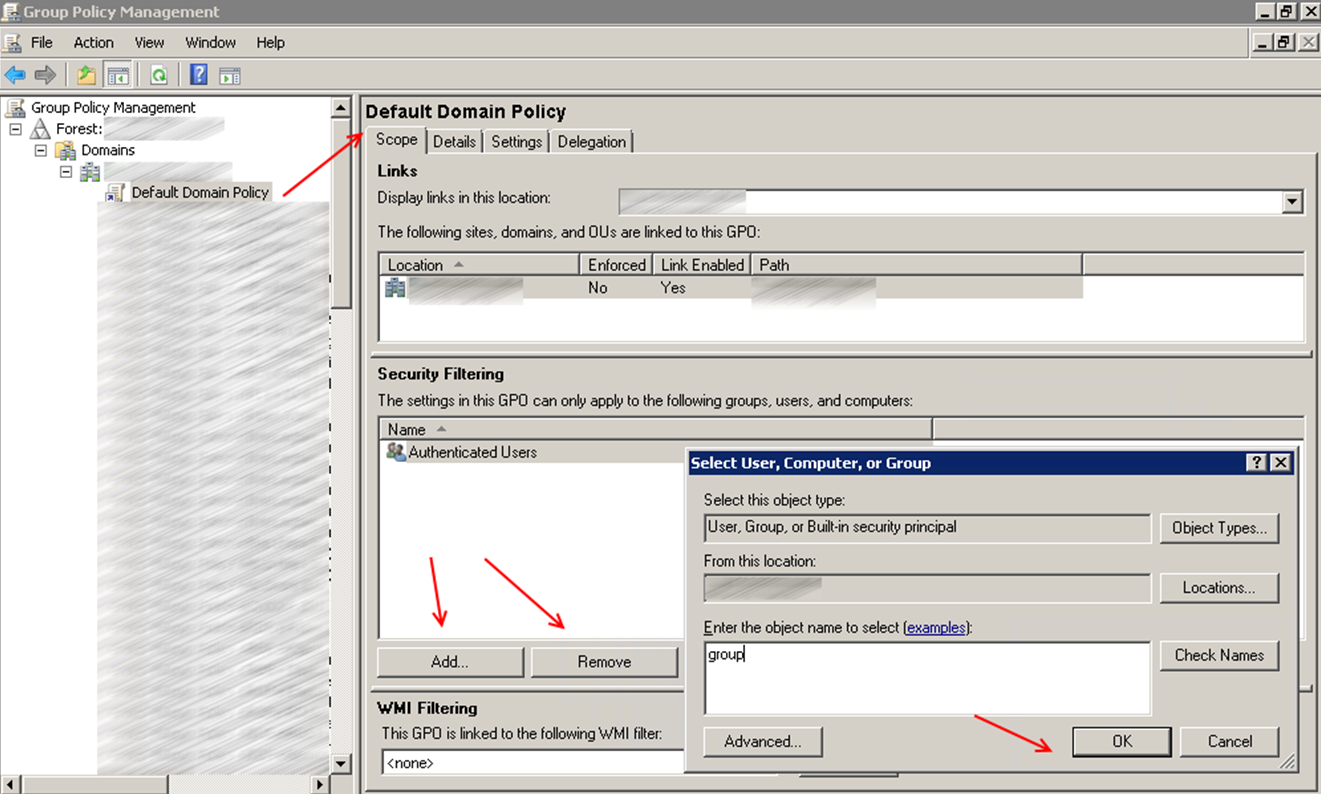
Механизм фильтрации прост, в закладке Security Filtering указаны группы к которым применяется политика, по умолчания политика применяется к группе Authenticated Users. Удалите группу Authenticated Users и укажите группы пользователей или ПК к которым должна применяться ваша политика.
Про проблемы и диагностику
После установки обновлений перестали работать некоторые политики.
Первое что я заметил, перестала работать политика которая монтировала сетевой диск пользователям. Долго я не разбирался и закрыл эту проблему инструментами Item-level targeting, а в настройках Security Filtering вернул стандартную группу Authenticated Users.
Item-level targeting можно использовать только для group policy preferences, и по этому это применимо не во всех случаях.
В чем же причина?
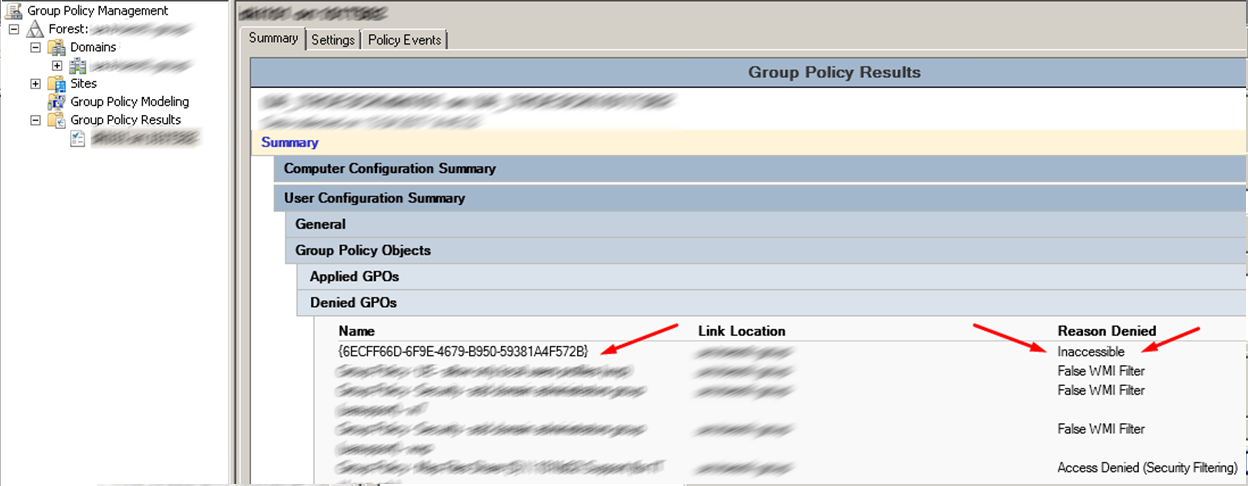
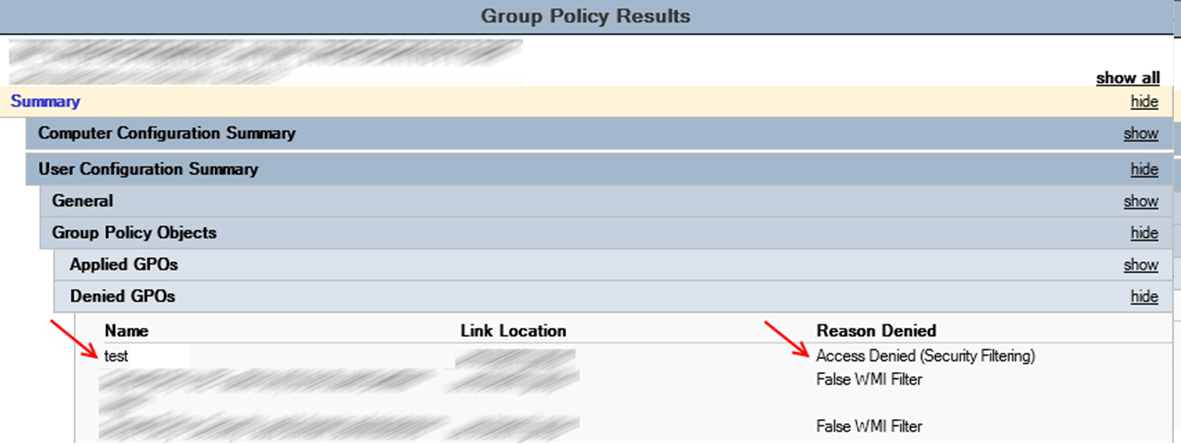
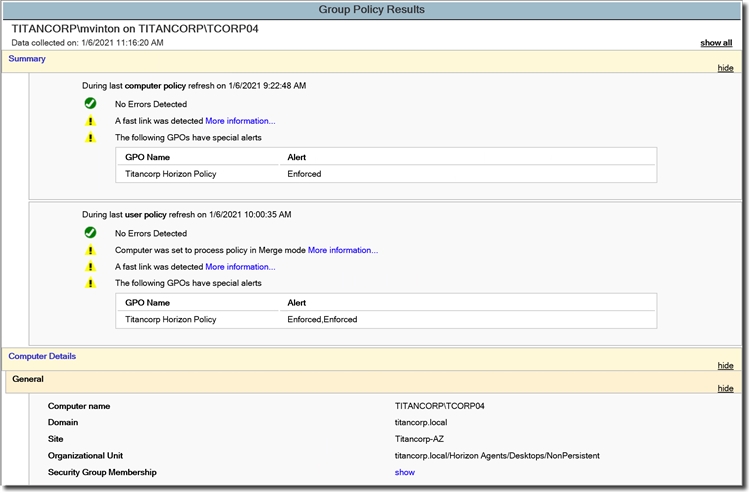
Если запустить визард Group Policy Results видно что политика с фильтром безопасности не применилась из за ошибки Inaccessable.
Решение я нашел на GROUP POLICY CENTRAL, это отличный ресурс посвященный групповым политикам, и на нем есть две статьи посвященных Security Filtering.
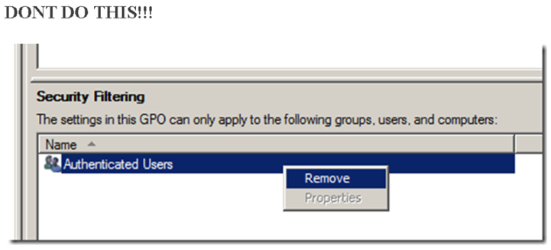
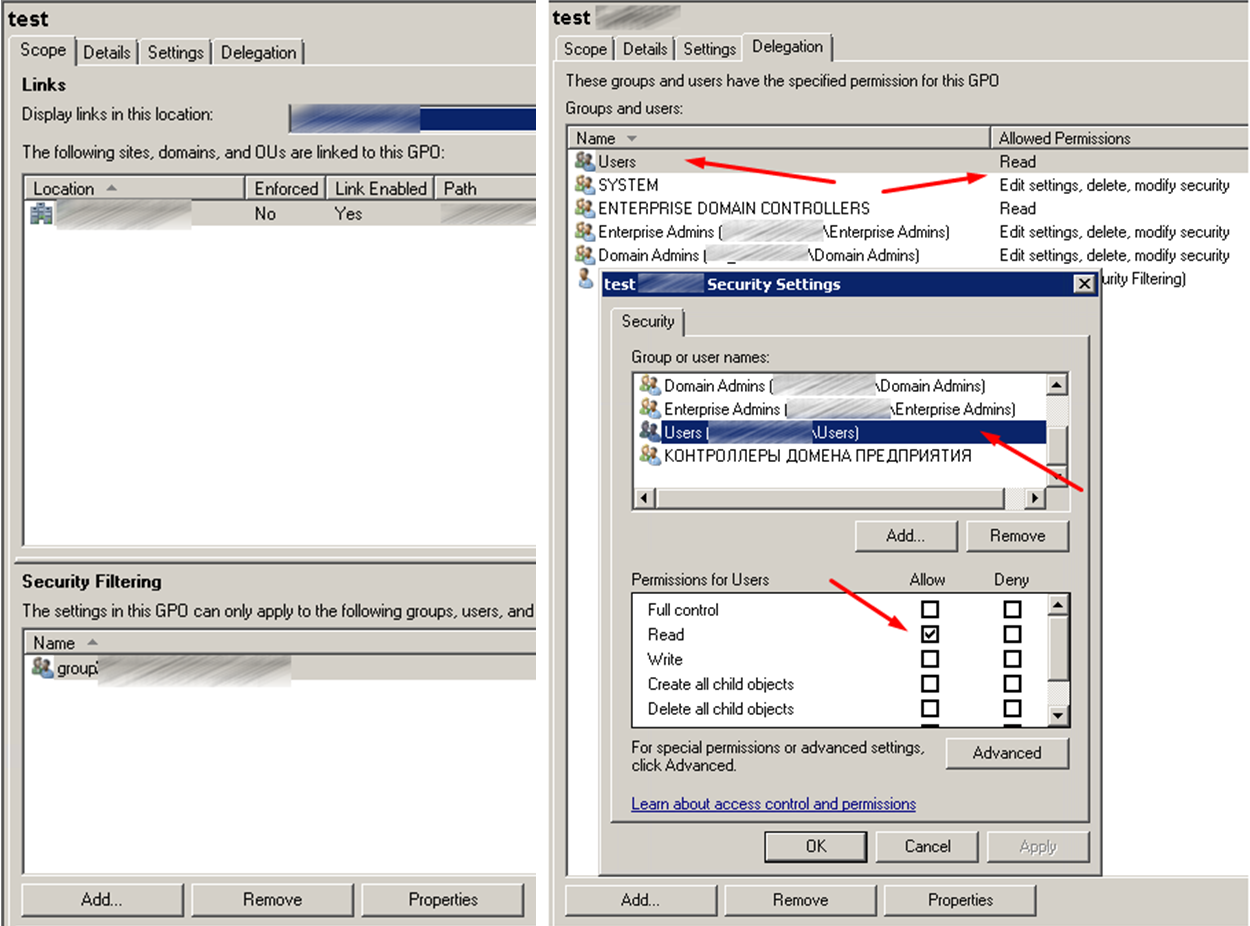
Автор пишет о том что нельзя удалять из фильтра безопасности группу Authenticated Users, и рекомендует использовать закладку GPO Delegation Advanced для фильтрации. Также говорится про то что политика будет работать, но микрософт все чаще преподносит сюрпризы своими обновлениями.

You should never do this as this however as this can cause “Inaccessible” (see image below) error messages on Group Policy Objects in the Group Policy Management Console for anyone who is not an Domain Administrator. This happens because you have removed the ability to for the user to read contents GPO but don’t worry this does not mean the policy will be applied to that user.
Я решил просто делегировал группе Users права только на чтение.
Проверяем Group Policy Results, политика применилась и нормально читается.
Если исключить пользователя из группы, причина отказа будет Access Denied (Security Filtering), все работает как и задумывалось.
Вот что по поводу проблем с Security Filtering пишут в микрософт
Коллеги из микрософта пишут что нужно предоставить права на чтение группе Authenticated Users или Domain Computers.
Symptoms
All user Group Policy, including those that have been security filtered on user accounts or security groups, or both, may fail to apply on domain joined computers.
Cause
This issue may occur if the Group Policy Object is missing the Read permissions for the Authenticated Users group or if you are using security filtering and are missing Read permissions for the domain computers group.
Resolution
To resolve this issue, use the Group Policy Management Console (GPMC.MSC) and follow one of the following steps:
— Add the Authenticated Users group with Read Permissions on the Group Policy Object (GPO).
— If you are using security filtering, add the Domain Computers group with read permission.
Подробный разбор MS16-072 уже присутствует на хабре — отличная статья
Более опытные коллеги предлагают изменить схему домена. Интересное решение, но я для себя не вижу проблемы руками настроить безопасность объекта групповой политики.
Пару слов про исключения пользователей.
Это отличный инструмент когда вам нужно исключить пользователей или ПК из зоны действия политики.
Пример: Такой политикой на терминальных серверах я скрываю от пользователей локальные диски в проводнике. Политика применяется на стандартную группу Authenticated Users, а в настройках безопасности для группы Administrators назначаю права Denay для Allow Apply group policy.
Так приходится делать потому что применив политику на группу по умолчанию Authenticated Users, вы автоматически применяете ее на всех пользователей, ведь администраторы автоматически являются участниками группы Authenticated Users.
Working with Group Policy Objects using GPMC
This topic describes procedures for configuring, filtering, backing up, restoring and importing Group Policy Objects using the Group Policy Management Console (GPMC).
Introduction
The Local Group Policy object (Local GPO) is stored on each individual computer, in the hidden Windows\System32\GroupPolicy directory. Generally, each computer running Windows has exactly one Local GPO, regardless of whether the computers are part of an Active Directory environment. Local GPOs are always processed, but are the least influential GPOs in an Active Directory environment, because Active Directory-based GPOs have precedence.
At the domain level, a GPO is a collection of Group Policy settings stored as a virtual object consisting of a Group Policy container and a Group Policy template. The Group Policy container, which contains information about the properties of a GPO, is stored in Active Directory on each domain controller in the domain. The Group Policy template contains the data in a GPO and is stored in the SYSVOL in the /Policies subdirectory. GPOs affect users and computers that are contained in sites, domains, and OUs.
Because GPOs contain policy settings, the GPOs can be configured, backed up, restored, copied, and scoped using the GPMC.
How to add a comment to a Group Policy Object
You can include comments for each Group Policy object. You can use this space to document the Group Policy object and why its implementation is important to your environment. Commenting GPOs allows you to later use keyword filter to help you quickly find GPOs with matching keywords.
Adding a comment to a Group Policy Object
Open the Group Policy Management Console. Expand the Group Policy Objects node.
Right-click the Group Policy object you want to comment and then click Edit.
In the console tree, right-click the name of the Group Policy object and then click Properties.
Click the Comment tab.
Type your comments in the Comment box.
Click OKВ
How to back up a Group Policy Object
To back up a Group Policy object
In the Group Policy Management Console (GPMC) console tree, open Group Policy Objects in the forest and domain containing the Group Policy object (GPO) to back up.
To back up a single GPO, right-click the GPO, and then click Back Up. To back up all GPOs in the domain, right-click Group Policy objects and click Back Up All.
In the Backup Group Policy object dialog box, in the Location box, enter the path for the location in which you want to store the GPO backups, or click Browse, locate the folder in which you want to store the GPO backups, and then click OK.
In the Description box, type a description for the GPOs that you want to back up, and then click Back Up. If you are backing up multiple GPOs, the description will apply to all GPOs you back up.
After the operation completes, click OK.
To secure backed-up GPOs, ensure that only authorized administrators have permission to access the folder to which you are exporting the GPOs.
Additional considerations
You must have Read permissions on the GPO and Write permissions on the folder containing the GPO backup to perform this procedure.
The backup function also serves as the export capability for GPOs.
How to block Group Policy Object inheritance
You can block inheritance for a domain or organizational unit. Blocking inheritance prevents Group Policy objects (GPOs) that are linked to higher sites, domains, or organizational units from being automatically inherited by the child-level.
To block inheritance
In the Group Policy Management Console (GPMC) console tree, double-click the forest containing the domain or organizational unit (OU) for which you want to block inheritance for GPO links, and then do one of the following:
To block inheritance of the GPO links of an entire domain, double-click Domains, and then right-click the domain.
To block inheritance for an OU, double-click Domains, double-click the domain containing the OU, and then right-click the OU.
Click Block Inheritance.
Additional considerations
To complete this procedure, you must have Link GPOs permission for the domain or OU.
If a domain or OU is set to block inheritance, it will appear with a blue exclamation mark in the console tree.
GPO links that are enforced cannot be blocked from the parent container.
How to copy a Group Policy Object
You can copy a Group Policy object (GPO) either by using the drag-and-drop method or right-click method. Both methods are described in this topic.
To copy a Group Policy object (drag-and-drop method)
In the Group Policy Management Console (GPMC) console tree, click the Group Policy object (GPO) that you want to copy.
Do one of the following:
To create a copy of the GPO on the same domain as the source GPO, drag and drop the GPO you want to copy to Group Policy Objects, select a permissions option under Specify the permissions for the new GPO, and then click OK.
To create a copy of the GPO in a different domain, double-click the destination domain, then drag and drop the GPO you want to copy to Group Policy objects. Answer all the questions in the cross-domain copying wizard that appears, and then click Finish.
To copy a Group Policy object (right-click method)
In the GPMC console tree, right-click the GPO that you want to copy, and then click Copy.
Do one of the following:
To create a copy of the GPO in the same domain as the source GPO, right-click Group Policy objects, click Paste, specify permissions for the new GPO in the Copy GPO box, and then click OK.
To create a copy of the GPO in a different domain, double-click the destination domain, right-click Group Policy objects, and then click Paste. Answer all the questions in the cross-domain copying wizard that appears, and then click Finish.
Additional considerations
You must have privileges to create GPOs in the destination domain to complete this procedure.
For copy operations to another domain, you may need to specify a migration table.
How to create and edit a Group Policy Object
You can also create a GPO from a Starter GPO. For more information, see Create a New GPO from a Starter GPO.
To create a Group Policy object
In the GPMC console tree, right-click Group Policy Objects in the forest and domain in which you want to create a GPO.
Click New.
In the New GPO dialog box, specify a name for the new GPO, and then click OK.
To edit a Group Policy Object
In the GPMC console tree, double-click Group Policy Objects in the forest and domain containing the GPO that you want to edit.
Right-click the GPO, and then click Edit.
In the console tree, edit the settings as appropriate.
The Default Domain Policy GPO and Default Domain Controllers Policy GPO are vital to the health of any domain. As a best practice, you should not edit the Default Domain Controllers Policy GPO or the Default Domain Policy GPO, except in the following cases:
Account policy settings are required to be configured in the Default Domain GPO.
If you install applications on domain controllers requiring modifications to User Rights or Audit policy settings, you must modify the policy settings in the Default Domain Controllers Policy GPO.
Additional considerations
When you create a GPO, it will not have an effect until it is linked to a site, domain, or organizational unit (OU).
By default only domain administrators, enterprise administrators, and members of the Group Policy creator owners group can create and edit GPOs.
To edit IPSec policy settings from within a GPO, you must be a member of the domain administrators group.
You can also edit a GPO by right-clicking the name of the GPO in any container in which it is linked, and then clicking Edit.
How to create and populate a Migration Table
A migration table is used when you copy or import a Group Policy Object (GPO) from one domain or forest to another. The key challenge when migrating Group Policy objects (GPOs) from one domain or forest to another is that some information in the GPO is actually specific to the domain or forest where the GPO is defined. When transferring the GPO to a new domain or forest, it may not always be desirable, or even possible, to use the same settings. You can use a migration table to reference users, groups, computers, and UNC paths in the source GPO to new values in the destination GPO.
You can create migration tables using the Migration Table Editor.
You can use the migration table editor to scan one or more Group Policy objects (GPOs) or backup GPOs, extract all references to security principals and UNC paths, and automatically enter these items in the migration table as source name entries.
To create a migration table
In the Group Policy Management Console (GPMC) console tree, double-click the forest from which you want to create a migration table.
Do either of the following:
Right-click Domains and then click Open Migration Table Editor.
Right-click Group Policy objects, and then click Open Migration Table Editor.
Specify a source you want to include in the migration table by doing the following:
Under Source Name, type the source name or right-click the cell and click Browse to find and then specify the object type, location, and name.
If you enter the source name manually, you must type the exact name of the User, Computer, Group, or UNC Path referenced in the source GPO (for example, TestDomain\PolicyAdmins or \\server1\publicshare). The type of the source name must match the source type specified in the migration table.
Security principals can be specified using any of the following formats:
UPN: For example, someone@contoso.com.
SAM: For example, contoso\someone.
DNS: For example, contoso.com\someone.
Free text: For example, someone. You must specify the type as Free Text or SID.
SID: For example, S-1-11-111111111-111111111-1111111111-1112. You must specify the type as Free Text or SID.
Under Source Type, specify the type of source in the cell adjacent to the source name cell by using the drop-down list and selecting the appropriate type. If you have used Browse to find the source name, the source type is entered by default.
Under Destination Name, type the destination name or right-click the cell adjacent to the source name and source type cells, and then do one of the following:
Click Browse to find a user, computer, or group.
Point to Set Destination, and then click the appropriate selection. You cannot use the No Destination option for UNC paths.
Repeat Step 3 for each source you want to include in the migration table.
Click File, and then click Save.
Specify the location where you want to save the migration table, and then click Save.
You can use the migration table editor to check that destination entries can be resolved. If destination entries do not resolve in the migration table, then the copy or import operation might fail. To validate your migration table, from the Tools menu, click Validate.
To automatically populate a migration table from a GPO
Open the migration table editor.
From the Tools menu, click Populate from GPO.
In the Look in this domain drop-down list, select the domain that contains the GPO.
In the Group Policy objects list, click the GPO or GPOs from which you want to populate the migration table, select Include security principals from the DACL on the GPO during scan if appropriate, and then click OK.
To automatically populate a migration table from a backup GPO
Open the migration table editor.
From the Tools menu, click Populate from Backup.
In the Backup location drop-down box, type the path of the folder that contains the backup GPO, or click Browse to locate the folder.
In the Backed up GPOs list, select one or more backed-up GPOs, select Show only the latest version of each GPO or Include security principals from the DACL on the GPO if appropriate, and then click OK.
Additional considerations
How to delete a Group Policy Object
Insert section body here.
To delete a GPO
In the Group Policy Management Console (GPMC) console tree, double-click Group Policy Objects in the forest and domain containing the Group Policy object (GPO) that you want to delete.
Right-click the GPO, and then click Delete.
When prompted to confirm the deletion, click OK.
Additional considerations
To delete a GPO, you must have Edit Settings, Delete, and Modify Security permissions for the GPO.
When you delete a GPO, GPMC attempts to delete all links to that GPO in the domain of the GPO. If you do not have rights to delete a link, the GPO will be deleted, but the link will remain. Links from other domains and sites are not deleted. The link to a deleted GPO appears in GPMC as Not Found. To delete Not Found links, you must have permission on the site, domain, or organizational unit containing the link.
You cannot delete the Default Domain Controllers Policy GPO or the Default Domain Policy GPO.
How to disable a Group Policy Object link
To disable a Group Policy object link
In the Group Policy Management Console (GPMC) console tree, double-click to expand the forest containing the domain, site, or organizational unit (OU) containing the link you want to disable, and then do one of the following:
Right-click the GPO link. A check mark next to Link Enabled indicates that the link is enabled.
Click Link Enabled to disable the link. No check mark will be displayed when the link is disabled.
Additional considerations
You must have Link GPOs permission for the domain, site, or OU to complete this procedure.
You can also click the GPO link and look at the information in the Links section of the Scope tab to determine if a GPO link is enabled.
How to disable user or computer settings in a Group Policy Object
To disable user or computer settings in a Group Policy object
In the Group Policy Management Console (GPMC) console tree, double-click the forest containing the domain or organizational unit (OU) that contains the Group Policy object (GPO).
Double-click the domain or OU.
Right-click the GPO that contains the user or computer settings you want to disable, point to GPO Status, and then do one of the following:
Click User settings disabled to disable user settings for the GPO.
Click Computer settings disabled to disable computer settings for the GPO.
A check mark next to User settings disabled or Computer settings disabled indicates that user or computer settings are disabled.
Additional considerations
You must have Edit permission on the GPO to complete this procedure.
You can also modify GPO Status from the Details tab of a GPO.
How to enforce a Group Policy Object link
To enforce a Group Policy object link
In the Group Policy Management Console (GPMC) console tree, double-click the forest containing the domain, site, or organizational unit (OU) containing the link you want to enforce, and then do one of the following:
To enforce a GPO link at the domain level, double-click Domains, and then double-click the domain containing the GPO link.
To enforce a GPO link at the OU level, double-click Domains, double-click the domain containing the OU, and then double-click the OU containing the GPO link.
To enforce a GPO link at the site level, double-click Sites, and double-click the site containing the GPO link.
Right-click the GPO link, and then click Enforced to enable or disable enforcing the link. A check mark next to Enforced indicates that the link is enforced.
Additional considerations
You must have Link GPOs permission for the domain, site, or organizational unit containing the GPO link to complete this procedure.
To determine whether a GPO link is enforced, you can also click the GPO link and look at the information in the Links section of the Scope tab.
How to filter Group Policy Objects using WMI filters
Windows Management Instrumentation (WMI) filters allow you to dynamically determine the scope of Group Policy objects (GPOs), based on attributes of the target computer.
When a GPO that is linked to a WMI filter is applied on the target computer, the filter is evaluated on the target computer. If the WMI filter evaluates to false, the GPO is not applied (unless the client computer is running Windows 2000, in which case the filter is ignored and the GPO is always applied). If the WMI filter evaluates to true, the GPO is applied.
To create a WMI filter
In the Group Policy Management Console (GPMC) console tree, right-click WMI Filters in the forest and domain in which you want to create a WMI filter.
Click New.
In the New WMI Filter dialog box, type a name for the new WMI Filter in the Name box, and type a description of the filter in the Description box.
Click Add.
In the WMI Query dialog box, either leave the default namespace (root\CIMv2) or enter another namespace by doing one of the following:
In the Namespace box, type the name of the namespace that you want to use for the WMI query.
Click Browse, select a namespace from the list, and then click OK.
Type a WMI query in the Query box, and then click OK.
To add more queries, repeat Steps 4 through 6 to add each query.
After adding all queries, click Save.
Additional considerations
You must have privileges to create WMI filters in the domain in which you want to create the filter. By default, the Domain Administrators, Enterprise Administrators, and Group Policy Creator Owners groups have this permission.
WMI Filters is only available if at least one domain controller in the domain is running Microsoft Windows Serverв„ўВ 2003. The same is true for WMI Filtering on the Scope tab for Group Policy Objects.
To delete a WMI filter, in the console tree, right-click the WMI filter and then click Delete. When asked to confirm whether you want to delete the WMI filter, click Yes.
WMI Filters are not evaluated on Microsoft WindowsВ® 2000. A GPO targeted to a Windows 2000 machine will always apply the GPO regardless of the query associated with the WMI Filter (the filter is ignored)
Import a WMI Filter
In the Group Policy Management Console (GPMC) console tree, right-click WMI Filters in the forest and domain into which you want to import a WMI filter.
Click Import.
In the Import WMI Filter dialog box, specify the appropriate information in the Name and Description boxes, and then do one of the following:
To import the WMI filter without changing it, click Import.
To change the WMI filter and then import it, click Edit, make the appropriate changes to the namespace or query, click OK, and then click Import.
Additional considerations
You must have privileges to create WMI filters in the domain in which you want to create the filter to complete this procedure. By default the Domain Administrators, Enterprise Administrators, and Group Policy Creator Owners groups have this permission.
WMI Filters is only available if at least one domain controller in the domain is running Microsoft Windows ServerВ 2003. The same is true for WMI Filtering on the Scope tab for Group Policy objects.
Importing a WMI filter creates a new filter instead of modifying an existing filter.
Export a WMI filter
In the Group Policy Management Console (GPMC) console tree, right-click the WMI filter that you want to export, and then click Export.
In the Export WMI filter dialog box, select a secure file system location from the Save in drop-down list box, type a name for the filter that you want to export, and then click Save.
Additional considerations
You can also export a WMI filter by clicking WMI Filters and, in the results pane, clicking the Contents tab, right-clicking the filter name, and then clicking Export.
To copy a WMI Filter
In the Group Policy Management Console (GPMC) console tree, click the WMI filter in the forest and domain containing the WMI filter that you want to copy.
Right-click the WMI filter you want to copy, and then click Copy.
In the destination domain, right-click WMI Filters, and then click Paste.
Additional considerations
To link a WMI filter to a Group Policy object
In the Group Policy Management Console (GPMC) console tree, double-click Group Policy Objects in the forest and domain containing the Group Policy object (GPO) to which you want to link a WMI filter.
In the results pane, on the Scope tab, under WMI Filtering, select a WMI filter from the drop-down list.
When prompted to confirm the selection, click Yes.
Additional considerations
To link a WMI filter to a GPO, you must have Edit permissions on the GPO.
Only one WMI filter can be linked to a GPO, and you can only link a WMI filter to a GPO in the same domain.
WMI Filters and WMI Filtering on the Scope tab for GPOs are available only if at least one domain controller in the domain is running Microsoft Windows ServerВ 2003.
How to filter for Group Policy Objects using security groups
To filter using security groups
In the Group Policy Management Console (GPMC) console tree, expand Group Policy Objects and click the Group Policy object (GPO) to which you want to apply security filtering.
In the results pane, on the Scope tab, click Add.
In the Enter the object name to select box, type the name of the group, user, or computer that you want to add to the security filter. Click OK.
Additional considerations
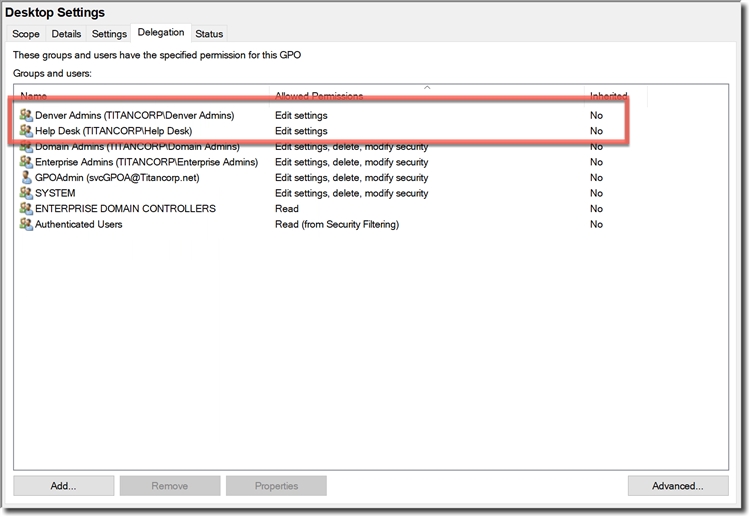
In order to ensure that only members of the group or groups you added in Step 3 can receive the settings in this GPO, you will need to remove Authenticated Users if this group appears in the Scope tab. Click the Scope tab, select this group, and then click Remove.
You must have Edit settings, delete, and modify security permissions on the GPO to perform these procedures.
The settings in a GPO will apply only to users and computers that are contained in the domain, organizational unit, or organizational units to which the GPO is linked, and that are specified in or are members of a group that are specified in Security Filtering.
How to import settings from a Group Policy Object
To import settings from a Group Policy object
In the Group Policy Management Console (GPMC) console tree, expand the Group Policy Objects node in the forest and domain containing the Group Policy object (GPO) to import settings.
Right-click the GPO and click Import Settings.
Follow the instructions in the Import Settings Wizard.
Additional considerations
To complete this procedure, you must have Edit permissions on the GPO into which you want to import settings.
For import operations to another domain or forest, you may need to specify a migration table.
How to link Group Policy Objects
To link a GPO
In the Group Policy Management Console (GPMC) console tree, locate the site, domain, or organizational unit (OU) to which you want to link a Group Policy object (GPO)
Do one of the following:
To link an existing GPO, right-click the domain or OU within the domain, and then click Link an Existing GPO. In the Select GPO dialog box, click the GPO that you want to link, and then click OK.
To link a new GPO, right-click the domain or OU within a domain, and then click Create a GPO in this domain, and link it here. In the Name box, type a name for the new GPO, and then click OK.
Additional considerations
To link an existing GPO to a site, domain, or OU, you must have Link GPOs permission on that site, domain, or OU. By default, only domain administrators and enterprise administrators have this privilege for domains and OUs. Enterprise administrators and domain administrators of the forest root domain have this privilege for sites.
To create and link a GPO, you must have Link GPOs permissions on the desired domain or organizational unit, and you must have permission to create GPOs in that domain. By default, only domain administrators, enterprise administrators, and Group Policy Creator owners have permission to create GPOs.
The Create a GPO in this domain, and link it here option is not available for sites. The administrator can create a GPO in any domain in the forest, and then use the Link an Existing GPO option to link it to the site.
How to restore a deleted or previous version of an existing Group Policy Object
To restore a deleted or previous version of an existing Group Policy object
In the Group Policy Management Console (GPMC) console tree, in the forest and domain containing the Group Policy object (GPO) that you want to restore, locate Group Policy Objects.
Right-click Group Policy Objects and then click Manage Backups.
In the Manage Backups dialog box, in the Backup location box, type the path for the backup folder. You can also use Browse to locate the backup folder.
In the Backed up GPOs box, select the GPO that you want to restore from the list of GPO backups shown, and then click Restore.
When prompted to confirm the restore operation, click OK.
After the operation completes, click OK and then click Close.
Additional considerations
You must have privileges to create GPOs in the domain and Read permissions on the file system location of the backed-up GPO to restore a GPO that has been deleted.
You can also restore an existing or deleted GPO using the Manage Backups function by right-clicking Domains.
How to search for a Group Policy Object
To search for a Group Policy object
In the Group Policy Management Console (GPMC) console tree, double-click the forest containing the domain where you want to search for a Group Policy object (GPO). Double-click Domains, right-click the domain, and then click Search.
In the Search for Group Policy objects dialog box, in the Search for GPOs in this domain box, select a domain or select All domains shown in this forest.
In the Search item box, select the type of object on which you want to base your search.
If you select Security Group, the Select User, Computer, or Group dialog box appears. Specify the appropriate object type, location of the object, and object name, and then click OK.
You can choose GPO-links on the Search item dropdown menu to find unlinked GPOs and GPOs linked across domains.
In the Condition box, select the condition that you want to use in the search.
In the Value box, select or specify the value that you want to use to filter the search, and then click Add.
Repeat Steps 4 and 5 until you complete the definition of all search criteria, and then click Search.
When search results are returned, do one of the following:
To save the search results, click Save results and then, in the Save GPO Search Results dialog box, specify the file name for the saved results, and then click Save.
To navigate to a GPO found in the search, double-click the GPO in the search results list.
To clear the search results, click Clear.
Additional considerations
You can also open the search dialog box by right-clicking a forest and then clicking Search. In this case, the search for GPOs in this domain box defaults to All domains shown in this forest.
If a policy setting is enabled and then all the policy settings in that extension are removed, there can be false-positive search results for certain types of settings. This happens because the GPO has the extension listed as active. The extensions with this behavior are Security Settings, Software Installation, Folder Redirection, Internet Explorer Maintenance, and Encrypting File System (EFS).
What is Group Policy (GPO) and What Role Does It Play in Data Security
First things first, what is Group Policy? Group Policy is a feature of Windows that facilitates a wide variety of advanced settings that network administrators can use to control the working environment of users and computer accounts in Active Directory. It essentially provides a centralized place for administrators to manage and configure operating systems, applications and users’ settings.
Group Policies, when used correctly, can enable you to increase the security of user’s computers and help defend against both insider threats and external attacks.
In this blog, we will go through a detailed explanation of what Group Policies and GPOs are, and how system administrators can use them to help prevent data breaches.
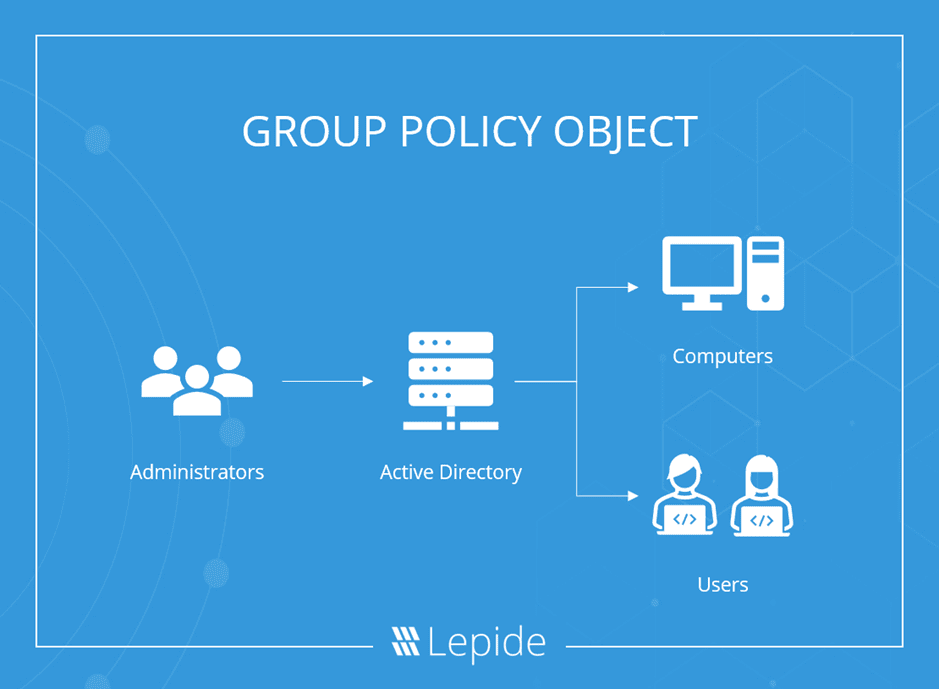
What is a Group Policy Object (GPO)?
A Group Policy Object (GPO) is a group of settings that are created using the Microsoft Management Console (MMC) Group Policy Editor. GPOs can be associated with a single or numerous Active Directory containers, including sites, domains, or organizational units (OUs). The MMC allows users to create GPOs that define registry-based policies, security options, software installation and much more.
Active Directory applies GPOs in the same, logical order; local policies, site policies, domain policies and OU policies.
Note: GPOs that are in nested OUs work from the OU closest to the root first and outwards from there.
Examples of GPOs
Group Policy Objects can be used in a number of ways that benefit security, many of which will be mentioned throughout this article. Below are a few more specific examples:
How Are Group Policy Objects Processed?
The order at which GPOs are processed affects what settings are applied to the computer and user. The order that GPOs are processed is known as LSDOU, which stands for local, site, domain, organizational unit. The local computer policy is the first to be processed, followed by the site level to domain AD policies, then finally into organization units. If there happen to be conflicting policies in LSDOU, the last applied policies wins out.
Should You Use Group Policy?
The short answer is yes. If you want to ensure that your data and your core IT infrastructure is set up in a secure way, then you probably need to understand how to properly use Group Policy.
It might surprise you to learn that Windows straight out-of-the-box isn’t exactly secure. There are numerous gaps in security, most of which can be addressed using GPOs. Without plugging these gaps, you leave yourself exposed to a plethora of security threats.
GPOs, for example, can help you implement a policy of least privilege where your users only have the permissions they require to do their job. They can do this through disabling Local Administrator rights globally in your network and grant admin privileges to individuals or groups based on their roles.
Group Policies can be used in numerous ways to bolster security, including disabling outdated protocols, preventing users from making certain changes and more. Let’s take a look at some of the benefits of Group Policy.
The Benefits of Group Policy for Data Security
The benefits of Group Policy are not limited solely to security, there are a number of other advantages that are worth mentioning.
If you like this, you’ll love this:
The Limitations of Group Policy
I’d be lying if I said to you that GPOs were the magic bullet to keeping your data secure. There are a number of limitations that you need to be aware of before you start implementing them.
Firstly, the GPO editor isn’t the most user-friendly console that you’re likely to come across. A deep understanding of PowerShell will help make it easier to do all the GPO updates.
Speaking of GPO updates, they are undertaken randomly every 90 to 120 minutes whenever the computer gets rebooted. You can be specific with an update rate from 0 minutes up to 45 days. However, if you do specify 0 minutes, then by default the GPOs will attempt to update every 7 seconds, which is likely to choke your network with traffic.
GPOs are also not immune to cyberattacks. If an attacker wanted to change local GPOs on a computer in order to move laterally across the network, it would be very difficult to detect this without a Group Policy auditing and monitoring solution in place.
How Lepide Helps
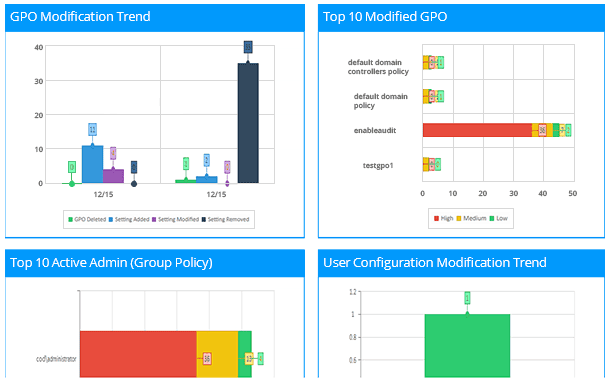
The Lepide’s Group Policy Auditing solution (part of Lepide Data Security Platform) will help you to get more visibility over the changes being made to your Group Policy Objects. Every time a critical change is made, Lepide will send the admin a real time alert and provide the option to roll back unwanted changes to their previous state; allowing admins to maintain a policy of least privilege and ensure the security policies of the organization remain intact.
Want to see how Lepide can help you to audit changes being made to GPOs and automatically disable the stolen account to stop the attack? Schedule a demo with one of engineer or download free trial to see the principle in action.
Групповые политики (GPO) Active Directory: разбираемся почему это важно и как ими управлять в GPOAdmin
Групповая политика — важный элемент любой среды Microsoft Active Directory (AD). Её основная цель — дать ИТ-администраторам возможность централизованно управлять пользователями и компьютерами в домене. Групповая политика, в свою очередь, состоит из набора политик, называемых объектами групповой политики (GPO). У Microsoft реализованы тысячи разных политик и настроек, в которых можно утонуть и потом не всплыть. Все они подробно описаны в справочной таблице.
В этой статье мы расскажем о работах по настройке групповых политик и удобном инструменте для упрощения управления ими — Quest GPOAdmin. Подробности под катом.
Как устроены групповые политики
При создании домена AD автоматически создаются два объекта групповой политики:
Политика домена по умолчанию устанавливает базовые параметры для всех пользователей и компьютеров в домене в трех плоскостях: политика паролей, политика блокировки учетных записей и политика Kerberos.
Политика контроллеров домена по умолчанию устанавливает базовые параметры безопасности и аудита для всех контроллеров домена в рамках домена.
Для вступления настроек в силу, объект групповой политики необходимо применить (связать) с одним или несколькими контейнерами Active Directory: сайт, домен или подразделение (OU). Например, можно использовать групповую политику, чтобы потребовать от всех пользователей в определённом домене использовать более сложные пароли или запретить использование съемных носителей на всех компьютерах только в финансовом подразделении данного домена.
Объект групповой политики не действует, пока не будет связан с контейнером Active Directory, например, сайтом, доменом или подразделением. Любой объект групповой политики может быть связан с несколькими контейнерами, и, наоборот, с конкретным контейнером может быть связано несколько объектов групповой политики. Кроме того, контейнеры наследуют объекты групповой политики, например, объект групповой политики, связанный с подразделением, применяется ко всем пользователям и компьютерам в его дочерних подразделениях. Аналогичным образом, объект групповой политики, применяемый к OU, применяется не только ко всем пользователям и компьютерам в этом OU, но и наследуется всем пользователям и компьютерам в дочерних OU.
Настройки различных объектов групповой политики могут перекрываться или конфликтовать. По умолчанию объекты групповой политики обрабатываются в следующем порядке (причем созданные позднее имеют приоритет над созданными ранее):
Изменение последовательности GPO. Объект групповой политики, созданный позднее, обрабатывается последним и имеет наивысший приоритет, перезаписывая настройки в созданных ранее объектах. Это работает в случае возникновения конфликтов.
Блокирование наследования. По умолчанию дочерние объекты наследуют все объекты групповой политики от родительского, но вы можете заблокировать это наследование.
Принудительное игнорирование связи GPO. По умолчанию параметры родительских политик перезаписываются любыми конфликтующими политиками дочерних объектов. Вы можете переопределить это поведение.
Отключение связей GPO. По умолчанию, обработка включена для всех связей GPO. Вы можете предотвратить применение объекта групповой политики для конкретного контейнера, отключив связь с объектом групповой политики этого контейнера.
Иногда сложно понять, какие политики фактически применяются к конкретному пользователю или компьютеру, определить т.н. результирующий набор политик (Resultant Set of Policy, RSoP). Microsoft предлагает утилиту командной строки GPResult, который умеет генерировать отчет RSoP.
Для управления групповыми политиками Microsoft предоставляет консоль управления групповыми политиками (GPMC). Используя этот бесплатный редактор групповой политики, ИТ-администраторы могут создавать, копировать, импортировать, создавать резервные копии и восстанавливать объекты групповой политики, а также составлять отчеты по ним. Microsoft также предлагает целый набор интерфейсов GPMC, которые можно использовать для программного доступа ко многим операциям, поддерживаемым консолью.
По умолчанию любой член группы администраторов домена может создавать объекты групповой политики и управлять ими. Кроме того, существует глобальная группа под названием «Владельцы-создатели групповых политик»; его члены могут создавать объекты групповой политики, но они могут изменять только созданные ими политики, если им специально не предоставлены разрешения на редактирование других объектов групповой политики.
В этой же консоли можно делегировать вспомогательным ИТ-администраторам разрешения для различных действий: создание, редактирование и создание связей для определенных объектов групповой политики. Делегирование — ценный инструмент; например, можно предоставить группе, ответственной за управление Microsoft Office, возможность редактировать объекты групповой политики, используемые для управления настройками Office на рабочем столе пользователей.
Управление групповой политикой и делегирование
Делегирование— та вещь, которая быстро выходит из-под контроля. Права делегируются то так то эдак и, в конце концов, не те люди могут получить не те права.
Ценность групповой политики заключается в ее силе. Одним махом вы можете применить политики в домене или подразделении, которые значительно укрепят безопасность или улучшат производительность бизнеса. Или наоборот.
Но этой властью также можно злоупотребить, намеренно или случайно. Одно неправильное изменение объекта групповой политики может привести к нарушению безопасности. Взломщик или злонамеренный администратор могут легко изменить объекты групповой политики, чтобы, например:
Почему встроенные инструменты работы с GPO недостаточно удобны
К сожалению, встроенные инструменты не всегда позволяют в удобном формате поддерживать безопасность и контроль групповой политики. Изменения, внесенные в объекты групповой политики, по умолчанию вступают в силу, как только окно закрывается — отсутствует кнопка «Применить», которая могла бы дать администраторам шанс остановиться, одуматься и выявить ошибки, прежде чем организация подвергнется атаке.
Из-за того, что разрешения безопасности основаны на объектах групповой политики, любой администратор домена может изменять любой параметр безопасности объекта групповой политики. И даже параметры, которые должны препятствовать злонамеренным действиям этого человека. Например, администратор может отключить объект групповой политики, который отвечает за разрешение входа в систему на определенном сервере, на котором размещены конфиденциальные данные. Ну, а дальше скопировать часть или весь ценный контент на свой компьютер и продать в даркнете.
Но самое ужасное во всей этой истории с безопасностью GPO — изменения настроек не отслеживаются в собственных журналах безопасности, нет предупреждений, следовательно, невозможно отслеживать такие нарушения, даже если использовать SIEM-систему.
Как обезопасить GPO (объекты групповой политики)
Лучший способ минимизировать риск неправильной настройки объектов групповой политики — это создать многоуровневую структуру безопасности, которая дополняет собственные инструменты. Для надёжной защиты групповой политики нужны решения, которые позволят:
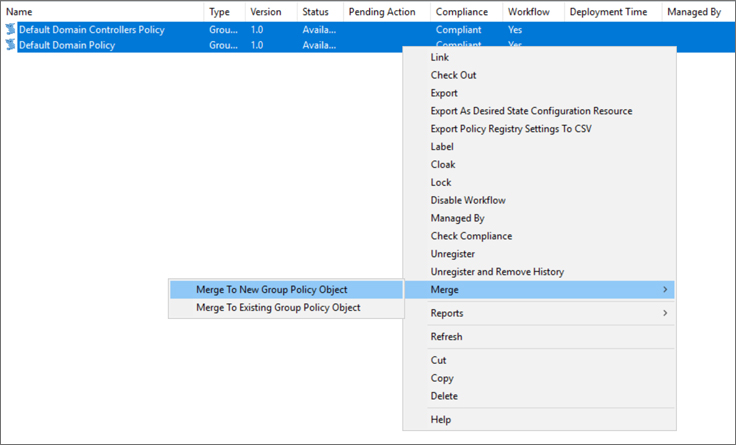
В интерфейсе можно выбрать избыточные или конфликтующие параметры групповой политики и объединить их в один объект групповой политики или создать новый.
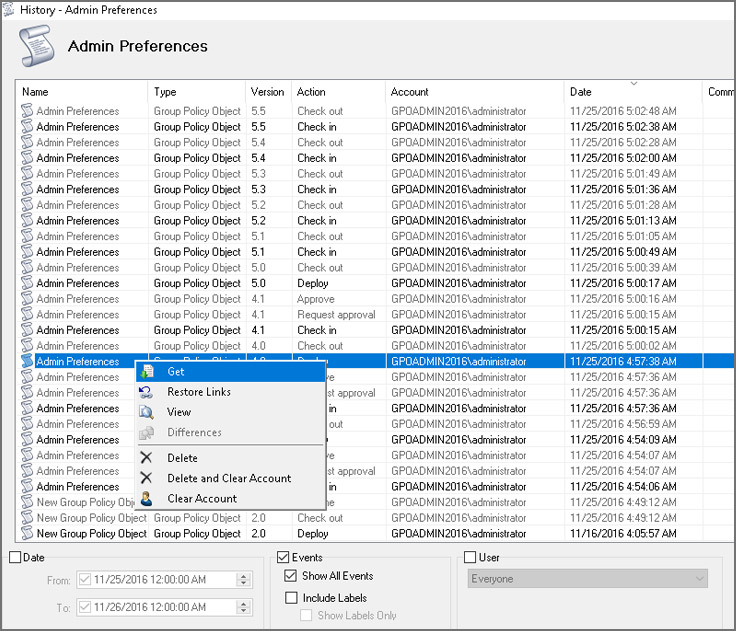
Откат. Можно легко откатиться к предыдущим версиям объектов групповой политики и устранить негативные последствия.
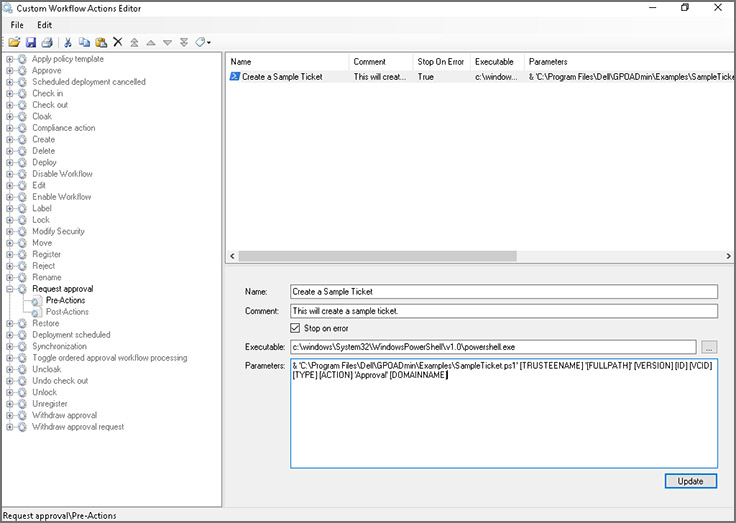
Настраиваемый воркфлоу. В интерфейсе GPOADmin можно заранее определить автоматические действия для различных сценариев.
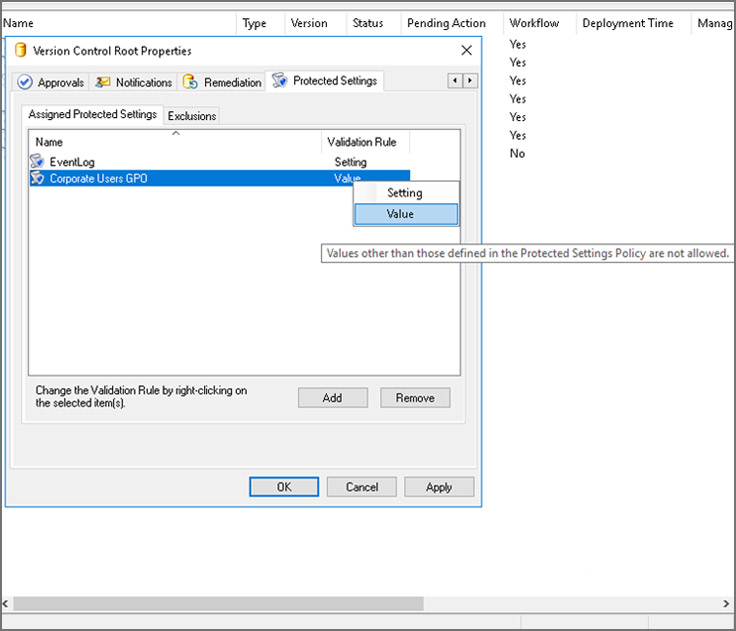
Политики защищенных настроек. Определите список параметров, по которым проверяются разрешенные настройки для политик.
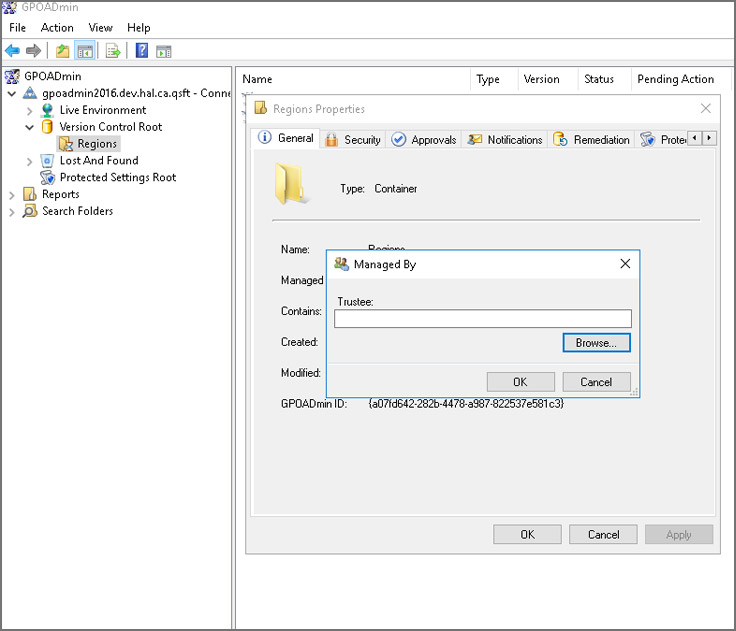
Управление объектами. В интерфейсе легко определить, кто отвечает за управление определенными политиками.
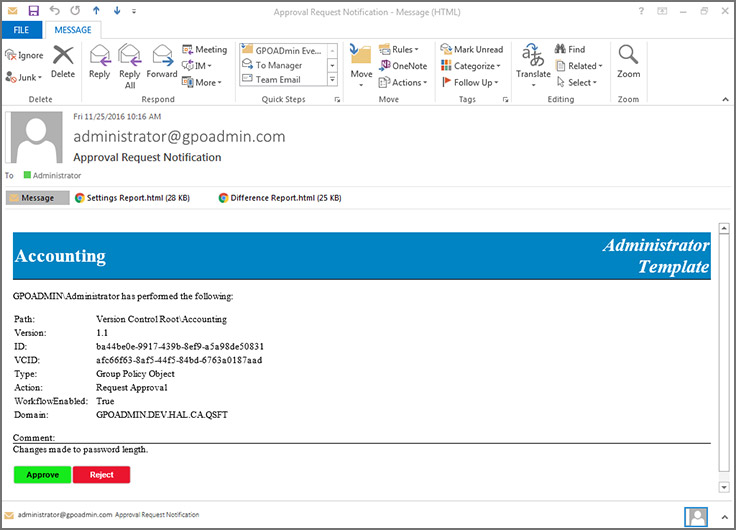
Подтверждение по электронной почте. Утверждать или отклонять запросы на изменение объекта групповой политики можно прямо из письма в почте.
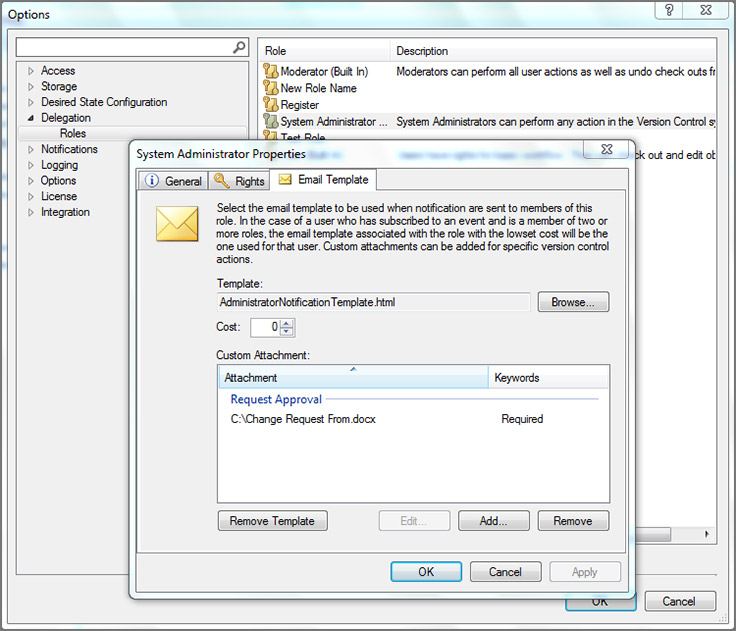
Пользовательские шаблоны писем. Для определенных ролей шаблоны писем можно кастомизировать.
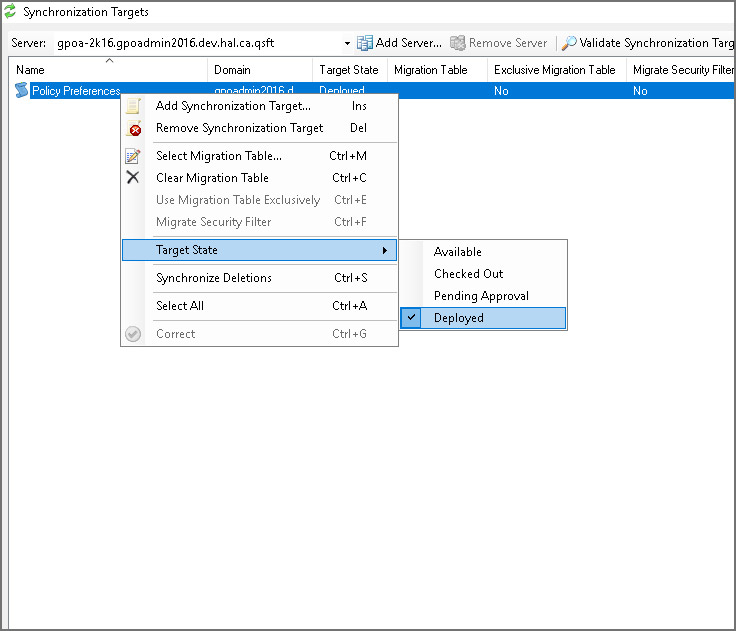
Синхронизация GPO. Доступна возможность синхронизации настроек между несколькими GPO.
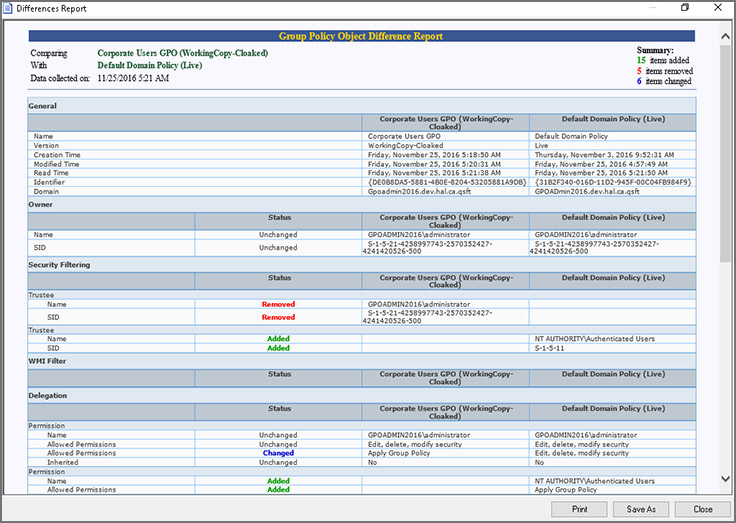
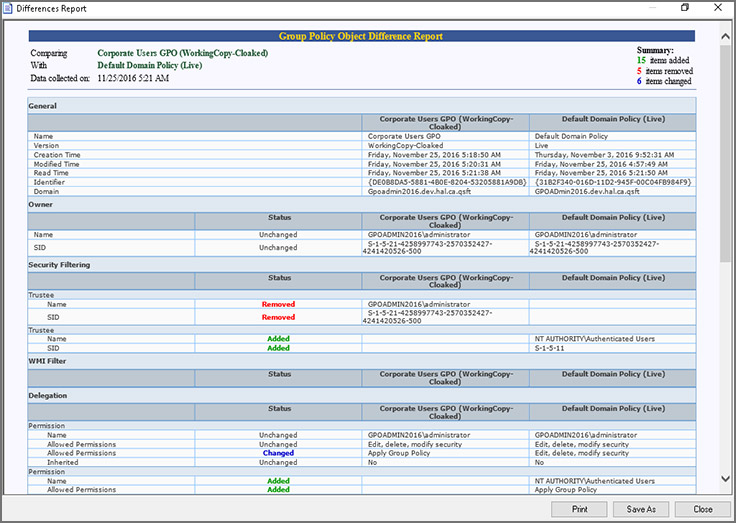
Сравнение GPO. Обеспечьте целостность настроек GPO и снизьте риск нарушения политики.
С GPOAdmin можно навести порядок в работе десятка администраторов, которые могут намеренно или случайно вносить неправильные изменения в объекты групповой политики. Теперь о каждом изменении будут знать все.
Мы готовы провести для вас демонстрацию или развернуть решение в вашей инфраструктуре, чтобы вы могли убедиться в ценности GPOAdmin для вашей организации. Решение, действительно, поможет уберечься от фатальных ошибок и навести порядок в домене. Свяжитесь с нами удобным для вас способом.