How to spawn dummy in gpo
How to spawn dummy in gpo
How to spawn dummy in gpo
Sorry, I really am very new to this. On a side note, where is best to be hosting GPO’s, on the DC or our image deployment server?
The GPOs themselves will be the \\mydomain\sysvol folder which is synced between all your DCs (assuming you have more than one).
Where you have the GPO management tools is entirely up to you. It should be on your DC by default, but you can add it in anywhere else you like. We have the AD Users & Computers and the GPO management tools on most of our tech PCs.
Have you checked out https://technet.microsoft.com/en-gb/. (v=ws.10).aspx
Classic shell is a 3rd party program that makes the windows 10 start menu look like the windows 7 one (or possibly even the xp one depending on your settings.)
So I thought I’d start with a simple one first. I’ve just been having a look through the settings in User Config>Admin Templates>Start Menu and Taskbar and I have enabled the setting ‘Remove and prevent access to the shutdown, Restart, Sleep and Hibernate commands’ but that policy does not seem to be working. I’ve set the policy in the OU in which our test PC is sat, and I’ve even done a gpupdate /force on the PC, to no avail. Have I missed something along the way maybe?
have you tried on a pc that the policy is applied to running rsop.msc from the run menu and see what it thinks its policies are (rsop dosent show everything but shows most non preferences settings if you want everything (any usually you dont need it) open up a command prompt and type gpresult /h c:\gpr.html (adjust file path to suit))
also be aware not ever gpo applies to every version of windows some only affect windows 2000 or 2000/xp or 8/10 and so on
also depending on how many policies you have it might be that another policy elsewhere trumps that one again rsop is your friend it shows you what settings are applied why and from where
Thanks to sted from:
Safety first, you probably shouldn’t be making changes to the default domain policy at all. If you get it badly wrong you can lock yourself out of the domain completely
Thanks to JJonas from:
Cool, I’ll check using rsop. I did clock that this particualr setting was supported on ‘at least’ Windows 2000 so presumed it should work. And no, I’ve not gone anywhere near the default domain policy 🙂
So, the results are showing that particular policy is not being applied :-/
I think I see your problem. You said you have the GPO in the OU with your test computer. But the setting is a user one.
Anything under «User Config» will only* apply to targeted users, and anything under «Computer Config» will apply to target computers.
So if you’re setting User Config settings you need to have the policy in the same OU as your user account (or a parent OU).
Sorry if I’m not explaining this very well.
*there are ways of changing this behavior, but don’t worry about them yet.
Thanks to Rob_D from:
Aaaaah, that makes complete sense! I think. So I’ve deleted the policy from it’s current location, and linked it to our OU called Teaching Staff (this is where our test staff account is sat, along with all other teachers). I’ll see if that does the trick.
Not wanting to be rude but see if there is a willing EduGeek nearby with half hour on their hands, buy a book or get on a course. GPO and AD is not something you want to just have a stab at.
I’m guessing GPO’s are already running so you have a central store? As Rob_D said you need to bear in mind User and Computer settings. Generally never mix them and in fact it is a good idea to disable the section not being used to speed up the GPO and prevent accidents.
If you have a test OU you could set that to Block Inheritance and they you could link the GPOs you want, one by one. Do the same with a test user OU.
I think I see your problem. You said you have the GPO in the OU with your test computer. But the setting is a user one.
Anything under «User Config» will only* apply to targeted users, and anything under «Computer Config» will apply to target computers.
So if you’re setting User Config settings you need to have the policy in the same OU as your user account (or a parent OU).
Sorry if I’m not explaining this very well.
*there are ways of changing this behavior, but don’t worry about them yet.
You my friend are a complete legend! That has done the trick. Now all I have left to do is get my head around configuring the tiles and start menu. It’s a very simple setup we have, there’s no network storage as we are a GAFE school. All PC’s just have office installed and google chrome. If possible, I’d like to try have the Office tiles only showing, and in the taskbar, and get rid of everything else.
Not wanting to be rude but see if there is a willing EduGeek nearby with half hour on their hands, buy a book or get on a course. GPO and AD is not something you want to just have a stab at.
I’m guessing GPO’s are already running so you have a central store? As Rob_D said you need to bear in mind User and Computer settings. Generally never mix them and in fact it is a good idea to disable the section not being used to speed up the GPO and prevent accidents.
If you have a test OU you could set that to Block Inheritance and they you could link the GPOs you want, one by one. Do the same with a test user OU.
No, we are an apple school. We don’t have any GPO’s currently and no central store. I completely get where you’re coming from but the situation here is quite unique in that, my network manager left recently. The current exec principal will not be promoting or employing another network manager. The school is in special measures and we have an exec principal who has decided to get rid of all things apple. As the school has no money, I have started to trade in our current apple kit in exchange for credit with a supplier, which we can then use to purchase PC’s. I have about 50 PC’s in stock now ready to roll out. We have also just learned that our current academy trust (whom our exec principal is director of) is to be handing us over to a new, very large Academy Trust. The process of due diligence is currently under way. This means that come September, we will be under a new Academy Trust, will be given a new name and have a new Principal. I have met with the IT guys from the new Trust, they came in to see our network setup. They are happy with our current setup on the server side, hardware wise, but when they come in September, they will be just wiping everything and ‘doing it their way’.
With all this going on, I am having to get rid of all apple kit while it still has value, and roll out the PC’s. learning as I go. No time (and probably no money) for going on a course. The great people on here have been fabulous with helping so far. I’m just wanting a basic setup that I can roll out that will put us on until we break up in around 6 weeks time. Because at that point, everything I have done will be undone by the network guys at the new Trust :-/ Mearly just trying to keep the school going for the next few weeks.
Oh, and there is only me and my technician. 12 months ago we were a team of four!
Sorry for the head mashing reply 🙂
Working with startup, shutdown, logon, and logoff scripts using the Local Group Policy Editor
This topic describes how to use the Local Group Policy Editor (gpedit) to manage four types of event-driven scripting files.
Introduction
Group Policy allows you to associate one or more scripting files with four triggered events:
You can use Windows PowerShell scripts, or author scripts in any other language supported by the client computer. Windows Script Host (WSH) supported languages are also used, including VBScript and Jscript. For more information about the editor, see Local Group Policy Editor.
Additional considerations
For more information about scripting, see the Group Policy Script Center (https://go.microsoft.com/fwlink/?LinkID=66013).
Local Group Policy Editor and the Resultant Set of Policy snap-in are available in Windows Server 2008 R2 and Windows 7 Professional, Windows 7 Ultimate, and Windows 7 Enterprise. For more information, see https://go.microsoft.com/fwlink/?LinkId=139815.
How to assign computer startup scripts
To assign computer startup scripts
Open the Local Group Policy Editor.
In the console tree, click Scripts (Startup/Shutdown). The path is Computer Configuration\Windows Settings\Scripts (Startup/Shutdown).
In the results pane, double-click Startup.
In the Startup Properties dialog box, click Add.
In the Add a Script dialog box, do the following:
In the Script Name box, type the path to the script, or click Browse to search for the script file in the Netlogon shared folder on the domain controller.
In the Script Parameters box, type any parameters that you want, the same way as you would type them on the command line. For example, if your script includes parameters called //logo (display banner) and //I (interactive mode), type //logo //I.
In the Startup Properties dialog box, specify the options that you want:
Startup Scripts for : Lists all the scripts that currently are assigned to the selected Group Policy object (GPO). If you assign multiple scripts, the scripts are processed in the order that you specify. To move a script up in the list, click it and then click Up. To move a script down in the list, click it and then click Down.
Add: Opens the Add a Script dialog box, where you can specify any additional scripts to use.
Edit: Opens the Edit Script dialog box, where you can modify script information, such as name and parameters.
Remove: Removes the selected script from the Startup Scripts list.
Show Files: Displays the script files that are stored in the selected GPO.
Additional considerations
To complete this procedure, you mustВ have Edit setting permission to edit a GPO. By default, members of the Domain Administrators security group, the Enterprise Administrators security group, or the Group Policy Creator Owners security groupВ have Edit setting permission to editВ a GPO.
Startup scripts are run under the Local System account, and they have the full rights that are associated with being able to run under the Local System account.
Beginning in WindowsВ Vista, startup scripts are run asynchronously, by default. This is a different behavior from earlier operating systems.
Setting startup scripts to run synchronously may cause the boot process to run slowly.
In WindowsВ 7 and WindowsВ Vista, startup scripts that are run asynchronously will not be visible. Enabling the Run Startup Scripts Visible policy setting will have no effect when running startup scripts asynchronously.
Local Group Policy Editor and the Resultant Set of Policy snap-in are available in Windows Server 2008 R2 and Windows 7 Professional, Windows 7 Ultimate, and Windows 7 Enterprise. For more information, see https://go.microsoft.com/fwlink/?LinkId=139815.
How to assign computer shutdown scripts
To assign computer shutdown scripts
Open the Local Group Policy Editor.
In the console tree, click Scripts (Startup/Shutdown). The path is Computer Configuration\Windows Settings\Scripts (Startup/Shutdown).
In the results pane, double-click Shutdown.
In the Shutdown Properties dialog box, click Add.
In the Add a Script dialog box, do the following:
In Script Name, type the path to the script, or click Browse to search for the script file in the Netlogon shared folder on the domain controller.
In Script Parameters, type any parameters that you want, the same way as you would type them on the command line. For example, if your script includes parameters called //logo (display banner) and //I (interactive mode), type //logo //I.
In the Shutdown Properties dialog box, specify the options that you want:
Shutdown Scripts for : Lists all the scripts that are currently assigned to the selected Group Policy object (GPO). If you assign multiple scripts, the scripts are processed in the order that you specify. To move a script up in the list, click it and then click Up. To move a script down in the list, click it and then click Down.
Add: Opens the Add a Script dialog box, where you can specify any additional scripts to use.
Edit: Opens the Edit Script dialog box, where you can modify script information, such as name and parameters.
Remove: Removes the selected script from the Shutdown Scripts list.
Show Files: Displays the script files that are stored in the selected GPO.
Additional considerations
To complete this procedure, you mustВ have Edit setting permission to edit a GPO. By default, members of the Domain Administrators security group, the Enterprise Administrators security group, or the Group Policy Creator Owners security groupВ have Edit setting permission to editВ a GPO.
Shutdown scripts are run as Local System, and they have the full rights that are associated with being able to run as Local System.
Setting shutdown scripts to run synchronously may cause the shutdown process to run slowly.
Local Group Policy Editor and the Resultant Set of Policy snap-in are available in Windows Server 2008 R2 and Windows 7 Professional, Windows 7 Ultimate, and Windows 7 Enterprise. For more information, see https://go.microsoft.com/fwlink/?LinkId=139815.
How to assign user logon scripts
To assign user logon scripts
Open the Local Group Policy Editor.
In the console tree, click Scripts (Logon/Logoff). The path is User Configuration\Windows Settings\Scripts (Logon/Logoff).
In the results pane, double-click Logon.
In the Logon Properties dialog box, click Add.
In the Add a Script dialog box, do the following:
In Script Name, type the path to the script, or click Browse to search for the script file in the Netlogon shared folder on the domain controller.
In Script Parameters, type any parameters that you want, the same way as you would type them on the command line. For example, if your script includes parameters called //logo (display banner) and //I (interactive mode), type //logo //I.
In the Logon Properties dialog box, specify the options that you want:
Logon Scripts for : Lists all the scripts that currently are assigned to the selected Group Policy object (GPO). If you assign multiple scripts, the scripts are processed in the order that you specify. To move a script up in the list, click it and then click Up. To move a script down in the list, click it and then click Down.
Add: Opens the Add a Script dialog box, where you can specify any additional scripts to use.
Edit: Opens the Edit Script dialog box, where you can modify script information, such as name and parameters.
Remove: Removes the selected script from the Logon Scripts list.
Show Files: Displays the script files that are stored in the selected GPO.
Additional considerations
To complete this procedure, you mustВ have Edit setting permission to edit a GPO. By default, members of the Domain Administrators security group, the Enterprise Administrators security group, or the Group Policy Creator Owners security groupВ have Edit setting permission to editВ a GPO.
Setting logon scripts to run synchronously may cause the logon process to run slowly.
Logon scripts are run as User, not Administrator, and their rights are limited accordingly.
Local Group Policy Editor and the Resultant Set of Policy snap-in are available in Windows Server 2008 R2 and Windows 7 Professional, Windows 7 Ultimate, and Windows 7 Enterprise. For more information, see https://go.microsoft.com/fwlink/?LinkId=139815.
How to assign user logoff scripts
To assign user logoff scripts
Open the Local Group Policy Editor.
In the console tree, click Scripts (Logon/Logoff). The path is User Configuration\Windows Settings\Scripts (Logon/Logoff).
In the results pane, double-click Logoff.
In the Logoff Properties dialog box, click Add.
In the Add a Script dialog box, do the following:
In Script Name, type the path to the script, or click Browse to search for the script file in the Netlogon shared folder on the domain controller.
In Script Parameters, type any parameters that you want, the same way as you would type them on the command line. For example, if your script includes parameters called //logo (display banner) and //I (interactive mode), type //logo //I.
In the Logoff Properties dialog box, specify the options the you want:
Logoff Scripts for : Lists all the scripts that currently are assigned to the selected Group Policy object (GPO). If you assign multiple scripts, the scripts are processed in the order that you specify. To move a script up in the list, click it and then click Up. To move a script down in the list, click it and then click Down.
Add: Opens the Add a Script dialog box, where you can specify any additional scripts to use.
Edit: Opens the Edit Script dialog box, where you can modify script information, such as name and parameters.
Remove: Removes the selected script from the Logoff Scripts list.
Show Files: Displays the script files that are stored in the selected GPO.
Additional considerations
To complete this procedure, you mustВ have Edit setting permission to edit a GPO. By default, members of the Domain Administrators security group, the Enterprise Administrators security group, or the Group Policy Creator Owners security groupВ have Edit setting permission to editВ a GPO.
Logoff scripts are run as User, not Administrator, and their rights are limited accordingly.
Setting logoff scripts to run synchronously may cause the logoff process to run slowly.
How to Set-Up Dummy Stations for Accessing Workstations?
I want to lock down (hopefully via GPO) some existing PC’s in our home office so that they can only be used to access to run the Amazon Workspaces app to access their Workspaces.
Any advice or documentation you can point me to on this topic? The machines/pc’s are newer with Windows 10, I’m pretty sure.
Traditional, Headless or Hybrid CMS: Which Is Best
5 Replies
Are they windows 10 pro?
We use an OS called Stratodesk and it is like a «Thin Client» that works really good for doing something like that. We use it for something other than Workspaces, but it should be similar to what you are trying to accomplish. If you contact them, they have free trial license you can try out and see if it will work out for you.
Are they windows 10 pro?
Basically your wanting to convert the win pc or laptops to thin clients
If there Dells they have the wyse converter
Hp has one as well
I have heard good thing about ThinScale
Basically your wanting to convert the win pc or laptops to thin clients
If there Dells they have the wyse converter
Hp has one as well
I have heard good thing about ThinScale
Thank you SO MUCH! Yeah these are HP machines. I’m looking into this. What’s the fastest route to get an idea of the cost to implement this? I contacted HP sales support and put a message in for a callback. I looked at a Youtube video on it, and it looks good so far.
Login or sign up to reply to this topic.
Didn’t find what you were looking for? Search the forums for similar questions or check out the Active Directory & GPO forum.
Read these next.
No Network Access
Hello,Suddenly, my Windows 2012R server has NO network access through either of its two nic cards; it is a DELL PE T430. It is configured to get IP info from DHCP, and that works ok; both NICs can get an IP just fine, but after I get the IP address, I am.
Understanding VPNs
Hello I’m trying to learn the concept of VPN’s and there’s some aspect of VPN’s I’m not sure about. When I configure a remote access VPN on a Fortigate, I configure the following client range 192.168.3.10-192.168.3.40When the client connects and I do a ro.
Snap! Outlook crashes, getting phished, supermoon, CyberOne, DALL·E 2 + SpiceRex
Spark! Pro series – 12th August 2022
I’ve got a UTM Firewall and I’m constantly getting notifications that someone is trying to gain access through an SSL-VPN. The attacking IP address is almost always different, so blocking the IP every time is not a sustainable solution. They haven’t got t.
Delegate Permissions for Group Policy
This topic describes procedures for an administrator to delegate permissions to others using the GPMC so that they can perform some Group Policy administrative tasks.
Introduction
With GPMC, the following tasks can be delegated:
Create GPOs in a domain.
Set permissions on a GPO.
Set policy-related permissions on site, domain or organizational unit.
Link GPOs to a given site, domain or organizational unit.
Perform Group Policy Modeling analyses on a given domain or organizational unit (but not on a site).
Read Group Policy Results data for objects in a given domain or organizational unit (but not on a site).
Create WMI filters in a domain.
Set permissions on a WMI filter.
GPMC simplifies delegation by managing the various ACEs required for a task as a single bundle of permissions for the task. If you want to see the ACL in detail, you can click the Advanced button on the Delegation tab. The underlying mechanism for achieving delegation is the application of the appropriate DACLs to GPOs and other objects in Active Directory. This mechanism is identical to using security groups to filter the application of GPOs to various users.
You can also specify Group Policy to control the behavior of MMC and MMC snap-ins. For example, you can use Group Policy to manage the rights to create, configure, and use MMC consoles, and to control access to individual snap-ins.
How to delegate permissions for a group or user on a Group Policy Object
To delegate permissions for a group or user on a Group Policy Object
In the Group Policy Management Console (GPMC) console tree, expand the Group Policy Objects node in the forest and domain containing the Group Policy object (GPO) for which you want to add or remove permissions.
In the results pane, click the Delegation tab.
Click Add.
In the Select User, Computer, or Group dialog box, click Object Types, select the types of objects for which you want to add GPO permissions, and then click OK.
Click Locations, select either Entire Directory or the domain or organizational unit containing the object for which you want to add GPO permissions, and then click OK.
In the Enter the object name to select box, type the name of the object for which you want to add GPO permissions by performing one of the following actions:
If you know the name, type it and then click OK.
To search for the name, click Advanced, type the search criteria, click Find Now, select the name in the list box, click OK, and then click OK again.
In the Permissions box of the Add Group or User dialog box, select the appropriate permissions from the drop-down list, and then click OK.
Additional considerations
To perform this procedure, you must have Edit settings, delete, and modify security permissions on the GPO.
Groups and users that have Custom in the Allowed Permissions column in the Groups and users list box on the Delegation tab have permissions that do not match one of the three standard levels of permissions. To view the permissions for groups with custom permissions or to set custom permissions, click Advanced.
You can also click the Delegation tab to change or remove permissions for a group or user on a GPO.
How to delegate permissions to link Group Policy Objects
To delegate permissions to link Group Policy Objects
In the Group Policy Management Console (GPMC) console tree, do one of the following:
To delegate permission to link Group Policy objects (GPOs) to either the domain or an organizational unit (OU), click the domain or the OU.
To delegate permission to link GPOs to a site, click the site.
In the results pane, click the Delegation tab.
In the Permission drop down-list box, select Link GPOs. Click Add.
In the Select User, Computer, or Group dialog box, click Object Types, select the types of objects to which you want to delegate permissions for the domain, site, or OU, and then click OK.
Click Locations, select either Entire Directory or the domain or OU containing the object to which you want to delegate permissions, and then click OK.
In the Enter the object name to select box, enter the name of the object to which you want to delegate permissions by doing one of the following:
If you know the name, type it and then click OK.
To search for the name, click Advanced, enter the search criteria, click Find Now, select the name in the list box, click OK, and then click OK again.
In the Add Group or User dialog box, in the Permissions drop-down list, select the level to which you want permissions to apply for this group or user, and then click OK.
Additional considerations
To delegate permissions to link GPOs to a site, domain, or OU, you must have Modify Permissions on that site, domain, or OU. By default, only Domain Administrators and Enterprise Administrators have this permission.
Users and groups with permission to link GPOs to a specific site, domain, or OU can link GPOs, change link order, and set block inheritance on that site, domain, or OU.
You cannot remove groups and users that inherit permissions from a parent container.
Some entries in the Groups and users drop-down list, such as System, do not have an associated property dialog box, so Properties is unavailable for these entries.
How to delegate permissions for generating Group Policy Modeling data
To delegate permissions for generating Group Policy Modeling data
In the Group Policy Management Console (GPMC) console tree, click the domain or organizational unit (OU) for which you want to delegate Group Policy Modeling permissions.
In the results pane, click the Delegation tab.
In the Permission box, select Perform Group Policy Modeling analyses to add a new group or user to the permissions list**.**
On the Delegation tab, click Add.
In the Select User, Computer, or Group dialog box, click Object Types, select the types of objects to which you want to delegate permissions for the domain, site, or OU, and then click OK.
Click Locations, select either Entire Directory or the domain or OU containing the object to which you want to delegate permissions, and then click OK.
In the Enter the object name to select box, find the name of the object to which you want to delegate permissions by doing one of the following:
If you know the name, type it, and then click OK again.
To search for the name, click Advanced, enter the search criteria, click Find Now, select the name in the drop-down list, click OK, and then click OK.
In the Add Group or User dialog box, in the Permissions drop-down list, select the level to which you want permissions to apply for this group or user, and then click OK.
Additional considerations
To delegate permissions to perform Group Policy Modeling analyses for objects in a domain or organizational unit, you must have Modify Permissions on that domain or organizational unit. By default, only domain administrators and enterprise administrators have this permission.
You cannot delegate permission to perform Group Policy Modeling analyses for sites.
You can also use the Delegation tab to change or remove permissions for a group or user for Group Policy Modeling data.
How to delegate permissions to generate Group Policy Results
To delegate permissions to generate Group Policy Results
In the Group Policy Management Console (GPMC) console tree, click the domain or organizational unit (OU) for which you want to delegate permission to generate Group Policy Results.
In the results pane, click the Delegation tab.
In the Permissions drop-down list, select Read Group Policy Results data to add a new group or user to the permissions list.
On the Delegation tab, click Add.
In the Select User, Computer, or Group dialog box, click Object Types, select the types of objects to which you want to delegate permissions for the domain, site, or OU, and then click OK.
Select the user or group to which permission should be delegated.
In the Add Group or User dialog box, in the Permissions drop-down list, select the level to which you want permissions to apply for this group or user, and then click OK.
Additional considerations
To delegate permissions to generate Group Policy Results for objects in a domain or OU, you must have Modify Permissions on that domain or OU. By default, only domain administrators and enterprise administrators have this permission.
You cannot delegate permission to generate Group Policy Results for sites.
You can also use the Delegation tab to change or remove permissions for a group or user for Group Policy Results data.
How to delegate permissions for a group or user on a WMI filter
To delegate permissions for a group or user on a WMI filter
In the Group Policy Management Console (GPMC) console tree, click the WMI filter for which you want to delegate permissions.
In the results pane, click the Delegation tab.
Click Add.
In the Select User, Computer, or Group dialog box, click Object Types, select the types of objects to which you want to delegate permissions on the WMI filter, and then click OK.
Click Locations, select either Entire Directory or the domain or organizational unit containing the object to which you want to delegate permissions, and then click OK.
In the Enter the object name to select box, type the name of the object to which you want to delegate permissions by doing one of the following:
If you know the name, type it and then click OK.
To search for the name, click Advanced, type the search criteria, click Find Now, select the name in the list box, click OK, and then click OK again.
In the Add Group or User dialog box, in the Permissions box, select the permissions level you want to assign to the group or user, and then click OK.
Additional considerations
You must have Full Control permissions on a WMI filter to change its permissions.
You cannot remove or change inherited permissions for WMI filters.
All users must have Read access to all WMI filters. Otherwise, Group Policy stops processing when it encounters a WMI filter that cannot be read.
You cannot use the GPMC to remove Read permissions from WMI filters.
WMI Filters are available if at least one domain controller in the domain is running Microsoft WindowsВ ServerВ 2003 or later.
You can also use the delegation tab to change or remove permissions for a group or user for WMI filters.
How to delegate permissions for a Group or User on a Starter GPO
Delegating permissions for a Group or User on a Starter GPO
Open the Group Policy Management Console. Expand the Starter GPOs node.
Click the Starter GPO you want to delegate.
In the results pane, click the Delegation tab.
Click Add.
In the Select User, Computer, or Group dialog box, click Object Types, select the types of objects for which you want to add Starter GPO permissions, and then click OK.
Click Locations, select either Entire Directory or the domain or organizational unit containing the object for which you want to add Starter GPO permissions, and then click OK.
In the Enter the object name to select box, type the name of the object for which you want to add Starter GPO permissions by performing one of the following actions:
If you know the name, type it and then click OK.
To search for the name, click Advanced, type the search criteria, click Find Now, select the name in the list box, click OK, and then click OK again.
In the Permissions box of the Add Group or User dialog box, select the appropriate permissions from the drop-down list, and then click OK.
Сетевые заметки системного администратора
Режим обработки замыкания групповой политики (Loopback Policy Processing)
Пара статей как это работает.
ОБЪЯСНЕНИЕ 1
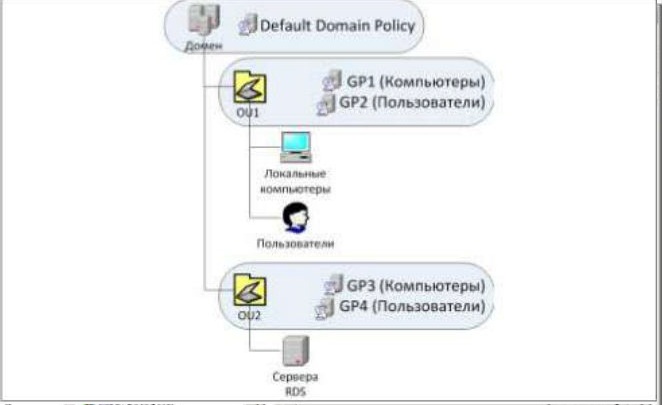
Например, на рис. 5 изображен домен с двумя организационными подразделениями — OU1 и OU2.
В первом находятся объекты учетных записей пользователей и их локальные компьютеры, во втором — объекты серверов RDS.
Если пользователь осуществляет вход в систему на локальном компьютере, то он оказывается под действием доменной групповой политики (Default domain policy), затем политики GP1 локального компьютера (которая была применена при его включении) и политики GP2 пользователя (примененной при входе в систему).
Если пользователь осуществляет вход на сервер RDS, то будут действовать доменная политика, политика сервера GP3 и политика пользователя GP2.
Если же включить Loopback Policy Processing, то при входе на сервер RDS будут действовать доменная политика, политика сервера GP3 и политика пользователя GP2+GP4 (в режиме Merge) или только GP4 (в режиме Replace).
При возникновении любых конфликтов настроек между политиками OU пользователя и OU сервера в режиме Merge политика в OU сервера будет иметь более высокий приоритет.
Используя несколько серверов RDS в кластере, просто необходимо управлять пользовательскими профилями. К счастью, для этого есть достаточно много возможностей со своими сильными и слабыми сторонами. Остается только выбрать то сочетание, которое лучше всего будет подходить для каждого конкретного случая.
( взято тут: http://www.xnets.ru/plugins/content/content.php?content.240.4 )
ОБЪЯСНЕНИЕ 2
Когда GPO линкуется к какому-то OU, то по умолчанию политики из раздела Computer Configuration данной GPO применяются ко всем компьютерным объектам внутри этого OU (и его подконтейнеров), а политики из раздела User Configuration применяются ко всем пользовательским объектам внутри этого OU (и его подконтейнеров).
Если вы прилинкуете GPO к OU, в котором лежат только компьютерные объекты, и в этом GPO укажете какие-то настройки в разделе User Configuration, то по умолчанию эти пользовательские настройки будут проигнорированы и никем не будут использоваться (т.к. я уже указал выше, что по умолчанию к компьютерным объектам применяются только настройки из Computer Configuration).
Так вот, чтобы к пользователям, которые логинятся на какие-то машины, применялись пользовательские настройки (раздел User Configuration) из GPO, которая прилинкована к компьютерному объекту, и включается «User Group Policy Loopback processing mode».
При этом в режиме Replace пользовательские настройки (User Configuration) из других GPO, назначенных на пользовательский объект, будут отменены и будут действовать только пользовательские настройки (User Configuration) из GPO, назначенного на компьютерный объект, куда логинится пользователь.
А в режиме Merge эти настройки совместятся (ранее назначенные сохранятся, новые добавятся, конфликтующие перезапишутся). Т.е. частично у пользователя останутся настройки, назначенные на самого пользователя через другие GPO, плюс добавятся пользовательские настройки (User Configuration) из GPO, назначенного на компьбютер.
Но нужно понимать, что хоть в этом случае меняются пользовательские настройки, но сам GPO назначается всё же на компьютерный объект. И при настройке линковки Security Filtering про это не нужно забывать.
Если вы для GPO, прилинкованному к OU, настраиваете Security Filtering, тогда политики из этого GPO применяются не ко всем объектам внутри данного OU, а только к тем, которые указаны в фильтре безопасности прямо или косвенно (через группы).
Чтобы данный GPO применился к какому-то объекту, этот объект:
а) должен быть внутри OU, к которому прилинкован GPO;
б) должен подпадать под указанный фильтр безопасности (с правами: read group policy + apply group policy).
В Security Filter нет смысла включать объекты, которые не содержатся внутри OU, к которому вы линкуете GPO, — политики к таким объектам всё равно не применятся.
А вы же в своём описании:
1) Создаёте OU, переносите в него компьютерные объекты терминальных серверов.
2) Создаёте GPO и линкуете его к этому OU.
3) Для GPO указываете Security Filter, в который включаете не только терминальные серверы (которые находятся в этом OU), но ещё зачем-то и пользователей (которые находятся за пределами данного OU).
Во-первых, нет смысла вообще делать Security Filtering, если вы и так терминальные серверы вынесли в отдельный OU. Просто линкуете GPO к этому OU с терминальными серверами (например: ou=terminal servers,ou=servers,dc=example,dc=org) без всякой фильтрации и всё.
Во-вторых, если и не выносить терминальные серверы в отдельный OU, а оставить их, например, в контейнере со всеми прочими серверами (ou=servers,dc=example,dc=org), то тогда можно использовать Security Filtering, но только в этот фильтр нужно добавлять никак не пользователей, а только терминальные серверы, которые содержатся в прилинкованном OU. Например создать domain local security-группу с именем TerminalServers, в неё включить компьютерныеобъекты всех терминальных серверов, находящихся в контейнере Setrvers. И уже эту группу добавлять в Security Filtering, убирая оттуда Authenticated Users.
Итого, как было правильно реализовать задуманное вами:
Вариант 1 (с созданием отдельного OU для терминальных серверов).
1. Создаёте отдельный подконтейнер для ТС: ou=terminal servers,ou=servers,dc=example,dc=org
2. В этот контейнер перемещаете компьютерные объекты всех терминальных серверов.
3. Создаёте GPO, например, TermSrv_Minimal_UserConf.
4. В настройках GPO TermSrv_Minimal_UserConf:
— в разделе User Configuration: задаёте нужные вам разрешения для пользователя.
— в разделе Computer Configuration включаете «User Group Policy Loopback processing mode» в режим Merge (или Replace).
5. Линкуете GPO TermSrv_Minimal_UserConf к OU, в котором находятся терм.серверы, т.е. к ou=terminal servers,ou=servers,dc=example,dc=org
6. Настройки безопасности GPO оставляете по умолчанию, т.е. Authenticated Users: Read+apply group policy.
Вариант 2 (без создания отдельного OU для терминальных серверов).
1. Терминальные серверы лежат в одном OU с прочими компьюьерными объектами (например, в ou=servers,dc=example,dc=org).
2. Создаёте доменную группу, например, TermServers (domain local, security), включаете в неё все терминальные серверы (комп. объекты).
3. Создаёте GPO, например, TermSrv_Minimal_UserConf.
4. В настройках GPO TermSrv_Minimal_UserConf:
— в разделе User Configuration: задаёте нужные вам разрешения для пользователя.
— в разделе Computer Configuration включаете «User Group Policy Loopback processing mode» в режим Merge (или Replace).
5. Линкуете GPO TermSrv_Minimal_UserConf к OU, в котором находятся терм.серверы (и не только), т.е. к ou=servers,dc=example,dc=org
6. Настраиваете для этого GPO Security Filtering: удаляете Authenticated User, добавляете созданную вами ранее группу TermServers (с правами по умолчанию: Read+apply group policy).
Вот и всё. При этом:
а) Если юзеры будут логиниться на свою рабочцю станцию и на какие-то прочие нетерминальные серверы (куда им разрешено), то к ним будут применяться пользовательские настройки из GPO, назначенных на их пользовательскую учётку (в частности из Default Domain Policy И прочих, созданных вами).
б) Если юзеры будут логиниться на терминальные серверы, то к ним сначала, как обычно, будут применяться пользовательские настройки из GPO, назначенных на их пользовательскую учётку, а потом сразу же поверх них будут накатываться пользовательские настройки из GPO TermSrv_Minimal_UserConf, прилинкованного к контейнеру с терминальными серверами, путём полной замены (Replace) или дополнения с перезаписью конфликтных значений (Merge).
Лепить непонятный винегрет, когда и отдельный OU и Security Filtering, да ещё и в группу для фильтрации добавлены и пользователи и компьютеры — это явный бред, который происходит от непонимания того, как это всё работает.
Нет похожих постов.
Источники информации:
- http://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/dn789190(v=ws.11)
- http://community.spiceworks.com/topic/2329814-how-to-set-up-dummy-stations-for-accessing-workstations
- http://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/dn789195(v=ws.11)
- http://msbro.ru/index.php/archives/5463