How to use proxy
How to use proxy
What is a Proxy Server? How does it work?
Proxy Server Definition
A proxy server is a system or router that provides a gateway between users and the internet. Therefore, it helps prevent cyber attackers from entering a private network. It is a server, referred to as an “intermediary” because it goes between end-users and the web pages they visit online.
When a computer connects to the internet, it uses an IP address. This is similar to your home’s street address, telling incoming data where to go and marking outgoing data with a return address for other devices to authenticate. A proxy server is essentially a computer on the internet that has an IP address of its own.
Proxy Servers and Network Security
Proxies provide a valuable layer of security for your computer. They can be set up as web filters or firewalls, protecting your computer from internet threats like malware.
This extra security is also valuable when coupled with a secure web gateway or other email security products. This way, you can filter traffic according to its level of safety or how much traffic your network—or individual computers—can handle.
How to use a proxy? Some people use proxies for personal purposes, such as hiding their location while watching movies online, for example. For a company, however, they can be used to accomplish several key tasks such as:
How a Proxy Works
Because a proxy server has its own IP address, it acts as a go-between for a computer and the internet. Your computer knows this address, and when you send a request on the internet, it is routed to the proxy, which then gets the response from the web server and forwards the data from the page to your computer’s browser, like Chrome, Safari, Firefox, or Microsoft Edge
How to Get a Proxy
There are hardware and software versions. Hardware connections sit between your network and the internet, where they get, send, and forward data from the web. Software proxies are typically hosted by a provider or reside in the cloud. You download and install an application on your computer that facilitates interaction with the proxy.
Often, a software proxy can be obtained for a monthly fee. Sometimes, they are free. The free versions tend to offer users fewer addresses and may only cover a few devices, while the paid proxies can meet the demands of a business with many devices.
How Is the Server Set Up?
To get started with a proxy server, you have to configure it in your computer, device, or network. Each operating system has its own setup procedures, so check the steps required for your computer or network.
In most cases, however, setup means using an automatic configuration script. If you want to do it manually, there will be options to enter the IP address and the appropriate port.
How Does the Proxy Protect Computer Privacy and Data?
A proxy server performs the function of a firewall and filter. The end-user or a network administrator can choose a proxy designed to protect data and privacy. This examines the data going in and out of your computer or network. It then applies rules to prevent you from having to expose your digital address to the world. Only the proxy’s IP address is seen by hackers or other bad actors. Without your personal IP address, people on the internet do not have direct access to your personal data, schedules, apps, or files.
With it in place, web requests go to the proxy, which then reaches out and gets what you want from the internet. If the server has encryption capabilities, passwords and other personal data get an extra tier of protection.
Can Zero Trust Network Access (ZTNA) Replace VPN and Proxy Server?
Benefits of a Proxy Server
Proxies come with several benefits that can give your business an advantage:
Types of Proxy Servers
While all proxy servers give users an alternate address with which to use the internet, there are several different kinds—each with its own features.
Forward Proxy
A forward proxy sits in front of clients and is used to get data to groups of users within an internal network. When a request is sent, the proxy server examines it to decide whether it should proceed with making a connection.
A forward proxy is best suited for internal networks that need a single point of entry. It provides IP address security for those in the network and allows for straightforward administrative control. However, a forward proxy may limit an organization’s ability to cater to the needs of individual end-users.
Transparent Proxy
A transparent proxy can give users an experience identical to what they would have if they were using their home computer. In that way, it is “transparent.” They can also be “forced” on users, meaning they are connected without knowing it.
Transparent proxies are well-suited for companies that want to make use of a proxy without making employees aware they are using one. It carries the advantage of providing a seamless user experience. On the other hand, transparent proxies are more susceptible to certain security threats, such as SYN-flood denial-of-service attacks.
Anonymous Proxy
An anonymous proxy focuses on making internet activity untraceable. It works by accessing the internet on behalf of the user while hiding their identity and computer information.
A transparent proxy is best suited for users who want to have full anonymity while accessing the internet. While transparent proxies provide some of the best identity protection possible, they are not without drawbacks. Many view the use of transparent proxies as underhanded, and users sometimes face pushback or discrimination as a result.
High Anonymity Proxy
A high anonymity proxy is an anonymous proxy that takes anonymity one step further. It works by erasing your information before the proxy attempts to connect to the target site.
The server is best suited for users for whom anonymity is an absolute necessity, such as employees who do not want their activity traced back to the organization. On the downside, some of them, particularly the free ones, are decoys set up to trap users in order to access their personal information or data.
Distorting Proxy
A distorting proxy identifies itself as a proxy to a website but hides its own identity. It does this by changing its IP address to an incorrect one.
Distorting proxies are a good choice for people who want to hide their location while accessing the internet. This type of proxy can make it look like you are browsing from a specific country and give you the advantage of hiding not just your identity but that of the proxy, too. This means even if you are associated with the proxy, your identity is still secure. However, some websites automatically block distorting proxies, which could keep an end-user from accessing sites they need.
Data Center Proxy
Data center proxies are not affiliated with an internet service provider (ISP) but are provided by another corporation through a data center. The proxy server exists in a physical data center, and the user’s requests are routed through that server.
Data center proxies are a good choice for people who need quick response times and an inexpensive solution. They are therefore a good choice for people who need to gather intelligence on a person or organization very quickly. They carry the benefit of giving users the power to swiftly and inexpensively harvest data. On the other hand, they do not offer the highest level of anonymity, which may put users’ information or identity at risk.
Residential Proxy
A residential proxy gives you an IP address that belongs to a specific, physical device. All requests are then channeled through that device.
Residential proxies are well-suited for users who need to verify the ads that go on their website, so you can block cookies, suspicious or unwanted ads from competitors or bad actors. Residential proxies are more trustworthy than other proxy options. However, they often cost more money to use, so users should carefully analyze whether the benefits are worth the extra investment.
Public Proxy
A public proxy is accessible by anyone free of charge. It works by giving users access to its IP address, hiding their identity as they visit sites.
Public proxies are best suited for users for whom cost is a major concern and security and speed are not. Although they are free and easily accessible, they are often slow because they get bogged down with free users. When you use a public proxy, you also run an increased risk of having your information accessed by others on the internet.
Shared Proxy
Shared proxies are used by more than one user at once. They give you access to an IP address that may be shared by other people, and then you can surf the internet while appearing to browse from a location of your choice.
Shared proxies are a solid option for people who do not have a lot of money to spend and do not necessarily need a fast connection. The main advantage of a shared proxy is its low cost. Because they are shared by others, you may get blamed for someone else’s bad decisions, which could get you banned from a site.
SSL Proxy
A secure sockets layer (SSL) proxy provides decryption between the client and the server. As the data is encrypted in both directions, the proxy hides its existence from both the client and the server.
These proxies are best suited for organizations that need enhanced protection against threats that the SSL protocol reveals and stops. Because Google prefers servers that use SSL, an SSL proxy, when used in connection with a website, may help its search engine ranking. On the downside, content encrypted on an SSL proxy cannot be cached, so when visiting websites multiple times, you may experience slower performance than you would otherwise.
Rotating Proxy
A rotating proxy assigns a different IP address to each user that connects to it. As users connect, they are given an address that is unique from the device that connected before it.
Rotating proxies are ideal for users who need to do a lot of high-volume, continuous web scraping. They allow you to return to the same website again and again anonymously. However, you have to be careful when choosing rotating proxy services. Some of them contain public or shared proxies that could expose your data.
Reverse Proxy
Unlike a forward proxy, which sits in front of clients, a reverse proxy is positioned in front of web servers and forwards requests from a browser to the web servers. It works by intercepting requests from the user at the network edge of the web server. It then sends the requests to and receives replies from the origin server.
Reverse proxies are a strong option for popular websites that need to balance the load of many incoming requests. They can help an organization reduce bandwidth load because they act like another web server managing incoming requests. The downside is reverse proxies can potentially expose the HTTP server architecture if an attacker is able to penetrate it. This means network administrators may have to beef up or reposition their firewall if they are using a reverse proxy.
Proxy Server vs. VPN
On the surface, proxy servers and virtual private networks (VPNs) may seem interchangeable because they both route requests and responses through an external server. Both also allow you to access websites that would otherwise block the country you’re physically located in. However, VPNs provide better protection against hackers because they encrypt all traffic.
Choosing VPN or Proxy
If you need to constantly access the internet to send and receive data that should be encrypted or if your company has to reveal data you must hide from hackers and corporate spies, a VPN would be a better choice.
If an organization merely needs to allow its users to browse the internet anonymously, a proxy server may do the trick. This is the better solution if you simply want to know which websites team members are using or you want to make sure they have access to sites that block users from your country.
A VPN is better suited for business use because users usually need secure data transmission in both directions. Company information and personnel data can be very valuable in the wrong hands, and a VPN provides the encryption you need to keep it protected. For personal use where a breach would only affect you, a single user, a proxy server may be an adequate choice. You can also use both technologies simultaneously, particularly if you want to limit the websites that users within your network visit while also encrypting their communications.
How Fortinet Can Help?
FortiProxy is a secure web proxy that protects employees against internet-borne attacks by incorporating multiple detection techniques such as web filtering, DNS filtering, data loss prevention, antivirus, intrusion prevention, and advanced threat protection. FortiProxy helps to reduce bandwidth demands and optimize the network with content and video caching.
FortiGate has the capability of both proxies and VPNs. It shields users from data breaches that often happen with high-speed traffic and uses IPsec and SSL to enhance security. FortiGate also harnesses the power of the FortiASIC hardware accelerator to enhance performance without compromising privacy. Secure your network with FortiGate VPN and proxy capabilities. Contact us to learn more.
What is a proxy server?
A proxy server is a system or router that provides a gateway between users and the internet. Therefore, it helps prevent cyber attackers from entering a private network.
How does a proxy server work?
Because a proxy server has its own IP address, it acts as a go-between for a computer and the internet. Your computer knows this address, and when you send a request on the internet, it is routed to the proxy, which then gets the response from the web server and forwards the data from the page to your computer’s browser, like Chrome, Safari, Firefox, or Microsoft Edge.
Proxy server vs. VPN?
On the surface, proxy servers and virtual private networks (VPNs) may seem interchangeable because they both route requests and responses through an external server. Both also allow you to access websites that would otherwise block the country you’re physically located in. However, VPNs provide better protection against hackers because they encrypt all traffic.
What are the benefits of a proxy server?
The benefits of a proxy server include enhanced security, private browsing, watching, and listening, access to location-specific content, and preventing employee from browsing inappropriate or distracting sites.
What is a proxy, why do we need one and how do we use it?
Today let’s talk about what a proxy server is, why we need one, and how to use it. We’ll show you how IP addresses work using examples and tell you how to avoid IP leaks.
To understand why we need a proxy and how it works, let’s dive into theory.
Theory: how do we see information on the web and what does a proxy have to do with it?
When we open a Web page, the device sends a request transmitting its data. Thanks to that data, the site knows which device to show the content of the page to: your phone, not your neighbor’s. And it shows it: it transmits information about itself. This text, pictures, videos and so on. So we see the content of the entire site.
The device sends data by which you can tell:
Among this data is the IP address. It allows us to know where we live.
If a site is blocked in a certain region, the device will not receive information about the web page, because there is a restriction on the IP-address. A proxy is just a way to bypass this restriction.
What is a proxy
A proxy is a server that you connect to to change your IP address. The way it works is this:
The web page sees the U.S. ipi, so it delivers information without any problems.
In some cases, users build IP chains. This makes it even harder to discover the real address, but you don’t need chains for surfing the Internet or forking. They are built by hackers.
The most popular types of intermediate servers are HTTPS and Socks. “Socks” are considered more anonymous by default because they use actual encryption technology, unlike HTTPS.
A distinction is made between IPv4 and IPv6 proxies. For 2021, IPv4 is the most popular. Once a long time ago was planned a global move to IPv6, but it never happened, all sites remain on the “four”. “Six” is supported by very few sites, so this protocol is cheap – 10 ₽ per IP. In the next 5 years IPv4 will not give way to IPv6, so feel free to buy “four”.
How to use it
A proxy server connects in:
Let’s consider each option in more detail.
In the computer/phone
When you set up an intermediate server in the system of the device, then the work of the proxy applies to all programs, games and browsers in general. But not always.
For example, the IP for Mozilla Firefox is connected separately, right in the browser. The same is true for Safari: a proxy will not work in this browser if you connect it in the Mac OS system.
In the browser
There are two options here: the IP can be connected in the browser settings or you can use a special plug-in. Plugins are more convenient, because they allow you to load several intermediate servers and switch between them in one click, delete unwanted addresses in one second, name the IP in a certain way to make it easy to navigate in them.
We advise you to use the ProxyControl extension. It loads IP addresses in two ways: with a special API key or individually, as you prefer.
In the messenger/program/game system
In this case, IP is set up directly where you are sitting. For example, if you want to enter Instagram through a proxy, you set it up there. Or if you want to speed up the process of collecting the semantic core, you can connect the intermediate server directly in the program.
In a special application
Special applications are like Proxifier. They are used to work through a proxy in a program that does not support its configuration. For example, if you need to enter “Vyber” from your computer through a proxy, first you connect the IP in Proxifier, and then open the messenger.
There are paid and free software. Which one you choose depends on your tasks.
How not to leak IP-addresses
If you connect only an intermediate server, the real IP will still be visible. It will leak via WebRTC. So disable this option in your browser.
How to do it. Type “How to disable WebRTC in” in the search box and paste the name of your browser. The Internet will give you several ways, choose any.
Disabling WebRTC along with a proxy completely hides your IP address.
Paid or free proxies: which one to choose?
Choose paid IPs. Both paid and free intermediate servers will hide your address, but free ones are less useful. They are used by 5-10 people at once, that’s why:
In addition, many sites have added free IPs to the blacklist and therefore immediately see the use of proxies. For example, a user decided to download the sixth book from an online library where the download limit is 5 per day. The user connected a free IP and tried to download the book, but the site gave an error because the IP is in the blacklist.
This is not going to happen with paid intermediate servers. They are protected by username and password, so they use only you. Internet does not stutter, pages are loaded quickly. IPs are stable, they do not change every 5 minutes.
Conclusion
We have understood what a proxy server is, why it is needed and how to use it. The most anonymous protocol is Socks. Most of the time IPv4 is used because very few web-sites support IPv6. IP-address can be set on your device, in a browser, program or special software. It depends on your task and where you like it best.
Что такое прокси и зачем он нужен и как им пользоваться
Сегодня поговорим о том, что такое прокси-сервер, зачем он нужен и как им пользоваться. Разберём работу IP-адресов на примерах и расскажем, как не допустить утечки айпи.
Чтобы понять, зачем нужен прокси и как он работает, нырнём в теорию.
Теория: как мы видим информацию в Сети и причём тут прокси
Когда открываем веб-страницу, то устройство отправляет запрос, передавая свои данные. Благодаря этим данным сайт понимает, какому именно устройству показывать содержимое страницы – именно вашему телефону, а не соседа. И показывает: передаёт информацию о себе. Это текст, картинки, видео и так далее. Так мы видим содержимое всего сайта.
Устройство отправляет данные, по которым можно сказать:
Среди таких данных и айпи-адрес. Он позволяет узнать, где мы живём.
Если сайт заблокирован в определённом регионе, то устройство не получит информацию о веб-странице, потому что есть ограничение по IP-адресу. Прокси как раз помогает обойти это ограничение.
Что такое прокси
Прокси – это сервер, к которому вы подключаетесь, чтобы изменить свой айпи-адрес. Работает это так:
При этом веб-страница видит айпи США, поэтому без проблем доставляет информацию.
В некоторых случаях пользователи выстраивают цепочки IP. Так раскрыть реальный адрес ещё сложнее, но для сёрфинга в интернете или вилкования цепочки не нужны. Их выстраивают хакеры.
Самые популярные типы промежуточных серверов – HTTPS и Socks. “Соксы” по умолчанию считаются более анонимными, потому что используют актуальные технологии шифрования, в отличие от HTTPS.
Различают IPv4 и IPv6 прокси. На 2021 год самые популярные IPv4. Когда-то давно планировался глобальный переход на протокол IPv6, но этого так и не произошло, все сайты остались на “четвёрке”. “Шестёрку” поддерживает очень мало сайтов, поэтому этот протокол стоит дёшево – 10 ₽ за один айпи. В ближайшие 5 лет IPv4 не уступит позиций IPv6, поэтому спокойно покупайте “четвёрку”.
Как им пользоваться
Прокси-сервер подключается в:
Рассмотрим каждый из вариантов подробнее.
В компьютере/телефоне
Когда настраиваете промежуточный сервер в системе устройства, то работа прокси распространяется вообще на все программы, игры и браузеры. Но не всегда.
Например, IP для Mozilla Firefox подключается отдельно, прямо в браузере. То же самое и с Safari: прокси в этом браузере не будет работать, если подключите его в системе Mac OS.
В браузере
Здесь два варианта: айпи подключается в настройках браузера либо с помощью специального расширения. Плагины удобнее, потому что позволяют загружать несколько промежуточных серверов и переключаться между ними в один клик, в одну секунду удалять ненужные адреса, называть айпи определённым образом, чтобы было удобно ориентироваться в них.
Советуем использовать расширение ProxyControl. В нём загружаете IP-адреса двумя способами: с помощью специального API-ключа или же каждый адрес по отдельности, как удобнее.
В системе мессенджера/программы/игры
В этом случае IP настраивается непосредственно там, где вы сидите. Например, хотите зайти в “Инстаграм” через прокси – там его и настраиваете. Или намереваетесь ускорить процесс сбора семантического ядра – подключаете промежуточный сервер прямо в программе.
В специальном приложении
Специальные приложения – это софты типа Proxifier. Их используют для того, чтобы работать через прокси в программе, которая не поддерживает его настройку. Например, если вам нужно зайти в “Вайбер” с компьютера через прокси, то сначала подключается айпи в Proxifier, а уже потом открывается мессенджер.
Есть платные, есть бесплатные софты. Какой выбрать, зависит от ваших задач.
Как не допустить утечки IP-адреса
Если подключить только промежуточный сервер, то настоящий айпи всё равно будет виден. Произойдёт его утечка через WebRTC. Поэтому отключите этот параметр в браузере.
Как это сделать. Наберите в поисковой строке “Как отключить WebRTC в” и вставьте название вашего браузера. Интернет выдаст вам несколько способов, выберите любой.
Отключение параметра WebRTC вместе с прокси полностью скрывает IP-адрес.
Платные или бесплатные прокси: какие выбрать?
Выбирайте платные айпи. Как платные, так и бесплатные промежуточные серверы скроют ваш адрес, но от бесплатных толку меньше. Ими пользуется 5-10 человек сразу, поэтому:
Кроме того, многие сайты добавили бесплатные IP в чёрный список и поэтому сразу видят использование прокси. Например, пользователь решил скачать шестую книгу из онлайн-библиотеки, где лимит на скачивание – 5 штук в день. Юзер подключил бесплатный айпи и попробовал загрузить книгу, но сайт выдал ошибку, потому что IP находится в блэклисте.
С платными промежуточными серверами такого не будет. Они защищены логином и паролем, поэтому ими пользуетесь только вы. Интернет не тупит, страницы грузятся быстро. Айпи работают стабильно, их не меняют каждые 5 минут.
Заключение
Мы разобрались, что такое прокси-сервер, зачем он нужен и как им пользоваться. Самым анонимным протоколом считается Socks. Чаще всего используют IPv4, потому что IPv6 поддерживают очень мало сайтов. Айпи-адрес настраивается в системе устройства, в браузере, программе или в специальном софте. Зависит от вашей задачи и от того, где вам больше нравится.
How to Use a Proxy
Clon Browser is a foreign antidetect browser for multi-accounting
Anonymous (antidetect) browsers are necessary to hide PC footprints and parameters. For example, if for attracting visitors to another web-site such platforms as Facebook, Yandex or Google Ads are used, you might be banned when launching ads from several accounts from browsers such as Firefox or Chrome if settings are incorrect. Or when you have more than three accounts in a social network for product advertisement: without a proxy or antidetect browser such accounts can be blocked because of the same IP-address.
Clow Browser is a product by a small team of Singapore developers. As they declare on project’s official web-site, “profile setup in ClonBrowser creates individual environment for information view and search”. To use ClonBrowser, it is recommended to have translator at hand unless you speak English. Translation into Russian is available, but it is incomplete, so far. They promise to fix the situation in future updates.
What XRumer is and which proxies should be chosen to work with it in 2022
Xrumer is a powerful tool for spam which is able to independently register accounts on web-sites, to bypass captures and protections from automatic registrations and publications.
The principle tasks which are resolved using Xrumer:
Traffic Arbitrage: What to Start With in 2022
So, you know what traffic arbitrage is and what people do in it. You know that it isn’t a scam. And you decide to try it. This article will be your step-by-step guide. Use it as a manual: to do such things, to consider these ones, etc.
We can talk about arbitrage for so long, but you should keep in mind that no article will become a full guide for you. You need to constantly find new information, analyze it and compare, especially when reading cases: if they were published two-three years ago or even a year ago, they aren’t actual.
So let’s explore what you need to do to become an arbitrageur. Let’s dive in!

Functionality
Mr. Denis’ browser enables users to work in a team and set roles of team members. Also, the following traffic sources are available:
Proxies for TikTok: why you need it, how to use it and which ones are suitable
According to data on 1st July 2021, TikTok is used by 689 million people monthly; therefore, there is a sense to make ads on this social media. The main audience of this network are girls and women; hence, amulets and weight loss products will go with a bang.
To avoid bans on TikTok, you should use proxies. In this article, we’ll tell you all you need to know about them and where you can buy IP addresses.
Why You Need Proxies for TikTok + Where You Can Buy Them
Proxies for TikTok are used in order to cheat an antifraud system, as TikTok is a lot like Facebook when it comes to bans – it blocks all things. Especially when we talk about multi-accounting. And it doesn’t matter whether you’re doing mass following or just farming accounts – if you have several profiles, TikTok bans all of them immediately. This is because profiles with the same IP are suspected in a network of accounts while such a network is useless for a normal user.
In our busy world, you can often see multi-accounting or, in other words, managing several on a single website concurrently. Sometimes users turn to using multiple browsers or devices for work.
GoLogin service has changed the concept of multi-accounting because it enabled its users to make their switches from one account to another easier. Now you needn’t type new data for switching or open one more browser window.
Such an antidetect browser came out in 2019 and is available now. First, developers considered GoLogin as an addon for Orbita Browser, but eventually, we know it as an independent antidetect.
What is the Difference Between IPv4 and IPv6 Proxies

How Does IPv4 Work
This protocol uses NAT technology that means Network Address Translation. Its essence is that each device receives its own IP address by website systems that see only one address. It’s the main disadvantage of this technology. For example, several users from a corporate network wanted to visit one web source. Their network works via IPv4 and translates only one public address. Employees have their own IPs only inside such a corporate network. Therefore, the server sees multiple concurrent requests and considers it a DDoS attack.
Web Scraping – What It is and What You Need It
Goods catalog, sports statistics, offers costs… You’ve probably heard about it, right? These and other data are collected by using special software or manually in docs. In such docs information is structured; there’s no need to puzzle out what and where.
If you’re interested in such a method of collecting and processing data, you should consider web-scraping.
What is Web Scraping and How Does It Work?
Web Scraping is data collection using special software. It means that you do it automatically. You should only launch a program and add on it URLs of web pages you need to scrape. Also, you need to add to the soft numbers, dates, and some information blocks you need to collect. Such a program will open mentioned websites and copy in a file all data that it finds. It can be a CSV file or an Excel table.
AdsPower – antidetect browser from Hong Kong programmers
Antidetect browsers help traffic arbitrageurs to get traffic without bans. In 2021, there are a lot of such browsers. Today we’ll talk about one of them created by programmers from Hong Kong. We are pleased to present you with AdsPower! In this article, we’ll tell you about its functionality, the process of registration, and configuring a proxy in it.
Functionality
Now we’ll tell you about what you can do in AdsPower.
The scope of work is evolving rapidly. But it challenges standards and users have to conform to them to work successfully and stay competitive. And our talking is not about time or money, but about less obvious things – multitasking and anonymity.
Multitasking is the capability to do several things concurrently. In our case it relates to the number of registering or working accounts. If more accounts run simultaneously – then more tasks are performed, and thus there are more benefits. Therefore you keep yourself competitive working with more clients. So we can’t underestimate the importance of multitasking in working on the Internet.
Anonymous is the capability to hide yourself on the Internet. In our case it relates to profiles. If your anonymity is more – then convenience to register accounts increases and the probability of their ban decreases. In other words, anonymity helps you to save sources for working.
Working on the Internet includes the range of directions from register and promotion accounts in social media to working with bulletin boards, betting shops, advertisements and even marketing. And in all these directions you have to be multitasked and have multithreading.
How To Configure Proxy Settings in Windows 10?
Are you a gamer? If yes, then you must be knowing Steam? But, do you know how can you use Steam on a Proxy Network? Let us discuss Steam before we discuss using Steam on a Proxy Network. Steam is basically a digital sharing platform dedicated to gaming. It is developed by Valve Corporation. The main services provided by steam are purchasing and playing video games. Along with that Steam also offers digital rights management (DRM), video streaming, and social networking services. Below are some other features provided by Steam:
Operating Systems Supported By Steam are as follows:
You can purchase games and other steam services through their digital store present in the steam client interface called the Steam Store. Once you buy the game a digital license will be attached to your Steam account, so that you will be able to download the software on any compatible device. Games are stored on the network of servers which are globally distributed. You can download them using a Steam proprietary file transfer protocol. Steam deals in almost all of the common currencies such as US dollars, Canadian dollars, euros, pounds sterling, Brazilian reais, Russian rubles, Indonesian rupiah and Indian rupees depending on the users geo-location.
Before we move further to the core of this article, below is the explanation of the few technical terms which is going to be used frequently in this article.
1. Proxy server: A proxy server is actually an intermediate channel often known as a gateway between the normal users (client) and the internet(server). Proxy servers provide many functionalities, including security, and privacy. It actually depends on how you are using the proxy, and the security and privacy level you need for your purpose.
Proxy servers also act as a firewall and web filter, and in some cases, it also caches data to speed up connection and webpage loading.
2. IP address: An IP address is a logical address which is configured on a device (which can communicate in a computer network) so that the device can be uniquely identified in a network. Currently, two versions of IP address are available. First one and the older one is IPv4 (IPv4 is a 32-bit address, the total number of possible IPv4 addresses is 2³² addresses i.e around 4 billion addresses). The second one and the latest one is IPv6(IPv6 is a 128-bit address, the total number of possible IpV4 addresses is 2¹²⁸ addresses).
BELOW ARE THE FEW POINTS YOU SHOULD KNOW BEFORE WE DISCUSS USING STEAM ON A PROXY NETWORK :
WORKING OF PROXY NETWORK:
Every system in a computer network has a unique IP address. No two end devices can have the same IP address in the same computer network. The Internet is smart enough and it knows how to send the correct data packet to the correct computer on the basis of the IP address.
A proxy server is basically a computer(server) on the internet with its own IP address (which could be multiple in number) that your computer knows. When you initiate a web request, your request goes to the proxy server first. The proxy server then forwards your web request on your behalf to the web server, and then revert back the response from the web server to your computer.
While forwarding the request the proxy server can make changes (if it is configured in such a way) to the data packets you send. For example, a proxy server can mask your IP address, so the web server doesn’t know exactly where you are in the world. It can also encrypt your data, to prevent your data from getting intercepted by any hacker. It can also act as a firewall by blocking and allowing certain inbound and outbound traffic as per the requirement.
FOR WHAT REASONS DO PEOPLE USE PROXIES?
Below are a few reasons out of several reasons why organizations and individuals use proxies:-
WHY DO ANYONE WILL NEED A PROXY NETWORK ALONG WITH STEAM, WHEN THEY CAN RUN STEAM WITHOUT A PROXY NETWORK?
There are three main reasons why someone will want to use a proxy network along with Steam. In the first case, you need proxy just because you want to access Steam in an area or in a network which is not allowing you to access Steam services normally, or they might have intentionally blocked it in the network. Schools and workplaces for most of the times block such services in their network so that it could not be reached by kids in school or employees in the workplace for justified reasons. This restriction falls under a category which has nothing to do with restrictions imposed by Steam, as they are not the people restricting you. Anyway, our main concern is not to find; who is responsible for this restriction? But, we are the victim here and we need to find a workaround to tackle this restriction. This is one of the three scenarios where we will need a proxy network to bypass these network restriction imposed by schools and workplaces authorities.
The second case is all about a very weird Steam’s pricing policy. Whenever you purchase a game from Steam, along with game you get keys to unlock the game. You normally get two types of keys; the first one is the regional keys and the second one is the local key. The regional key is independent of any location, but the local key is not location independent, it is for the players of the given country only. Still wondering how come it is a problem and how will proxy act as a helping hand here? Let us go through a scenario, this scenario will definitely clear all of your doubts. For example, the local key for Russian region for any game is much cheaper (because the target audience is much smaller when compared to the other countries) and at the same time, the same local key is comparatively costlier for other regions. It is really very strange, right? This restriction falls under a category which has everything to do with restrictions imposed by Steam, as they are the people restricting you. Using a proxy network you can bypass this geo-restriction by getting a proxy of the particular cheaper location you need.
The third case is about very weird Steam’s game distribution policies. Actually Steam has a different game list for different countries. In case you want to play a game that is not available in your country then you will not be able to do so. Again a very strange policy, right? This restriction falls under a category which has everything to do with restrictions imposed by Steam, as they are the people restricting you in this case. Using a proxy network you can bypass this content-based geo-restriction by getting an account and proxy of the particular location you want.
HOW TO USE STEAM ON A PROXY NETWORK — STEP BY STEP GUIDE:
So far we discussed Steam, proxy network and why do anyone will need a Proxy Network along with Steam when he or she can run Steam without a Proxy Network. Now let us get into the crux of our article i.e methods to use Steam on a proxy network:
1. By using Proxifier :- You may use Proxifier, as Proxifier is the most advanced proxy client software which gives us an ability to run network applications behind a proxy server, who normally do not have any inbuilt option on their settings page where anyone can configure the proxy. It gives you an option to route different application through a different proxy. And also you can route rest of the traffic via the normal internet. You can also bypass firewall restrictions with the help of Proxifier. Sometimes it acts like VPN by encrypting the traffic channel. It also helps in resolving DNS names through a proxy server.
Many wildcards options are available to easily allow or disallow application on Proxifier. Also provides you with a Dashboard to keep an eye on current network activities (connections, hosts, times, bandwidth usage, etc.) dynamically. It stores everything in form of log files.
Steps to configure Proxifier on your Windows PC:-
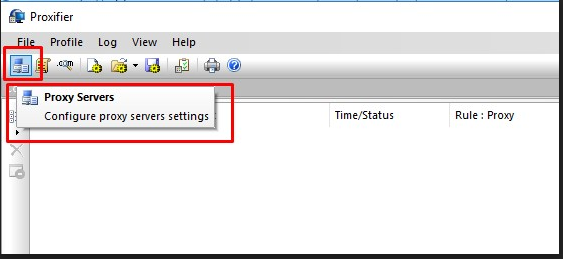
a. First, click on Proxy Servers in the Profile menu as shown in the screenshot.
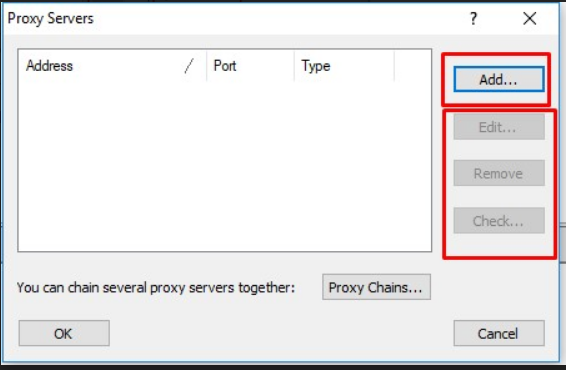
b. You will see a dialog box where you will get options to add, edit or remove proxy servers as shown in the screenshot.
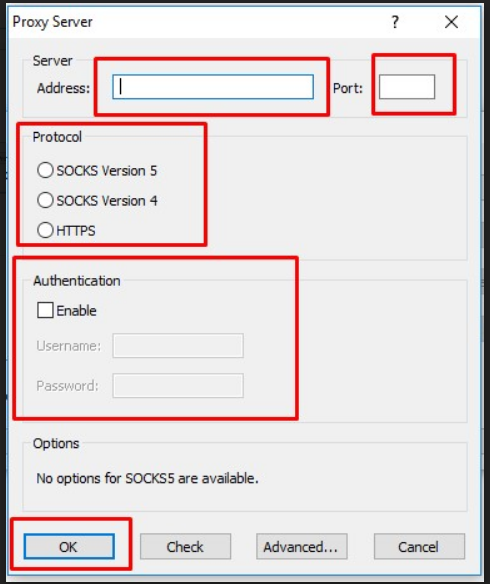
c. Finally to add a proxy network you need to click on the Add button, which will take you to a window where you can feed the details of the proxy network as shown in the screenshot.
Address: In the address filed you need to fill the address of the proxy server, it can be a hostname or IPv4/IPv6 address.
Port: In the port filed you need to fill the port of the proxy server
Protocol: Choose a suitable protocol, below is the brief explanation of all of them:
You can specify only User ID.
Technical documentation can be found at: http://www.ietf.org/rfc/rfc1928.txt and http://www.ietf.org/rfc/rfc1929.txt
Technical documentation can be found at: http://www.ietf.org/rfc/rfc2817.txt
Here is the download link.
2. By using Proxycap :- The Steam application is configured in a way to use UDP(User Datagram Protocol). You can use “-tcp launch” option while executing steam.exe to push the Steam application to route through TCP(Transmission control protocol) connections. This will allow you to run Steam application behind a proxy network.
But, most of the Steam games use UDP protocol and cannot be pushed forward to use TCP channel under any circumstances. In such cases, if you still want to play games using a proxy, you can use a proxy application that supports UDP, one of them is ProxyCap. ProxyCap has the ability to redirect UDP traffic via SOCKS5 proxy. It can only happen when UDP relay is already activated or can be activated on the proxy server. Also, you need to make sure that connection through the proxy server is not lacking required speed. Here is the download link.
3. By using Proxychain :- You may run Steam with the help of proxychains following below steps on Linux:
CONCLUSION:
In this article, we walked you through platforms like Steam, technology in a proxy network, we also gave you a reason why do anyone will need a Proxy Network along with Steam when he or she can run Steam without a Proxy Network. In the end, we discussed our main concern of this article i.e methods to use Steam on a proxy network.
According to Steam Subscriber Agreement: You agree that you will not use IP proxying or other methods to disguise the place of your residence, whether to circumvent geographical restrictions on game content, to purchase at pricing not applicable to your geography, or for any other purpose. If you do this, we may terminate your access to your Account.
But, we never heard any account was suspended or terminated for using Steam via a proxy. Still, it is up to you.
For pricing details please refer the link.
Feel free to contact us for a custom dedicated proxies setup from any particular location.
Stay tuned with this blog, we will keep updating the methodologies and workarounds to bypass Steam related restrictions. Should you have any queries related to any term discussed in this article. Write to us in the comments section below.
Что такое прокси-сервер, зачем он нужен и как его настроить
Поговорим о вечно актуальном: как обойти блокировку Hulu, как не остаться без Телеграма, если кто-то психанет и захочет его заблокировать, и как оставить без полезного трафика некоторые не особо качественные сайты. Поговорим о прокси-серверах.
Что такое прокси-сервер?
Прокси-сервер — это дополнительное звено между вами и интернетом. Некий посредник, который отделяет человека от посещаемого сайта. Создает условия, при которых сайт думает, что прокси — это и есть реальный человек. Только не вы.
Такие посредники довольно многофункциональны и используются в нескольких сценариях:
Все за счет того, что прокси подменяет IP-адрес, а трафик проходит через дополнительный сервер, на котором могут быть кэшированные данные или организованы дополнительные механизмы защиты данных.
Еще немножко об IP-адресе
Так как proxy-сервера отвечают за подмену IP, стоит немного пояснить, что он вообще делает и почему замена IP-адреса решает вышеописанные проблемы с доступом к сайтам и сервисам.
Поэтому люди используют proxy и прячутся за посторонними адресами, чтобы избегать блокировок и не так сильно светиться в интернете. Но опять же есть исключения, когда proxy-сервер в открытую делится данными о пользователе с сайтом и используется только для ускорения передачи запросов.
Типы прокси-серверов
Косвенно я уже упомянул о том, что proxy бывают разными. Зачастую тип сервера сопоставим с задачами, которые он выполняет. Но для начала мы обсудим именно базовую типизацию proxy, а потом более подробно поговорим о том, какие проблемы эти серверы решают.
Прозрачные
Такой прокси-сервер не утаивает от посещаемого сайта никакой информации. Во-первых, он честно сообщит ему о том, что является прокси, а во-вторых, передаст сайту IP-адрес пользователя по ту сторону сервера. С подобным типом можно встретиться в публичных заведениях, школах.
Анонимные
Более востребованный тип прокси. В отличие от первого, он тоже заявляет посещаемому ресурсу о своей proxy-сущности, но личные данные клиента не передает. То есть будет предоставлять обезличенную информацию для обеих сторон. Правда, неизвестно, как поведет себя сайт, который на 100% знает, что общается с proxy.
Искажающие
Такие прокси тоже идентифицируют себя честно, но вместо реальных пользовательских данных передают подставные. В таком случае сайты подумают, что это вполне себе реальный человек, и будут вести себя соответствующе. Например, предоставлять контент, доступный только в конкретном регионе.
Приватные
Вариант для параноиков. Такие прокси регулярно меняют IP-адреса, постоянно выдают фальшивые данные и заметно сокращают шансы веб-ресурсов отследить трафик и как-то связать его с клиентом.
Другие подкатегории
Прокси-серверы отличаются друг от друга и технически. Существуют:
Зачем нужен прокси-сервер?
На плечи proxy возлагают много задач. Сейчас подробно обсудим каждую.
Фильтрация доступных ресурсов
Распространенный сценарий использования в общественных сетях. С помощью такого сервера можно наблюдать за трафиком и при необходимости его «фильтровать». Это как родительский контроль. Только масштабы иные. Подобный proxy запросто могут поднять в крупной компании, чтобы сотрудники не лезли в Твиттер, пока занимаются делами. Поэтому при входе в соцсеть может вылезти предупреждение с просьбой заняться работой. Ну или вместо этого начальник просто зафиксирует все время пребывания в Фейсбуке, а потом вычтет это из зарплаты. С детьми ситуация примерно такая же. Можно ограничить их свободу в сети на время выполнения домашнего задания, к примеру.
Ускорение работы интернета
На прокси-серверах могут храниться кэшированные копии сайтов. То есть при входе на определенный сайт вы получите данные именно с proxy. С большой долей вероятности, через прокси загрузятся они заметно быстрее. Так происходит, потому что загруженность популярного сайта, на который вы хотите зайти, пострадает меньше, если большое количество людей будет заходить на него через шлюз в виде прокси-сервера.
Сжатие данных
Тоже весьма практичный сценарий. Помогает заметно снизить количество затрачиваемого трафика. На некоторых прокси установлены инструменты, которые сжимают весь запрашиваемый контент перед тем, как перенаправить его к конечному пользователю. По такому принципу работает «Турбо-режим» в браузерах Opera и Яндекса. Сжатие происходит на прокси-сервере, только он загружает полную версию медиа-контента и берет на себя всю нагрузку. А клиент уже скачивает те же данные, только в облегченном виде. Поэтому люди с лимитированным трафиком от этого выигрывают.
Конфиденциальность
Если возникают беспокойства за частную жизнь, то можно настроить приватный или анонимный шлюз, который будет всячески скрывать информацию о компьютере, который сделал первоначальный запрос (уберет его IP-адрес как минимум). Ими пользуются как отдельные личности, уставшие от слежки рекламистов, так и крупные корпорации, не желающие мириться со шпионажем со стороны конкурентов, например. Это, конечно, не панацея, но самые примитивные проблемы, связанные с конфиденциальностью, прокси решить может. А еще он не требует большого количества ресурсов и времени на реализацию.
Безопасность
Прокси может обезопасить не только частную жизнь, но и защитить от реальных угроз вроде вирусов. Можно настроить шлюз таким образом, чтобы он не принимал запросы с вредоносных ресурсов. И превратить получившийся прокси в своего рода массовый «антивирус», через который можно выпускать всех сотрудников компании, не переживая, что те нарвутся на какую-нибудь серьезную угрозу. Конечно, это не защитит пользователей на 100%, но зато даст небольшой прирост безопасности. А он тоже дорогого стоит. Поэтому proxy, используемые именно для защиты, не такая уж редкость.
Доступ к запрещенному контенту
Еще шлюз можно использовать, чтобы обойти региональные запреты. Это работает как с веб-страницами, так и с веб-приложениями. Можно смотреть заграничную библиотеку Netflix, слушать американский музыкальный сервис Pandora, смотреть что-то в Hulu и так далее. Можно заходить на сайты, которые блокируются конкретно в вашей стране. Или случайно заблокированные провайдером. Причем это могут быть совсем безобидные сайты. Я, например, долго не мог зайти на форум sevenstring.com. Ну и всем известная история с Телеграмом, который из недолгого забвения вытащили как раз таки proxy-серверы.
Сравнение прокси с VPN
VPN лучше как в плане безопасности, так и в плане удобства, но такая сеть чаще стоит приличных денег. Зачастую VPN сложнее в настройке и работают не так быстро. Сами посудите, вам обязательно нужен клиент для работы с виртуальными сетями или как минимум разрешения для браузера. Через proxy же можно подключаться, не устанавливая на компьютер ничего.
Риски, которые несет с собой использование прокси
Да, риски есть, причем серьезные. Придется потратить чуть больше времени на изучение proxy-серверов, прежде чем выбрать какой-то из них и начать использовать.
Например, стоит взять во внимание тот факт, что бесплатные прокси зачастую не очень хорошо подходят для решения вопросов безопасности. Чтобы как-то зарабатывать, владельцы шлюзов ищут иные пути для этого. Они продают пользовательские данные. Помогают распространять таргетинговую рекламу. Но даже этих денег не хватает, чтобы обеспечить высокую безопасность и скорость работы сервера, поэтому бесплатные варианты бывают тормозными и небезопасными.
Также стоит понимать: использование прокси-сервера равняется передаче личных данных третьему лицу. Обычно с ними знакомятся только провайдер связи и владельцы страниц, которые вы посещаете. Теперь появится еще одна сторона, у которой будет доступ ко всему вашему трафику. Не факт, что он будет шифроваться или храниться в безопасности. И неизвестно, на каких условиях proxy-сервер может взаимодействовать с государством.
Естественно, об этом никто напрямую рассказывать не станет. Но некоторые шлюзы смогли завоевать положительную репутацию. О них поговорим дальше.
Лучшие бесплатные прокси-серверы
Я не буду перечислять все сервисы. Поговорим лишь об основных анонимайзерах, которые работают прямо в браузере. А еще я расскажу о том, где можно найти прокси-серверы и на какие параметры обратить внимание, чтобы выбрать подходящий вариант.
Hide My Ass
Популярный анонимайзер от разработчиков антивируса Avast. Работает как расширение для Chrome и Firefox. Бесплатно разрешает подключиться к серверами из 5 стран. В их числе Германия, Нидерланды и США. Из особенностей можно отметить функцию автоматического включения при попытке зайти на некоторые сайты. Например, если заходите на американскую Pandora, то proxy включится сам.
Hotspot Shield
Это VPN-сервис с недурственной репутацией. Помимо предоставления доступа к VPN, у бренда есть как минимум 4 proxy-сервера, которыми можно пользоваться бесплатно. Для этого надо установить одноименное приложение на смартфон или расширение для браузера. Они тоже распространяются бесплатно.
ProxySite
Удобный сайт для быстрого доступа к Proxy-серверам. Работает как шлюз в духе Hide My Ass. Просто заходите на страницу, вводите адрес сайта, на который хотите попасть, а затем указываете страну, из которой хотите зайти. Тут даже есть несколько ссылок на популярные сайты, на которые часто заходят через прокси.
Как выбрать proxy-сервер?
Есть 5 факторов, на которые стоит положиться при выборе прокси:
Где найти proxy для ручной настройки?
Есть такой сайт как Hide My. На нем есть встроенный фильтр бесплатных proxy-серверов. Их там сотни. Можно выбрать страну, скорость, протокол, тип шифрования. В общем, что угодно.
Это работает так:
Настраиваем прокси-сервер
В зависимости от платформы и используемых программ, настройка шлюза будет выполняться по-разному. Я буду брать в пример типовые варианты систем и браузеров. Windows, Firefox, iOS. Но эти же инструкции справедливы для других ОС и программ. Просто пункты меню и их расположение могут немного отличаться.
Итак, как настроить proxy-сервер:
На компьютере
Тут тоже есть два разветвления. Одна инструкция для настройки шлюза во всей системе, а вторая — только для браузера. Начнем с первой.
В системе
Чтобы настроить Proxy-сервер в Windows 10, делаем следующее:
На этом все. В macOS и Linux принцип тот же. Даже меню в настройках со схожими названиями. Проблем возникнуть не должно.
В браузере
Чтобы настроить прокси-сервер в Firefox, делаем следующее:
Для каждого типа прокси тут есть отдельная строка. Главное, не перепутать и ввести нужные данные в верные поля.
В телефоне или планшете
Покажу, как настроить proxy-сервер в iOS. Для этого:
В большинстве сборок Android все устроено примерно так же. Безусловно, у некоторых вендоров параметры могут находиться в других местах, но разобрать каждого из них в рамках этой статьи точно не получится.
Создаем свой прокси-сервер
Чтобы быть менее зависимым от владельцев конкретных прокси-серверов, можно поднять свой.
Все. Теперь надо только подключиться к своему серверу. Это можно сделать так же, как я уже описывал в инструкции к браузеру Firefox. Только надо:
Теперь вам известно, что такое прокси-сервер, как он функционирует и зачем может понадобиться. Засим откланяюсь. Более мне вам поведать не о чем.
Источники информации:
- http://proxyrate.net/chto-takoe-proksi-i-zachem-on-nuzhen-i-kak-im-polzovatsya/
- http://proxys.io/en/blog/proxy-info
- http://medium.com/@limeproxiesserver/how-to-configure-proxy-settings-in-windows-10-9a360a6a93df
- http://timeweb.com/ru/community/articles/chto-takoe-proksi-server-zachem-on-nuzhen-i-kak-ego-nastroit