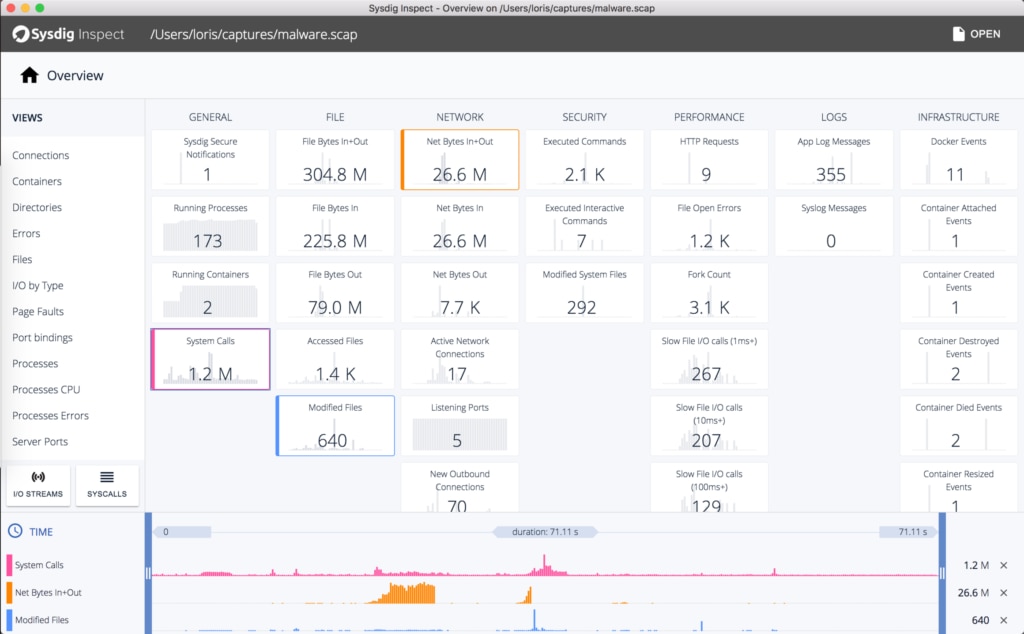
How to use wireshark
How to use wireshark
How to Use Wireshark: A Complete Tutorial
Capture and view the data traveling on your network with Wireshark
What to Know
Instructions in this article apply to Wireshark 3.0.3 for Windows and Mac.
What Is Wireshark?
Originally known as Ethereal, Wireshark displays data from hundreds of different protocols on all major network types. Data packets can be viewed in real-time or analyzed offline. Wireshark supports dozens of capture/trace file formats, including CAP and ERF. Integrated decryption tools display the encrypted packets for several common protocols, including WEP and WPA/WPA2.
How to Download and Install Wireshark
Wireshark can be downloaded at no cost from the Wireshark Foundation website for both macOS and Windows. You’ll see the latest stable release and the current developmental release. Unless you’re an advanced user, download the stable version.
During the Windows setup process, choose to install WinPcap or Npcap if prompted as these include libraries required for live data capture.
You must be logged in to the device as an administrator to use Wireshark. In Windows 10, search for Wireshark and select Run as administrator. In macOS, right-click the app icon and select Get Info. In the Sharing & Permissions settings, give the admin Read & Write privileges.
The application is also available for Linux and other UNIX-like platforms including Red Hat, Solaris, and FreeBSD. The binaries required for these operating systems can be found toward the bottom of the Wireshark download page under the Third-Party Packages section. You can also download Wireshark’s source code from this page.
How to Capture Data Packets With Wireshark
When you launch Wireshark, a welcome screen lists the available network connections on your current device. Displayed to the right of each is an EKG-style line graph that represents live traffic on that network.
To begin capturing packets with Wireshark:
Select one or more of networks, go to the menu bar, then select Capture.
To select multiple networks, hold the Shift key as you make your selection.
In the Wireshark Capture Interfaces window, select Start.
There are other ways to initiate packet capturing. Select the shark fin on the left side of the Wireshark toolbar, press Ctrl+E, or double-click the network.
Select File > Save As or choose an Export option to record the capture.
To stop capturing, press Ctrl+E. Or, go to the Wireshark toolbar and select the red Stop button that’s located next to the shark fin.
How to View and Analyze Packet Contents
The captured data interface contains three main sections:
Packet List
The packet list pane, located at the top of the window, shows all packets found in the active capture file. Each packet has its own row and corresponding number assigned to it, along with each of these data points:
To change the time format to something more useful (such as the actual time of day), select View > Time Display Format.
When a packet is selected in the top pane, you may notice one or more symbols appear in the No. column. Open or closed brackets and a straight horizontal line indicate whether a packet or group of packets are part of the same back-and-forth conversation on the network. A broken horizontal line signifies that a packet is not part of the conversation.
Packet Details
The details pane, found in the middle, presents the protocols and protocol fields of the selected packet in a collapsible format. In addition to expanding each selection, you can apply individual Wireshark filters based on specific details and follow streams of data based on protocol type by right-clicking the desired item.
Packet Bytes
At the bottom is the packet bytes pane, which displays the raw data of the selected packet in a hexadecimal view. This hex dump contains 16 hexadecimal bytes and 16 ASCII bytes alongside the data offset.
Selecting a specific portion of this data automatically highlights its corresponding section in the packet details pane and vice versa. Any bytes that cannot be printed are represented by a period.
To display this data in bit format as opposed to hexadecimal, right-click anywhere within the pane and select as bits.
How to Use Wireshark Filters
Capture filters instruct Wireshark to only record packets that meet specified criteria. Filters can also be applied to a capture file that has been created so that only certain packets are shown. These are referred to as display filters.
Wireshark provides a large number of predefined filters by default. To use one of these existing filters, enter its name in the Apply a display filter entry field located below the Wireshark toolbar or in the Enter a capture filter field located in the center of the welcome screen.
For example, if you want to display TCP packets, type tcp. The Wireshark autocomplete feature shows suggested names as you begin typing, making it easier to find the correct moniker for the filter you’re seeking.
Another way to choose a filter is to select the bookmark on the left side of the entry field. Choose Manage Filter Expressions or Manage Display Filters to add, remove, or edit filters.
You can also access previously used filters by selecting the down arrow on the right side of the entry field to display a history drop-down list.
Capture filters are applied as soon as you begin recording network traffic. To apply a display filter, select the right arrow on the right side of the entry field.
Wireshark Color Rules
While Wireshark’s capture and display filters limit which packets are recorded or shown on the screen, its colorization function takes things a step further: It can distinguish between different packet types based on their individual hue. This quickly locates certain packets within a saved set by their row color in the packet list pane.
Wireshark comes with about 20 default coloring rules, each can be edited, disabled, or deleted. Select View > Coloring Rules for an overview of what each color means. You can also add your own color-based filters.
Select View > Colorize Packet List to toggle packet colorization on and off.
Statistics in Wireshark
Other useful metrics are available through the Statistics drop-down menu. These include size and timing information about the capture file, along with dozens of charts and graphs ranging in topic from packet conversation breakdowns to load distribution of HTTP requests.
Display filters can be applied to many of these statistics via their interfaces, and the results can be exported to common file formats, including CSV, XML, and TXT.
Wireshark Advanced Features
Wireshark also supports advanced features, including the ability to write protocol dissectors in the Lua programming language.
Руководство и шпаргалка по Wireshark

Устранение неполадок сетевого подключения
Исследование сессий прикладного уровня (даже при шифровании с помощью SSL/TLS, см. ниже)
Устранение неполадок DHCP с данными на уровне пакетов
Извлечение файлов из сессий HTTP
Извлечение файлов из сессий SMB
Обнаружение и проверка вредоносных программ
Проверка сканирования портов и других типов сканирования на уязвимости
Установка Wireshark
Wireshark работает на различных операционных системах и его несложно установить. Упомянем только Ubuntu Linux, Centos и Windows.
Установка на Ubuntu или Debian
Установка на Fedora или CentOS
Установка на Windows
На странице загрузки лежит исполняемый файл для установки. Довольно просто ставится и драйвер захвата пакетов, с помощью которого сетевая карта переходит в «неразборчивый» режим (promiscuous mode позволяет принимать все пакеты независимо от того, кому они адресованы).
Начало работы с фильтрами
С первым перехватом вы увидите в интерфейсе Wireshark стандартный шаблон и подробности о пакете.
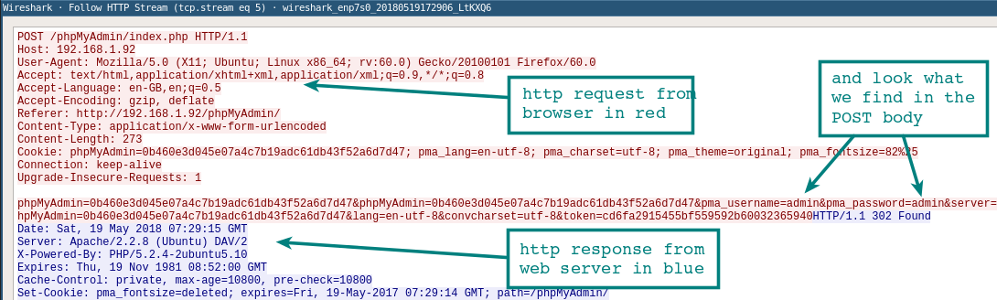
Как только захватили сессию HTTP, остановите запись и поиграйте с основными фильтрами и настройками Analyze | Follow | HTTP Stream.
Примеры фильтров по IP-адресам
Примеры фильтров по протоколу
Попробуйте сделать комбинацию фильтров, которая показывает весь исходящий трафик, кроме HTTP и HTTPS, который направляется за пределы локальной сети. Это хороший способ обнаружить программное обеспечение (даже вредоносное), которое взаимодействует с интернетом по необычным протоколам.
Следуйте за потоком
Как только вы захватили несколько HTTP-пакетов, можно применить на одном из них пункт меню Analyze | Follow | HTTP Stream. Он покажет целиком сессию HTTP. В этом новом окне вы увидите HTTP-запрос от браузера и HTTP-ответ от сервера.
Резолвинг DNS в Wireshark
По умолчанию Wireshark не резолвит сетевые адреса в консоли. Это можно изменить в настройках.
Edit | Preferences | Name Resolution | Enable Network Name Resolution
Tshark для командной строки
Составление правил для файрвола
Работа с географической базой GeoIP
Если Wireshark скомпилирован с поддержкой GeoIP и у вас есть бесплатные базы Maxmind, то программа может определять местоположение компьютеров по их IP-адресам. Проверьте в About | Wireshark, что программа скомпилирована с той версией, какая у вас в наличии. Если GeoIP присутствует в списке, то проверьте наличие на диске баз GeoLite City, Country и ASNum. Укажите расположение баз в меню Edit | Preferences | Name Resolution.
Проверьте систему на дампе трафика, выбрав опцию Statistics | Endpoints | IPv4. В колонках справа должна появиться информация о местоположении и ASN для IP-адреса.
Конечно, тот же фильтр можно применить к отдельным городам и странам. Удалите шум и оставьте только действительно интересный трафик.
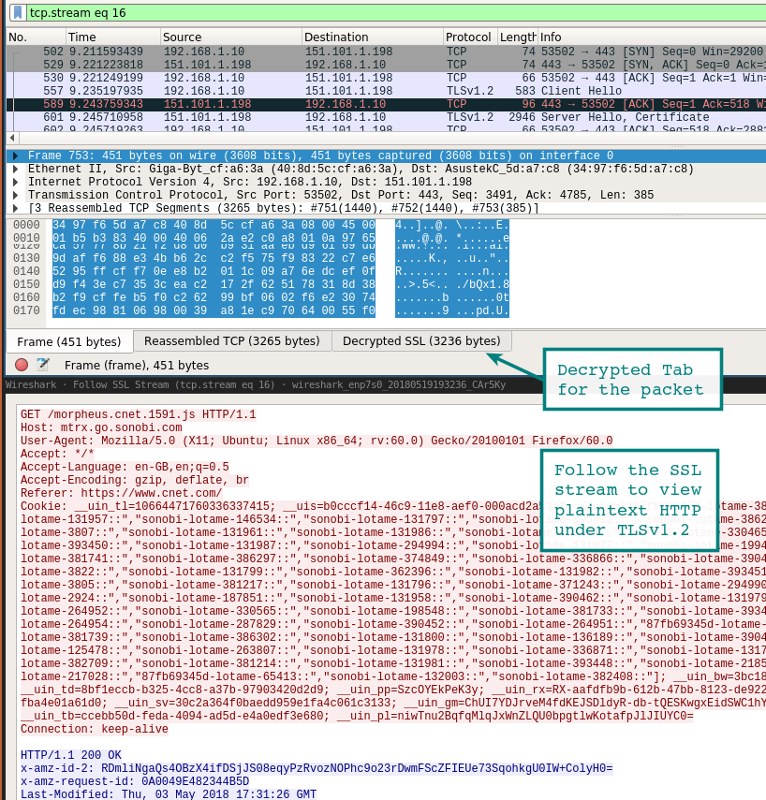
Расшифровка сессий SSL/TLS
Один из способов расшифровки сессий SSL/TLS — использовать закрытый ключ с сервера, к которому подключен клиент.
Конечно, у вас не всегда есть доступ к приватному ключу. Но есть другой вариант простого просмотра трафика SSL/TLS на локальной системе. Если Firefox или Chrome загружаются с помощью специальной переменной среды, то симметричные ключи отдельных сеансов SSL/TLS записаны в файл, который Wireshark может прочитать. С помощью этих ключей Wireshark покажет полностью расшифрованную сессию!
1. Настройка переменной среды
На вкладке System Properties | Advanced нажмите кнопку Environment Variables и добавьте имя переменной (SSLKEYLOGFILE), а в качестве значения — путь к файлу.
2. Настройка Wireshark
Из выпадающего меню выберите Edit | Preferences | Protocols | SSL | (Pre)-Master-Secret Log Filename — Browse, указав файл, который вы указали в переменную среды.
Начинайте захват трафика в локальной системе.
3. Перезапуск Firefox или Chrome
После перехода на сайт HTTPS лог-файл начнёт увеличиваться в размере, поскольку записывает симметричные ключи сессии.
Взгляните на ранее запущенную сессию Wireshark. Вы должны увидеть что-то похожее на скриншот внизу с расшифрованными сессиями. Расшифрованные пакеты — на вкладке в нижней панели.
Другой способ просмотра сеанса — через выпадающее меню Analysis | Follow | Stream | SSL. Если сеанс успешно расшифрован, вы увидите опцию для SSL.
Разумеется, будьте осторожны при записи этих ключей и пакетов. Если посторонний получит доступ к лог-файлу, то легко найдёт там ваши пароли и куки аутентификации.
Ещё один вариант выхода на базовый HTTP-трафика — использовать инструмент Burp Suite с загруженным сертификатом CA в браузере. В этом случае прокси расшифровывает соединение на стороне клиента, а затем устанавливает новый сеанс SSL/TLS на сервере. Есть много способов проведения такой MiTM-атаки на себя, это два самых простых.
Извлечение файлов из пакетов с помощью функции экспорта (HTTP или SMB)
Файлы легко извлекаются через меню экспорта.
File | Export Objects | HTTP
Все найденные файлы отобразятся в новом окне. Отсюда же можно сохранить отдельные файлы или сразу все. Аналогичный метод применяется для извлечения файлов из сессий SMB. Как мы уже упоминали, это протокол Microsoft Server Message Block, который используется для общего доступа к файлам под Windows.
Строка состояния
Строка состояния в правой части окна позволяет быстро перейти в нужное место сетевого дампа, щёлкнув по цветовому индикатору. Например, красным цветом в строке состояния помечены пакеты с ошибками.
Образец PCAP
Когда только начинаете работу с Wireshark, хочется посмотреть на какие-нибудь интересные дампы с пакетами. Их можно найти на странице Wireshark Samples. Примеров с разными протоколами там хватит вам на несколько месяцев анализа, есть даже образцы трафика червей и эксплоитов.
Настройка окружения
Внешний вид консоли по умолчанию всячески настраивается. Можно добавлять или удалять столбцы, добавляя даже такие простые вещи как столбец времени UTC, что сразу повышает информативность логов, если анализировать историю пакетов.
Столбцы настраиваются в меню Edit | Preferences | Appearance | Columns. Там же изменяется общий шаблон, шрифт и цвета.
На видео — полезные советы по настройке окружения, в том числе выявление неполадок по порядковым номерам последовательности TCP.
capinfos
How to Use Wireshark, the Best Packet Analyzer Around
Wireshark is the best network traffic analyzer and packet sniffer around. In this article, we will look at it in detail.
Wireshark is a network analyzer that lets you see what’s happening on your network. It lets you dissect your network packets at a microscopic level, giving you in-depth information on individual packets.
Wireshark was first released in 1998 (and was called Ethereal back then). It can run on all major operating systems. Most enterprises and government organizations now prefer Wireshark as their standard network analyzer.
Wireshark is also completely open-source, thanks to the community of network engineers around the world. While most security tools are CLI based, Wireshark comes with a fantastic user interface.
OSI Model
I am assuming you are new to networking, so we will go through some basics of the OSI model. This is important to understand the core functions of Wireshark.
The Open Systems Interconnection (OSI) model standardizes the way two or more devices connect with each other. The OSI Model segments network architecture into 7 layers: Application, Presentation, Session, Transport, Network, Datalink, and Physical.
Here is what each layer does:
The below diagram should help you to understand how these components work together.
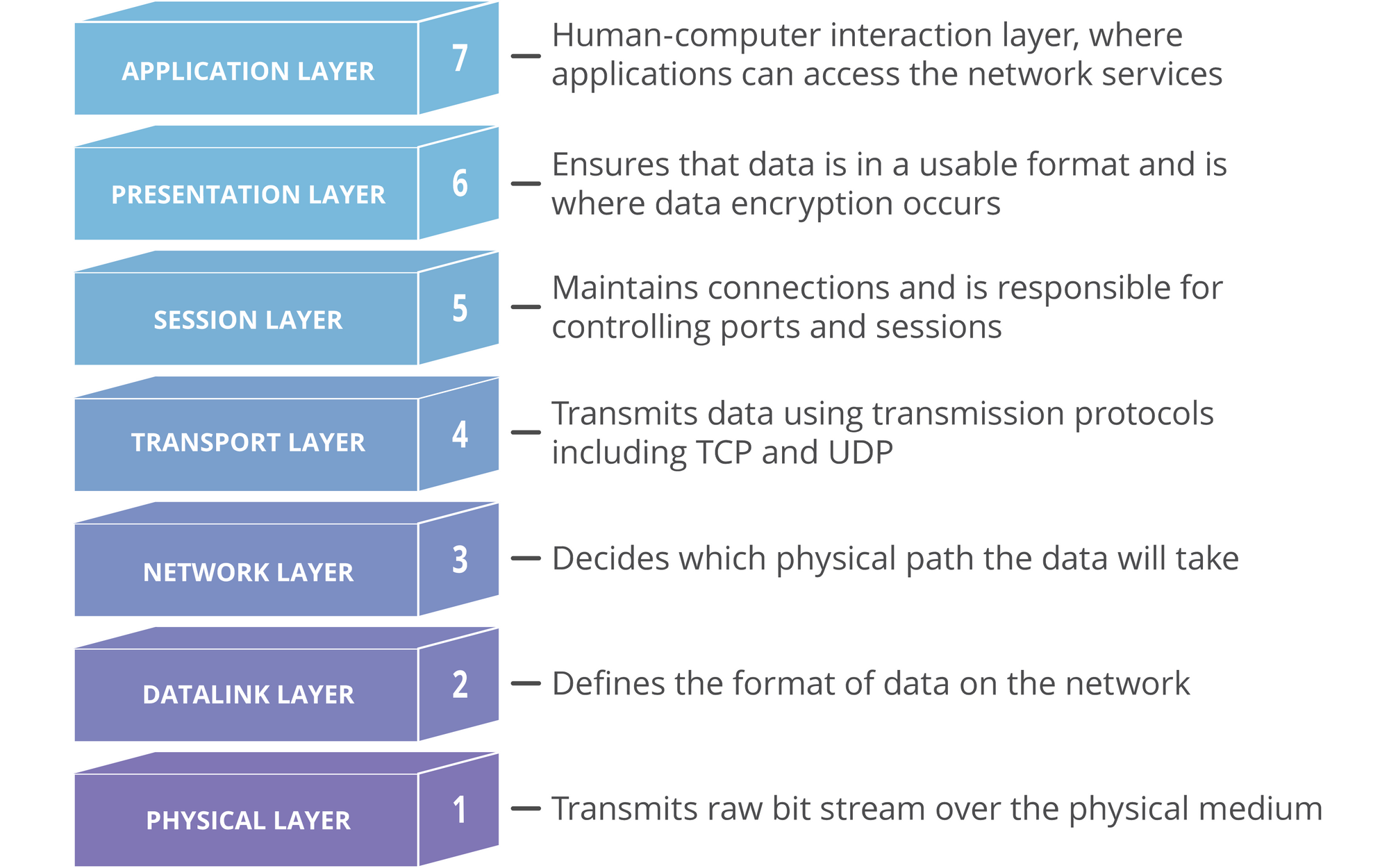
If you are interested in learning more about the OSI model, here is a detailed article for you.
Packets
Now that you have a solid grasp of the OSI model, let’s look at network packets. When data is transferred from one computer to another, the data stream consists of smaller units called packets.
When you download a file from the internet, the data is sent from the server as packets. These packets are re-assembled by your computer to give you the original file.
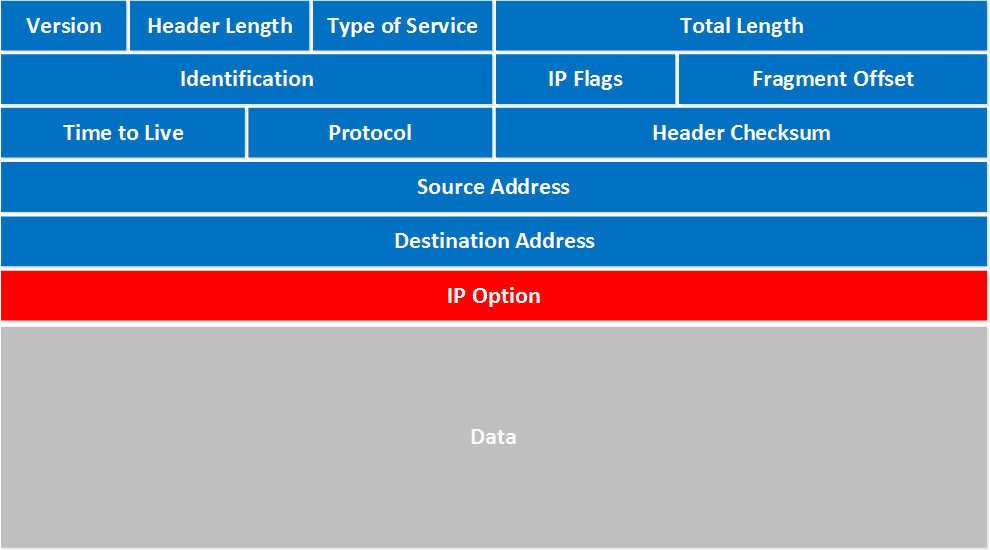
A packet can contain the following data:
Each packet contains valuable information about the devices involved in a packet transfer. Each data transfer involves thousands or even millions of these packets of data being sent between the source and the destination devices.
Now you can understand the importance of Wireshark. Wireshark lets you capture each of these packets and inspect them for data.
Wireshark, to a network engineer, is similar to a microscope for a biologist. Wireshark lets you ‘listen’ to a live network (after you establish a connection to it), and capture and inspect packets on the fly.
As a network engineer or ethical hacker, you can use Wireshark to debug and secure your networks. As a malicious hacker (which I don’t recommend), you can «sniff» packets in the network and capture information like credit card transactions.
This is why it is unwise to connect to a public network like Starbucks and perform financial transactions or access private data. Even though sites with HTTPS can encrypt your packets, it is still visible over the network. If someone really wants to crack it, they can.
Wireshark Basics
Now let’s look at how you can play with Wireshark. Download and install Wireshark from here.
Wireshark has an awesome GUI, unlike most penetration testing tools. Here’s how Wireshark looks when you load it.
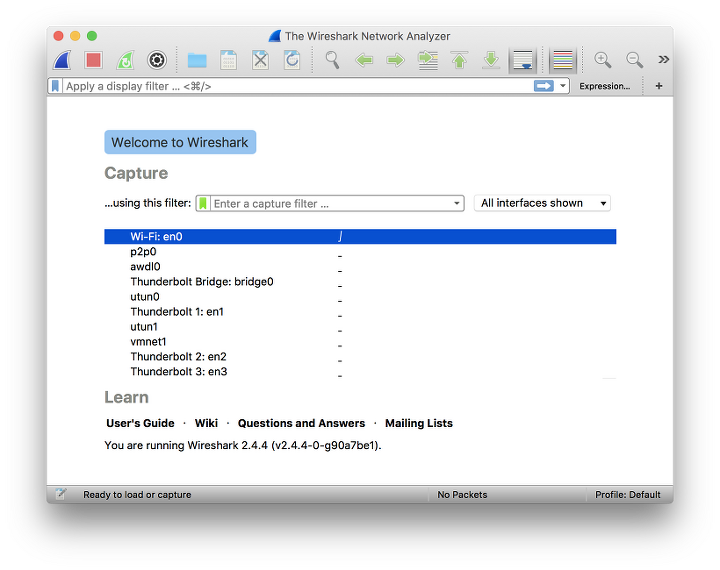
Wireshark lists out the networks you are connected to and you can choose one of them and start listening to the network.
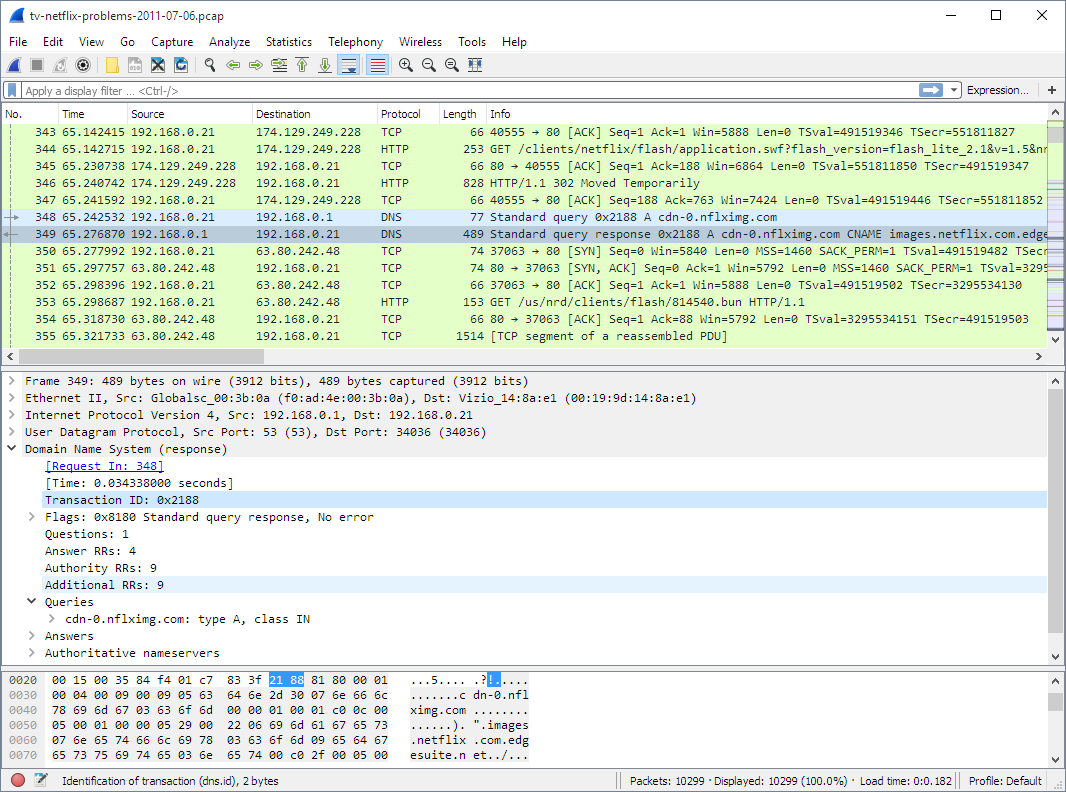
There are three panes in Wireshark.
Packet List Pane
This pane displays the packets captured. Each line represents an individual packet that you can click and analyze in detail using the other two panes.
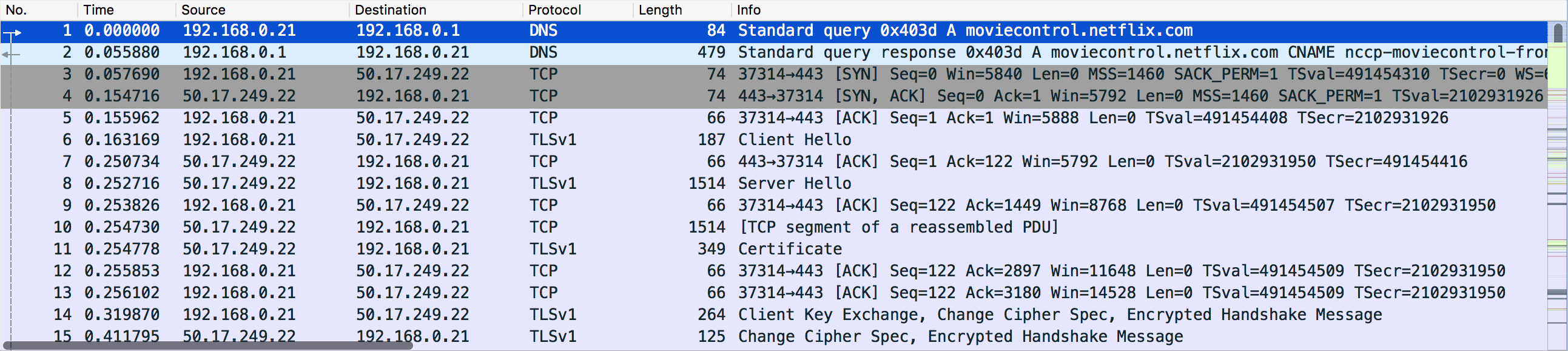
Packet Details Pane
You can select a packet and then look at the packet information in more detail using the Packet Details pane. It displays information such as IP addresses, ports, and other information contained within the packet.
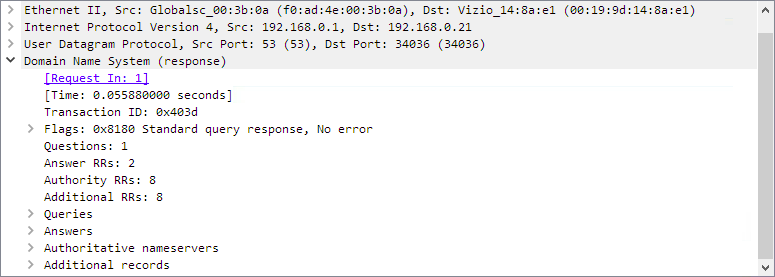
Packet Bytes Pane
This pane gives the raw data of the selected packet in bytes. The data is displayed as a hex dump, which is displaying binary data in hexadecimal.
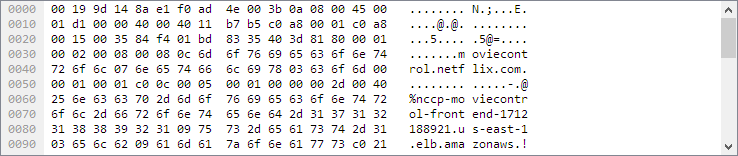
Filters
Wireshark has filters that help you narrow down the type of data you are looking for. There are two main types of filters: Capture filter and Display filter.
Capture Filter
You can set a capture filter before starting to analyze a network. When you set a capture filter, it only captures the packets that match the capture filter.
For example, if you only need to listen to the packets being sent and received from an IP address, you can set a capture filter as follows:
Once you set a capture filter, you cannot change it until the current capture session is completed.
Display Filters
Display filters are applied to capture packets. For example, if you want to display only the requests originating from a particular ip, you can apply a display filter as follows:
Since display filters are applied to captured data, they can be changed on the fly.
In short, capture filters enable you to filter the traffic while display filters apply those filters on the captured packets. Since Wireshark can capture hundreds of packets on a busy network, these are useful while debugging.
Core Features of Wireshark
Now that you have a good grasp of Wireshark basics, let’s look at some core features. With Wireshark, you can:
Conclusion
Wireshark is always ranked among the top 10 network security tools every year. With its simple yet powerful user interface, Wireshark is easy to learn and work with. It is a valuable asset in every penetration tester’s toolkit.
Hope this article helped you to get a solid grasp of Wireshark. I recently wrote an article on the top 10 tools you should know as a cybersecurity engineer. Do check it out if you are into cybersecurity.
I regularly write about Machine Learning, Cyber Security, and DevOps. You can signup for my weekly newsletter here.
How to Use Wireshark for Network Monitoring?
With an increase in demand for accessible services and applications, a good network has become more important than ever before. Issues such as packet loss, latency, network downtime, frequent errors, and jitters can hamper the overall user experience. Network monitoring has become a crucial and fundamental requirement for small, medium, and large enterprises. It’s considered the first line of defense when the network server performance begins to deteriorate. Network monitoring tools help teams to assess the availability of network devices, to check the overall health of the network, and troubleshoot performance issues such as bandwidth consumption/utilization and network downtime.
As the market is flooded with a wide variety of network monitoring tools, it becomes challenging to make a decision of choosing a reliable monitoring solution. Different network monitoring tools offer varying degrees of performance and integration capabilities. Some offer fully integrated architecture, whereas others include multiple components such as databases, polling engines, management consoles, and more. It can be confusing for the network administrators to choose the best solution with reliable and effective monitoring features. Therefore, before making a selection, organizations need to consider asking the following questions to the administrators.
Thorough research needs to be done to determine which tool offers the most beneficial features for the organization in the long run. This post covers one of the most reliable network analyzers available on the market, known as Wireshark. Let’s take a look at what Wireshark is, how it helps in detecting security issues, troubleshooting network errors, debugging protocols, and how the capabilities of Wireshark can be enhanced for advanced network monitoring.
What Is Wireshark?
Wireshark is known as the world’s leading network traffic analyzer. It’s the best tool for system administrators and IT professionals for troubleshooting network errors in real time. Wireshark quickly detects network issues such as latency, suspicious activity, and dropped packets. It can drill down into the traffic and find out the root cause of an issue. Usually, network administrators use Wireshark to resolve latency issues caused by equipment used to route traffic around the world and to monitor data exfiltration attempts against the business operations. Wireshark is a powerful yet free tool requiring extensive knowledge of the networking basics. To make the best use of the tool, administrators need to have a solid understanding of protocols such as TCP/IP and DHCP.
How Does It Work?
Wireshark is a popular open-source tool to capture network packets and convert them into human-readable binary format. It provides every single detail of the organization’s network infrastructure. It consists of devices designed to help measure the ins and outs of the network. The information collected through Wireshark can be utilized for various purposes, such as real-time or offline network analysis, identification of the traffic coming into your network, its frequency, and its latency between specific hops. This helps network administrators generate statistics based on real-time data.
Besides network monitoring, organizations use Wireshark for debugging programs, examining security issues, and learning network protocol internals. Wireshark is designed to efficiently perform packet-related functions and analyze and display the network metrics over the management console.
Wireshark also offers a great user-interface as it’s easy to use once the teams get familiar with the basics of capturing packets.
What Are the Core Features of Wireshark?
Wireshark consists of a rich feature set including the following:
How to Install or Download Wireshark?
To use Wireshark, the first thing users need to do is to download and install Wireshark on the system. Make sure you download the latest version of the tool directly from the company’s website for a better running experience. Given below are a few steps following which Wireshark can easily be downloaded and installed.
To successfully install Wireshark on Mac, users need to download an installer like xquartz. Once the installer is downloaded, open the Terminal and enter the following command:
Just wait for Wireshark to start.
To run Wireshark on Windows, visit the company’s website (Wireshark) and download the program. Once it’s done, simply start the setup process. Install WinPcap as well when it prompts to do so during the installation process. WInPcap is important to install as it helps in capturing live network traffic, and without it, users can only access the already saved capture files. To install WinPcap, select the Install WinPcap box.
How to Capture and Analyze Data Packets Using Wireshark?
One of the major functions of Wireshark is to capture data packets for conducting detailed network analysis. However, it can be tricky for beginners who aren’t familiar with the steps involved. There are majorly three important steps:
After following the above steps, the Wireshark is ready to capture packets. Usually, there are two capturing modes: promiscuous and monitor. Promiscuous mode sets the network interface to capture only the packets for which it’s assigned. Monitor mode is used by Unix/Linux systems and sets the wireless interface to capture as much of the network as it can. The data gathered while capturing packets is displayed in a human-readable format, so it’s easier to grasp. As Wireshark breaks the captured packets into a readable format, users can perform various other tasks such as select filters to find precise information and color code the crucial information. With Wireshark, administrators can also monitor multiple networks simultaneously.
Usually, promiscuous mode is used by system administrators to get a bird’s-eye view of the network packets transfer. On disabling this mode, only a small snapshot of the network is provided, which isn’t enough to conduct quality analysis. The promiscuous mode can easily be activated by clicking on the capture options provided in the dialog box. However, promiscuous mode isn’t available on every software or operating system. Therefore, users need to cross confirm about software compatibility either by visiting the Wireshark’s website or using the Device manager to check the settings (in case you’re a Windows user).
How to Analyze the Captured Network Packets?
Once the network data is captured, the list of network packets is displayed on the centralized management console or the dashboard. The screen consists of three panes: packet list, packet bytes, and packet details. However, to get important information on individual packets, users need to click on any of the panes mentioned above.
Packet List
The packet list pane consists of browsable captured network packets based on the timestamp to show exactly when the packet was captured, the packet’s protocol name, the source and destination of the packet, and support information.
Packet Details
Packet details pane provides information about the chosen packet. Users can expand each section and apply filters to get information about specific items.
Packet Bytes
Packet bytes pane consists of the internal data of the packet the user selects. The data is displayed in a hexadecimal format by default.
How Does Wireshark Help in Monitoring Network Performance?
Once the network packets are captured, the next step is to monitor and analyze them. Wireshark is a great tool to analyze and monitor the organization’s active network. Before doing this, it’s important to close down all the active applications on the network to reduce traffic, which helps in giving a clear picture of the network. Turning off all the applications won’t result in packet loss; in fact, the sending and receiving of packets is still an ongoing process.
However, conceptualizing the huge amount of data altogether isn’t easier. Therefore, Wireshark breaks these components into different forms to see what’s going on within the network. To help users quickly understand and analyze the data coming in, Wireshark uses color coding, filters, network statistics to segregate the network data.
What Is the Role of Filters in Wireshark?
Filters are beneficial when analyzing large files and a considerable amount of data. Filters help administrators find specific network data out of thousands of packets traveling through the network every second. Wireshark uses the two most common types of filters: Capture and Display, to segregate data based on their relevance. The capture filter gathers the live-monitoring data by reducing the size of the incoming packets. This helps in filtering out the non-essential packets during live capturing. However, capture filters are set before the filter process begins and cannot be modified once the process has started. Display filters, on the other hand, are used to filter the already recorded data.
How to Use Color-Coding in Wireshark?
Color coding is done to highlight the different packets based on certain factors. This helps users to identify packets based on colors. For instance, the UDP is denoted by light blue, ICMP with light pink, TCP traffic by light purple, and the packets with errors are highlighted with black. Wireshark’s default settings use twenty different colors to indicate various parameters. Users may modify, edit, add, or delete the settings as per their requirements. Colorization can also be disabled by turning off the Colorize Packet List field.
How to View Network Statistics on Wireshark?
Statistical data is beneficial in providing in-depth information about your network. To view those stats, click on the statistics drop-down menu providing metrics ranging from timing and size to plotting graphs and charts. Users can also apply a display filter to narrow down the list of options and find out the relevant information. The drop-down statistics menu displays the following metrics:
How to Visualize Network Packets Wfith IO Graphs?
Data packets or the network traffic can be represented in a visual format known as IO graphs. Users can view IO graphs by clicking on the statistics menu and selecting the IP graph tab. Once the graph window opens, users can view the data they wish for by configuring the graph settings accordingly. Due to Wireshark’s default settings, only one graph is displayed at a time. If users want to activate more graphs simultaneously, simply enable them. Moreover, users can also customize the graphs using filters and color codes to find out the relevant information for the purpose. Users can also modify the graph structure from the style column and can choose any of them: Line, Dot, Impulse, Fbar. Users can also not only adjust the style of the graphs but can also interact with the X and Y axis metrics of the graphs. Once the settings are done, the graphs can be stored in a file format for future purposes.
How to Expand Wireshark Capabilities?
Undoubtedly, Wireshark is a great packet sniffer, but it lacks a few advancements when it comes to meet the growing needs of network monitoring. Wireshark’s monitoring capabilities can be improved using complementary tools such as SolarWinds ® Response Time Viewer for Wireshark, Show Traffic, Cloudshark, and NetworkMiner. Outlined below are the features, capabilities, functions of these tools, and how they help in enhancing the network monitoring capabilities of Wireshark.
SolarWinds Network Performance Monitor
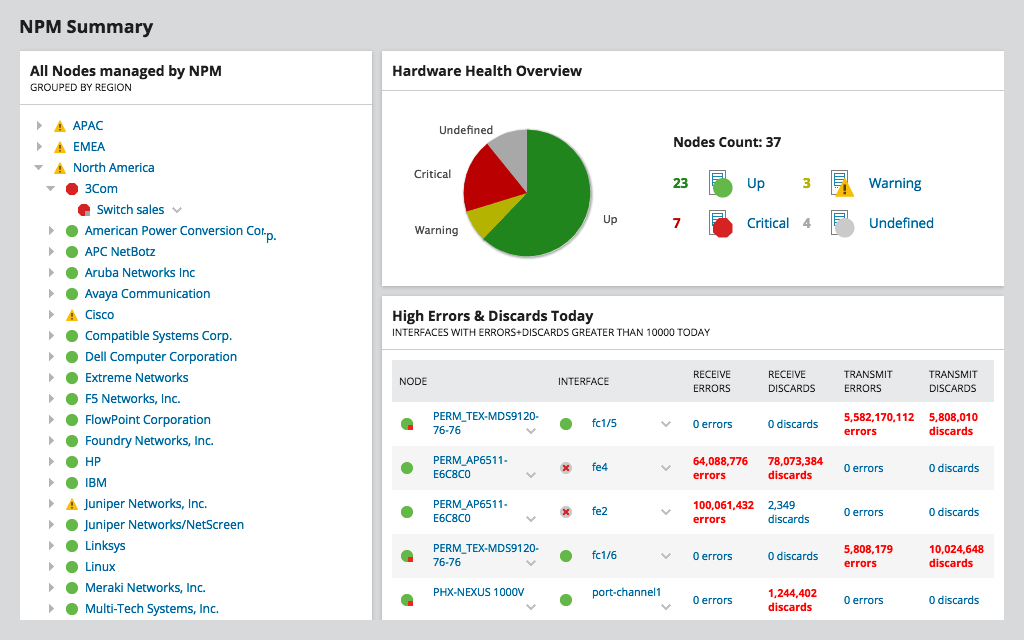
SolarWinds Network Performance Monitor (NPM) is a powerful network monitoring software used to detect, diagnose, and resolve network issues and outages. The tool is specially designed for advanced network troubleshooting for on-premises, hybrid, and cloud services, and detects issues with its hop-by-hop analysis. It not only helps to make the network scalable but also secure. NPM is also capable of reducing downtime resulting in improved operational efficiency, network availability, and high-performing applications. It offers out-of-the-box features including intuitive dashboards, advanced alerting systems, custom reporting, packet analysis, and more. Besides hop-by-hop analysis, NPM offers availability monitoring, cross-stack network data correlation, customizable topology, network discovery, mapping capabilities, packet capture analysis, drag-and-discover network performance charts, statistical network performance baselines, and hardware Health Monitoring. With NPM, areas with weak signals or network dead zones can be identified quickly using Wi-Fi heat maps. Try it out with a free, fully-functional trial.
SolarWinds Response Time Viewer for Wireshark
SolarWinds Response Time Viewer for Wireshark allows users to detect and analyze Wireshark’s packet captures and troubleshoot network performance outages in real-time. It can perform multiple tasks such as identify over 1200 applications, calculate their network response time, display data and transaction value, critical path visualization with Netpath, and wireless network monitoring and management. Evaluating these parameters helps users determine network flaws and faults.
Cloudshark
Cloudshark is a platform designed to display network capture files directly in the browser without the need for desktop applications or tools. Simply upload, email, or link the captures files and get the results. It helps to resolve network issues faster and flawlessly. Besides, it includes features such as drag-and-drop capture files, drop-box-like activity, allows sharing of links with co-workers, and offers advanced analysis.
Sysdig
Sysdig is a powerful, cross-platform, and open-source flexible network monitoring system designed specifically for Linux. It also works for Windows and Mac OSX but with limited functionalities such as inspection, debugging, and system analysis. Sysdig uses various monitoring and troubleshooting tools for Linux system performance, such as:
Sysdig integrates all the tools mentioned above and offers them in a single program. Users can easily capture, filter, save, modify, track, and examine network traffic and the real behavior of Linux systems. Sysdig features include:
Debooke
Debooke is one of the simplest and most powerful network monitoring and traffic analyzer tools for macOS. The tool allows users to intercept and monitor the network traffic of any device in the same subnet. It helps to capture data network packet data from any device such as a mobile, printer, Mac, TV, and more without using a proxy. Features of Debooke:
Final Thoughts
Wireshark is a simple, yet versatile and powerful network monitoring tool. It’s easy to use and easy to learn. Besides monitoring, Wireshark offers additional network analysis features such as:
However, for the new users who are willing to try Wireshark, it’s advisable to do some additional research and get detailed information on Wireshark by visiting the website. For existing users who are looking for more advanced network monitoring and analytical features and want to create their protocol dissectors, try using the external plugins and supporting programs highlighted above.
SolarWinds Network Performance Monitor and Response Time Viewer for Wireshark are professional tools and work amazingly. They can not only identify and troubleshoot network issues in real-time but also perform multiple tasks simultaneously, such as display essential data, calculate network response time, and more. These tools increase the depth of the network analysis efforts dramatically.
How to use Wireshark, the complete Tutorial
Share This Post
Have you ever struggled in finding the problem of a network? There are times when data seems to simply not reach its destination. It’s like your file, stream, or any other kind of content disappears on the cable. While cables don’t make data disappear, it is possible that some device is having problems. With this guide, you will learn how to use Wireshark to exactly find (and fix) your network problems.
In this tutorial, we will explain to you how to use Wireshark from scratch. First, we will start explaining how to download Wireshark for free, and how to install it on Windows/MAC/Linux. Then, we will see how to use it, how to sniff packets, how to store such packets, and how to read them. Before everything else, we will give explain what is Wireshark.
Introducing the WireShark Tutorial
What is Wireshark?
WireShark is an Open Source Software for sniffing packets. In other words, it is free software: you can download and use Wireshark for free. Technically, it’s even more than that: you can modify its code and change the way it works, or extend its functionalities. However, that’s what developers do: as network engineers, we will limit ourselves to just use Wireshark.
What does sniffing packets mean? Wireshark can capture network traffic on an interface, like your Ethernet interface or Wi-Fi interface. To say this in a different way, it can read everything you send and receive on a network. For example, if you send an email, it will see all the details, and see if you have effectively sent it. Among other things, Wireshark can capture:
As you might guess, all of that is extremely useful when you want to troubleshoot network issues.
Is using Wireshark safe?
Yes, using wireshark is completely safe. Of course, Wireshark is able to read all of your data, even sensitive data, but you tell Wireshark when to start and when to finish. Most importantly, Wireshark runs on your PC and won’t send what it reads to anyone else. So, what you see in Wireshark is only for you to see.
How to Download WireShark for Free
Wireshark is Open Source and completely free to use. To download it, you can simply consult their official website. Even better, go directly to their download page.
If you want to keep WireShark on a USB stick, to plug it in any Windows PC and run it, simply get the Portable version. In any other case, just select the WireShark version that reflects your Operating System.
How to install Wireshark
If you downloaded an executable version (not the portable), you will need to install it. Fortunately, installing Wireshark is extremely easy: you just need to run the file you downloaded. It will open a wizard, where everything you need to do is clicking “Next” until you see the “Finish” button.
At this point, you will have Wireshark within the programs installed on your computer. Search for it, and run it. If you downloaded the portable version, run that instead. This Wireshark tutorial will apply to both versions, as they are identical in their features.
A quick tip: if you installed Wireshark, you might have two software: Wireshark and Wireshark Legacy. They are almost the same, it only changes the graphical interface. Since we are geeks, and we always the most recent technology, we should use simply “Wireshark”.
How to use WireShark
Getting to know WireShark
Using WireShark is very easy, as you will see. If you launch Wireshark, you will see the window below. We marked the important stuff with red circles so that you know where to look at.
The first item we highlighted is the capture option button (1). From there, you can start a Packet Capture and specify all its settings. Then, in the middle of the window, we have the Open section (2). WireShark can save the captured data into special files, that you can later open: in this section, you can see the recently opened files. Finally, the Capture section (3). This is just a shortcut for the capture options, where you can quickly start a capture.
Since we are opening Wireshark for the first time, we have no file to open. Instead, we should capture data for the first time. To see how to use Wireshark for capturing packets, just read the next section.
How to use WireShark to sniff traffic
WireShark does two things: it captures the packets, and it presents them to you in a user-friendly way. Obviously, without the first, you can’t do the second. So, to start a packet capture, click on the capture option icon (the one with the gears). A new window will pop-up.
As you can see, the “Start” button is gray and you can’t click on it. This is because you haven’t selected any interface just yet. A computer sends and receive traffic on interfaces, or NICs. Therefore, you need to tell Wireshark on which interface do the capture. Remember, Wi-Fi is Wifi of course, while Ethernet is a cable interface. Most computers will have just two NICs, one Wi-Fi and one Ethernet.
How to be sure about what NIC to use? Next to the interface, we see a graph of the traffic. You expect a flat line on all NICs but one: that’s the one currently in use. If you let some time pass, you will see the graph getting its shape. For example, we are currently using Wi-Fi 2, as in the picture.
You could expand the Interface (the arrow at the very left) and filter per MAC address. However, there’s no need to do that, and it would be too advanced for our needs. So, just select the interface (the whole line will be highlighted in light blue). Then, click Start to launch the capture.
Capturing Traffic in Wireshark
As soon as you start, the following window will pop-up.
At first, this interface is not so intuitive. However, as soon as you get its sense, everything will be so easy and familiar. For convenience, we numbered important stuff.
Now, it’s time to analyze packets!
Analyzing the packets with WireShark
If you know how to use Wireshark, you know how to analyze packets. Here we will explain to you the basic fields you see in the table, the fifth item in the list above.
If you want to store the capture and check it at a later time, you can simply save it (from the file menu).
Conclusion
Now that you know how to use Wireshark, the best thing to do is try on your own. Just try to surf the web, send emails or even play online games while sniffing the traffic. Then, get back to Wireshark and stop the capture. Now, it’s just time to analyze it, look for protocols and interesting information. The best way to master Wireshark is using it.
What do you think about Wireshark? Was it useful to your troubleshooting? Just let me know in the comments. And, if you want to learn more about it, just wait for the next articles. You will learn the advanced stuff about Wireshark, like filtering – both display and capture, promiscuous mode, and more.
:max_bytes(150000):strip_icc()/ScottOrgera-f7aca23cc84a4ea9a3f9e2ebd93bd690.jpg)
:max_bytes(150000):strip_icc()/001_wireshark-tutorial-4143298-52d1294a66f64810b14dbfc6fdbe00de.jpg)
:max_bytes(150000):strip_icc()/001-wireshark-tutorial-4143298-8944764352c445c89af8571085055965.jpg)
:max_bytes(150000):strip_icc()/002-wireshark-tutorial-4143298-09827053b9cd4445ac165d68a0039808.jpg)
:max_bytes(150000):strip_icc()/003-wireshark-tutorial-4143298-024370e017284dc0a251f91a3566cf06.jpg)
:max_bytes(150000):strip_icc()/004-wireshark-tutorial-4143298-3db6aeba8777467c8fc3e42ac304f3f6.jpg)
:max_bytes(150000):strip_icc()/005-wireshark-tutorial-4143298-c60e3bb4537a4615b8326d5ff8550407.jpg)
:max_bytes(150000):strip_icc()/006-wireshark-tutorial-4143298-016d2b41501149d994d0d9e78239d964.jpg)
:max_bytes(150000):strip_icc()/008_wireshark-tutorial-4143298-7fc1de4be4e746278f59f2179a453528.jpg)
:max_bytes(150000):strip_icc()/007-wireshark-tutorial-4143298-ac0e56f1a0984c1b93a91b1641c7fe88.jpg)
:max_bytes(150000):strip_icc()/008-wireshark-tutorial-4143298-13534b80059945e88759286cb3338360.jpg)
:max_bytes(150000):strip_icc()/009-wireshark-tutorial-4143298-490a6676280b43cd900557647ff9e92d.jpg)
:max_bytes(150000):strip_icc()/010-wireshark-tutorial-4143298-9b5ba526d6e54f8bb3ac49eaea6d08fa.jpg)
:max_bytes(150000):strip_icc()/011-wireshark-tutorial-4143298-0b7390128b5a47c38aca851eeed120b5.jpg)
:max_bytes(150000):strip_icc()/012-wireshark-tutorial-4143298-5e45505c0f434a9ba2d3a8f70a850617.jpg)
:max_bytes(150000):strip_icc()/013-wireshark-tutorial-4143298-f169e33e47ba4aafb336b9d47029867d.jpg)
:max_bytes(150000):strip_icc()/014-wireshark-tutorial-4143298-f09d24778ff94ff29a2bbd3ee883fc4c.jpg)
:max_bytes(150000):strip_icc()/wireshark-colors-59512e8f3df78cae8137715b.png)
:max_bytes(150000):strip_icc()/015-wireshark-tutorial-4143298-91567e80185c4f16bfc46f6793c0301a.jpg)
:max_bytes(150000):strip_icc()/020__wireshark-tutorial-4143298-24bfe8984431438b9ba2ec43f701607d.jpg)