Isle how to hack
Isle how to hack
Hacking
Contents
Master Bypass Console
Spawn Location in the Facility
Spawn Location in the Radio Tower
The Master Bypass Console is an item required to hack objects. It can be found in two guaranteed locations and nowhere else: the Radio Tower and the room on the stairs that lead down to the Facility. This means that there are no more and no less than two Master Bypass Consoles in a single game.
The Master Bypass Console is only capable of hacking items that are locked by keycard readers. This includes Secured Crates and keycard doors. Hackable items are also shown by a rotating black circle around the keycard reader which is visible through walls, allowing the player to locate hackable items easily.
Hacking
Security Level 4 Hacking
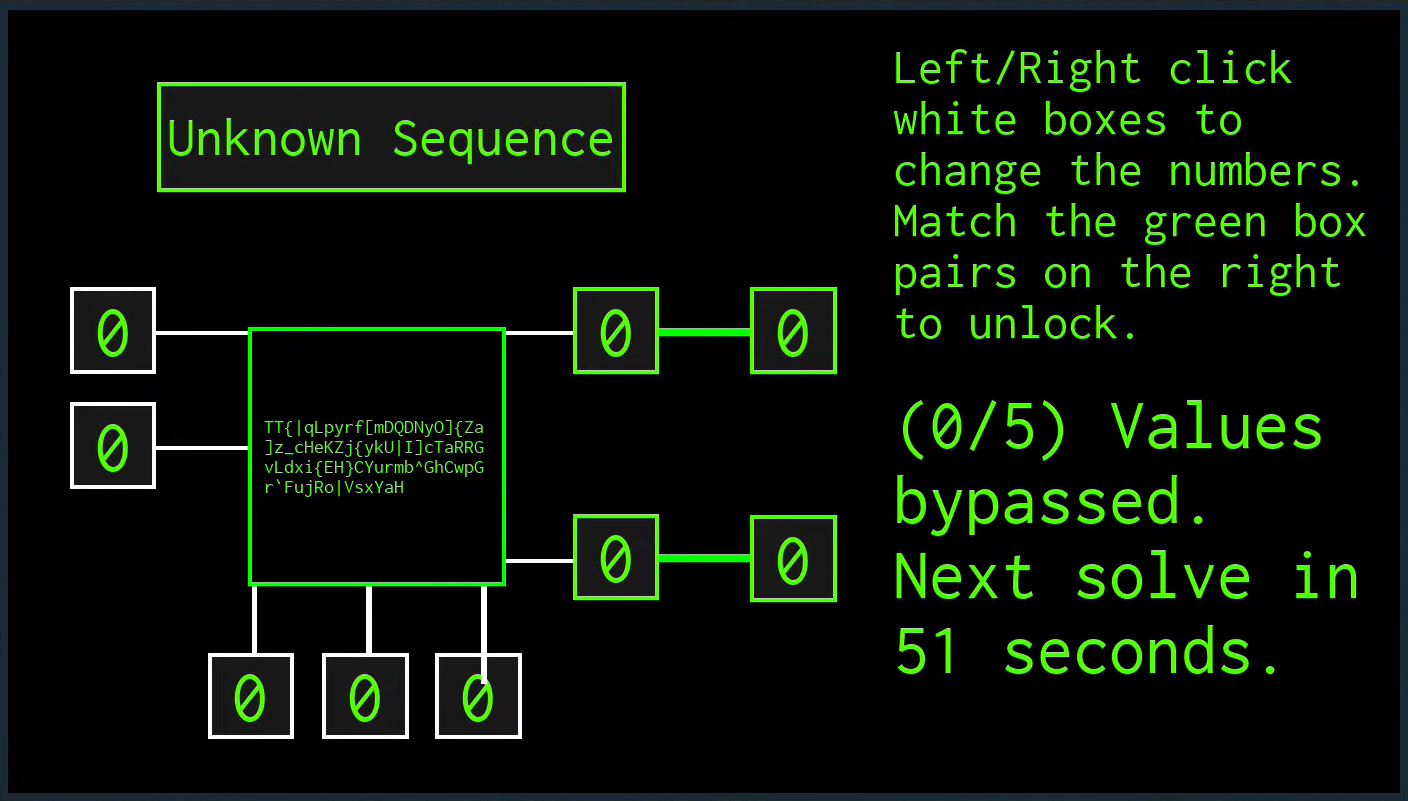
When you begin a hack, a mid-sized window will appear with many boxes and numbers. To the right of the boxes, there will be text stating that 0/X values have been bypassed, the X value being dependent on what level the object is. The boxes with white borders contain numbers 0 through 9 and are able to be changed by clicking on them. Left clicks increase the value by 1, while right clicks decrease the value by 1. Each box is considered an input, and these inputs affect the values of the right-most boxes. The ultimate goal of a hack is to get the right-most values equal to the boxes that are connected with red lines. Once the values are equal, the lines will turn green, completing the hack.
Currently, the effect of changing each value is randomized for each hack (as well as the solution), meaning there is no single method for guaranteed success. The recommended steps to follow, though, are:
Alternatively, you can either click the boxes randomly or attempting every single solution starting at 0,0,0,0,0 (or however many inputs there are) and going upwards, though both of those methods are extremely slow and may only work for lower difficulty hacks.
For a more in-depth guide to hacking, check the Advanced Hacking Guide page.
Value Bypassing
When trying to hack an object, the player can occasionally bypass a value. On the right side of the hacking screen, there will be text stating how many values have been bypassed so far. The following list is how many values there are per level:
How many seconds there is left depends on how many values have been bypassed already, and how much time has passed. The following list will show how much time it takes per level:
It’s possible to wait for every single value to be bypassed, though it would not be viable in gameplay. For example, trying to bypass every single value of a Level 4 object will result in 80% of the in-game day to pass, wasting almost an entire day. If the player is struggling on a system, their best choice of action is to wait until 1 or 2 values have been bypassed, then attempt to solve the system.
Solution Formulas
Hacks have predetermined ‘solution formulas’ that are unknown to the player. For example, a Difficulty 1 hack tends to have two different input boxes, which we will call A and B, and a single Output value. The formula for this output is A + B, which is unknown to the player. However, it can still be easily discovered through experimentation.
Difficulty 4 hacks, on the other hand, can get much more complex. They tend to have 5 separate inputs with 2 different outputs. A randomized formula could be:
The solution for this would be: C = 8, B = 5, E = 9, D = 5, F = 8
As you would think, such formulas would be near impossible to discover through experimenting with inputs. Therefore, the only way reasonable way to solve higher difficulty hacks would be to either make educated guesses (via the above steps) or to guess randomly, both with varying success rates.
Keycard Doors
These doors are rather obvious and you most likely already have seen them around the map. Keycard doors are most notably located on the shipwreck (for the armory and Engine room) and in the facility (for the room that disables the facility traps). For each keycard door, if you did not have a Master Bypass Console, a keycard of varying level would be required to open the door. The difficulty of the hack corresponds to the minimum level of the keycard that would open the door. For example, the engine room door requires a level 1 keycard to open, meaning the hack for it will be of difficulty 1, and the Facility door requires a level 3 keycard to open, meaning the hack for it will be of difficulty 3.
Secured Crates
Security Level 2 Crate
Secured Crates are crates normally found within or around the Facility. As discussed above, these crates are locked and require either the Master Bypass Console or a keycard to open. Each crate has a different security level ranging from 1 to 4. Security levels indicate both the minimum keycard required to open the crate and the difficulty of hacking it. Higher security level also crates have a cleaner look and provide better loot. This ranges from security level 1 crates spawning things like flashlights to security level 4 crates spawning things like flamethrowers and grenade launchers.
[ Roblox Isle ] Crate Hacking
ROBLOX ISLE EASIEST TEIR 4 CRATE HACKСкачатьПодробнее
Hacking lvl 4 crates (isle)СкачатьПодробнее
Island Hacker | Basic Hacking Guide (no math equations involved)СкачатьПодробнее
Hacking a Lv4 crate in under 5 seconds (Roblox isle)СкачатьПодробнее
Roblox | Isle: Hacking The Entire FacilityСкачатьПодробнее
[ Roblox Isle ] Crate Hacking v2СкачатьПодробнее
Roblox Isle | How to Get Persistent Badge / Island HackerСкачатьПодробнее
How To Hack Crates/Doors In The Facility In Roblox IsleСкачатьПодробнее
Hacking crates in 3 minutes or less! Part 1 (Isle)СкачатьПодробнее
Hacking level 3-4 crates in less than 3 minutes! (Isle)СкачатьПодробнее
[ Roblox Isle ] How to hack a Lv.4 crate in 5 secondsСкачатьПодробнее
Roblox Isle, How To Get Persistent Badge, Island Hacker
The Roblox Way HD 05:24
Описание
(If the video quality is bad, turn up your resolution to 1080p)
In this video I show you guys how to get The Persistent Badge which also gives you the Island Hacker Title
To get this badge you have to hack a level 4 crate in the facility
You dont have to be good at hacking to get this badge as there is a way to get it by being lucky, but if you are decent at hacking it makes it faster
Music — https://www.youtube.com/watch?v=h18gwLKQf_Q
Comment any feedback on the video
🔥I hope you guys enjoyed the video, make sure to like and subscribe so i can keep uploading content!🔥
Most recent channel videos:
More channel videos:
Useful links from this video
| Description | External Link |
|---|---|
| Join my Discord server! | https://discord.gg/uurbBnc |
Поделиться с друзьями:
Добавить временную метку
Фото обложки и кадры из видео
Roblox Isle, How To Get Persistent Badge, Island Hacker, The Roblox Way
Аналитика просмотров видео на канале The Roblox Way
Гистограмма просмотров видео «Roblox Isle, How To Get Persistent Badge, Island Hacker» в сравнении с последними загруженными видео.
Подписывайтесь на наш Telegram канал! @thewikihow открыть Мониторим видео тренды 24/7
How to Hack a Website: Step-by-Step Website Hacking Guide 2022
Table of Contents
What comes to mind when you imagine a hacker? Perhaps a hooded criminal, stealing information with super-whiz computer skills. The truth is, it wasn’t so hard for that hacker to learn how to hack a website. And, not all website hacking is criminal, either!
Some companies hire hackers to test their computer security, like banks, retail stores, and government agencies.
If you’re interested in webpage hacking, you’re in the right place. Today we’ll go through the steps on how to hack a website and introduce you to different types of cyberattacks and prevention methods.
Let’s get started!
How to Hack a Website Step-by-Step: Different Ways to Hack a Website
There are several ways for a hacker to perform website hacking. All he needs is to find the vulnerable point within the website to enter and gain access to the crucial information. In this article, we have mentioned some of the amazing tricks that you can perform to hack a website.
1. Hacking Online Website
The first method for how to hack a website and change it is by hacking an online website. We’ll hack “www.techpanda.org” as an example to demonstrate the steps for web page hacking. In this scenario, we’ll read the cookie session ID and impersonate a user session to gain admin information.
It is the JavaScript code adding a hyperlink with an on-click event. On clicking it, the event retrieves the PHP cookie session ID and sends it to the snatch_sess_id.php page along with the session id in the URL.
2. Session Impersonation
Different Types of Cyber Attacks
Unfortunately, there are a few different ways that hackers can get into a company’s cyberspace. Here are some examples of different cyber attacks.
1. SQL Injection Attack
An SQL injection attack entails a hacker providing a malicious SQL query to an application. The query gives the hacker access to read crucial information from the database and even execute unauthorized commands, resulting in critical data loss and compromise.
This type of cyberattack gives hackers the power to spoof identity, alter data, cause frauds, and damage company reputations. These attacks are widespread with the PHP and ASP applications because they have old interfaces. The severity of the injection attack depends on how skilled the hacker is. If the website is not protected with proper security measures, it can be easily exploited.
Different Types of SQL Injection Attacks
The attack has been divided into three categories depending on how they access the data and damage it. These are- In-band SQLi (Classic), Inferential SQLi (Blind), and Out-of-band SQLi.
How Does SQL Injection Work?
Impact of SQL Injection
Example
First, the attacker will find vulnerabilities and then inject the SQL query. As per the following example, the attacker takes out the necessary information for a specific product, which can be altered to read http://www.estore.com/product/product.asp?productid=999 or 1=1. This will send the below query to the database-
Due to condition 1=1, the statement will always be true and return all the product details.
How to Prevent This Attack?
You can prevent this attack by sanitizing the inputs to identify the unauthorized users to access the crucial data.
2. Cross-Site Scripting Attack
With this attack, a hacker impersonates the victim to gain victim data. These attacks are also referred to as XSS, and compromise the user’s interaction with an application. Under this attack, the attacker creates the same environment that keeps different websites distinct. If the attacker gets privileged access to the specific application, they can harm the crucial data stored within the application.
The attack starts with the victim’s access to the application or the web page. The attacker carries out the malicious JavaScript code in the victim’s web browser. The web page acts as a vehicle to deliver the injected code once the user accesses a web page. Some examples where the attacker can inject the code in the web page are- forums, comments, etc.
Impact of Cross-Site Scripting Attacks
How to Prevent Cross-Site Scripting Attacks
Different Types of XSS
This type of attack is simple to create. The attacker provides the code in the HTTP request of the application and gets the data through the immediate response.
In this attack, an application might receive the data from an untrusted source and includes that data in the HTTP responses for the server to process.
The data can be injected into the application via HTTP requests. For example, comments, contact details on a customer order, etc.
The comment section of the application allows users to submit messages as below.
The attacker can easily send a message that can even harm other users who can access the message from the comment section.
If the attacker controls the value of the input field, they can insert a malicious value to execute:
You searched for:
3. Denial-of-Service Attack (DDoS/DoS)
A distributed denial-of-service (DDoS) attack impacts the regular traffic of a targeted server by overflow the target with numerous requests. They’re usually carried out within networks of connected devices that are infected with malware and are controlled remotely by an attacker. These individual devices are called bots to which an attacker will send remote instructions to perform. When a bot targets the server, it will send a request to the target’s IP address and overwhelm the server resulting in severe damage.
Different Types of DDoS Attack
The following are the different types of DDoS attacks that are commonly practiced by attackers.
Impact of DDoS Attacks
Below is the impact that can be seen within the server and machines.
How to Prevent DDoS Attacks
4. DNS Spoofing Attack
Domain Name System (DNS) poisoning and spoofing mainly exploits the vulnerabilities of the DNS server and diverts traffic away from valid servers to fake ones. If the victim has accessed a fraudulent page, he will be transferred to another website that causes harm to your system. The main impact of this attack is data theft.
To perform this attack, a client requests an IP address from the DNS server. They then receive a response containing a fake IP address without an established connection to the address the client requested. So, the request goes to a malicious host, and the host returns the legitimate website to the client without a security certificate.
Different Types of DNS Spoofing Attack
Below are the different types of DNS spoofing attacks.
This type of DNS spoofing attack targets a valid DNS server and affects many users. For example- poisoning the DNS cache on the server, highjacking the DNS server, etc.
How to Prevent DNS Spoofing Attacks
5. Cross-Site Request Forgery Attack
Cross-Site Request Forgery (CSRF) attacks the victim and performs some unwanted actions as expected by the attacker on a web application without authorized access. The attacker tricks the victim into executing some illegal actions chosen by the attacker.
If in case, the victim is a regular user; the attacker can only perform actions such as transferring funds, changing their email address, and so forth. CSRF can impact the entire web application if the victim has administrative access.
The main impacts are a changed server state, data breach, and illegal transfer of funds.
How Cross-site Request Forgery Attacks Work
When a victim tries to access a website, the browser automatically picks their credentials from the saved cookies to make the login process seamless. Once users pass their login credentials, the site cannot differentiate between forged and legitimate requests. In such cases, attackers can easily impersonate the victim. Attackers typically follow this process:
Example of Cross-site Request Forgery Attack
GET https://abank.com/transfer.do?account=SomeAttacker&amount=$5000 HTTP/1.1
How to Prevent Cross-Site Request Forgery Attacks
Conclusion
We have only mentioned the most common attacks on a simple website where security has not been maintained. Today, technology is getting so advanced that it helps attackers get what they want. All they need is the proper usage of communication within the network. Each organization and website has its unique security policies and some robust strategies. But some hackers can hack into your system and create a blunder.
If you want to avoid such attacks on your website to protect its integrity, then you must understand how a website can be hacked and what measures can be implemented to avoid them. Go through this article, find the potential threat points for your website and eliminate the threats.
Interested in learning more about website security? Check out these information security and ethical hacking tutorials.
Sameeksha Medewar
Sameeksha is a freelance content writer for more than half and a year. She has a hunger to explore and learn new things. She possesses a bachelor’s degree in Computer Science. View all posts by the Author
Roblox Isle | How to Get Persistent Badge / Island Hacker
Kích thước video:
Hiển thị các điều khiển trình phát
NHẬN XÉT • 43
eaisest way: keep rejoining over and over until a crate has something really easy, like only 1 digit numbers or 0-0
so apparently, i did one with only moving one pad!
it was a gatling gun!
You. Are. A. Legend.
Hope you get 1k subs soon!
Oi mate keep going at this rate you’ll cover all the badges
@The Roblox Way Glad to hear it 😀
theres really no way to learn how to hack, theres no common pattern in all of them, you just learn how to find that singular pattern and make your way to the numbers needed
you just need to figure out what effect what and ur fine
@The Roblox Way I guess that’s true, once you hack a few level 4 crates, you figure out the basics and can occasionally open 1 or 2 crates quickly
While that is half true, as the formula changes every time, you can have a better chance of grasping how each one works with basic math skills. other than that, you cant really get good at it
How to get extinguishin badge?
Yay another video!
ree i wish there was a 3 level crate tutorial
@DaBeta Memes it still wouldn’t be 10 faster in all cases.
@some random guy Im saying pass guessing is 10x faster becayse instead of doing 0000 to 9999, its 000 to 999, meaning one less digit, making it 10x faster.
@DaBeta Memes not really 10x faster, lvl 4’s can have 16 and 0 while you have a lvl three with 157 and 296
Ok.
My brain just exploded
Its the same, except one less digit to pass guess. This makes it 10x faster to guess than a l4 crate.
man i dont know how to hack its so harddddddd
Im so bad at hacking lol
I guess no badge for me bcuz i am not good at hacking bruh
if i have the same hack of the video? HEHE BOY.
i tried to hack level 4 crate 6 days
HACKING IS JUST WAY TOO HARD IM LIKE A GOOD PLAYER IN THE GAME BUT HACKING IS MY WORST.
I EVEN TRIED PROGRAMMING BUT I JUST DONT HAVE THE SKILL FOR IT UGH WHY DONT I HAVE NO TALENT FOR HACKCING
HOW TO ESCAPE FACILITY? AFTER GOING TO VENT? PLEASE GIVE TUTORIAL
@Ash Blake To escape. Get the hacking device before you enter the ventilation. Go to disable security than disable the lasers, then get artifact D. Go raid the base for guns and loot. (optional)
@Tiggeristotallynotdumb dude dont laugh at me i took a day (ingame) just to finish a 3 security thing