Softether vpn how to use
Softether vpn how to use
4.4 Making Connection to VPN Server
Table of contents
After installing SoftEther VPN Client and creating a Virtual Network Adapter, configure a connection setting to connect to the Virtual Hub of the desired SoftEther VPN Server. This section describes the information that must be entered when creating a connection setting.
The settings described here are, for the most part, the same as the settings used to configure a cascade connection to VPN Server or VPN Bridge on a separate computer using the Virtual Hub of VPN Server or VPN Bridge described in 3.4 Virtual Hub Functions. The windows for editing the connection setting of the cascade connection and VPN Client are nearly the same, and the resulting operations when the connection settings are edited are also the same. Refer to the information described here when configuring a cascade connection.
4.4.1 Selecting the Proper Connection Method
Creating a Connection Setting
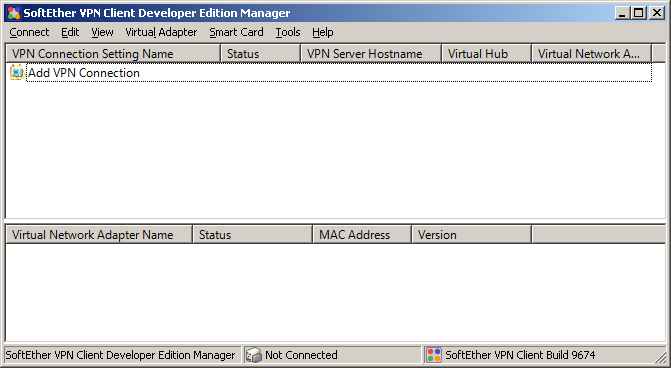
At the time SoftEther VPN Client is installed, no connection settings exist. To establish a VPN connection to SoftEther VPN Server, you must create a connection setting. To create a connection setting, select [New Connection Setting] on the [Connect] menu of VPN Client Manager. Hereafter, explanations on creating a connection setting and editing the settings assume this window is open.
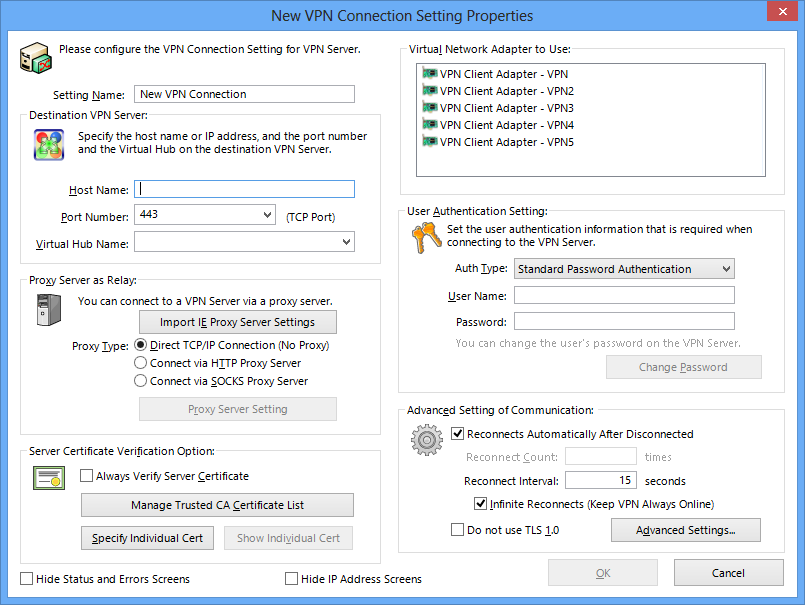
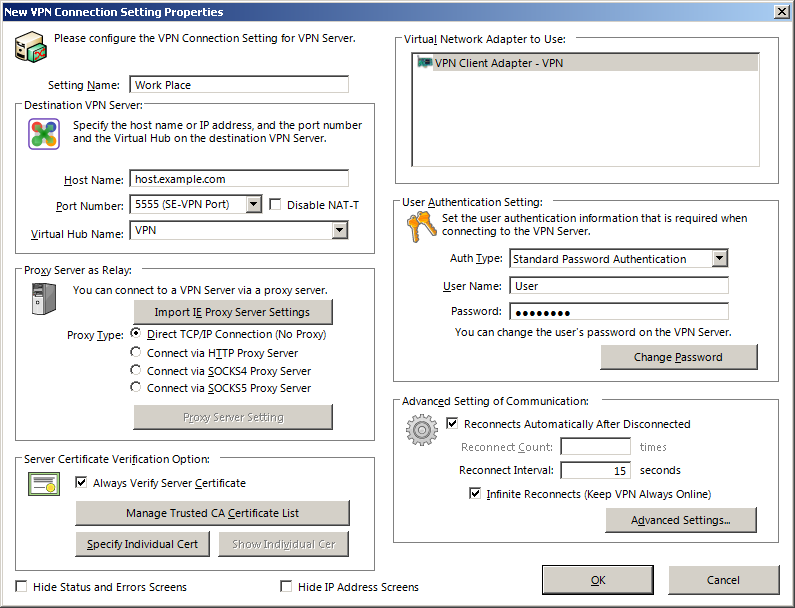
Window for Creating and Editing a Connection Setting.
To connect the computer with SoftEther VPN Client installed to the Virtual Hub of the desired SoftEther VPN Server, first you must click [Import IE Proxy Server Setting] to import Internet Explorer’s setting, or select the proper connection method according to the network environment of the client and server computers. Select the connection method in the [Proxy Server for Relaying] field. When using a proxy server, click [Proxy Server Connection Setting] and enter the required parameters.
Choose from the following three connection methods.
Specifying the Destination VPN Server
Regardless of the connection method, you must correctly enter the host name, port number, and Virtual Hub name of the destination VPN Server. The default port number is 5555, but you can specify any TCP/IP port waiting for incoming connections as the listener port on the destination VPN Server. When connecting via an HTTP proxy server or when using high firewall settings, consider using 443 (port for HTTPS access). For more information about setting the port number, please contact the VPN Server administrator.
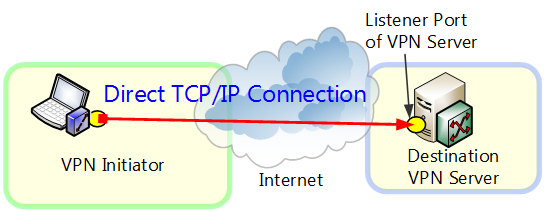
4.4.2 Direct TCP/IP Connection
Use a direct TCP/IP connection in an environment where only direct IP routing can be used to establish an IP connection between the VPN client computer and VPN server computer. Select this setting when, for example, the VPN client computer and VPN server computer are both directly connected to a global IP address usable on the Internet or when a normal NAT or transparent firewall exists between the two computers.
Direct TCP/IP Connection.
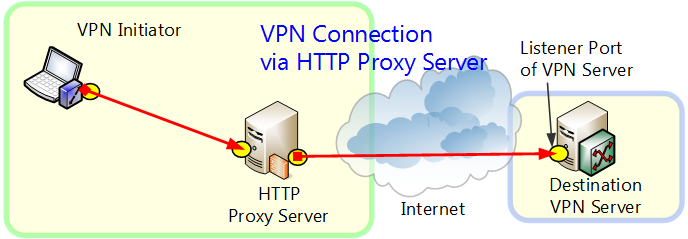
4.4.3 Connection Via HTTP Proxy Server
When a direct TCP/IP connection cannot be used, you can connect to VPN Server via an HTTP proxy server.
Connection Via HTTP Proxy Server.
To connect to VPN Server via an HTTP proxy server, select [Connect Via HTTP Proxy Server], and then click [Proxy Server Connection Setting] and enter the required information. For more information about the settings on the [Proxy Server Connection Setting] window, please contact the administrator of the HTTP server.
Proxy Server Connection Setting Window.
| You can connect through a standard proxy server that supports the CONNECT method. Depending on the proxy server, the connection via the CONNECT method may only be allowed through port 443. In this case, set port 443 of the destination SoftEther VPN Server as the listener port in advance, and then try connecting to that port. By default, port 443 is enabled on VPN Server, but separate software products may also use the same port, so caution must be exercised. For details, please contact the administrator of the destination VPN Server. |
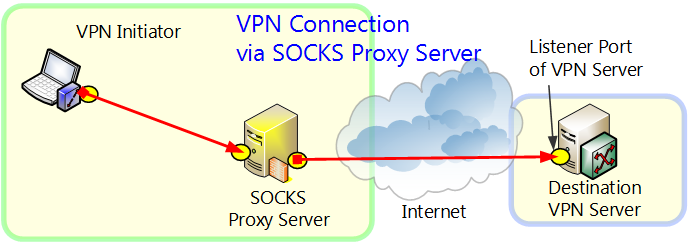
4.4.4 Connection Via SOCKS Proxy Server
When a direct TCP/IP connection cannot be used, you can connect to VPN Server via a SOCKS proxy server if available.
Connection Via SOCKS Proxy Server.
To connect to VPN Server via a SOCKS proxy server, select [Connect Via SOCKS Proxy Server], and then click [Proxy Server Connection Setting] and enter the required information. For more information about the settings on the [Proxy Server Connection Setting] window, please contact the administrator of the SOCKS server.
| At the time of writing this manual, SoftEther VPN Client supports SOCKS protocol version 4, but does not support version 5. |
4.4.5 Server-Certificate Verification
Enabling Server-Certificate Verification
As described in 2.3 Server Authentication, verifying that the server certificate of the destination VPN Server is valid on the VPN client computer guarantees through mathematical calculations that the destination VPN Server is the correct computer and that there is no «man-in-the-middle attacker». For high security applications requiring verification of the server certificate, use the server-certificate verification option.
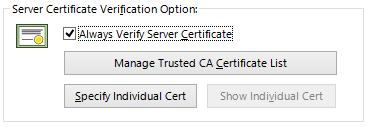
Checking the box next to [Always Verify Server Certificate] performs verification of the server SSL certificate when establishing a VPN connection using that connection setting. By default, this box is not checked, so check it if necessary.
Clicking [Manage Trusted CA Certificate List] opens a window with a list of certificates from trusted certification authorities managed by VPN Client (or the Virtual Hub in a cascade connection). You can use this window to add, delete, or confirm trusted certificates. When [Always Verify Server Certificate] is enabled and the user attempts to connect to the VPN, VPN Client (or the Virtual Hub) checks whether the certificate presented by the destination VPN Server is signed, according to the list of trusted certificates, and connects only to the VPN Server with a signed certificate.
Server-Certificate Verification Options Window.
Clicking [Specify Individual Cert] associates, in advance, the unique server certificate of the VPN Server to which VPN Client is connecting with that connection setting. If the destination VPN Server already has a server certificate, you can use this function to register that certificate, thereby authenticating the server. This is an easy way to authenticate a small-scale destination VPN server.
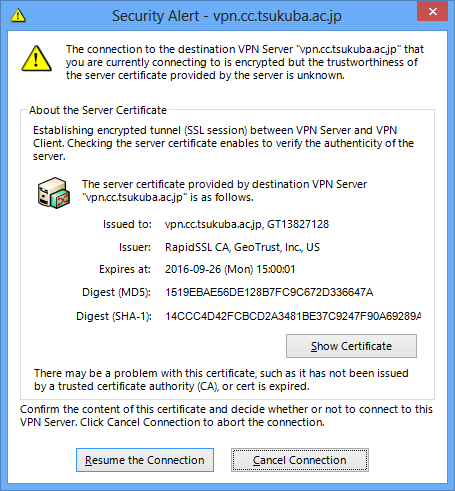
Window Displayed When Certificate Verification is Enabled and the Destination VPN Server Presents an Untrusted Server Certificate When Connecting (Only for VPN Client)
The [Security warning] window is displayed if it is determined that the certificate presented by the destination VPN Server cannot be trusted when connecting to VPN Server with the [Always Verify Server Certificate] option enabled. This window displays detailed information of the certificate presented by VPN Server. You can review the displayed information to determine whether to trust the destination VPN Server. For example, you can ensure the security of the destination VPN Server by checking the validity of the digest value displayed to the VPN Server administrator over the telephone or by using another relatively safe method. Clicking [Cancel Connection] cancels the connection attempt to VPN Server.
Security Warning Window Displayed for an Untrusted Server Certificate.
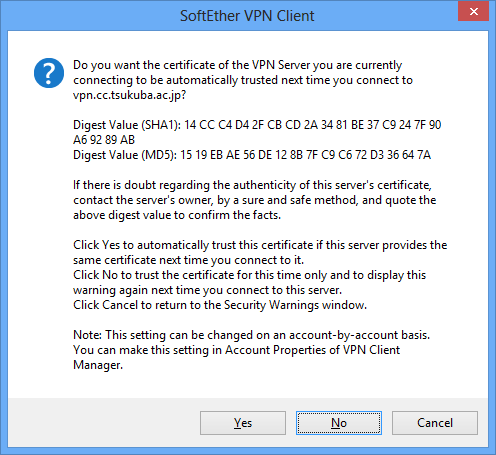
Clicking [Proceed with Connection] displays a dialog box asking the user whether to trust the certificate. Clicking [Yes] registers this certificate as a [individual certificate] for the connection setting, and the security alert is not displayed again if there are no changes to the certificate presented by VPN Server. Clicking [No] does not register the certificate.
Dialog Box Asking Whether to Trust the Server Certificate.
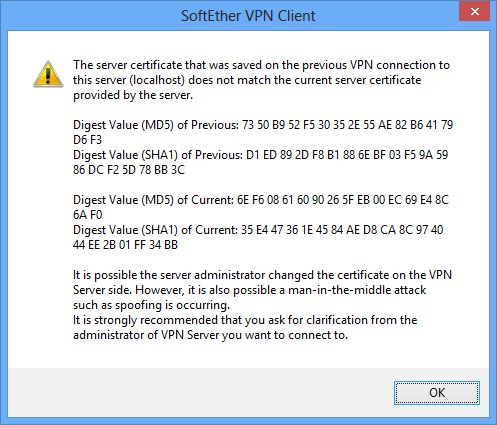
If the certificate presented by VPN Server differs from the individual certificate registered to the connection setting, the dialog box below is displayed. In this case, we recommend that you immediately terminate the connection.
Security Warning Window Displayed When Server Certificates Do Not Match.
| The security warning windows described here are only displayed on SoftEther VPN Client. When using a cascade connection on SoftEther VPN Server or SoftEther VPN Bridge, a connection error is automatically generated and these windows are not displayed, so caution must be exercised. |
4.4.6 Selecting a Virtual Network Adapter
The VPN Client user must select the Virtual Network Adapter for the connection setting. As described in 4.3 Virtual Network Adapter, a Virtual Network Adapter must be registered to Windows in advance. When creating a connection setting, select the Virtual Network Adapter you want to use to connect to VPN Server with the connection setting, from the [Virtual Network Adapter to Use] list.
4.4.7 User Authentication Setting
Selecting the Type of User Authentication
You must enter the settings related to user authentication on the connection setting. Select one of the following user authentication methods for [Auth Type].
You must enter a user name in [User Name] regardless of the selected user authentication type. The other required information varies depending on the selected authentication type.
Information Required for Anonymous Authentication
Other than the user name, no information is required to use anonymous authentication. For more information about anonymous authentication, please refer to 2.2 User Authentication.
Information Required for Standard Password Authentication and RADIUS or NT Domain Authentication
Enter the password for user authentication when using standard password authentication or RADIUS or NT domain authentication.
| The password entered here is saved and written to the disk drive as connection information of VPN Client. If this operation is not desirable for security reasons, you can leave the password field blank. This prevents the password from being saved as part of the connection setting and displays the password entry window each time you connect to VPN Server. |
For more information about password authentication, please refer to 2.2 User Authentication.
Information Required for Client Certificate Authentication
When using client certificate authentication, you must specify the certificate to be presented to VPN Server as the client certificate. To specify a certificate, click [Specify Client Certificate].
For more information about certificate authentication, please refer to 2.2 User Authentication.
The client certificate and private key specified here are written to the disk drive as setting information of VPN Client. Normally, only users with administrative rights can read files with VPN Client setting information, and therefore, it is safe. However, if, for example, a notebook computer with VPN Client installed is stolen, the contents of the hard disk can be analyzed and the private key data can be stolen. To eliminate this risk, we recommend using smart card authentication.
Information Required for Smart Card Authentication
When using smart card authentication, you must specify the smart card with the certificate to be presented to VPN Server as the client certificate and the smart card object name. First, click [Select Smart Card] and select the smart card you want to use. Then click [Specify Cert and Private Key] and select the certificate object and private key object for authentication. For more information about smart cards, please refer to 4.6 Using and Managing Smart Cards.
4.4.8 Use of the Smart Card Authentication
About an IC card, please refer to 4.6 Using and Managing Smart Cards.
4.4.9 Automatic Reconnection Function
You can configure the setting for automatic reconnection, as described in «Reconnection Setting When the VPN Connection Fails or is Dropped» in 2.1 VPN Communication Protocol. To use the automatic reconnection function, check the box next to [Reconnect When Lost Connection to VPN Server] and specify [Reconnection Count] and [Reconnection Interval]. Checking the box next to [Reconnection Endless (Keep VPN Session Always)] allows VPN Client to continually attempt to reconnect to VPN Server if the connection is dropped.
The automatic reconnection function cannot be used when using smart card authentication because the user would constantly be asked to enter the PIN code for user authentication in order to reconnect.
4.4.10 Connection Status and Error Message Displays
Checking the box next to [Don’t display connection status and error window when connecting to VPN Server] prevents the display of dialog boxes with error messages and the connection status to VPN Server. When this is enabled, the following dialog box, for example, is not displayed and the connection process runs in the background.
Dialog Box Displaying the Connection Status of VPN Client.
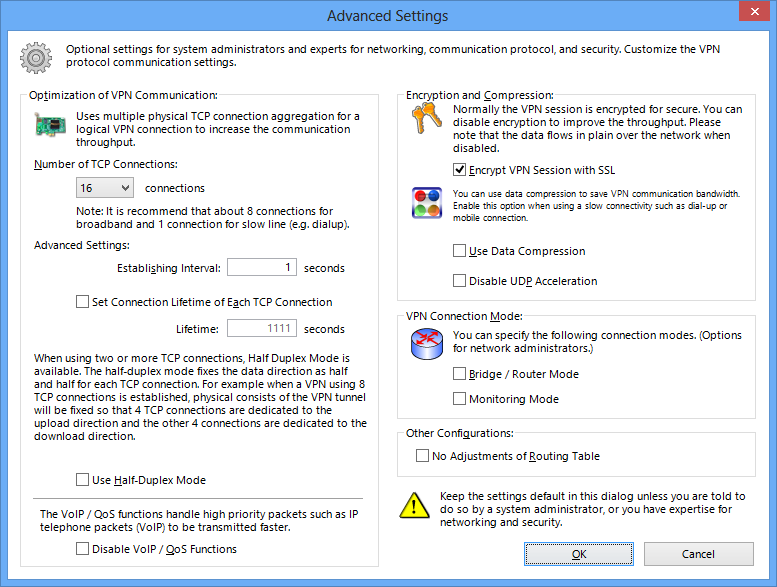
4.4.11 Advanced Communication Settings
To make changes to the advanced communication setting options, as described in 2.1 VPN Communication Protocol, click [Advanced Settings]. These settings are for the system administrator and users with a strong understanding of network communication protocols and network security. General end users should only change settings specified by the VPN Server administrator or network administrator.
[Advanced Settings] Window.
4.4.12 Number of TCP/IP Connections for VPN Session Communications
You can adjust the [Number of TCP Connections] setting on the [Advanced Settings] window. This setting is described in «Number of TCP/IP Connections for VPN Communications» in 2.1 VPN Communication Protocol.
4.4.13 Interval Between TCP Connections and Length of TCP Connection
You can adjust the [Establishing TCP Connection Interval] and [Keep Alive] settings on the [Advanced Settings] window. These settings are described in «Interval Between TCP/IP Connections and Length of TCP/IP Connection» in 2.1 VPN Communication Protocol.
4.4.14 Half-Duplex Mode Option
You can enable or disable the [Use Half-Duplex Mode] option on the [Advanced Settings] window. This function is described in «Using Half-Duplex Mode» in 2.1 VPN Communication Protocol.
4.4.15 SSL Encryption Option
You can disable the [Encrypt VPN Session by SSL] option on the [Advanced Settings] window. This function is described in «Disabling the Encryption Option» in 2.1 VPN Communication Protocol. When VPN Client is connected to VPN Server running on a local host (same host as the client), SSL encryption is not required, so this option is automatically disabled.
4.4.16 Data Compression Option
You can enable or disable the [Use Data Compression] option on the [Advanced Settings] window. This function is described in «Using Data Compression» in 2.1 VPN Communication Protocol.
4.4.17 Selecting the Connection Mode
You can enable either of the following two connection modes in the [Connection Mode Settings] field of the [Advanced Settings] window.
Checking the box next to either of these connection modes enables that connection mode for the connection session with VPN Server. For information about these special connection modes, please refer to 1.6 VPN Communication Details.
4.4.18 Routing Table Rewrite Process
By default, the [Don’t Modify Routing Table] option in the [Advanced Communication Settings] window is disabled.
Windows automatically rewrites the routing table to ensure proper VPN communication even when the Virtual Network Adapter side of VPN Client is set as the default gateway after connecting to VPN Server.
If, for a special reason, you do not want to rewrite the routing table, add a check to the box next to this option.
4.4.19 Startup Connection
You can set a connection setting for startup connection by using VPN Client Manager to select a connection setting and then clicking [Set as Startup Connection] on the [Connect] menu. When a connection setting is set for startup connection, a connection to VPN Server is automatically started using that connection setting when Windows is started.
If, for example, you want to maintain a constant connection to a specific Virtual Hub when the computer is running, set that connection setting to startup connection and enable the [Reconnection Endless (Keep VPN Session Always)] option. In this way, VPN Client automatically attempts to connect to VPN Server using the specified connection setting when Windows is started, even if a user is not logged on to Windows.
The icon of the connection setting registered as the startup connection changes as follows in VPN Client Manager.
Icon of the connection setting When Set to Startup Connection.
4.4.20 Exporting and Importing Connection Settings
Exporting and Importing
You can export a connection setting registered to VPN Client and save it as a file. An exported connection setting can also be copied by importing it to VPN Client running on the same or a separate computer.
To export a connection setting, select the connection setting and click [Export VPN Connection Setting] on the [Connect] menu. Next, specify the file name of the connection setting you want to save.
You can easily import an exported connection setting simply by double-clicking the connection setting file in Explorer or on the folder window. To import a connection setting using VPN Client Manager, click [Import VPN Connection Setting] on the [Connect] menu and specify the file name of the exported connection setting file.
Using the Export and Import Functions
The VPN Server or Virtual Hub administrator can use these functions to distribute a connection setting to users. The user can then double-click the connection setting file to easily add the connection setting data to VPN Client running on the user’s computer. The imported connection setting can also be edited by the user.
Content of the Exported Connection Setting File
The connection setting is exported as a special text file with the extension .vpn. The content of the connection setting file is as follows.
As shown in the example above, all content of the connection setting file is written in text. Any hiragana, kanji, or other multibyte characters are UTF-8 encoded. Normally, this text file does not need to be edited, but you can manually edit this file or write a program to automatically create a connection setting file, as shown above.
4.4.21 Creating a Shortcut for a Connection Setting
You can create a shortcut file for a connection setting registered to VPN Client. This shortcut file is the same type of shortcut file that can be created for files or folders in Windows.
To create a shortcut file for a connection setting, select a connection setting, click [Create VPN Connection Shortcut] on the [Connect] menu, and then specify the name of the shortcut file to be created. Once a shortcut file is created, it can be placed anywhere on the computer where a normal file can be set in Windows. For example, you can place the shortcut file on the desktop or add it to the Quick Launch bar.
Connection Setting Shortcut File.
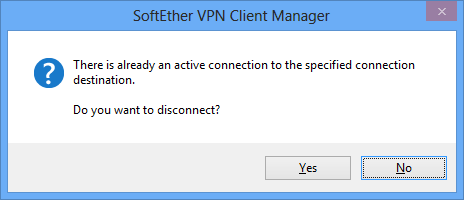
When the shortcut file for a connection setting is double-clicked while that connection setting is offline, the VPN connection for that connection setting is automatically started. When the shortcut file for a connection setting is double-clicked while VPN Client is connecting or is connected to the VPN, a dialog box is displayed asking whether to terminate the connection for that connection setting. Clicking [Yes] terminates the connection.
Dialog Box Displayed When Starting a Shortcut for a Connection Setting That is Already Connected.
4.4.22 VPN Server and VPN Bridge Cascade Connection Setting
You can use the same user interface as that used to create and edit a connection setting with VPN Client Manager to edit the settings to cascade-connect a Virtual Hub of VPN Server or VPN Bridge to a separate Virtual Hub with VPN Server Manager, as described in 3.4 Virtual Hub Functions.
You do not have to enter the following items when configuring the cascade connection settings.
Tutorials
Table of contents
This page describes how to build some typical examples of VPN networks.a
SoftEther VPN is an essential infrastructure to build-up IT systems on enterprises and small-businesses.
Ad-hoc VPN
Make an ad-hoc VPN consists of the small-number computers with SoftEther VPN. Despite long-distance, it is easy to communicate mutually with any kinds of LAN-oriented protocols.
LAN to LAN Bridge
Geologically distributed branches are isolated as networks by default. SoftEther VPN lays virtual Ethernet cables between your all branches. Then all computers of all branches are connected to the single LAN.
Remote Access to LAN
Employees need to connect to the company LAN from outside or home? Remote Access VPN realizes virtual network cable from a Client PC to the LAN from anywhere and anytime.
SoftEther VPN can build-up flexible and dependable virtual network around Clouds. Amazon EC2, Windows Azure and most of other Clouds are supporting SoftEther VPN.
Join a Local PC into Cloud
Your desktop or laptop PC can join into the Cloud VM network. You can make use of Cloud VM as if it is on your local network easily.
Join a Cloud VM into LAN
Your Cloud VM can join to your company LAN with SoftEther VPN. Anyone on your company can access to the Cloud VM without any settings.
Cloud to LAN Bridge VPN
SoftEther VPN keeps a virtual dedicate Ethernet line from the Cloud to the LAN 24h/365d. You can consider remote Cloud private network as a part of your corporate network.
Cloud to Cloud Bridge VPN
Using Amazon EC2 and Windows Azure, or using two or more remote datacenters of a Cloud service? SoftEther VPN can make a single united network between all Cloud VMs despite differences of physical locations.
SoftEther VPN supports several mobile devices including iPhone and Android. Your smartphone is now a part of your on-premise or Cloud network by using SoftEther VPN.
iPhone and Android
Windows and Mac Laptops
Your mobile PCs with Windows or Mac can easily connect to SoftEther VPN anywhere and anytime, despite firewalls or packet filters on Wi-Fi or overseas ISP. Windows RT is also supported.
SoftEther VPN is also an ultra-convenient tool for effective system management by IT professionals on enterprises and system integrators.
Remote Management
A lot of servers, clients and printers of your client companies are distributed around the state? SoftEther VPN helps a network administrator as a handy tool. Just from your desk, you can reach to any networks which you have installed SoftEther VPN in advance.
Building Your Own Cloud
You want to build and provide your own Cloud service which can beat Amazon EC2 or Windows Azure? SoftEther VPN helps you to build an inter-VMs network and remote-bridging network between your Cloud and your customer’s on-premise.
VPN for Network Testing, Simulation and Debugging
SoftEther VPN is not a program only for building remote network. It can be used for network design, test, and simulation by IT professionals. For example, delay, jitter and packet loss generator is implemented on SoftEther VPN so network designer can test VoIP phones under the bad-condition IP network.
SoftEther VPN is also convenient for home users. You can be proud of using enterprise-class VPN for your home-use.
Remote Access
Access to your home server or digital appliance from outside? Set up SoftEther VPN Server on your home PC and gain access to your server or HDTV recorder from anywhere even the opposite side of the earth, through the Internet.
Comfortable Network Anywhere
Are you a business man and running around the world? Most of Wi-Fi and local ISPs of several countries are discomfort to use because of packet filtering or censorship. So set up your private relay server on your home PC and use it from fields to gain ease.
Your network administrator hesitates to assign you global IP address? Your company has a firewall on the border between the private network and the Internet? Do not worry. SoftEther VPN has a strong function to penetrate troublesome corporate firewalls.
Dynamic DNS and NAT Traversal
Unlike legacy IPsec-based VPN, even if your corporate network doesn’t have any static global IP address you can set up your stable SoftEther VPN Server on your corporate network.
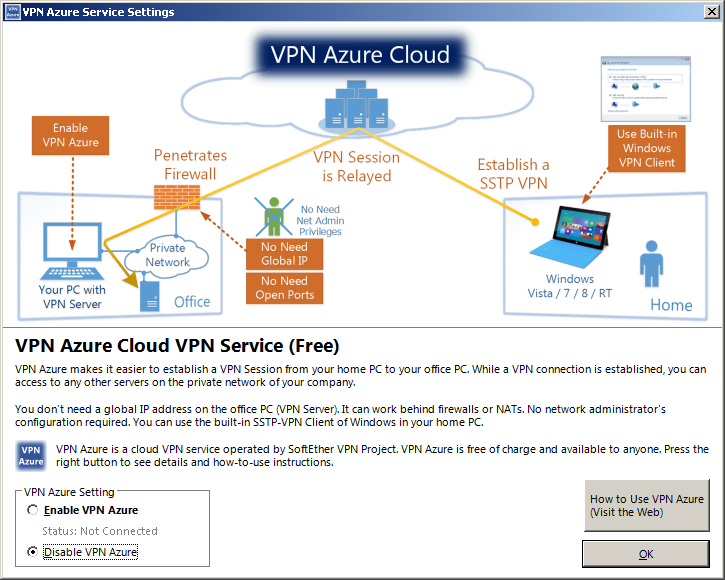
VPN Azure
If the corporate firewall is more restricted and the NAT Traversal of SoftEther VPN doesn’t work correctly, instead use VPN Azure to penetrate such a firewall.
IPsec-based VPN protocols which are developed on 1990’s are now obsoleted. IPsec-based VPN are not familiar with most of firewalls, NATs or proxies. Unlike IPsec-based VPN, SoftEther VPN is familiar with any kind of firewalls. Additionally SoftEther VPN requires no expensive Cisco or other hardware devices. You can replace your Cisco or OpenVPN to SoftEther VPN today.
Penetrates Firewall by SSL-VPN
Troubling with IPsec-based legacy VPN products? Replace it to SoftEther VPN. SoftEther VPN Protocol is based on HTTPS so almost all kinds of firewalls permits SoftEther VPN’s packets.
Replacements of Cisco or other hardware-based VPNs
Cisco, Juniper or other hardware-based IPsec VPNs are expensive for set-up and management. They are also lack of usability and compatibility with Firewalls. Replacement of them to SoftEther VPN is very easy because SoftEther VPN also has the L2TP/IPsec VPN function which is same to Cisco’s.
Replacements of OpenVPN
Are you still using OpenVPN? SoftEther VPN has more ability, better performance and easy-configurable GUI-based management tools. SoftEther VPN has also the OpenVPN Server Clone Function so that any OpenVPN clients, including iPhone and Android, can connect to SoftEther VPN easily.
Examples of Building VPN Networks

L2TP/IPsec Setup Guide for SoftEther VPN Server

About this Guide and SoftEther
This guide helps you install and operate SoftEther. SoftEther is an extremely versatile but still very user friendly VPN system. It supports it’s own SoftEther protocol as well as these common protocols: L2TP, SSTP, IPsec, OpenVPN.
PPTP is not supported as it’s no longer considered to be secure.
Note: This guide makes a few assumptions:
Installation and configuration will take approximately 15-30 minutes.
VPN Server Installation
This chapter explains the basic server installation.
Requirements
Requirements for the VPN server
Minimum
This guide will use Windows as the system of choice
Recommended/Optional
Download
For any supported OS:
Download the installer from softether-download.com. The component you need is the «Softether VPN Server». Select the appropriate operating system and processor architecture.
After all selections are made, download the file on top of the list.
Server Installation
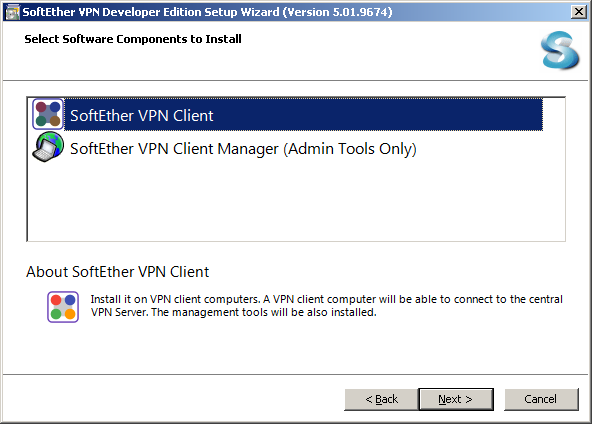
Run the installer on your server. When asked, select «SoftEther VPN Server». You can optionally install the «Admin tools only» selection on any machine you want to manage this server from later. The VPN server itself already contains the admin tools.
Accept the license agreement in the next step. Then continue with the installer. Leave all settings on their default values.
Initial Server Configuration
Note: Everything you configure in this chapter can be changed later. None of the settings are final. You can also at any time reset your server so feel free to experiment later on.
The server configuration is automatically started after the installer completes. You can also find it in the start menu. By default, the local machine will already be in the list of VPN servers.
Click «Connect» to connect to the local server. The first time you connect you will be prompted to enter a server password. Please enter a secure password (preferrably generated by a password manager). Anyone on the internet can try to break this password once you make the VPN server accessible.
A randomly generated password is shown below.
JavaScript is turned off. Open a text editor and place your cat on the keyboard as an alternative random number generator. New
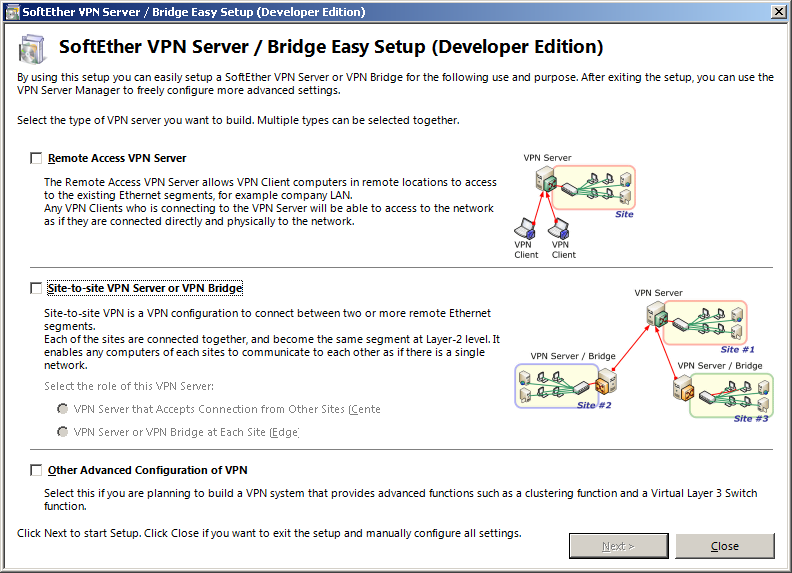
VPN Type
The first time you connect you will see an «Easy Setup» dialog. Check the «Remote Access VPN Server» option and click «Next». You will be asked to confirm your selection. After confirmation, you can name your hub. By default, the name is «VPN» but you can change it as you like. In most cases you want to leave it on its default value.
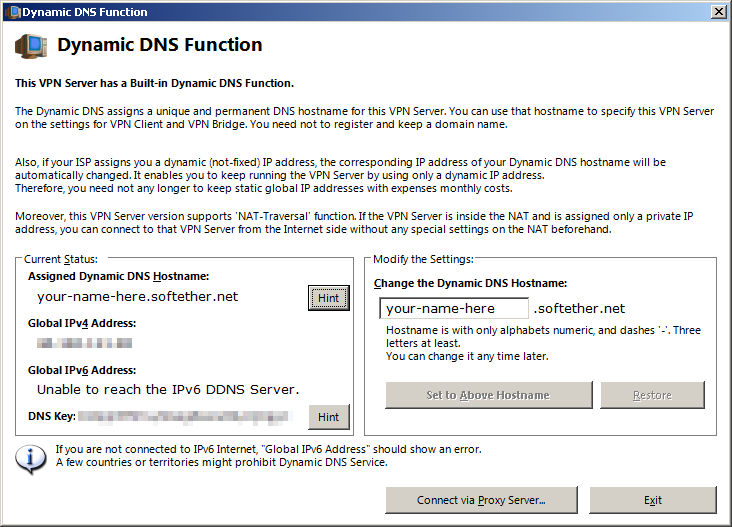
Dynamic DNS
Next you will be asked about a dynamic DNS name. If you have a fixed IP address you can ignore this page and just click «Exit».
Otherwise, chose a name you like before exiting. This feature can be completely disabled at a later point if you don’t want it enabled.
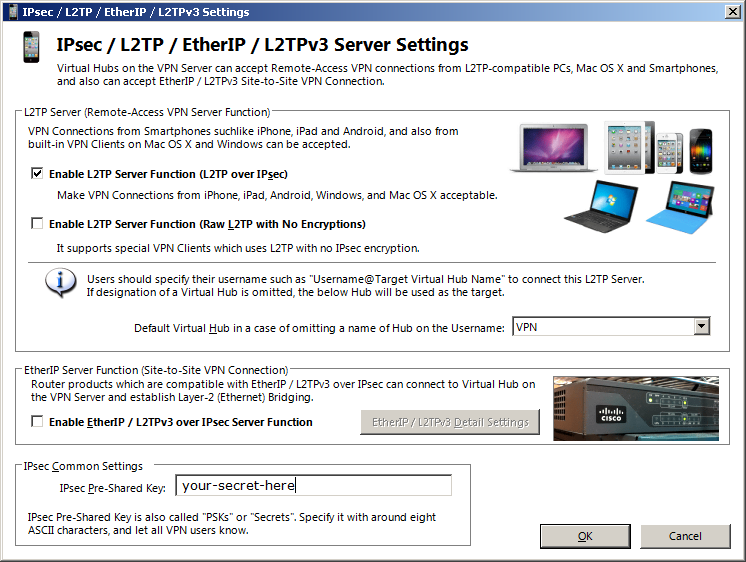
L2TP and IPSec
Next you will be asked about L2TP. L2TP is a VPN protocol that is supported by most operating systems. This means that if you enable it, you won’t need to install a VPN program on your clients. If you want to connect using L2TP you can check the first box «Enable L2TP Server Function (L2TP over IPsec)».
Enter a shared secret in the «IPsec Pre-Shared Key» box at the bottom.
Later on, that key has to be entered on all devices that connect via L2TP VPN. This means if you change this later, all devices will lose connectivity.
Enter something that can also be typed on a phone keyboard and is limited to ASCII. ASCII means this:
A randomly generated pre-shared key is shown below.
JavaScript is turned off. Open a text editor and place your cat on the keyboard as an alternative random number generator. New
When you’re done, click «OK». If your chosen shared secret is 10 or more characters, you will get a warning that long secrets make problems with some versions of Android. Read the message carefully, and decide for yourself whether to keep or change the key. I never had problems with Android, in fact Google recommends 32 character secrets for their own cloud services.
VPN Azure
The next screen is for VPN Azure Services. In most cases, you can disable them in the lower left corner of the window. VPN Azure Services allow you to run your VPN server in an environment that doesn’t normally allows you to operate a VPN server. This can be your company network as well as your home network if you can’t configure the router your provider forces you to use.
VPN Azure will add some delay to your VPN connections. If you’re unsure whether or not you can run a VPN server in your network, try to run it without APN Azure first.
Note: VPN Azure will only work with the MS-SSTP VPN protocol.
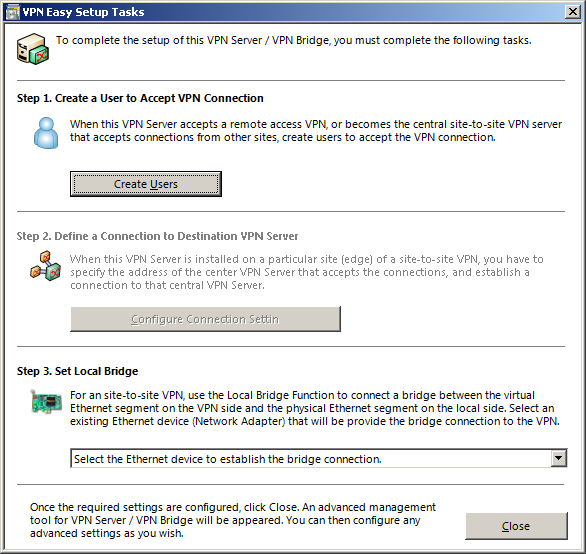
Final Steps
This is the last screen of the initial configuration. You can perform a few final configurations here. Creation of users is explained in a later chapter. Do not bridge the VPN adapter yet (Step 3). Depending on the type of VPN access you want to grant, you might not want to bridge the adapter. See the chapters below for when to bridge adapters and when not to.
Configuration
This chapter explains how to configure your VPN server. It explains configuration for the most common VPN access types and all user authentication types.
Configuration Overview
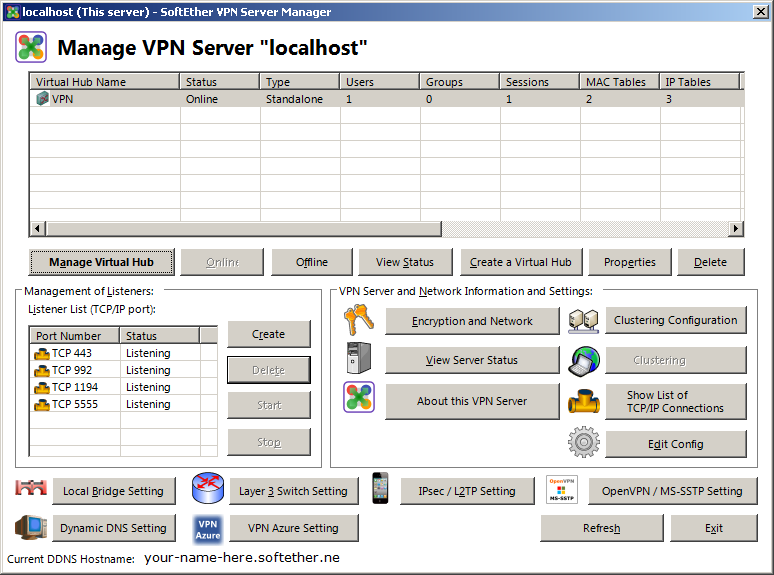
After you’ve completed the initial configuration during the installation process, this will be the window that is shown whenever you connect to the server. The main configuration window appears crowded at a first glance. The window is however divided into three sections.
The top section is where you configure most of the VPN settings. This includes users, access restrictions, and routing configuration.
The middle section is for the general server configuration. Here you’ll make changes that will have an effect on the entire server. The only function you need in most cases is the «Encryption and Network» button. You can use this to change your password or install a server certificate.
The bottom section of the dialog is to bring up various configuration windows. Most of those were already shown to you during the initial configuration steps.
Network Configuration
At this point you want to give your VPN server a static IP address if you did not already do this. If you don’t do that, you risk your server becoming unreachable in case your local DHCP server assigns it a new IP. As an alternative, you can check your DHCP configuration. Some DHCP servers allow you to make reservations. You can use that to have it always assign the same IP to your VPN server.
You also want to open at least one (but preferrably all) TCP ports shown in the main window in your firewall and forward them on your router if they need forwarding. If you want to accept OpenVPN connections, forward at least one UDP port also. You can configure OpenVPN UDP ports with the «OpenVPN» button in the bottom right corner.
You normally don’t want to change the ports, but the configuration window allows you to add and remove ports as you want. By default, SoftEther listens on 443, 992, 1194 and 5555. Port 443 is the one that SoftEther VPN clients will default to. If you remove that port, your users have to select another port number. SoftEther makes no distinction between VPN types. All TCP ports accept all VPN types. However, most L2TP and SSTP implementations don’t allow users to set the ports. Depending on the protocols you enabled, you have to forward additional ports that are not explicitly listed in the management window.
SSTP is enabled by default. You can disable it on the bottom right in the main window.
UDP Hole Punching
This VPN server supports NAT traversal via UDP hole punching. This means that it will try to abuse how UDP works to forward ports if you don’t do this yourself. Whether NAT traversal is in effect or not, can be seen by connecting to the server from a VPN client. If NAT traversal is in effect and was used to make the connection, a message will be displayed on the client. To disable this feature, change bool DisableNatTraversal false to bool DisableNatTraversal true in the ServerConfiguration section of the configuration file. How to edit the file is shown in the next chapter.
Disabling dynamic DNS
If you want to disable the integrated dynamic DNS client, you can do so by editing the configuration.
Note: Disabling dynamic DNS also disables VPN Azure support.
Note: you cannot edit the file directory in the «Edit Config File» window itself, however, you can edit the real config file in the installation directory if you shut down the VPN server service before editing.
VPN Access Type
There are three possible types of access you can configure. This is access to the LAN, access to the Internet, and access to both. You can at any time switch from one type to another by reverting the changes made to get one type and then applying the changes needed to get another type.
Access to Internet and LAN
This type is useful if you’re setting up this VPN in a company and want all traffic to flow through your company network. This is recommended if you hand out company laptops and mobile phones to users.
There are two ways to grant access to the LAN and the internet at the same time. The simple configuration will be explained first.
Simple Configuration
Use this type if you want the simplest configuration and maximum compatibility with devices in your LAN.
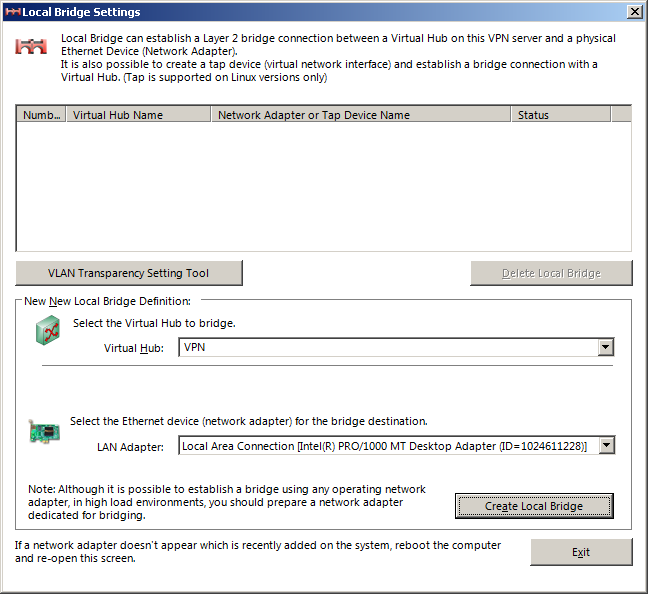
This is the simplest type to configure but also the least flexible. In the main window, open the «Local Bridge Setting». Select your hub from the drop down and select the network adapter to bridge this hub to. If you can chose from multiple adapters, pick the one that is connected to your LAN.
Click on «Create Local Bridge» and then exit the dialog.
Your VPN is now configured. Authenticated users will appear as if their device was connected to the LAN. When they connect, they will get an IP address assigned by your local DHCP server. Nobody will know that these people are from another network. They can access all LAN resources and the internet as if they were locally connected.
SecureNAT Configuration
Using SecureNAT places the VPN users into their own subnet. To do so, simply enable SecureNAT in the hub properties (see below on how to reach this). Do not change any of the values unless they conflict with an existing network. Note that because your users appear on another network, things like broadcasts over the LAN will not propagate between VPN and LAN.
Access to LAN Only
Use this type if you’re setting up this VPN server in a data center, or when you set it up at a slow home connection with a small bandwidth.
This type of VPN will allow users to connect to your LAN, but if they try to access anything outside of it (for example a public website), their computer will use their normal internet connection for this. This reduces the bandwidth requirement and you’re not held accountable if users visit illicit websites.
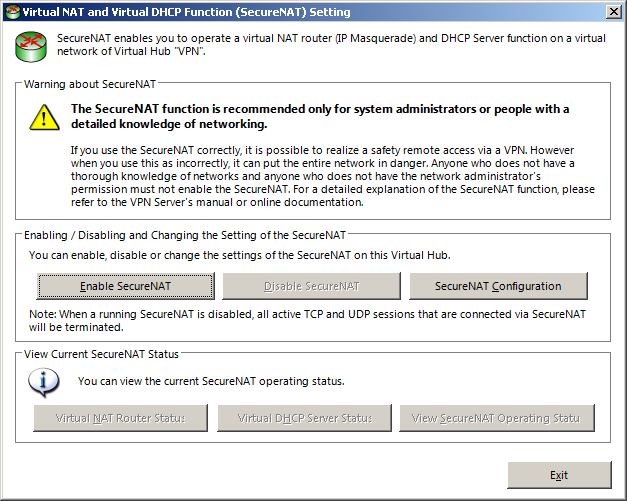
In the main Window, double click your hub or select it and click «Manage Virtual Hub». The window that pops up will be explained further down in more detail, for now, click on the large «Virtual NAT and Virtual DHCP Server (SecureNAT)» button.
Click «Enable SecureNAT» and confirm the alert with OK.
Click on «SecureNAT Configuration»
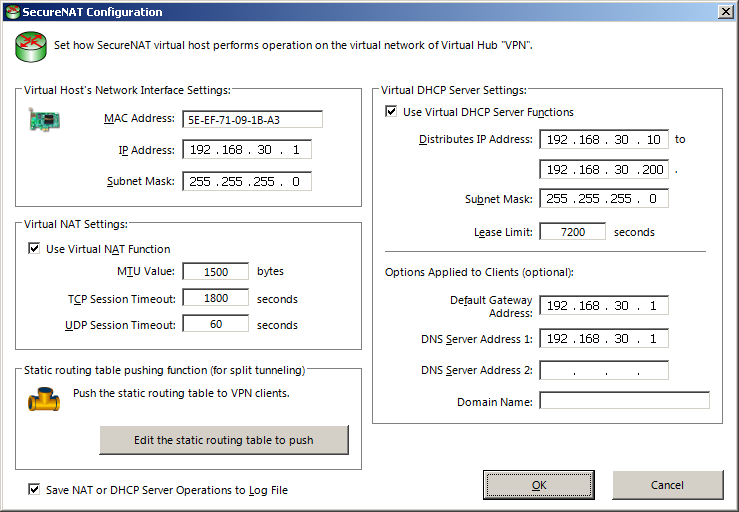
In this window you can change the network configuration for the virtual network. You normally don’t need to touch the basic settings, but you can change the IP address ranges of the DHCP server and the IP address and netmask of the virtual network adapter if they conflict with another network.
In the lower right portion, clear the field of the «Default Gateway Address» so it’s empty. Clearing the «DNS Server Address» fields is optional.
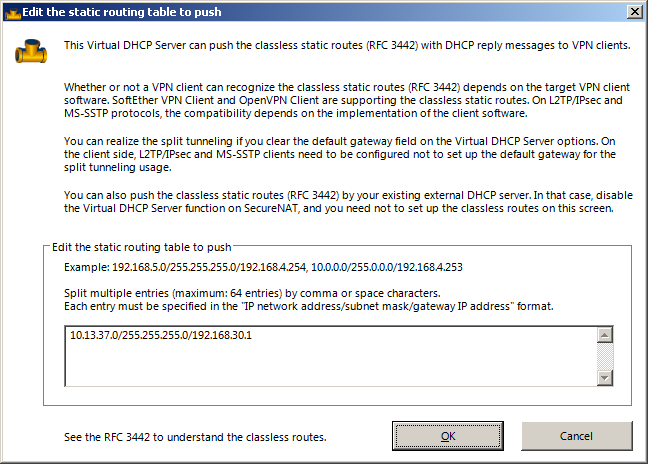
When you’re done, click on the «Edit the static routing table to push» button.
In this window you configure access to your LAN network. For this you need to know the network address of the LAN as well as the subnet mask. You enter the configuration in the format network/subnet/router as seen in the screenshot.
The router IP is the «IP Address» field in the top left of the previous dialog. If you did not change the default, it’s likely 192.168.30.1
Once you are done, you can exit with «OK» button twice to get back to the hub settings, and exit from there using the «Exit» button.
Access to Internet Only
Use this type if you’re setting up this VPN server to bypass restrictive firewalls, for example at a public Wifi network. It also helps to keep traffic away from spying eyes to some degree. See the traffic security warning further down to get to know what this means.
This type of VPN will make a device route all traffic through the VPN, but will not grant access to any devices in the network this VPN server is.
To configure this type of VPN, enable SecureNAT as instructed in the previous chapter. DO NOT delete the default gateway address, and DO NOT add entries to the static routing table. Keep it empty.
Click «OK» to accept the settings and «OK» again to go back to te hub window
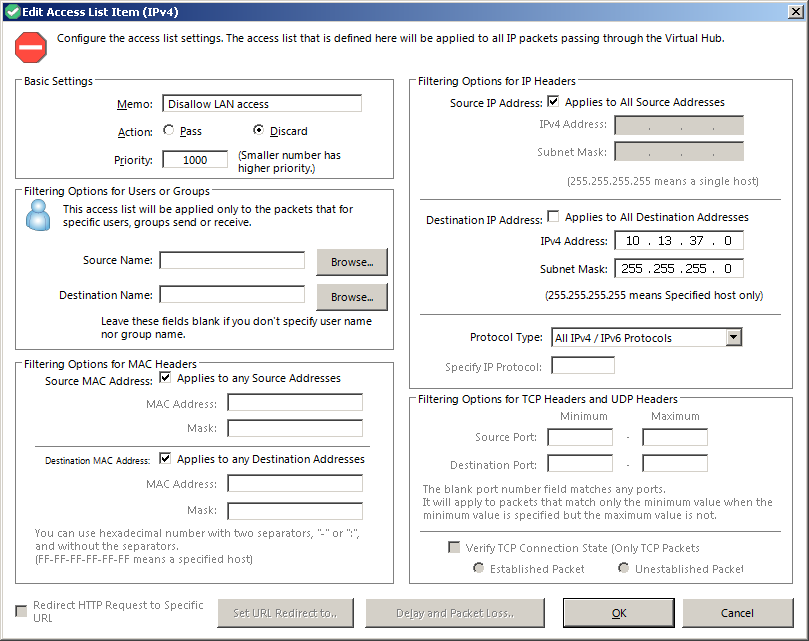
Back in the hub window, click on «Manage Access Lists» in the top left section. Click «New (IPv4)» and add a rule to discard traffic to the LAN. Set the name to anything you like, set the type to «Discard», then fill in your LAN network and subnet address on the right side of the Window. Fill it into the destination section only, then click «OK».
Repeat this step again but this time, fill the addresses into the Source fields only.
If your LAN has IPv6 set up, create two rules for the IPv6 ranges too.
After you’re done, click «Save», then exit the hub manager
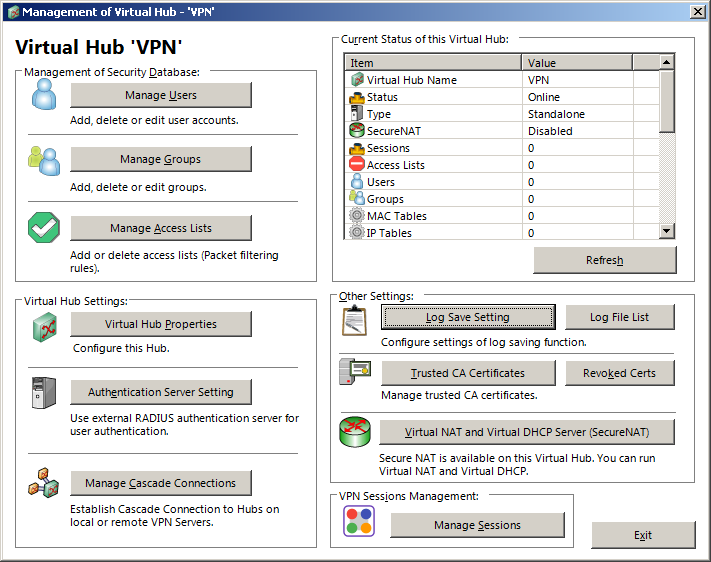
Managing Users and Groups
Users and groups are managed through the hubs. Each hub has its individual user and group settings. Double click on the hub you want to manage in the main window to bring up the hub window.
Groups
Groups are optional and can be used to apply security policies to users more easily. A user can be in at most one group. To add a group, click on «Manage Groups», then «New». The security policy will be explained in a later step.
Users
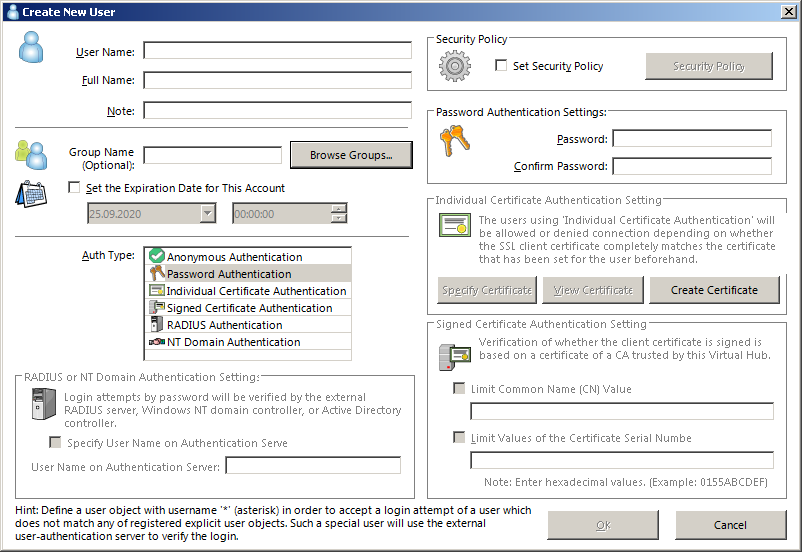
Create a new user by clicking on «Manage Users», then «New» in the hub manager.
The minimum you want to do is setting a user name, selecting «Password Authentication» from the authentication type, then define a password and click «OK». Authentication types are explained further below.
This window allows for a few additional configurations, such as the security policy (this is identical to the policies in groups) and an automatic expiration of accounts.
Special User
You can use * as a user name. This user is then used for all logins that don’t match any other defined name. This special user can only use RADIUS or NT domain authentication. Selecting other authentication types will leave the «OK» button disabled.
If you create this user, you can manage users on your RADIUS or Active Directory server and don’t need to fiddle with any more users on this VPN server.
User Authentication Types
This chapter explains the user authentication types available on the VPN server. Each user account can have exactly one authentication type. You cannot create duplicate user names to bypass the single auth restriction. If you want to allow a user to log in via different means, you need to create multiple users with different names.
Anonymous Authentication
This type requires no form of authentication at all. Merely knowing the user name will grant access to the VPN. There is almost no practical reason to use this type. There’s only two scenarios where you want to use this type. One is that you run a VPNGate server (but then this is usually done for you), the other scenario is that you can otherwise secure the connection, for example by only permitting a certain IP address to connect.
Password Authentication
This is the most common form of authentication. Simply specify the password on the right side of the user window and you’re done.
Note: This VPN implementation allows users to change their password. To do so, they have to open the properties of the VPN connection in their client, then click on «Change Password». If you don’t want to allow this, you can disable password changes. There’s a «Deny Changing Password» policy in the security policy settings.
Individual Certificate Authentication
This authentication type uses a certificate instead of a password. You can specify the certificate on the right side of the user management window. The client also offers you to generate a certificate. Certificate authentication is generally more secure than password authentication, but it’s also more difficult to configure, especially on mobile platforms.
Note: The server does not needs the private key of the certificate. After you install the certificate on a user machine, you want to either delete the private key from the server, or store it in a secure location.
If you decide to use certificates, use the «Signed Certificate Authentication» method instead. It allows for a more fine grained control, and if you run an Active Directory, you can set up tools and scripts to automatically push certificates to the clients that are allowed to use the VPN.
Signed Certificate Authentication
This method is almost identical to the other certificate authentication, but instead of manually configuring a certificate for each user, you can make the server accept trusted certificates automatically.
This setting allows you to apply limits in the lower right corner of the window. There you should use the «Limit Common Name» option, and write the user name into the text box. This prevents users to log in with their certificate but a different user name.
For this authentication type to work, you need to run a CA. An example with a portable CA implementation that runs on most operating systems is provided further below. To trust a CA, you can add its certificate in the hub manager. You can add multiple certificates if you have multiple CA. Adding CA certificates needs to be done only once for each hub, not for every user.
In the hub manager, you can also revoke certificates. This is useful if a user left the company but the certificate has not expired yet. This is also useful if the certificate got lost and a new one is needed. You can remove revoked certificates from the list once they’re expired.
Note: The VPN server can operate as kind of a CA. You can create root certificates as well as certificates signed by said root. You should generally not do this, because the certificates have way too many permissions assigned to them. User certificates created by this system can be used to create and sign further certificates. This would allow user A to create and sign a certificate for user B, then log in as user B on the server.
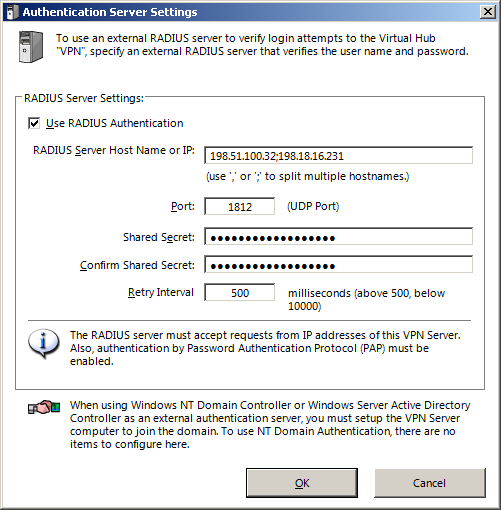
RADIUS Authentication
This authentication type uses a RADIUS server. To use this authentication type, you have to click on «Authentication Server Setting» in the hub properties and configure your server values.
The authentication server must accept connections from the VPN server. The protocol in use will be PAP (Password Authentication Protocol).
When using RADIUS for a user, you can configure an alternative user name in the lower left corner of the dialog. This is useful if the user name on the RADIUS differs from the VPN user name. Setting a custom name is only available for regular users. For the special * user, you can’t specify an alternate name.
NT Domain Authentication
This authentication type uses a local NT Active Directory domain to authenticate users. This is likely the method of choice for an enterprise installation.
This method has no method for configuring servers and users. For this method to work, the VPN server itself must join the domain against which authentication is to be performed.
When using an NT domain for a user, you can configure an alternative user name in the lower left corner of the dialog. This is useful if the user name on the active directory differs from the VPN name. Setting a custom name is only available for regular users. For the special * user, you can’t specify an alternate name.
Automatic VPN Accounts
The * user in combination with an NT domain is a powerful method of automatomatically enabling VPN for all users in a domain. Using this method, you don’t have to worry about disabling accounts on the server when users are removed and/or disabled in the NT domain.
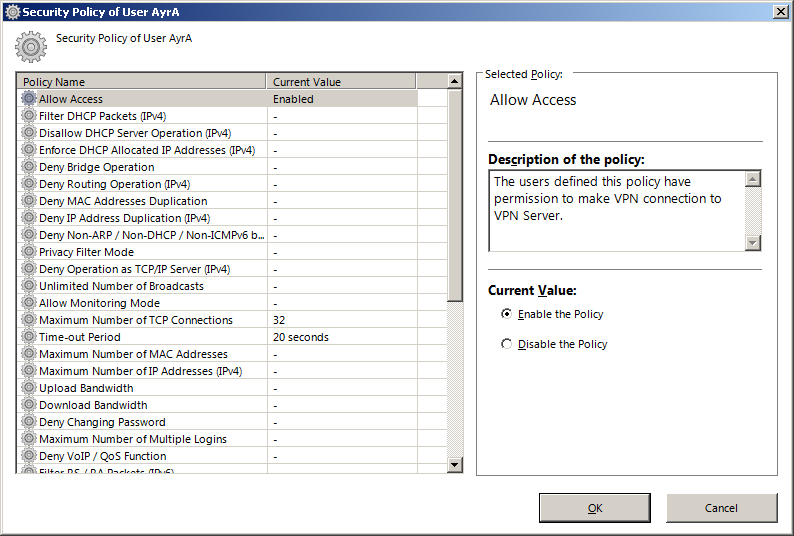
Security Policy
By default, users are not restricted in any way on the VPN server. They can do the same things they can do if they were on premise. The security policy can be used to restrict users. Policies can be applied to individual users and user groups. The available policies for users and groups are identical. In most cases, you want to apply basic policies to a group, then put all users into that group.
Recommended Restrictions
Security policies protect your network from misconfiguration but also malicious actions.
Policies (unless it doesn’t makes sense) are usually on a per-session basis. Each policy has a description. Some policies might break applications that VPN users need.
Note: Most policies that have an «IPv4» in parenthesis at the end exist twice, once with «IPv4» and once with «IPv6». The policies will not be mentioned twice here but you almost always want to enable both.
Optional settings
This chapter explains some policies you might want to define depending on your needs
Privacy Filter Mode
You want to enable this if you have people connect to this VPN that should not interact with other people on the same VPN. An example would be if the VPN is offered to your customers. You don’t want them to detect other customers on the network. You might also want to enable this if the VPN is used to reach a data center.
Maximum Number of MAC Addresses
You normally want to limit this to one. It prevents the user from changing/injecting MAC addresses into the network.
Maximum Number of IP Addresses
Same as with the MAC address limit. Usually you want this to be set to one. It prevents the user from injecting IP addresses into the network or consuming many addresses from the DHCP server.
Upload Bandwidth & Download Bandwidth
You can define these policies if you expect many users and don’t want them to consume too much bandwidth.
Deny Changing Password
Useful for accounts that are used for demonstrational purposes. This only has an effect for password based login. Users cannot change the RADIUS or NT domain password regardless of this policy setting.
Maximum Number of Multiple Logins
This limits the number of simultaneous logins a user can have. You want to set this to at least the number of devices the user uses. Recommendation: Set to one more than the user should ever simultaneously use. This avoids problems if the user lost his internet connection for a brief moment and tries to re-establish the VPN connection before the old one expired.
Deny VoIP / QoS Functions
This prevents a user from prioritizing his traffic. This WILL NOT prevent a user from using VoIP.
VPN Client Automatic Disconnect
Setting this to 86400 will disconnect connections that run for longer than 24 hours.
Filter All IPv6 Packets
If your network is not using IPv6, you can set this policy to avoid any problems with autoconfigured IPv6.
Backup and Restore
It’s generally a good idea to create a backup of your server configuration. To do so, use the «Edit Config» button in the main window to back up and restore the configuration to a file.
Note: Be careful when you use this feature to copy the configuration from one server to another. Configuration that is bound to hardware (for example a bridged adapter) will likely not apply properly on another server. For the purpose of redundancy, consider using the «Clustering Configuration» in the main window instead.
Operating a CA
Operating a CA is recommended if you opt for certificate based authentication. This chapter explains how to do this with XCA. XCA is a CA that can run under all common operating systems and is fairly easy to operate.
Download
You can download XCA via Gitload. For Windows, there’s an msi (installer) and a zip (portable).
Creating a Database
XCA can use common SQL servers as backend as well as SQLite file based database. For simplicity, this documentation focuses on the SQLIte method as it requires no other dependencies.
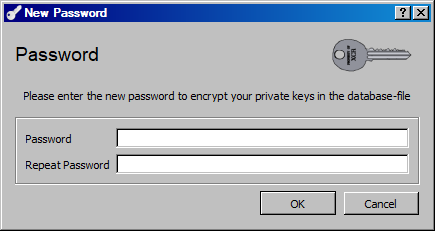
Create a new database in the file menu. You will be prompted to specify a file name, then you will have to enter a password to protect private keys. This should be very strong (20+ characters).
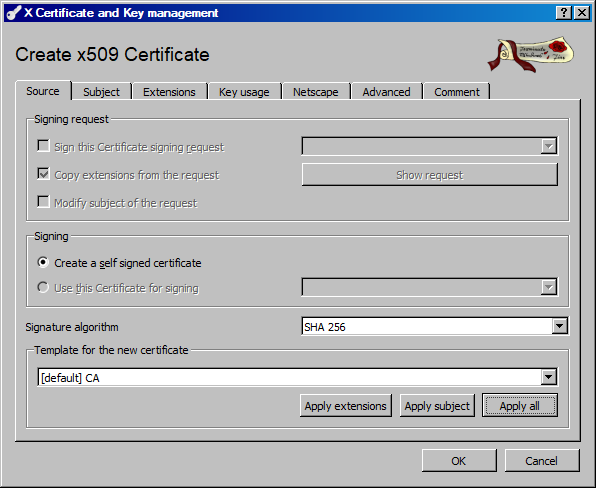
Creating the CA Certificate
Creating a CA certificate is simple.
Exporting the CA Certificate
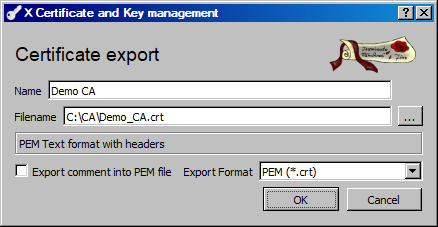
Select the CA certificate in the main window, and click «Export».
Change the name if you want to (this has no effect on the certificate) and select any path you like. Make sure the export format is set to «PEM (*.crt)»
The CA certificate is public information. It’s usually a good idea to have this certificate present in an easily accessible location, for example a web server.
Using the CA Certificate
This certificate can now be imported into the VPN server and the VPN client.
On the server, you can import it in the hub manager. You have to import the certificate into every hub you want it to be valid for, using the «Trusted CA Certificates» button.
On the client, press CTRL + R or select the appropriate option in the «Tools» menu of the client manager. Importing the certificate is optional but it avoids a security prompt for when the user makes the first VPN connection.
Creating the Server Certificate
The server certificate is used for clients to ensure that they are talking to the appropriate machine.
Using the TLS Certificate
The TLS certificate can now be imported into the VPN server. To do so, you need to export the certificate and the key. Exporting the certificate is identical to exporting the CA certificate, so check the chapter above.
Exporting the key is almost identical. Select the key that matches your certificate in the «Private Keys» tab adn click «Export». Enter a name and a path. Make sure the format is «PEM private (*.pem)» and click «OK»
Now on the server, import the certificate in the server manager (not the hub manager) using the «Encryption and Network» button.
Creating the VPN Template
It’s a good idea to create a template for VPN user certificates. When the first certificate expires and you have to issue a new one, you will likely have forgotten the original settings, so a template will help in that regards.
Templates can be changed at any time, but be aware that this will not change the contents of already issued certificates.
Using a Pre-made Template
Copy all the code in the box below, then in the «Templats» tab, right click into the empty area and select «Paste PEM Data», then «Import All». Note: The «Internal Name» will be empty, you can double click the template after importing it and assign it a name. The name is displayed in the «Template» drop down box whenever you create a certificate. The pre-made template has all the proper key usages already selected.
Creating a VPN Client Certificate
This process is very similar to the TLS certificate
Using the Client Certificate
The client certificate can be supplied as authentication mechanism in the VPN client. Check the chapters below for how to configure the client and how to distribute pre-made settings for your users.
Working with Signing Requests
A proper CA never comes into contact with the private key of the user certificates. This reduces the chance of key compromise, but it depends on the user to retain a copy of the key and to generate a signing request.
Creating a Signing Request
One of the easiest ways to create such a request is using OpenSSL. The user has to use these two commands to create a private key and a request. The request (not the private key) is to be sent to you. The request command will ask the user various questions. None of the information is really important as we can override them on the CA.
Using a Signing Request
After the request has been sent to you, you can import it in the «Certificate signing requests» tab. The request will then appear in the list as «Unhandled»
To convert the request into a certificate, right click the request and select «Sign»
This brings up the certificate creation window. The top part has the signing request filled in.
Note: Apart from the public key, any value from the signing request can be overridden by you.
After signing, the request will appear as «Signed» now. The certificate can be exported and sent to the user.
Note: You can’t export the private key, since there is none. The user is already in possession of the key.
You can delete the signing request once you are done, but there is no real reason to do so because it serves as kind of a history.
Using RSA Public Keys
Instead of using a signing request (as it is done for a proper CA), you can also just use public keys. The user has to type these two commands and send you the pub.key file:
To import the key, copy the contents of the file to the clipboard, then use the «Import PEM Data» context menu option in XCA to import the key.
After that, create the certificate as you would with an RSA private key. The difference is that instead of generating a key, you select the imported key.
VPN Client
This chapter explains the installation and configuration of the VPN client. You only need to do this if you want to use the SoftEther protocol.
Installation
The installation is pretty straight forward. Unless you require a custom installation path, you can install the client using default settings.
The client can (like the server) be administered remotely. In that case, you can install the remote administration tools instead. Be aware that remote administration is disabled by default in the client and has to be enabled in the «Tools > Options» menu
Initial Configuration
The client needs a virtual network adapter to perform VPN operations. When you create yorur first VPN connection, you will be asked to create an adapter. You can also at any time create an adapter in the «Virtual Adapter» menu. Up to 128 adapters can be created.
When you create an adapter, use the default «VPN» name. If you want to manage multiple clients or distribute VPN connections automatically, be sure that the adapter name is identical on all machines.
Resetting Adapters and IP
Managing VPN Connections
You can create a new VPN connection using the top entry in the list, or the «Connect» menu item.
You will then be required to fill in a few entries. They depend on how your server was configured. You want to enter a setting name and a host name. The port 443 is usually OK but if your VPN server is shared with a web server, another port can be chosen from the drop down list, or you can enter a port manually. Note that SoftEther listens for all protocols on all ports. The names in parenthesis are mere suggestions of what the port is usually for. The client will always use the SoftEther protocol.
When you leave the host name and port field, the client tries to automatially query the server for hub names. If you opted to hide hubs from anonymous users, you have to write in the name manually.
Below the host name you can configure a proxy server in case you need to use one.
Below the proxy settings are the certificate settings. For your own security, you should enable certificate verification. You can now either supply the root certificate that will be used to sign the server certificate, or you can supply the server certificate directly. Specifying a CA certificate is usually better because otherwise you have to supply a new certificate every time the old one expires or is replaced for other reasons.
On the right side you can pick the VPN adapter. There’s usually only one in the list. If you want to open multiple VPN connections simultaneously, you have to assign each one a different adapter.
Below the adapter settings are the user authentication settings. Select the method of choice and supply the required information for that method. If you use password authentication, you can also change the password here.
Note: You can’t change external passwords (from RADIUS or NT domain).
Below the user settings are advanced settings. You almost never want to change anything there.
Deploying VPN Connections
The best way to depoly VPN connections is to use remote control for the client. This is explained further below. As an alternative, you can create and configure a VPN connection the way you want it, then right click the entry in the VPN list and export it. You can then import it into another client using the «Connect» menu.
This will not export/import the CA list (see «Tools» menu or press CTRL + R )
Restricting the Client
In a work environment you might want to restrict the VPN client. To do so, use «Tools > Switch Operation mode»
In most cases, you want to switch to «Easy Mode» to not overwhelm the user. Enable the setting locker and enter a secure password.
Switching to easy mode is not required, and users can switch back to the normal mode at any point. They will not be able to add/edit/delete VPN connections until they confirm the password and disable the setting locker.
A shortcut can be placed on the user desktop to make connecting to the VPN even simpler.
A VPN connection can be set as «startup connection» in the context menu. This makes the VPN connect automatically at system start before the first user logs in.
Remote Management
The VPN client, like the server, can be managed remotely. This should only be enabled if remote management is desired, for example in a corporate environment.
Installing Remote Tools
The remote administration tools are part of the regular VPN client installer. You only have to install them if you don’t have the VPN client itself installed locally. The remote administration tools are installed together with the regular client installation. You don’t have to install the tools on the client that is being remotely connected to.
To create a shortcut for remote management, duplicate the regular VPN client desktop shortcut, and add /remote to the command line.
Enabling Remote Management
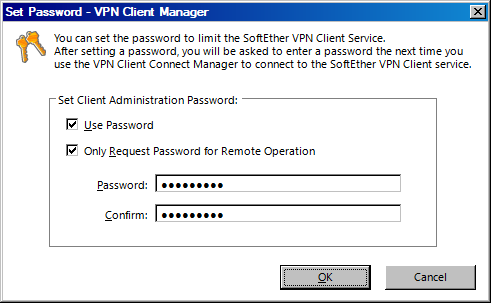
In the client, go to «Tools > Options» and check the «Allow Remote Management of VPN Client Service» checkbox, then click «OK»
After enabling remote management, press CTRL + P (or use the appropriate «Tools» menu option) to set a password. Check the checkbox to use the password, and optionally to only require the password for remote management. If you don’t check the second checkbox, you have to enter the password each time you start the client.
8.2 Install on Windows and Initial Configurations
Table of contents
This section describes how to install SoftEther VPN Client to an operating system with Windows 2000 or later. This assumes that in the Windows operating system, no extra application software is installed after performing a clean install of the system.
8.2.1 Installation Procedure Using the Installer
Preparing the Installer File
The installation of the Windows version of SoftEther VPN Client is very easy as it is almost completely performed automatically. To install VPN Client, you can download the latest VPN Client installer file from the SoftEther VPN Project website (http://www.softether.org/).
VPN Client Installer
Starting the Installer
Start the installer by double-clicking the VPN client installer file. Using the installation wizard, you can select the name of the installation directory. (By default, the program is installed to Program Files\SoftEther VPN client on the system drive.) The VPN Server process writes large log files to the installation directory, so we recommend selecting an area on the hard drive that has a large amount of disk space and is quickly accessible.
Specifying the VPN Client Installation Directory.
During the installation, the end-user license agreement may be displayed. Please thoroughly read the agreement. If you agree to the terms and conditions, the installation continues.
VPN Client End-User License Agreement.
The installer automatically registers the SoftEther VPN Client system service and sets the program to automatically start in background mode at Windows startup.
8.2.2 Precautions After Installation
When installation of the Windows version of VPN Client is completed, the SoftEther VPN Client service is already running in the background on the Windows system. Normally, the computer does not have to be restarted after installation of the program. However, if you expect to use the local bridge function while using a network adapter that supports hardware offloading, as described in 3.6 Local Bridges, we recommend that you restart the computer.
To check whether the VPN Client installer properly installed the SoftEther VPN Client service to the Windows system, click [Control Panel] > [Administrative Tools] > [Services], and check that [SoftEther VPN Client] is displayed on the list of services.
8.2.3 VPN Client Manager Operations
After VPN Client is installed, use SoftEther VPN Client Manager to perform all VPN Client operations. For detailed operations of VPN Client using VPN Client Manager, please refer to 4. SoftEther VPN Client Manual.
8.2.4 Operating with vpncmd
You can also use the command line-based vpncmd software to control VPN Client. For information about detailed vpncmd operations, please refer to 6. Command Line Management Utility Manual. For example, you can combine vpncmd and an existing schedule software program to initiate a connection to a specific connection setting at a specified time and, later, automatically terminate the connection of the connection setting.
SoftEther VPN Project recommends using VPN Client Manager to control VPN Client and using vpncmd as a supplemental management utility for automating simple repetitive tasks.
8.2.5 Creating a Virtual Network Adapter
The first operation that must be performed to use VPN Client is to create a Virtual Network Adapter. For more information about creating a Virtual Network Adapter, please refer to 4.3 Virtual Network Adapter. You cannot define a connection setting if a Virtual Network Adapter is not registered.
8.2.6 Configuring a Virtual Network Adapter
After you create a Virtual Network Adapter, you must properly configure the Virtual Network Adapter. The administrator of the destination VPN Server should have already provided instructions for configuring the Virtual Network Adapter. Configure the Virtual Network Adapter using these instructions.
In particular, if the DHCP server does not seem to be operating on the Layer 2 segment of the destination Virtual Hub, the IP address of the Virtual Network Adapter must be manually configured on the client computer.
8.2.7 Creating a Connection Setting
After creating a Virtual Network Adapter, create a connection setting for connecting to a Virtual Hub on the destination VPN Server, and try establishing a VPN connection. Follow the instructions from the VPN Server administrator for entering the required settings. In addition, adjust the connection method according to the configuration of the local network to which the client computer running VPN Client is connected. For more information about operating VPN Client, please refer to 4. SoftEther VPN Client Manual.
After configuring all the settings, connect to the connection setting and establish VPN communication.
Why SoftEther VPN
Table of contents
SoftEther VPN is one of the most powerful and easiest VPN software in the world. It is freeware, developed as an academic research project in University of Tsukuba, Japan.
Walkthrough
Read the walkthrough to grasp the key features and advantages of SoftEther rapidly.
Features
Architecture of SoftEther VPN
Virtualization of Ethernet devices is the key of the SoftEther VPN architecture. SoftEther VPN virtualizes Ethernet devices in order to realize a flexible virtual private network for both remote-access VPN and site-to-site VPN. SoftEther VPN implements the Virtual Network Adapter program as a software-emulated traditional Ethernet network adapter. SoftEther VPN implements the Virtual Ethernet Switch program (called Virtual Hub) as a software-emulated traditional Ethernet switch. SoftEther VPN implements VPN Session as a software-emulated Ethernet cable between the network adapter and the switch.
You can create one or many Virtual Hub with SoftEther VPN on your server computer. This server computer will become a VPN server, which accepts VPN connection requests from VPN client computers.
You can create one or many Virtual Network Adapter with SoftEther VPN on your client computer. This client computer will become a VPN client, which establishes a VPN connections to the Virtual Hub on the VPN server.
You can establish VPN sessions, as called ‘VPN tunnels’, between VPN clients and VPN servers. A VPN session is the virtualized network cable. A VPN session is realized over a TCP/IP connection. The signals through the VPN session is encrypted by SSL. Therefore, you can safely establish a VPN session beyond the Internet. A VPN session is established by SoftEther VPN’s «VPN over HTTPS» technology. It means that SoftEther VPN can create a VPN connection beyond any kinds of firewalls and NATs.
The Virtual Hub exchanges all Ethernet packets from each connected VPN session to other connected sessions. The behavior is same to traditional Ethernet switches. The Virtual Hub has a FDB (forwarding database) to optimize the transmission of Ethernet frames.
You can define a local bridge between the Virtual Hub and the existing physical Ethernet segment by using the Local Bridge function. The Local Bridge exchanges packets between the physical Ethernet adapter and the Virtual Hub. You can realize a remote-access VPN from home or mobile to the company network by using the Local Bridge function.
You can define a cascading connection between two or more remote Virtual Hubs. With cascading, you can integrate two or more remote Ethernet segments to a single Ethernet segment. For example, after you establish cascading connections between the site A, B and C, then any computers in the site A will be able to communicate with the computers in the site B and the site C. This is a site-to-site VPN.
SoftEther VPN can also establish a VPN session over UDP. The UDP-mode of SoftEther VPN supports NAT traversal. The NAT traversal function allows the VPN server behind existing NATs or firewalls to accept incoming VPN sessions. You need no network administrator’s special permission before setting up a VPN server on the company network behind firewalls or NATs. Additionally, SoftEther VPN Server may be placed on the dynamic IP address environment since SoftEther VPN has built-in Dynamic DNS (DDNS) function.
SoftEther VPN Server supports additional VPN protocols, including L2TP/IPsec, OpenVPN, Microsoft SSTP, L2TPv3 and EtherIP. These realizes the interoperability with built-in L2TP/IPsec VPN clients on iPhone, iPad, Android, Windows and Mac OS X, and also with Cisco’s VPN routers and other vendors VPN products.
SoftEther VPN is an essential infrastructure to build-up IT systems on enterprises and small-businesses.
Ad-hoc VPN
Make an ad-hoc VPN consists of the small-number computers with SoftEther VPN. Despite long-distance, it is easy to communicate mutually with any kinds of LAN-oriented protocols.
LAN to LAN Bridge
Geologically distributed branches are isolated as networks by default. SoftEther VPN lays virtual Ethernet cables between your all branches. Then all computers of all branches are connected to the single LAN.
Remote Access to LAN
Does employees need to connect to the company LAN from outside or home? Remote Access VPN will realizes virtual network cable from a Client PC to the LAN from anywhere and anytime.
SoftEther VPN can build-up flexible and dependable virtual network around Clouds. Amazon EC2, Windows Azure and most of other Clouds are supporting SoftEther VPN.
Join a Local PC into Cloud
Your desktop or laptop PC can join into the Cloud VM network. You can make use of Cloud VM as if it is on your own local network easily.
Join a Cloud VM into LAN
Your Cloud VM can join to your company LAN with SoftEther VPN. Anyone on your company can access to the Cloud VM without any settings.
Cloud to LAN Bridge VPN
SoftEther VPN keeps a virtual dedicate Ethernet line from the Cloud to the LAN 24h/365d. You can consider remote Cloud private network as a part of your corporate network.
Cloud to Cloud Bridge VPN
Are you using Amazon EC2 and Windows Azure, or using two or more remote datacenters of a Cloud service?SoftEther VPN can make a single united network between all Cloud VMs despite differences of physical locations.
SoftEther VPN supports several mobile devices including iPhone and Android. Your smartphone is now a part of your on-premise or Cloud network by using SoftEther VPN.
iPhone and Android
Windows and Mac Laptops
Your mobile PCs with Windows or Mac can be easily connected to SoftEther VPN anywhere and anytime, despite firewalls or packet filters on Wi-Fi or overseas ISP. Windows RT is also supported.
SoftEther VPN is also an ultra-convenient tool for effective system management by IT professionals on enterprises and system integrators.
Remote Management
Are you having problem with many servers, clients and printers of your client companies are distributed around the state? SoftEther VPN will help you a network administrator as a handy tool just from your desk. You can reach to any networks by only installing SoftEther VPN.
Building Your Own Cloud
Do you want to build and provide your own Cloud service which can beat Amazon EC2 or Windows Azure? SoftEther VPN can help you to build an inter-VMs network and remote-bridging network between your Cloud and your customer’s on-premise.
VPN for Network Testing, Simulation and Debugging
SoftEther VPN is not a program only for building remote network. It can be used for network design, test, and simulation by IT professionals. For example, delay, jitter and packet loss generator is implemented on SoftEther VPN. So network designer can test VoIP phones under the bad-condition IP network.
SoftEther VPN is also convenient for home users. You can be proud of using enterprise-class VPN for your home-use.
Remote Access
Do you want to access to your home server or digital appliance from outside? Set up SoftEther VPN Server on your home PC and gain access to your server or HDTV recorder from anywhere even the opposite side of the earth, through the Internet.
Comfortable Network Anywhere
Are you a business man and running around the world? Most of Wi-Fi and local ISPs of several countries are discomfort to use because of packet filtering or censorship. So set up your private relay server on your own home PC and use it from fields to gain ease.
Does your network administrator hesitates to assign you a global IP address? Or Does your company has a firewall on the border between the private network and the Internet? No problem! SoftEther VPN has a strong function to penetrate troublesome corporate firewalls.
Dynamic DNS and NAT Traversal
Unlike legacy IPsec-based VPN, even if your corporate network doesn’t have any static global IP address you can set up your stable SoftEther VPN Server on your corporate network.
VPN Azure
If the corporate firewall is more restricted and the NAT Traversal of SoftEther VPN doesn’t work correctly, use VPN Azure to penetrate such a firewall.
IPsec-based VPN protocols which are developed on 1990’s are now obsoleted. IPsec-based VPN are not familiar with most of firewalls, NATs or proxies. Unlike IPsec-based VPN, SoftEther VPN is familiar with any kind of firewalls. Additionally SoftEther VPN requires no expensive Cisco or other hardware devices. You can replace your Cisco or OpenVPN to SoftEther VPN today.
Penetrates Firewall by SSL-VPN
Are you having trouble with IPsec-based legacy VPN products? Replace it to SoftEther VPN. SoftEther VPN Protocol is based on HTTPS so almost all kinds of firewalls will permits SoftEther VPN’s packets.
Replacements of Cisco or other hardware-based VPNs
Cisco, Juniper or other hardware-based IPsec VPNs are expensive for set-up and management. They are also lack of usability and compatibility with Firewalls. Replace them to SoftEther VPN. You can very easily replace because SoftEther VPN also has the L2TP/IPsec VPN function which is same to Cisco’s.
Replacements of OpenVPN
Are you still using OpenVPN? SoftEther VPN has more ability, better performance and easy-configurable GUI-based management tools. SoftEther VPN has also the OpenVPN Server Clone Function so that any OpenVPN clients, including iPhone and Android, can connect to SoftEther VPN easily.
Screenshots
SoftEther VPN consists of three software: VPN Client, VPN Server and VPN Bridge.