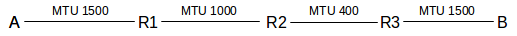How many ip addresses can one find in the header of an ip packet
How many ip addresses can one find in the header of an ip packet
How many ip addresses can one find in the header of an ip packet
Вы используете устаревший браузер. Этот и другие сайты могут отображаться в нём некорректно.
Необходимо обновить браузер или попробовать использовать другой.
Mikrotik Pre MTCNA Test
Один очень хороший человек помог Яше попасть на дорогие подкурсы, и Яша смог защитить экзамен MTCNA на 90% и получить первый в его жизни сертификат.
Решил тут оставить ответы на предварительный тест. Вдруг кому-то понадобиться, кто не может набрать 100%
MAC layer by OSI model is also known as
* Layer 2
Which computers would be able to communicate directly (without any routers involved):
V 10.5.5.1/24 and 10.5.5.100/25
V 10.10.0.17/22 and 10.10.1.30
The network address is
* The first address of the subnet
How many IP addresses can one find in the header of an IP packet?
* 2
Select valid MAC-address
* 00:00:5E:80:EE:B0
In MikroTik RouterOS, Layer-3 communication between 2 hosts can be achieved by using an address subnet of:
* /29
* /30
* /32
You have a router with configuration
— Public IP :202.168.125.45/24
— Default gateway:202.168.125.1
— DNS server: 248.115.148.136, 248.115.148.137
— Local IP: 192.168.2.1/24
Mark the correct configuration on client PC to access to the Internet
* IP:192.168.2.115/24 gateway: 192.168.2.1
The basic unit of a physical network (OSI Layer 1) is the:
* Bit
How many layers does Open Systems Interconnection model have?
* 7
A network ready device is directly connected to a MikroTik RouterBOARD with a correct U.T.P. RJ45 functioning cable. The device is configured with an IPv4 address of 192.168.100.70 using a subnet mask of 255.255.255.252. What will be a valid IPv4 address for the RouterBOARD 750 for a successful connection to
the device?
Select which of the following are ‘Public IP addresses’:
V 172.168.254.2
V 11.63.72.21
What is term for the hardware coded address found on an interface?
* MAC Address
Which of the following are valid IP addresses?
V 1.27.14.254
V 192.168.13.255
V 10.10.14.0
Select valid subnet masks:
V 255.192.0.0
V 192.0.0.0
V 255.255.224.0
Which of the following is NOT a valid MAC Address?
* 80:GF:AA:67:13:5D
Which of the following protocols / port s are used for SNMP. (Simple Network Managemnt Protocol)
V UDP 161
V UDP 162
How many usable IP addresses are there in a 20-bit subnet?
* 4094
Collisions are possible in full-duplex Ethernet networks
FALSE
Choose all valid hosts address range for subnet 15.242.55.62/27
* 15.242.55.33-15.242.55.62
What protocol does ping use?
* ICMP
IP Protocol Header Fundamentals Explained with Diagrams
IP protocol is one of the main protocols in the TCP/IP stack.
It is in the form of IP datagrams that all the TCP, UDP, ICMP and IGMP data travels over the network.
IP is connection less and unreliable protocol. It is connection less in the sense that no state related to IP datagrams is maintained either on source or destination side and it is unreliable in the sense that it not guaranteed that an IP data gram will get delivered to the destination or not.
If an IP datagram encounters some error at the destination or at some intermediate host (while traveling from source to destination) then the IP datagram is generally discarded and an ICMP error message is sent back to the source.
IP Layer in TCP/IP Suite
As can be seen from the image above, the IP protocol sits at the layer-2 of TCP/IP protocol suite ie the Internet layer. Another point worth noting here is how the data is packed in TCP/IP suite. If we analyze the figure above, we see :
On the destination host, the reverse process happens. This means that each layer reads its own header in the packet and then strips the header so that finally application receives the app-data.
IP Header
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| copy flag | option class | option num | |||||
| class | number | length | description |
| 0 | 0 | – | end of option list |
| 0 | 1 | – | no operation |
| 0 | 2 | 11 | security |
| 0 | 3 | var. | loose source routing |
| 0 | 9 | var. | strict source routing |
| 0 | 7 | var. | record route |
| 0 | 8 | 4 | stream id |
| 2 | 4 | var. | INTERNET time stamp |
Life Is Routing
Pages
MikToTik | MCQ
2. In MikroTik RouterOS, Layer-3 communication between 2 hosts can be achieved by using an address subnet of:
a. /31
b. /29
c. /32
d. /30
3. Which computers would be able to communicate directly (without any routers involved)
a. 192.168.17.15/29 and 192.168.17.20/28
b. 192.168.0.5/26 and 192.168.0.100
c. 10.5.5.1/24 and 10.5.5.100/25
d. 10.10.0.17/22 and 10.10.1.30/23
4. How many IP addresses can one find in the header of an IP packet?
a. 1
b. 3
c. 2
d. 4
5. The network address is
a. The first usable address of the subnet
b. The last address of the subnet
c. The first address of the subnet
6. What is term for the hardware coded address found on an interface?
a. IP Address
b. MAC Address
c. FQDN Address
d. Interface Address
7. How many usable IP addresses are there in a 23-bit (255.255.254.0) subnet?
a. 512
b. 510
c. 508
d. 254
9. Which of the following protocols / port s are used for SNMP. (Simple Network Management Protocol)
a. TCP 162
b. UDP 162
c. UDP 161
d. TCP 25
e. TCP 123
f. TCP 161
10. If ARP=reply-only is configured on an interface, what will this interface do
a. Accept all IP/MAC combinations listed in /ip arp as static entries
b. Accept all IP addresses listed in /ip arp as static entries
c. Add new MAC addresses in /ip arp list
d. Accept all MAC-addresses listed in /ip arp as static entries
e. Add new IP addresses in /ip arp list
11. Select which of the following are ‘Public IP addresses’:
a. 192.168.0.1
b. 172.168.254.2
c. 172.28.73.21
d. 10.110.50.37
e. 11.63.72.21
12. Which of the following IP addresses are publicly routable?
a. 127.34.155.3
b. 192.168.1.4
c. 172.16.13.23
d. 11.3.10.4
13. If ARP=reply-only is enabled on one router interface, router can add dynamic ARP entries for the particular interface.
False
True
14. The basic unit of a physical network (OSI Layer 1) is the:
a. Header
b. Byte
c. Bit
d. Frame
15. Which ones of the following are valid IP addresses?
a. 192.168.13.255
b. 10.10.14.0
c. 192.168.256.1
d. 1.27.14.254
16. How many usable IP addresses are there in a 20-bit subnet?
a. 2046
b. 2047
c. 4094
d. 4096
e. 2048
17. Which of the following is NOT a valid MAC Address?
a. 13:16:86:53:89:43
b. 80:GF:AA:67:13:5D
c. 88:0C:00:99:5F:EF
d. EA:BA:AA:EE:FF:CB
e. 95:B5:DD:EE:78:8A
18. MAC layer by OSI model is also known as
a. Layer 3
b. Layer 7
c. Layer 1
d. Layer 2
e. Layer 6
19. Select valid MAC-address
a. G2:60:CF:21:99:H0
b. 00:00:5E:80:EE:B0
c. AEC8:21F1:AA44:54FF:1111:DD
d. AE:0212:1201
e. 192.168.0.0/16
20. How many layers does Open Systems Interconnection model have?
a. 7
b. 6
c. 5
d. 12
e. 9
1. Action=redirect is applied in
a. chain=srcnat
b. chain=dstnat
c. chain=forward
2. You have 802.11b/g wireless card. What frequencies are available to you?
a. 5800MHz
b. 2412MHz
c. 5210MHz
d. 2422MHz
e. 2327MHz
3. Mark all correct statements about /export (rsc file).
a. Exports logs from /log print
b. Exports full configuration of the router
c. Exports only part of the configuration (for example /ip firewall)
d. Exports scripts from /system script
e. Exports files could not edited
4. What wireless card can we use to achieve 100 Mbps actual wireless throughput?
a. 802.11 b/g
b. 802.11 a/b/g
c. 802.11 a
d. 802.11 a/n
e. 802.11 a/b/g/n
5. It is possible to add user-defined chains in ip firewall mangle
True
False
6. Choose all valid hosts address range for subnet 15.242.55.62/27
a. 15.242.55.31-15.242.55.62
b. 15.242.55.32-15.242.55.63
c. 15.242.55.33-15.242.55.62
d. 15.242.55.33-15.242.55.63
7. Action=redirect allows you to make
a. Transparent DNS Cache
b. Forward DNS to another device IP address
c. Enable Local Service
d. Transparent HTTP Proxy
8. Which is correct masquerade rule for 192.168.0.0/24 network on the router with outgoing interface=ether1?
a. /ip firewall nat add action=masquerade chain=srcnat
b. /ip firewall nat add action=masquerade chain=srcnat src-address=192.168.0.0/24
c. /ip firewall nat add action=masquerade out-interface=ether1 chain=dstnat
d. /ip firewall nat add action=masquerade chain=srcnat out-interface=ether1
9. What letters appear next to a route, which is automatically created by RouterOS when user adds a valid address to an active interface?
a. I
b. D
c. A
d. S
e. C
10. Mark all features that are compatible with Nstreme
a. WDS between a device in station-wds mode and a device in station-wds mode
b. Encryption
c. WDS between a device in ap-bridge mode with a device in station-wds mode
d. Bridging a device in station mode with a device in ap-bridge mode
11. Can you manually add drivers to RouterOS in case your PCI Ethernet card is not recognized, and it’s a driver issue?
a. Yes
b. No
12. For static routing functionality, additionally to the RouterOS system package, you will also need the following software package:
a. none
b. dhcp
c. routing
d. advanced-tools
13. Which are necessary sections in /queue simple to set bandwidth limitation?
a. target-address, max-limit
b. target-address, dst-address, max-limit
c. target-address, dst-address
d. max-limit
15. From which of the following locations can you obtain Winbox?
a. Router’s webpage
b. Files menu in your router
c. Via the console cable
d. mikrotik.com
16. Two hosts, A and B, are connected to a broadcast LAN. Select all the answers showing pairs of IP address/mask which would allow IP connections to be established between the two hosts.
a. A: 10.1.2.66/25 and B: 10.1.2.109/26
b. A: 10.2.2.1/23 and B: 10.2.0.1/22
c. A: 10.1.2.192/24 and B: 10.1.2.129/26
d. A: 10.2.1.0/23 and B: 10.2.0.1/22
17. Why is it useful to set a Radio Name on the radio interface?
a. To identify a station in a list of connected clients
b. To identify a station in the Access List
c. To identify a station in Neighbor discovery
18. What kind of users are listed in the Secrets window of the PPP menu?
a. pptp users
b. l2tp users
c. winbox users
d. wireless users
e. pppoe users
f. hotspot users
20. MikroTik RouterOS DHCP client can receive following options
a. Byte limit
b. IP Gateway
c. Rate limit
d. Uptime limit
e. IP Address and Subnet
1. If you need to make sure that one computer in your HotSpot network can access the Internet without HotSpot authentication, which menu allows you to do this?
a. Users
b. IP bindings
c. Walled-garden
d. Walled-garden IP
2. How many different priorities can be selected for queues in MikroTik RouterOS?
a. 8
b. 16
c. 0
d. 1
3. Which default route will be active? /ip route add disabled=no distance=10 dst-address=0.0.0.0/0 gateway=1.1.1.1 add disabled=no distance=5 dst-address=0.0.0.0/0 gateway=2.2.2.2
a. Route via gateway 1.1.1.1
b. Route via gateway 2.2.2.2
4. How long is level 1 (demo) license valid?
a. 24 hours
b. Infinite time
c. 1 month
d. 1 year
6. In MikroTik RouterOS, Layer-3 communication between 2 hosts can be achieved by using an address subnet of:
a. /30
b. /29
c. /32
d. /31
7. A PC with IP 192.168.1.2 can access internet, and static ARP has been set for that IP address on gateway. When the PC Ethernet card failed, the user change it with a new card and set the same IP for it. What else should be done? [multiple answers]
a. Old static ARP entry on gateway has to be updated for the new card
b. Nothing – it will work as before
c. MAC-address of the new card has to be changed to MAC address of old card
d. Another IP has to be added for Internet access
8. How many usable IP addresses are there in a 20-bit subnet?
a. 2047
b. 4096
c. 2048
d. 2046
e. 4094
10. The network address is
a. The first usable address of the subnet
b. The last address of the subnet
c. The first address of the subnet
11. Which ones of the following are valid IP addresses? [multiple answers]
a. 192.168.13.255
b. 1.27.14.254
c. 10.10.14.0
d. 192.168.256.1
12. Which of the following is NOT a valid MAC Address?
a. 95:B5:DD:EE:78:8A
b. 13:16:86:53:89:43
c. 80:GF:AA:67:13:5D
d. 88:0C:00:99:5F:EF
e. EA:BA:AA:EE:FF:CB
13. If ARP=reply-only is configured on an interface, what will this interface do
a. Add new IP addresses in /ip arp list
b. Accept all IP/MAC combinations listed in /ip arp as static entries
c. Accept all MAC-addresses listed in /ip arp as static entries
d. Add new MAC addresses in /ip arp list
e. Accept all IP addresses listed in /ip arp as static entries
14. What is term for the hardware coded address found on an interface?
a. IP Address
b. Interface Address
c. MAC Address
d. FQDN Address
15. Which of the following IP addresses are publicly routable?
a. 127.34.155.3
b. 192.168.1.4
c. 172.16.13.23
d. 11.3.10.4
16. What protocol does ping use?
a. UDP
b. TCP
c. ARP
d. ICMP
17. MAC layer by OSI model is also known as
a. Layer 3
b. Layer 7
c. Layer 2
d. Layer 6
e. Layer 1
18. How many layers does Open Systems Interconnection model have?
a. 12
b. 6
c. 9
d. 5
e. 7
19. How many IP addresses can one find in the header of an IP packet?
a. 3
b. 4
c. 1
d. 2
20. The basic unit of a physical network (OSI Layer 1) is the:
a. Byte
b. Frame
c. Bit
d. Header
1. You have a router with configuration
— Public IP :202.168.125.45/24
— Default gateway:202.168.125.1
— DNS server: 248.115.148.136, 248.115.148.137
— Local IP: 192.168.2.1/24
Mark the correct configuration on client PC to access to the Internet
a. IP:192.168.0.1/24 gateway:192.168.2.1
b. IP:192.168.2.253/24 gateway:202.168.0.1
c. IP:192.168.1.223/24 gateway:248.115.148.136
d. IP:192.168.2.115/24 gateway: 192.168.2.1
e. IP:192.168.2.2/24 gateway:202.168.125.45
2. On the advanced menu of the wireless setup there is a parameter called “Area”, it works directly with:
a. Connect List
b. Access List
c. None of these
d. Security Profile
3. What menus should be used to allow certain websites to be accessed from behind a hotspot interface, without client authentication
a. ip hotspot ip-binding
b. ip hotspot profile
c. ip hotspot walled-garden
d. ip hotspot walled-garden ip
4. You want to use PCQ and allow 256k maximum download and upload for each client. Choose correct argument values for the required queue.
a. kind=pcq pcq-limit=1256000 pcq-classifier=dst-address
b. kind=pcq pcq-limit=256000 pcq-classifier=dst-address
c. kind=pcq pcq-limit=5000000 pcq-classifier=src-address
d. kind=pcq pcq-limit=256000 pcq-classifier=src-address
e. kind=pcq pcq-limit=5000000 pcq-classifier=dst-address
5. Which of the following is true for connection tracking
a. Enabling connection tracking reduces CPU usage in RouterOS
b. Connection tracking must be enabled for firewall to be effective
c. Connection tracking must be enable for NAT’ed network
d. Disable connection tracking for mangle to work
6. Which of these are possible solutions to bridge two networks over a wireless link:
a. Both devices in AP mode and enable WDS mode
b. One device in AP mode, another one in station-pseudobridge-clone
c. One device in AP mode, another one in station-pseudobridge
d. One device in AP mode, another one in station
7. When backing up your router by using the ‘Export’ command, the following happens:
a. Winbox usernames and passwords are backed up
b. The Export file can be edited with a standard text editor after its creation
c. You are requested to give the export file a name
8. You need to reboot a RouterBoard after importing a previously exported rsc file to activate the new configuration.
True
False
9. It is impossible to disable user “admin” at the menu “/user”
True
False
10. If a packet comes to a router and starts a new, previously unseen connection, which connection state would be applied to it?
a. no connection state would be applied to such packet
b. new
c. unknown
d. invalid
e. established
11. We have two radio cards in a point-to-point link with settings:
Card Nr 1.: mode=ap-bridge ssid=”office”
frequency=2447 band=2.4ghz-b/g default-authentication=yes default-forwarding=yes security-profile=wpa
Card Nr 2.: mode=station ssid=”office”
frequency=2412 band=2.4ghz-b/g default-authentication=yes default-forwarding=yes security-profile=wpa2
Is Card Nr2. able to connect to Card Nr 1.?
a. Yes, if Nstreme is enabled or disabled on both
b. Yes, when security profile settings are compatible with each other and Nstreme is enabled or disabled on both
c. No, because of the different frequencies
d. No, because of the different security profiles
12. If you need to make sure that one computer in your HotSpot network can access the Internet without HotSpot authentication, which menu allows you to do this?
a. Walled-garden IP
b. Walled-garden
c. Users
d. IP bindings
13. Consider the following network diagram. In R1, you have the following configuration:
/ip route
add dst-address=192.168.1.0/24 gateway=192.168.99.2
/ip firewall nat
add chain=srcnat out-interface=Ether1 action=masquerade
On R2, if you wish to prevent all access to a server located at 192.168.1.10 from LAN1 devices, which of the following rules would be needed?
a. /ip firewall filter add chain=forward src-address=192.168.99.1 dst-address=192.168.1.10 action=drop
b. /ip firewall filter add chain=input src-address=192.168.99.1 dst-address=192.168.1.10 action=drop
c. /ip firewall nat add chain=dstnat src-address=192.168.99.1 dst-address=192.168.1.10 action=drop
d. /ip firewall filter add chain=forward src-address=192.168.0.0/24 dst-address=192.168.1.10 action=drop
14. What is the default protocol/port of (secure) winbox?
a. UDP/5678
b. TCP/8291
c. TCP/22
d. TCP/8080
15. Mark the queue types that are available in RouterOS
a. SFQ – Stochastic Fairness Queuing
b. DRR – Deficit Round Robin
c. FIFO – First In First Out (for Bytes or for Packets)
d. LIFO – Last In First Out
e. PCQ – Per Connection Queuing
f. RED – Random Early Detect (or Drop)
16. A network ready device is directly connected to a MikroTik RouterBOARD 750 with a correct U.T.P. RJ45 functioning cable. The device is configured with an IPv4 address of 192.168.100.70 using a subnet mask of 255.255.255.252. What will be a valid IPv4 address for the RouterBOARD 750 for a successful connection to the device?
a. 192.168.100.70/255.255.255.252
b. 192.168.100.69/255.255.255.252
c. 192.168.100.71/255.255.255.252
d. 192.168.100.68/255.255.255.252
17. How many usable IP addresses are there in a 23-bit (255.255.254.0) subnet?
a. 512
b. 510
c. 508
d. 254
19. Which of the following protocols / port s are used for SNMP. (Simple Network Managemnt Protocol)
a. TCP 162
b. UDP 162
c. UDP 161
d. TCP 25
e. TCP 123
f. TCP 161
20. Select which of the following are ‘Public IP addresses’:
a. 192.168.0.1
b. 172.168.254.2
c. 172.28.73.21
d. 10.110.50.37
e. 11.63.72.21
21. If ARP=reply-only is enabled on one router interface, router can add dynamic ARP entries for the particular interface.
False
True
22. MAC layer by OSI model is also known as
a. Layer 3
b. Layer 7
c. Layer 1
d. Layer 2
e. Layer 6
23. Select valid MAC-address
a. G2:60:CF:21:99:H0
b. 00:00:5E:80:EE:B0
c. AEC8:21F1:AA44:54FF:1111:DDAE:0212:1201
d. 192.168.0.0/16
24. Which computers would be able to communicate directly (without any routers involved)
a. 192.168.17.15/29 and 192.168.17.20/28
b. 192.168.0.5/26 and 192.168.0.100
c. 10.5.5.1/24 and 10.5.5.100/25
d. 10.10.0.17/22 and 10.10.1.30/2
7 IP version 4В¶
There are multiple LAN protocols below the IP layer and multiple transport protocols above, but IP itself stands alone. The Internet is essentially the IP Internet. If you want to run your own LAN somewhere or if you want to run your own transport protocol, the Internet backbone will still work for you. But if you want to change the IP layer, you may encounter difficulty. (Just talk to the IPv6 people, or the IP-multicasting or IP-reservations groups.)
IP is, in effect, a universal routing and addressing protocol. The two are developed together; every node has an IP address and every router knows how to handle IP addresses. IP was originally seen as a way to interconnect multiple LANs, but it may make more sense now to view IP as a virtual LAN overlaying all the physical LANs.
A crucial aspect of IP is its scalability. As the Internet has grown to
10 9 hosts, the forwarding tables are not much larger than 10 5 (perhaps now 10 5.5 ). Ethernet, in comparison, scales poorly.
Furthermore, IP, unlike Ethernet, offers excellent support for multiple redundant links. If the network below were an IP network, each node would communicate with each immediate neighbor via their shared direct link. If, on the other hand, this were an Ethernet network with the spanning-tree algorithm, then one of the four links would simply be disabled completely.
The IP network service model is to act like a LAN. That is, there are no acknowledgments; delivery is generally described as best-effort. This design choice is perhaps surprising, but it has also been quite fruitful.
If you want to provide a universal service for delivering any packet anywhere, what else do you need besides routing and addressing? Every network (LAN) needs to be able to carry any packet. The protocols spell out the use of octets (bytes), so the only possible compatibility issue is that a packet is too large for a given network. IP handles this by supporting fragmentation: a network may break a too-large packet up into units it can transport successfully. While IP fragmentation is inefficient and clumsy, it does guarantee that any packet can potentially be delivered to any node.
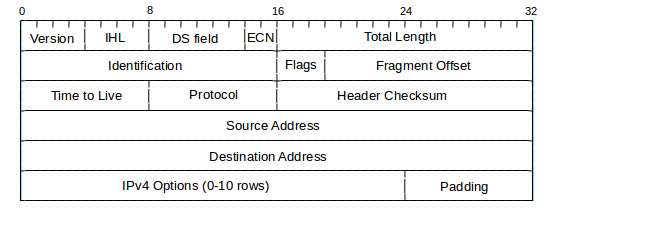
7.1 The IPv4 Header¶
The IPv4 Header needs to contain the following information:
Here is how it is all laid out in the header. Each row is 32 bits wide.
The IP header, and basics of IP protocol operation, were defined in RFC 791; some minor changes have since occurred. Most of these changes were documented in RFC 1122, though the DS field was defined in RFC 2474 and the ECN bits were first proposed in RFC 2481.
The Version field is, for IPv4, the number 4: 0100. The IHL field represents the total IP Header Length, in 32-bit words; an IP header can thus be at most 15 words long. The base header takes up five words, so the IP Options can consist of at most ten words. If one looks at IPv4 packets using a packet-capture tool that displays the packets in hex, the first byte will most often be 0x45.
The Differentiated Services (DS) field is used by the Differentiated Services suite to specify preferential handling for designated packets, eg those involved in VoIP or other real-time protocols. The Explicit Congestion Notification bits are there to allow routers experiencing congestion to mark packets, thus indicating to the sender that the transmission rate should be reduced. We will address these in 14.8.2 Explicit Congestion Notification (ECN). These two fields together replace the old 8-bit Type of Service field.
The Total Length field is present because an IP packet may be smaller than the minimum LAN packet size (see Exercise 1) or larger than the maximum (if the IP packet has been fragmented over several LAN packets. The IP packet length, in other words, cannot be inferred from the LAN-level packet size. Because the Total Length field is 16 bits, the maximum IP packet size is 2 16 bytes. This is probably much too large, even if fragmentation were not something to be avoided.
The second word of the header is devoted to fragmentation, discussed below.
The Time-to-Live (TTL) field is decremented by 1 at each router; if it reaches 0, the packet is discarded. A typical initial value is 64; it must be larger than the total number of hops in the path. In most cases, a value of 32 would work. The TTL field is there to prevent routing loops – always a serious problem should they occur – from consuming resources indefinitely. Later we will look at various IP routing-table update protocols and how they minimize the risk of routing loops; they do not, however, eliminate it. By comparison, Ethernet headers have no TTL field, but Ethernet also disallows cycles in the underlying topology.
The Protocol field contains a value to indicate if the body of the IP packet represents a TCP packet or a UDP packet, or, in unusual cases, something else altogether.
The Header Checksum field is the “Internet checksum” applied to the header only, not the body. Its only purpose is to allow the discarding of packets with corrupted headers. When the TTL value is decremented the router must update the header checksum. This can be done “algebraically” by adding a 1 in the correct place to compensate, but it is not hard simply to re-sum the 8 halfwords of the average header.
The Source and Destination Address fields contain, of course, the IP addresses. These would be updated only by NAT firewalls.
One option is the Record Route option, in which routers are to insert their own IP address into the IP header option area. Unfortunately, with only ten words available, there is not enough space to record most longer routes (but see 7.9.1 Traceroute and Time Exceeded, below). Another option, now deprecated as security risk, is to support source routing. The sender would insert into the IP header option area a list of IP addresses; the packet would be routed to pass through each of those IP addresses in turn. With strict source routing, the IP addresses had to represent adjacent neighbors; no router could be used if its IP address were not on the list. With loose source routing, the listed addresses did not have to represent adjacent neighbors and ordinary IP routing was used to get from one listed IP address to the next. Both forms are essentially never used, again for security reasons: if a packet has been source-routed, it may have been routed outside of the at-least-somewhat trusted zone of the Internet backbone.
7.2 Interfaces¶
IP addresses (IPv4 and IPv6) are, strictly speaking, assigned not to hosts or nodes, but to interfaces. In the most common case, where each node has a single LAN interface, this is a distinction without a difference. In a room full of workstations each with a single Ethernet interface eth0 (or perhaps Ethernet adapter Local Area Connection ), we might as well view the IP address assigned to the interface as assigned to the workstation itself.
Workstations often have special other interfaces as well. Most recent versions of Microsoft Windows have a Teredo Tunneling pseudo-interface and an Automatic Tunneling pseudo-interface; these are both intended (when activated) to support IPv6 connectivity when the local ISP supports only IPv4. The Teredo protocol is documented in RFC 4380.
When VPN connections are created, as in 3.1 Virtual Private Network, each end of the logical connection typically terminates at a virtual interface (one of these is labeled tun0 in the diagram of 3.1 Virtual Private Network). These virtual interfaces appear, to the systems involved, to be attached to a point-to-point link that leads to the other end.
When a computer hosts a virtual machine, there is almost always a virtual network to connect the host and virtual systems. The host will have a virtual interface to connect to the virtual network. The host may act as a NAT router for the virtual machine, “hiding” that virtual machine behind its own IP address, or it may act as an Ethernet switch, in which case the virtual machine will need an additional public IP address.
What’s My IP Address?
This simple-seeming question is in fact not very easy to answer, if by “my IP address” one means the IP address assigned to the interface that connects directly to the Internet. One strategy is to find the address of the default router, and then iterate through all interfaces (eg with the Java NetworkInterface class) to find an IP address with a matching network prefix. Unfortunately, finding the default router is hard to do in an OS-independent way, and even then this approach can fail if the Wi-Fi and Ethernet interfaces both are assigned IP addresses on the same network, but only one is actually connected.
Many workstations have both an Ethernet interface and a Wi-Fi interface. Both of these can be used simultaneously (with different IP addresses assigned to each), either on the same IP network or on different IP networks.
Routers always have at least two interfaces on two separate LANs. Generally this means a separate IP address for each interface, though some point-to-point interfaces can be used without being assigned an IP address (7.10 Unnumbered Interfaces).
Finally, it is usually possible to assign multiple IP addresses to a single interface. Sometimes this is done to allow two IP networks to share a single LAN; the interface might be assigned one IP address for each IP network. Other times a single interface is assigned multiple IP addresses that are on the same LAN; this is often done so that one physical machine can act as a server (eg a web server) for multiple distinct IP addresses corresponding to multiple distinct domain names.
While it is important to be at least vaguely aware of all these special cases, we emphasize again that in most ordinary contexts each end-user workstation has one IP address that corresponds to a LAN connection.
7.3 Special Addresses¶
A few IP addresses represent special cases.
Private addresses are IP addresses intended only for site internal use, eg either behind a NAT firewall or intended to have no Internet connectivity at all. If a packet shows up at any non-private router (eg at an ISP router), with a private IP address as either source or destination address, the packet should be dropped. Three standard private-address blocks have been defined:
The last block is the one from which addresses are most commonly allocated by DHCP servers (7.8.1 DHCP and the Small Office) built into NAT routers.
Broadcast addresses are a special form of IP address intended to be used in conjunction with LAN-layer broadcast. The most common forms are “broadcast to this network”, consisting of all 1-bits, and “broadcast to network D”, consisting of D’s network-address bits followed by all 1-bits for the host bits. If you try to send a packet to the broadcast address of a remote network D, the odds are that some router involved will refuse to forward it, and the odds are even higher that, once the packet arrives at a router actually on network D, that router will refuse to broadcast it. Even addressing a broadcast to ones own network will fail if the underlying LAN does not support LAN-level broadcast (eg ATM).
The highly influential early Unix implementation Berkeley 4.2 BSD used 0-bits for the broadcast bits, instead of 1’s. As a result, to this day host bits cannot be all 1-bits or all 0-bits in order to avoid confusion with the IP broadcast address. One consequence of this is that a Class C network has 254 usable host addresses, not 256.
7.3.1 Multicast addresses¶
Finally, IP multicast addresses remain as the last remnant of the Class A/B/C strategy: multicast addresses are Class D, with first byte beginning 1110 (meaning that the first byte is, in decimal, 224-239). Multicasting means delivering to a specified set of addresses, preferably by some mechanism more efficient than sending to each address individually. A reasonable goal of multicast would be that no more than one copy of the multicast packet traverses any given link.
Support for IP multicast requires considerable participation by the backbone routers involved. For example, if hosts A, B and C each connect to different interfaces of router R1, and A wishes to send a multicast packet to B and C, then it is up to R1 to receive the packet, figure out that B and C are the intended recipients, and forward the packet twice, once for B’s interface and once for C’s. R1 must also keep track of what hosts have joined the multicast group and what hosts have left. Due to this degree of router participation, backbone router support for multicasting has not been entirely forthcoming. A discussion of IP multicasting appears in 18 Quality of Service.
7.4 Fragmentation¶
If you are trying to interconnect two LANs (as IP does), what else might be needed besides Routing and Addressing? IP explicitly assumes all packets are composed on 8-bit bytes (something not universally true in the early days of IP; to this day the RFCs refer to “octets” to emphasize this requirement). IP also defines bit-order within a byte, and it is left to the networking hardware to translate properly. Neither byte size nor bit order, therefore, can interfere with packet forwarding.
There is one more feature IP must provide, however, if the goal is universal connectivity: it must accommodate networks for which the maximum packet size, or Maximum Transfer Unit, MTU, is smaller than the packet that needs forwarding. Otherwise, if we were using IP to join Token Ring (MTU = 4KB, at least originally) to Ethernet (MTU = 1500B), the token-ring packets might be too large to deliver to the Ethernet side, or to traverse an Ethernet backbone en route to another Token Ring. (Token Ring, in its day, did commonly offer a configuration option to allow Ethernet interoperability.)
So, IP must support fragmentation, and thus also reassembly. There are two major strategies here: per-link fragmentation and reassembly, where the reassembly is done at the opposite end of the link (as in ATM), and path fragmentation and reassembly, where reassembly is done at the far end of the path. The latter approach is what is taken by IP, partly because intermediate routers are too busy to do reassembly (this is as true today as it was thirty years ago), and partly because IP fragmentation is seen as the strategy of last resort.
An IP sender is supposed to use a different value for the IDENT field for different packets, at least up until the field wraps around. When an IP datagram is fragmented, the fragments keep the same IDENT field, so this field in effect indicates which fragments belong to the same packet.
As an example, consider the following network, where MTUs are excluding the LAN header:
Suppose A addresses a packet of 1500 bytes to B, and sends it via the LAN to the first router R1. The packet contains 20 bytes of IP header and 1480 of data.
R1 fragments the original packet into two packets of sizes 20+976 = 996 and 20+504=544. Having 980 bytes of payload in the first fragment would fit, but violates the rule that the sizes of the data portions be divisible by 8. The first fragment packet has FragOffset = 0; the second has FragOffset = 976.
R2 refragments the first fragment into three packets as follows:
R2 refragments the second fragment into two:
R3 then sends the fragments on to B, without reassembly.
Note that it would have been slightly more efficient to have fragmented into four fragments of sizes 376, 376, 376, and 352 in the beginning. Note also that the packet format is designed to handle fragments of different sizes easily. The algorithm is based on multiple fragmentation with reassembly only at the final destination.
Each fragment has its IP-header Total Length field set to the length of that fragment.
We have not yet discussed the three flag bits. The first bit is reserved, and must be 0. The second bit is the “Don’t Fragment” bit. If it is set to 1 by the sender then a router must not fragment the packet and must drop it instead; see 12.12 Path MTU Discovery for an application of this. The third bit is set to 1 for all fragments except the final one (this bit is thus set to 0 if no fragmentation has occurred). The third bit tells the receiver where the fragments stop.
The receiver must take the arriving fragments and reassemble them into a whole packet. The fragments may not arrive in order – unlike in ATM networks – and may have unrelated packets interspersed. The reassembler must identify when different arriving packets are fragments of the same original, and must figure out how to reassemble the fragments in the correct order; both these problems were essentially trivial for ATM.
Fragments are considered to belong to the same packet if they have the same IDENT field and also the same source and destination addresses and same protocol.
As all fragment sizes are a multiple of 8 bytes, the receiver can keep track of whether all fragments have been received with a bitmap in which each bit represents one 8-byte fragment chunk. A 1 KB packet could have up to 128 such chunks; the bitmap would thus be 16 bytes.
If a fragment arrives that is part of a new (and fragmented) packet, a buffer is allocated. While the receiver cannot know the final size of the buffer, it can usually make a reasonable guess. Because of the FragOffset field, the fragment can then be stored in the buffer in the appropriate position. A new bitmap is also allocated, and a reassembly timer is started.
As subsequent fragments arrive, not necessarily in order, they too can be placed in the proper buffer in the proper position, and the appropriate bits in the bitmap are set to 1.
If the bitmap shows that all fragments have arrived, the packet is sent on up as a completed IP packet. If, on the other hand, the reassembly timer expires, then all the pieces received so far are discarded.
TCP connections usually engage in Path MTU Discovery, and figure out the largest packet size they can send that will not entail fragmentation (12.12 Path MTU Discovery). But it is not unusual, for example, for UDP protocols to use fragmentation, especially over the short haul. In the Network File Sharing (NFS) protocol, for example, UDP is used to carry 8KB disk blocks. These are often sent as a single 8+ KB IP packet, fragmented over Ethernet to five full packets and a fraction. Fragmentation works reasonably well here because most of the time the packets do not leave the Ethernet they started on. Note that this is an example of fragmentation done by the sender, not by an intermediate router.
Finally, any given IP link may provide its own link-layer fragmentation and reassembly; we saw in 3.8.1 ATM Segmentation and Reassembly that ATM does just this. Such link-layer mechanisms are, however, generally invisible to the IP layer.
7.5 The Classless IP Delivery Algorithm¶
Recall from Chapter 1 that any IP address can be divided into a net portion IPnet and a host portion IPhost; the division point was determined by whether the IP address was a Class A, a Class B, or a Class C. We also hinted in Chapter 1 that the division point was not always so clear-cut; we now present the delivery algorithm, for both hosts and routers, that does not assume a globally predeclared division point of the input IP address into net and host portions. We will, for the time being, punt on the question of forwarding-table lookup and assume there is a lookup() method available that, when given a destination address, returns the next_hop neighbor.
Let D be the given IP destination address; we want to decide if D is local or nonlocal. The host or router involved may have multiple IP interfaces, but for each interface the length of the network portion of the address will be known. For each network address B/k assigned to one of the host’s interfaces, we compare the first k bits of B and D; that is, we ask if D matches B/k.
The forwarding table is, abstractly, a set of network addresses – now also with lengths – each of the form B/k, with an associated next_hop destination for each. The lookup() routine will, in principle, compare D with each table entry B/k, looking for a match (that is, equality of the first k bits). As with the interfaces check above, the net/host division point (that is, k) will come from the table entry; it will not be inferred from D or from any other information borne by the packet. There is, in fact, no place in the IP header to store a net/host division point, and furthermore different routers along the path may use different values of k with the same destination address D. In 10 Large-Scale IP Routing we will see that in some cases multiple matches in the forwarding table may exist; the longest-match rule will be introduced to pick the best match.
The forwarding table may also contain a default entry for the next_hop, which it may return in cases when the destination D does not match any known network. We take the view here that returning such a default entry is a valid result of the routing-table lookup() operation, rather than a third option to the algorithm above; one approach is for the default entry to be the network address 0.0.0.0/0, which does indeed match everything (use of this would definitely require the above longest-match rule, though).
Default routes are hugely important in keeping leaf forwarding tables small. Even backbone routers sometimes expend considerable effort to keep the network address prefixes in their forwarding tables as short as possible, through consolidation.
Routers may also be configured to allow passing quality-of-service information to the lookup() method, as mentioned in Chapter 1, to support different routing paths for different kinds of traffic (eg bulk file-transfer versus real-time).
For a modest exception to the local-delivery rule described here, see below in 7.10 Unnumbered Interfaces.
7.6 IP Subnets¶
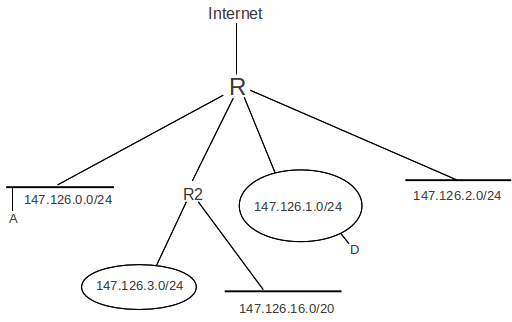
Subnets were the first step away from Class A/B/C routing: a large network (eg a class A or B) could be divided into smaller IP networks called subnets. Consider, for example, a typical Class B network such as Loyola University’s (originally 147.126.0.0/16); the underlying assumption is that any packet can be delivered via the underlying LAN to any internal host. This would require a rather large LAN, and would require that a single physical LAN be used throughout the site. What if our site has more than one physical LAN? Or is really too big for one physical LAN? It did not take long for the IP world to run into this problem.
Subnets were first proposed in RFC 917, and became official with RFC 950.
Getting a separate IP network prefix for each subnet is bad for routers: the backbone forwarding tables now must have an entry for every subnet instead of just for every site. What is needed is a way for a site to appear to the outside world as a single IP network, but for further IP-layer routing to be supported inside the site. This is what subnets accomplish.
Subnets introduce hierarchical routing: first we route to the primary network, then inside that site we route to the subnet, and finally the last hop delivers to the host.
Routing with subnets involves in effect moving the IPnet division line rightward. (Later, when we consider CIDR, we will see the complementary case of moving the division line to the left.) For now, observe that moving the line rightward within a site does not affect the outside world at all; outside routers are not even aware of site-internal subnetting.
In the following diagram, the outside world directs traffic addressed to 147.126.0.0/16 to the router R. Internally, however, the site is divided into subnets. The idea is that traffic from 147.126.1.0/24 to 147.126.2.0/24 is routed, not switched; the two LANs involved may not even be compatible. Most of the subnets shown are of size /24, meaning that the third byte of the IP address has become part of the network portion of the subnet’s address; one /20 subnet is also shown. RFC 950 would have disallowed the subnet with third byte 0, but having 0 for the subnet bits generally does work.
What we want is for the internal routing to be based on the extended network prefixes shown, while externally continuing to use only the single routing entry for 147.126.0.0/16.
To implement subnets, we divide the site’s IP network into some combination of physical LANs – the subnets –, and assign each a subnet address: an IP network address which has the site’s IP network address as prefix. To put this more concretely, suppose the site’s IP network address is A, and consists of n network bits (so the site address may be written with the slash notation as A/n); in the diagram above, A/n = 147.126.0.0/16. A subnet address is an IP network address B/k such that:
An example B/k in the diagram above is 147.126.1.0/24. (There is a slight simplification here in that subnet addresses do not absolutely have to be prefixes; see below.)
We now have to figure out how packets will be routed to the correct subnet. For incoming packets we could set up some proprietary protocol at the entry router to handle this. However, the more complicated situation is all those existing internal hosts that, under the class A/B/C strategy, would still believe they can deliver via the LAN to any site host, when in fact they can now only do that for hosts on their own subnet. We need a more general solution.
We proceed as follows. For each subnet address B/k, we create a subnet mask for B consisting of k 1-bits followed by enough 0-bits to make a total of 32. We then make sure that every host and router in the site knows the subnet mask for every one of its interfaces. Hosts usually find their subnet mask the same way they find their IP address (by static configuration if necessary, but more likely via DHCP, below).
Hosts and routers now apply the IP delivery algorithm of the previous section, with the proviso that, if a subnet mask for an interface is present, then the subnet mask is used to determine the number of address bits rather than the Class A/B/C mechanism. That is, we determine whether a packet addressed to destination D is deliverable locally via an interface with subnet address B/k and corresponding mask M by comparing D&M with B&M, where & represents bitwise AND; if the two match, the packet is local. This will generally involve a match of more bits than if we used the Class A/B/C strategy to determine the network portion of addresses D and B.
As stated previously, given an address D with no other context, we will not be able to determine the network/host division point in general (eg for outbound packets). However, that division point is not in fact what we need. All that is needed is a way to tell if a given destination host address D belongs to the current subnet, say B; that is, we need to compare the first k bits of D and B where k is the (known) length of B.
In the diagram above, the subnet mask for the /24 subnets would be 255.255.255.0; bitwise ANDing any IP address with the mask is the same as extracting the first 24 bits of the IP address, that is, the subnet portion. The mask for the /20 subnet would be 255.255.240.0 (240 in binary is 1111 0000).
In the diagram above none of the subnets overlaps or conflicts: the subnets 147.126.0.0/24 and 147.126.1.0/24 are disjoint. It takes a little more effort to realize that 147.126.16.0/20 does not overlap with the others, but note that an IP address matches this network prefix only if the first four bits of the third byte are 0001, so the third byte itself ranges from decimal 32 to decimal 63 = binary 0001 1111.
Note also that if host A = 147.126.0.1 wishes to send to destination D = 147.126.1.1, and A is not subnet-aware, then delivery will fail: A will infer that the interface is a Class B, and therefore compare the first two bytes of A and D, and, finding a match, will attempt direct LAN delivery. But direct delivery is now likely impossible, as the subnets are not joined by a switch. Only with the subnet mask will A realize that its network is 147.126.0.0/24 while D’s is 147.126.1.0/24 and that these are not the same. A would still be able to send packets to its own subnet. In fact A would still be able to send packets to the outside world: it would realize that the destination in that case does not match 147.126.0.0/16 and will thus forward to its router. Hosts on other subnets would be the only unreachable ones.
Properly, the subnet address is the entire prefix, eg 147.126.65.0/24. However, it is often convenient to identify the subnet address with just those bits that represent the extension of the site IP-network address; we might thus say casually that the subnet address here is 65.
The class-based IP-address strategy allowed any host anywhere on the Internet to properly separate any address into its net and host portions. With subnets, this division point is now allowed to vary; for example, the address 147.126.65.48 divides into 147.126 | 65.48 outside of Loyola, but into 147.126.65 | 48 inside. This means that the net-host division is no longer an absolute property of addresses, but rather something that depends on where the packet is on its journey.
Technically, we also need the requirement that given any two subnet addresses of different, disjoint subnets, neither is a proper prefix of the other. This guarantees that if A is an IP address and B is a subnet address with mask M (so B = B&M), then A&M = B implies A does not match any other subnet. Regardless of the net/host division rules, we cannot possibly allow subnet 147.126.16.0/20 to represent one LAN while 147.126.16.0/24 represents another; the second subnet address block is a subset of the first. (We can, and sometimes do, allow the first LAN to correspond to everything in 147.126.16.0/20 that is not also in 147.126.16.0/24; this is the longest-match rule.)
The strategy above is actually a slight simplification of what the subnet mechanism actually allows: subnet address bits do not in fact have to be contiguous, and masks do not have to be a series of 1-bits followed by 0-bits. The mask can be any bit-mask; the subnet address bits are by definition those where there is a 1 in the mask bits. For example, we could at a Class-B site use the fourth byte as the subnet address, and the third byte as the host address. The subnet mask would then be 255.255.0.255. While this generality was once sometimes useful in dealing with “legacy” IP addresses that could not easily be changed, life is simpler when the subnet bits precede the host bits.
7.6.1 Subnet Example¶
As an example of having different subnet masks on different interfaces, let us consider the division of a class-C network into subnets of size 70, 40, 25, and 20. The subnet addresses will of necessity have different lengths, as there is not room for four subnets each able to hold 70 hosts.
Because of the different subnet-address lengths, division of a local IP address LA into net versus host on subnets cannot be done in isolation, without looking at the host bits. However, that division is not in fact what we need. All that is needed is a way to tell if the local address LA belongs to a given subnet, say B; that is, we need to compare the first n bits of LA and B, where n is the length of B’s subnet mask. We do this by comparing LA&M to B&M, where M is the mask corresponding to n. LA&M is not necessarily the same as LAnet, if LA actually belongs to one of the other subnets. However, if LA&M = B&M, then LA must belong subnet B, in which case LA&M is in fact LAnet.
We will assume that the site’s IP network address is 200.0.0.0/24. The first three bytes of each subnet address must match 200.0.0. Only some of the bits of the fourth byte will be part of the subnet address, so we will switch to binary for the last byte, and use both the /n notation (for total number of subnet bits) and also add a vertical bar | to mark the separation between subnet and host.
Example: 200.0.0.10 | 00 0000 / 26
Note that this means that the 0-bit following the 1-bit in the fourth byte is “significant” in that for a subnet to match, it must match this 0-bit exactly. The remaining six 0-bits are part of the host portion.
To allocate our four subnet addresses above, we start by figuring out just how many host bits we need in each subnet. Subnet sizes are always powers of 2, so we round up the subnets to the appropriate size. For subnet A, this means we need 7 host bits to accommodate 2 7 = 128 hosts, and so we have a single bit in the fourth byte to devote to the subnet address. Similarly, for B we will need 6 host bits and will have 2 subnet bits, and for C and D we will need 5 host bits each and will have 8-5=3 subnet bits.
We now start choosing non-overlapping subnet addresses. We have one bit in the fourth byte to choose for A’s subnet; rather arbitrarily, let us choose this bit to be 1. This means that every other subnet address must have a 0 in the first bit position of the fourth byte, or we would have ambiguity.
Now for B’s subnet address. We have two bits to work with, and the first bit must be 0. Let us choose the second bit to be 0 as well. If the fourth byte begins 00, the packet is part of subnet B, and the subnet addresses for C and D must therefore not begin 00.
Finally, we choose subnet addresses for C and D to be 010 and 011, respectively. We thus have
| subnet | size | address bits in fourth byte | host bits in 4th byte | decimal range |
|---|---|---|---|---|
| A | 128 | 1 | 7 | 128-255 |
| B | 64 | 00 | 6 | 0-63 |
| C | 32 | 010 | 5 | 64-95 |
| D | 32 | 011 | 5 | 96-127 |
As desired, none of the subnet addresses in the third column is a prefix of any other subnet address.
The end result of all of this is that routing is now hierarchical: we route on the site IP address to get to a site, and then route on the subnet address within the site.
7.6.2 Links between subnets¶
Suppose the Loyola CS department subnet (147.126.65.0/24) and a department at some other site, we will say 147.100.100.0/24, install a private link. How does this affect routing?
Each department router would add an entry for the other subnet, routing along the private link. Traffic addressed to the other subnet would take the private link. All other traffic would go to the default router. Traffic from the remote department to 147.126.64.0/24 would take the long route, and Loyola traffic to 147.100.101.0/24 would take the long route.
A long time ago I was responsible for two hosts, abel and borel. One day I was informed that machines in computer lab 1 at the other end of campus could not reach borel, though they could reach abel. Machines in lab 2, adjacent to lab 1, however, could reach both borel and abel just fine. What was the difference?
It turned out that borel had a bad (/16 instead of /24) subnet mask, and so it was attempting local delivery to the labs. This should have meant it could reach neither of the labs, as both labs were on a different subnet from my machines; I was still perplexed. After considerably more investigation, it turned out that between abel/borel and the lab building was a bridge-router: a hybrid device that properly routed subnet traffic, but which also forwarded Ethernet packets directly, the latter feature apparently for the purpose of backwards compatibility. Lab 2 was connected directly to the bridge-router and thus appeared to be on the same LAN as borel, despite the apparently different subnet; lab 1 was connected to its own router R1 which in turn connected to the bridge-router. Lab 1 was thus, at the LAN level, isolated from abel and borel.
Moral 1: Switching and routing are both great ideas, alone. But switching mixed with routing is not.
Moral 2: Test thoroughly! The reason the problem wasn’t noticed earlier was that previously borel communicated only with other hosts on the same subnet and with hosts outside the university entirely. Both of these worked with the bad subnet mask; it is different-subnet local hosts that are the problem.
How would nearby subnets at either endpoint decide whether to use the private link? Classical link-state or distance-vector theory (9 Routing-Update Algorithms) requires that they be able to compare the private-link route with the going-around-the-long-way route. But this requires a global picture of relative routing costs, which, as we shall see, almost certainly does not exist. The two departments are in different routing domains; if neighboring subnets at either end want to use the private link, then manual configuration is likely the only option.
7.6.3 Subnets versus Switching¶
A frequent network design question is whether to have many small subnets or to instead have just a few (or even only one) larger subnet. With multiple small subnets, IP routing would be used to interconnect them; the use of larger subnets would replace much of that routing with LAN-layer communication, likely Ethernet switching. Debates on this route-versus-switch question have gone back and forth in the networking community, with one aphorism summarizing a common view:
This aphorism reflects the idea that switching is faster, cheaper and easier to configure, and that subnet boundaries should be drawn only where “necessary”.
Ethernet switching equipment is indeed generally cheaper than routing equipment, for the same overall level of features and reliability. And switching requires no configuration at all, while to implement subnets not only must the subnets be created by hand but one must also set up and configure the routing-update protocols. However, the price difference between switching and routing is not always significant in the big picture, and the configuration involved is often straightforward.
Somewhere along the way, however, switching has acquired a reputation – often deserved – for being faster than routing. It is true that routers have more to do than switches: they must decrement TTL, update the header checksum, and attach a new LAN header. But these things are relatively minor: a larger reason many routers are slower than switches may simply be that they are inevitably asked to serve as firewalls. This means “deep inspection” of every packet, eg comparing every packet to each of a large number of firewall rules. The firewall may also be asked to keep track of connection state. All this drives down the forwarding rate, as measured in packets-per-second. The industry has come up with the term “Layer 3 Switch” to describe routers that in effect do not support all the usual firewall bells and whistles; such streamlined routers may also be able to do most of the hard work in specialized hardware, another source of speedup. (It should be no surprise that Layer 3 switching is usually marketed in terms of the hardware speedup, not in terms of the reduced flexibility.)
Switching scales remarkably well, but it does have limitations. First, broadcast packets must be forwarded throughout a switched network; they do not, however, pass to different subnets. Second, LAN networks do not like redundant links (that is, loops); while one can rely on the spanning-tree algorithm to eliminate these, that algorithm too becomes less efficient at larger scales.
7.7 Address Resolution Protocol: ARP¶
If a host or router A finds that the destination IP address D = DIP matches the network address of one of its interfaces, it is to deliver the packet via the LAN. This means looking up the LAN address DLAN corresponding to DIP.
One approach would be via a special server, but the spirit of early IP development was to avoid such servers, for both cost and reliability issues. Instead, the Address Resolution Protocol (ARP) is used. This is our first protocol that takes advantage of the existence of LAN-level broadcast; on LANs without physical broadcast (such as ATM), some other mechanism (usually involving a server) must be used.
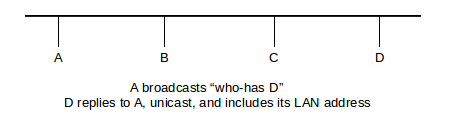
The basic idea of ARP is that the host A sends out a broadcast ARP query or “who-has DIP?” request, which includes A’s own IP and LAN addresses. All hosts on the LAN receive this message. The host for whom the message is intended, D, will recognize that it should reply, and will return an ARP reply or “is-at” message containing DLAN. Because the original request contained ALAN, D’s response can be sent directly to A, that is, unicast.
Additionally, all hosts maintain an ARP cache, consisting of вџЁIP,LANвџ© address pairs for other hosts on the network. After the exchange above, A has вџЁDIP,DLANвџ© in its table; anticipating that A will soon send it a packet to which it needs to respond, D also puts вџЁAIP,ALANвџ© into its cache.
ARP-cache entries eventually expire. The timeout interval used to be on the order of 10 minutes, but linux systems now use a much smaller timeout (
The above protocol is sufficient, but there is one further point. When A sends its broadcast “who-has D?” ARP query, all other hosts C check their own cache for an entry for A. If there is such an entry (that is, if AIP is found there), then the value for ALAN is updated with the value taken from the ARP message; if there is no pre-existing entry then no action is taken. This update process serves to avoid stale ARP-cache entries, which can arise is if a host has had its Ethernet card replaced.
7.7.1 ARP Finer Points¶
Most hosts today implement self-ARP, or gratuitous ARP, on startup (or wakeup): when station A starts up it sends out an ARP query for itself: “who-has A?”. Two things are gained from this: first, all stations that had A in their cache are now updated with A’s most current ALAN address, in case there was a change, and second, if an answer is received, then presumably some other host on the network has the same IP address as A.
Self-ARP is thus the traditional IPv4 mechanism for duplicate address detection. Unfortunately, it does not always work as well as might be hoped; often only a single self-ARP query is sent, and if a reply is received then frequently the only response is to log an error message; the host may even continue using the duplicate address! If the duplicate address was received via DHCP, below, then the host is supposed to notify its DHCP server of the error and request a different IPv4 address.
RFC 5227 has defined an improved mechanism known as Address Conflict Detection, or ACD. A host using ACD sends out three ARP queries for its new IP address, spaced over a few seconds and leaving the ARP field for the sender’s IP address filled with zeroes. This last step means that any other host with that IP address in its cache will ignore the packet, rather than update its cache. If the original host receives no replies, it then sends out two more ARP queries for its new address, this time with the ARP field for the sender’s IP address filled in with the new address; this is the stage at which other hosts on the network will make any necessary cache updates. Finally, ACD requires that hosts that do detect a duplicate address must discontinue using it.
It is also possible for other stations to answer an ARP query on behalf of the actual destination D; this is called proxy ARP. An early common scenario for this was when host C on a LAN had a modem connected to a serial port. In theory a host D dialing in to this modem should be on a different subnet, but that requires allocation of a new subnet. Instead, many sites chose a simpler arrangement. A host that dialed in to C’s serial port might be assigned IP address DIP, from the same subnet as C. C would be configured to route packets to D; that is, packets arriving from the serial line would be forwarded to the LAN interface, and packets sent to CLAN addressed to DIP would be forwarded to D. But we also have to handle ARP, and as D is not actually on the LAN it will not receive broadcast ARP queries. Instead, C would be configured to answer on behalf of D, replying with вџЁDIP,CLANвџ©. This generally worked quite well.
Proxy ARP is also used in Mobile IP, for the so-called “home agent” to intercept traffic addressed to the “home address” of a mobile device and then forward it (eg via tunneling) to that device. See 7.11 Mobile IP.
One delicate aspect of the ARP protocol is that stations are required to respond to a broadcast query. In the absence of proxies this theoretically should work quite well: there should be only one respondent. However, there were anecdotes from the Elder Days of networking when a broadcast ARP query would trigger an avalanche of responses. The protocol-design moral here is that determining who is to respond to a broadcast message should be done with great care. ( RFC 1122 section 3.2.2 addresses this same point in the context of responding to broadcast ICMP messages.)
ARP-query implementations also need to include a timeout and some queues, so that queries can be resent if lost and so that a burst of packets does not lead to a burst of queries. A naive ARP algorithm without these might be:
To see the problem with this approach, imagine that a 32KB packet arrives at the IP layer, to be sent over Ethernet. It will be fragmented into 22 fragments (assuming an Ethernet MTU of 1500 bytes), all sent at once. The naive algorithm above will likely send an ARP query for each of these. What we need instead is something like the following:
How many ip addresses can one find in the header of an ip packet
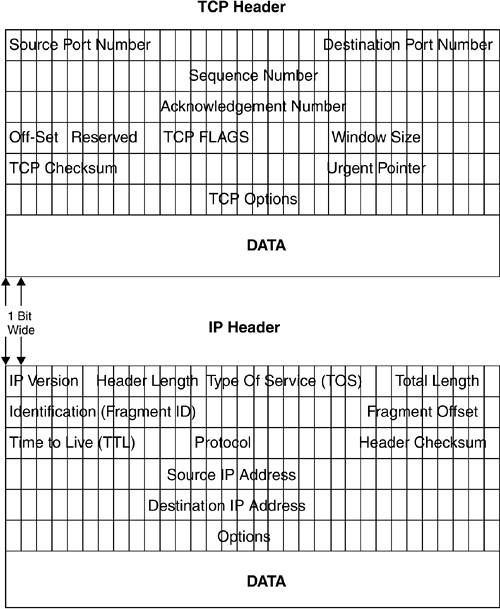
This section describes the contents of a TCP/IP packet header so you can understand what you see in the Tcpdump display. The layout of the TCP/IP packet is specified in RFC 793 for the TCP portion and RFC 791 for the IP portion. You can find the full text of these RFCs online at www.rfc-editor.org. Figure 6.1 is a graphical representation of TCP and IP headers. Both header types are at least 20 bytes long and are usually shown in 32-bit (4-byte) sections with the addresses, options, and other settings for the session.
Figure 6.1. TCP/IP Header
Let’s look at the IP portion first, since this is the lowest layer of the network model. The IP protocol header contains the delivery address for the packet and its sender. Since each address is 32 bits (4 octets of 8 bits each), the source and destination IP address takes up 8 bytes. The first part of the header contains various switches and options for the packet. The first line contains several switches that identify the IP version. Most networks uses IP version 4 (IPv4), but a newer 128-bit IP system called IP version 6 (IPv6) has been circulating for several years and has been gradually gaining acceptance. IPv6 is supposed to solve the IP address space problem by allowing up to 128 bits for the address portion.
This should create enough addresses to solve any foreseeable address space needs. IPv6 also resolves the security and verification issues with IPv4. But for now, you will mostly see IPv4 packets. Then there are the Header Length and the Type Of Service settings (TOS), which allow for differentiating in the priority of packets. The last part of this line is the total length of the header, which is normally the same from packet to packet (20 bytes), but can vary for newer protocols like IPv6.
The next two lines deal with identification of the packet and a checksum to make sure that it is valid. Finally, there are the source and destination IP addresses, and an options field that can be variable length or padded with zeros and any data.
The TCP header takes care of establishing a TCP session and higher-level functions. It is usually 20 bytes long and starts with a source port number of 16 bits and a destination port number of 16 bits. This is why the port numbers can only go up to 65,535—because the port number field in TCP/IP is a 16-bit binary number and 2 16 power equals 65,536, or 0–65,565. (It is interesting how all these seemingly arbitrary numbers always have a basis in something.)
The port numbers, as mentioned earlier, identify which program the packets need to be directed to on the remote machine and identify the session on the local machine. The next line contains a sequence number. This is used to reassemble the packets in the right order at the other end, even if they arrive in a different order. This is one of the fault-tolerant aspects of TCP sessions. After that, there is an acknowledgment number, also 32 bits long, which allows for verification that it is coming from the right machine. The next line contains a 4-bit section called the data offset, which gives how many 32-bit lines or «words» are in this header (typically 4) and 6 bits that are reserved for future use. After that there is a 6-bit section called the TCP Flags; the last half of that line is used to confer the window size, which tells the recipient how many bits the sender is willing to accept. The Flags are pretty important, as this is where different TCP control bits are set that control how the packet is handled. Each type of TCP communication is designated by one bit, with one being on, or set, and zero being off. Table 6.1 lists the six fields of the TCP Flag section and describes their use. Note: Each «field» is one bit wide, simply a one or zero, on or off.