How to connect via ssh
How to connect via ssh
Search Results
No Results
Filters
Connecting to a Remote Server Over SSH on Windows
A secure shell (SSH) is used for secure communication between devices. When most people refer to SSH, it is within the context of a connecting from a local computer to a remote server, commonly for administration tasks related to website hosting.
This article walks you through how to use SSH from Windows, covering the basics of installing a Windows SSH command-line tool and connecting to a remote server (such as a Linode) over SSH on a local Windows system.
Before You Begin
Ensure you have a Linux server with an SSH server (like OpenSSH) installed. Most Linux distributions have an SSH server preinstalled. If you wish to deploy a new server, follow the Creating a Compute Instance guide to create a Linode.
If using Windows 10 or Windows 11, install any pending updates to ensure you are running the latest version of Windows before you enable SSH.
Open the Terminal
On your local Windows computer, open the terminal application you wish to use. The terminal allows you to access your operating system’s shell environment and run programs through the command line, such as the SSH command.
There are two terminals on Windows 10 and 11, the Command Prompt (also called CMD) and PowerShell. To connect to a server using SSH on Windows 10 within one of these tools, the OpenSSH client needs to be installed. OpenSSH is a Windows SSH client and available on newer versions of Windows 10 (April 2018 update and later), though it may need to be manually enabled.
Install the OpenSSH Client
Open up Windows Search by selecting the search area (or search button) on the taskbar or by pressing Windows + S on the keyboard.
Start typing “Manage optional features” and select Manage optional features (System settings) from the search results.
The Optional features page of the Settings application launches. Under the Installed features list, look for the OpenSSH Client feature.
If the OpenSSH Client feature is not installed, click the Add a feature button at the top of the page. A dropdown menu appears. Select OpenSSH Client and press the Install button to install the ssh on Windows.
Open the Command Prompt or PowerShell
To run the SSH command, you first need to open your preferred command line utility. Open Windows Search through the Windows + S hotkey, type “Command Prompt” or “PowerShell” into the search area, and select the corresponding application from the results. PowerShell 7 or later, the newer cross-platform PowerShell application, can also be used if installed.
Instead of using the Command Prompt or PowerShell environment (which is significantly different than both the macOS and Linux command-line environments), you can run Linux directly within Windows through WSL (Windows Subsystem for Linux). This may be preferred if you are more comfortable working within a Linux shell environment.
Install WSL by following the instructions within Microsoft’s Install WSL guide. If you already have WSL1 installed, it’s recommended to update to WSL2.
Once everything has been configured, you can use the WSL environment by opening your installed Linux distribution through the Start Menu or Windows Search. By default, WSL uses a fairly basic terminal emulator. You can also use a more customizable terminal, such as Windows Terminal or Hyper.
There is no native SSH client in Windows 8 and earlier. Instead, you’ll need to use a third party application, such as PuTTY, Cygwin, the Secure Shell extension for Google Chrome, or any other SSH-enabled terminal emulator:
Connecting to the Remote Server Over SSH from Windows
Once you’ve opened your preferred Windows SSH client (Command Prompt, PowerShell, or WSL), you can run the ssh command to connect to your server.
Within the terminal, enter the following command, replacing [username] with the username of the remote user and [ip-address] with the IP address or domain name of the remote server.
The SSH client attempts to connect to the remote server over port 22 (the default SSH port).
When you connect with a server for the first time, the SSH client on Windows 10 prompts you to check and verify the host key’s fingerprint. This is normal, and results in output similar to:
You can verify the fingerprint by following the instructions on the Verifying the Authenticity of a Remote Server guide.
Ending the SSH Session
At this point, the shell prompt returns to the one for the local workstation and the terminal application can be closed if it’s no longer needed.
Sending Commands Over SSH
Instead of using SSH to open your remote server’s console, you can run commands on your server without leaving your local shell environment. This can enable you to quickly run commands both locally and remotely in the same terminal window.
Sending a Single Command
To run a single command on your remote server, use the following command. Replace [username] with the username of the remote user, [ip-address] with the IP address or domain name of the remote server, and [command] with the command you wish to run.
Sending Multiple Commands
To run multiple commands on your remote server (one after the other), use the following command. Replace [command-1], [command-2], and [command-3] with the commands you wish to run.
Using sudo
Going Further
Troubleshooting SSH Connection Issues
If SSH isn’t connecting you to your Linode, you may need to investigate the state of your server. See the guide Troubleshooting SSH for assistance.
Increasing Security
Now that you can connect from your Linux machine to the Linode over SSH, save not only time but also make the connection even more secure by using SSH public key authentication. For more information, see SSH add keys.
See the “Harden SSH Access” section of Setting Up and Securing a Compute Instance guide to review how to secure SSH on the server’s side, and the Advanced SSH Server Security for more information on making it even more secure.
This page was originally published on Friday, June 25, 2021.
How to Connect to a Linux Server Using Secure Shell (SSH)
Need Hosting? Try ours, it’s fast, reliable and feature loaded with support you can depend on.
Remote Login
There are times when we have access to physical servers and we can login directly from the server console in front of the server, or at least next to the server via KVM console. But, most of the time we don’t have access to the physical server so that we have to login remotely to the server. In this tutorial we’ll learn how to login remotely to a Linux Server using Secure Shell (SSH). Of course, you can also use this tutorial as guide to login to *NIX family operating systems as long as they have SSH installed.
Tools
Login Using a Password
The most simple way to login to Linux Server is using a password as an authentication mechanism. In this section we’ll learn how to login to Linux server using a username and password pair.
Login From Linux or MacOS X
Linux, MacOS X and most UNIX variants have SSH installed by default, you don’t need to install any additional packages unless you only install the minimalist package that does not install openssh package. In this tutorial I assume that you already have ssh client installed.
To login to a Linux server using ssh you can use the command below :
The warning above is shown if you are connecting to the server for the first time. The SSH client will check the authenticity of the server by checking the SSH fingerprinting. Since this is first time connection, SSH does not have any record of this server fingerprint and wil ask you whether you want to trust this server or not. You can type yes on the question above and input your password.
If you have logged into this server before and you get this message again there are several possibilities that could happen :
Login From Windows
Now we’ll learn how to login to a Linux Server from a Windows Machine using PuTTY. I assume that you already download PuTTY.
If you login to this server for the first time you will get a security alert regarding server fingerprint. If you are sure that you’re connecting to the right server you can click Yes.
You have to input your username and password to login.
Password-less Login
In the section above, we already learned how to login using username and password pair. In this section we’ll learn how to login without password, we’ll use keypair instead.
First thing that we have to do is creating keypair. We’ll get a private and public key. You have to keep your private key secure while you can use the public key on the server. You can use the same private & public key on multiple servers.
Generate an SSH Keypair on MacOS X and Linux
To generate keypair on MacOS X and Linux, you can use comand below :
Copy a Public Key to a Server
To copy public key to server, we can use scp program. We’ll learn a little bit more about using scp on the section below. You can run command below to copy keyfile.pub that you just generated to a server:
(tidle) symbol above means home. So this command will copy the public key to the user home directory.
After copying the file you need to login to the server and run command below on the server:
Securing a Private Key
I recommend moving your private key to
Login With a Keypair on Linux or MacOS X
Now the keypair is ready to be used to login to the server. You can use the ssh command below :
Generate an SSH Keypair on Windows
Login using Keypair using PuTTY
Copying Files Using Secure Copy
Copying Files From Linux or MacOS X Using SCP
In this section we’ll learn how to copy files and or folders to a Linux server and vice versa. Linux and MacOS X also have scp program installed by default so you don’t have to install additional program.
To copy a single file from our computer to a server, we can run :
Copying Files From Windows Using WinSCP
You can copy files and/or folders from a Windows client to Linux Servers and vice versa using WinSCP. You can choose between portable executable or installable WinSCP.
Running a Command Remotely On Server
Conclusion
In this tutorial we’ve learn how to connect via SSH from Windows, Linux and MacOS X machine. We also learned how to do password-less login and run remote commands on the server from the computer.
How to connect to your server via SSH
This guide will explain how to connect to your server via SSH. For customers using LCN Cloud servers or legacy VPS/Dedicated servers.
Let’s get started…
What is SSH?
SSH (Secure-shell) is a network protocol used to securely connect to a remote computer – this is commonly used for command line access on Unix/Linux systems.
If you have a server with LCN, you’ll be provided with SSH login details to access it. The following guide will explain how to connect to your server via SSH in Windows, Mac OS/x or Linux systems.
Connecting using SSH
To connect to your server via SSH, access to the server over port 22 will need to be enabled – this is enabled by default in the firewall rules for Cloud servers. If you have customised the firewall settings for your server, check that access via port 22 is enabled.
Windows
To connect using SSH in Windows, you’ll need to download an SSH client like Putty. Select the appropriate version for your operating system (32 or 64 bit) to download and run the installer for Putty.
When you run the Putty application you’ll see the following menu for Putty configuration:
Enter the hostname or IP address of your server into the Host Name field and leave the port number set to 22.
Select Open to open a connection to your server, you’ll see a login prompt to enter a username, then just enter your SSH username and password to connect to your server.
Please Note: that when entering your SSH password, the cursor will not move or provide an indication that you have entered any text.
Mac OS/x and Linux
Mac OS and Linux operating systems will include an SSH client by default that you can use to connect to a remote server.
In Mac OS this can be accessed by opening the terminal application, for Linux based operating systems open the terminal or command prompt application for the Linux distro/desktop environment you are using.
You can then connect to your server via SSH by entering a command in the following format:
Replace with your SSH username and with the hostname or IP address of your server. You’ll then be prompted to enter the password for your SSH username.
Please Note: that when entering your SSH password, the cursor will not move or provide an indication that you have entered any text.
That’s it, you’ve successfully connected to the command line interface for your server via SSH and should see a prompt allowing you to enter commands.
How to Use SSH to Connect to a Remote Server in Linux or Windows
Home » Web Servers » How to Use SSH to Connect to a Remote Server in Linux or Windows
Introduction
Accessing machines remotely became a necessity a long time ago and we can barely imagine how it would be if we couldn’t control computers from remote locations. There are many ways to establish a connection with a remote machine depending on the operating system you are running, but the two most used protocols are:
The two protocols use the client and server applications to establish a remote connection. These tools allow you to gain access and remotely manage other computers, transfer files, and do virtually anything you can do while physically sitting in front of the machine.
Prerequisites
Before you can establish a secure remote desktop protocol with a remote machine, there are a few basic requirements to meet:
What is SSH?
Secure Shell, sometimes referred to as Secure Socket Shell, is a protocol which allows you to connect securely to a remote computer or a server by using a text-based interface.
When a secure SSH connection is established, a shell session will be started, and you will be able to manipulate the server by typing commands within the client on your local computer.
System and network administrators use this protocol the most, as well as anyone who needs to manage a computer remotely in a highly secure manner.
How Does SSH Work?
In order to establish an SSH connection, you need two components: a client and the corresponding server-side component. An SSH client is an application you install on the computer which you will use to connect to another computer or a server. The client uses the provided remote host information to initiate the connection and if the credentials are verified, establishes the encrypted connection.
On the server’s side, there is a component called an SSH daemon that is constantly listening to a specific TCP/IP port for possible client connection requests. Once a client initiates a connection, the SSH daemon will respond with the software and the protocol versions it supports and the two will exchange their identification data. If the provided credentials are correct, SSH creates a new session for the appropriate environment.
The default SSH protocol version for SSH server and SSH client communication is version 2.
How to Enable an SSH Connection
Since creating an SSH connection requires both a client and a server component, you need to make sure they are installed on the local and the remote machine, respectively. An open source SSH tool—widely used for Linux distributions— is OpenSSH. Installing OpenSSH is relatively easy. It requires access to the terminal on the server and the computer that you use for connecting. Note that Ubuntu does not have SSH server installed by default.
How to Install an OpenSSH Client
Before you proceed with installing an SSH client, make sure it is not already installed. Many Linux distributions already have an SSH client. For Windows machines, you can install PuTTY or any other client of your choice to gain access to a server.
To check if the client is available on your Linux-based system, you will need to:
This means that you are ready to remotely connect to a physical or virtual machine. Otherwise, you will have to install the OpenSSH client:
You are now able to SSH into any machine with the server-side application on it, provided that you have the necessary privileges to gain access, as well as the hostname or IP address.
How to Install an OpenSSH Server
In order to accept SSH connections, a machine needs to have the server-side part of the SSH software toolkit.
If you first want to check if OpenSSH server is available on the Ubuntu system of the remote computer that needs to accept SSH connections, you can try to connect to the local host:
If the above is the case, you will need to install the OpenSSH server. Leave the terminal open and:
The required support files will be installed, and then you can check if the SSH server is running on the machine by typing this command:
The response in the terminal should look similar to this if the SSH service is now running properly:
Another way to test if the OpenSSH server is installed properly and will accept connections is to try running the ssh localhost command again in your terminal prompt. The response will look similar to this screen when you run the command for the first time:
Enter yes or y to continue.
Congratulations! You have set up your server to accept SSH connection requests from a different
computer using an SSH client.
TIP
You can now edit the SSH daemon configuration file, for example, you can change the default port for SSH connections. In the terminal prompt, run this command:
The configuration file will open in the editor of your choice. In this case, we used Nano.
If you need to install Nano, run this command:
Please note that you need to restart SSH service every time you make any changes to the sshd_config file by running this command:
How to Connect via SSH
Now that you have the OpenSSH client and server installed on every machine you need, you can establish a secure remote connection with your servers. To do so:
If the computer you are trying to remotely connect to is on the same network, then it is best to use the private IP address instead of the public IP address. Otherwise, you will have to use the public IP address only. Additionally, make sure that you know the correct TCP port OpenSSH is listening to for connection requests and that the port forwarding settings are correct. The default port is 22 if nobody changed configuration in the sshd_config file. You may also just append the port number after the host IP address.
Here is the example of a connection request using the OpenSSH client. We will specify the port number as well:
You are now able to manage and control a remote machine using your terminal. If you have trouble connecting to a remote server, make sure that:
Note: If SSH responds with a message “Connection refused”, please refer to our article How To Fix The SSH “Connection Refused” Error for possible reasons and solutions.
SSH Further Steps
Now that you are able to establish a connection to your server using SSH, we highly recommend a few further steps to improve SSH security. When you leave the setup with the default values, it is more likely to be hacked and your server can easily become a target of scripted attacks.
Some of the suggestions for hardening SSH by editing the sshd configuration file include:
You can also use TCP wrappers to restrict access to certain IP addresses or hostnames. Configure which host can connect using TCP wrappers by editing the /etc/hosts.allow and etc/hosts.deny files.
Note that allowed hosts supersede the denied hosts. For example, to allow SSH access to a single host you will first deny all hosts by adding these two lines in the etc/hosts.deny :
sshd : ALL
ALL : ALL
Make sure to keep your log in information secure at all times and to apply security at multiple layers. Use different methods to limit SSH access to your servers, or use services that will block anyone who tries to use brute force to gain access to your servers. Fail2ban is one example of such service.
VNC Over SSH
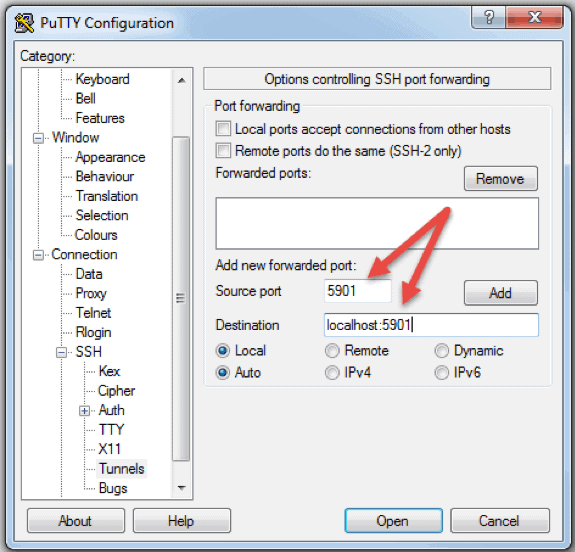
For users who are used to working in a graphical desktop environment with Virtual Network Computing (VNC), it is possible to completely encrypt connections using SSH tunneling. In order to tunnel VNC connections over SSH, you will need to run this command in the terminal on your Linux or UNIX machine:
Here is the breakdown of the command above:
You can also connect to a remote server via SSH tunnel from a Windows machine by using PuTTY. In the PuTTY configuration window:
Note: If you are using Ubuntu, refer to our installation guide How to Install PuTTY on Ubuntu.
What is RDP?
Remote Desktop Protocol (RDP) is a protocol developed by Microsoft. It is used to control and manage machines with a Windows operating system remotely.
Unlike Secure Shell, connections established using an RDP client provide a user with a graphical interface through which they can gain access to a remote computer and control it in the same manner as their local computer.
Using Remote Desktop services, formerly known as terminal services, allows network and system engineers to easily manipulate remote computers connected to a local network or the Internet.
This comes with a price. If you do not use a virtual private network (VPN), connecting via RDP is far less secure than SSH because you are directly exposed to the internet. There are many automated scripts constantly looking for weaknesses in your connection, especially for open ports that Windows Remote Desktop connections use. In that case, it is highly recommended to have strong, secure passwords and change them regularly. This does not make RDP connections safe, but less vulnerable.
How Does Remote Desktop Protocol Work?
Windows Remote Desktop connection is based on a rather simple client-server model using Remote Desktop Protocol (RDP). After you enable it, the Windows Remote Desktop server-side service starts listening for connection requests on port 3389. Whenever you try to connect to a Windows server, you will need to provide a valid username for the account you are using to gain access remotely. Once you gain access to the server, you will be able to manage applications, transfer files between the two computers, and virtually perform any task you can perform locally with the account in question.
No matter what version of the Windows operating system you have, you will be able to establish a secure remote connection to another computer since the Remote Desktop client is available by default. On the other hand, a computer can be remotely accessible only if it runs on a Pro, Enterprise, or Server edition of a Windows operating system. So, we can conclude that RDP connections are possible only between computers with a Windows OS on them.
How to Enable an RDP Connection
Establishing a Remote Desktop connection to another computer over network requires you to enable the Windows Remote Desktop server service. The Remote Desktop client is integrated into Windows systems, ready out of the box, and does not need any special setup before you can connect to another Windows-based machine. However, accepting Remote Desktop connections from another machines is disabled by default on all version of Windows OS.
If you want to remotely connect to a server over the Internet and not through the local network, you need to take a few things into consideration before you enable this service:
Enabling Remote Access in Windows 7, 8, 10 and Windows Server Versions
The procedure to configure remote desktop and allow secure remote connections to a server or a PC from a different computer is similar for all versions of Windows operating systems. I will list the basic steps to enable remote access to a desired machine. Before you begin, please make sure that you have taken into consideration the notes listed above concerning port forwarding, VPN, and firewall settings.
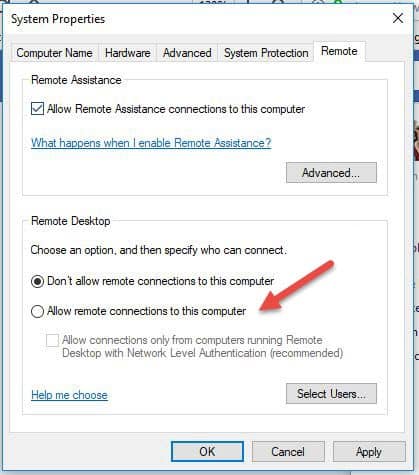
Step 1: Allow Remote Connections
Go to the computer information on the machine where you want to allow remote connections:
Step 2: Add Users to the List of Remote Users
You need to perform this step only if you want to allow users other than administrators to access the machine in question. If you are an administrator, your account is automatically included in the list of allowed users but you will not see it. To select more users:
There are not many other options to change in order to configure Remote Desktop. Provided that other settings do not interfere with your Remote Desktop connection, you are now able to remotely connect and control this computer.
How to Use the Remove Desktop Connection Client
Using the Remote Desktop client is straightforward and you do not need to specifically configure Remote Desktop on the local computer. The steps below will work for all versions of Windows starting from Windows 7.
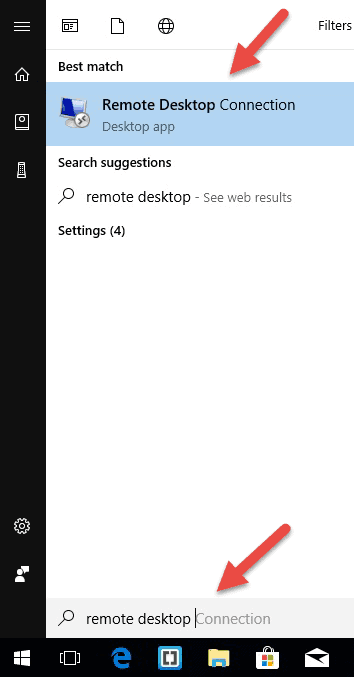
Step 1: Launch the Destkop Connection Unit
On your local Windows computer, locate the Remote Desktop Connection application. You can find it in a couple of different ways:
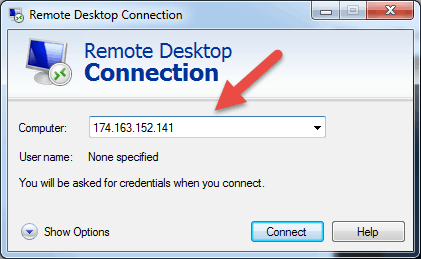
Step 2: Enter the Remote Hosts IP Address or Name
Once you launch the Remote Desktop Connection application, you will get a window where you can enter the name or the IP address of a remote machine you want to access.
In the Computer field, type in the corresponding name or IP address and click Connect.
Note: If the default listening port for Remote Desktop connection (port 3389) has been changed on the remote host to a different value, you will have to specify it after the IP address.
Example: 174.163.152.141:6200
Depending on your circumstances, you will either need to enter the private or public IP address of the remote host. Here are the possible scenarios:
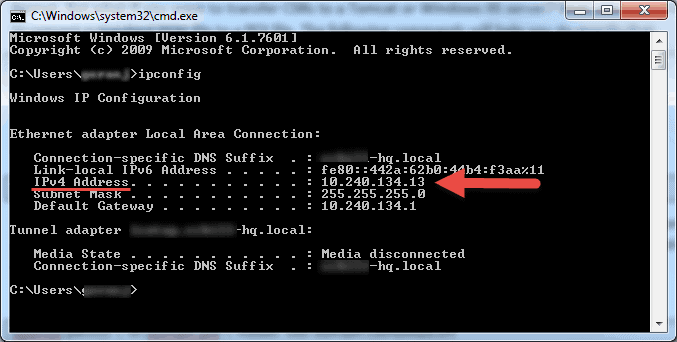
How to Find the IP Address and Host Name
There are many ways to locate the name, public or private IP address of a computer where you want to configure Remote Desktop service. Here are the quickest and easiest methods:
To determine a computer’s private IP address:
To determine which public IP address a computer is using:
To find a computer’s name:
Step 3: Entering the RDP Credentials and Finalizing the Connection
After you hit connect, the loading bar will appear. When it finishes initiating and configuring the remote session you will get a pop-up window that will look similar to this:
Note: Only one user can be logged in at the same time on a Windows computer. If someone else is using the machine you are trying to remotely access, that user has to disconnect. The warning logon message will appear in such cases.
You will not see the desktop of the remote machine. Depending on the user account permission settings, you can now perform any operation that you can while working directly in front of it.
Remote Desktop Protocol Further Steps
When setting up your remote server or machine to accept remote desktop connections, it is important to take precautions concerning securing RDP. Your server is especially vulnerable if you are accessing it over the Internet.
Here are a few pieces of advice to keep in mind if you are using remote desktop protocol to remotely connect to your machines:
These best practices for additionally securing RDP will help you tighten down remote desktop access. You will avoid most of the unauthorized login attempts without spending too much time making configuration changes to your machines.
Note: Learn how to use SSHFS to mount remote file systems over SSH.
Conclusion
The steps and processes listed in this guide will work for most users and most versions of Linux and Windows operating systems.
You should now be able to Connect to a Remote Server with Linux or Windows.
There are of course many other methods to establish a connection between two remote computers, but the ones covered here are most common.
How To Use SSH to Connect to a Remote Server
Introduction
One essential tool to master as a system administrator is SSH.
SSH, or Secure Shell, is a protocol used to securely log onto remote systems. It is the most common way to access remote Linux servers.
In this guide, we will discuss how to use SSH to connect to a remote system.
Core Syntax
To connect to a remote system using SSH, we’ll use the ssh command.
If you are using Windows, you’ll need to install a version of OpenSSH in order to be able to ssh from a terminal. If you prefer to work in PowerShell, you can follow Microsoft’s documentation to add OpenSSH to PowerShell. If you would rather have a full Linux environment available, you can set up WSL, the Windows Subsystem for Linux, which will include ssh by default. Finally, as a lightweight third option, you can install Git for Windows, which provides a native Windows bash terminal environment that includes the ssh command. Each of these are well-supported and whichever you decide to use will come down to preference.
If you are using a Mac or Linux, you will already have the ssh command available in your terminal.
The most straightforward form of the command is:
The remote_host in this example is the IP address or domain name that you are trying to connect to.
This command assumes that your username on the remote system is the same as your username on your local system.
If your username is different on the remote system, you can specify it by using this syntax:
Once you have connected to the server, you may be asked to verify your identity by providing a password. Later, we will cover how to generate keys to use instead of passwords.
To exit the ssh session and return back into your local shell session, type:
How Does SSH Work?
In the previous section, ssh was the client program. The ssh server was already running on the remote_host that we specified.
On nearly all Linux environments, the sshd server should start automatically. If it is not running for any reason, you may need to temporarily access your server through a web-based console, or local serial console.
The process needed to start an ssh server depends on the distribution of Linux that you are using.
On Ubuntu, you can start the ssh server by typing:
That should start the sshd server and you can then log in remotely.
How To Configure SSH
When you change the configuration of SSH, you are changing the settings of the sshd server.
Back up the current version of this file before editing:
Open it using nano or your favourite text editor:
You will want to leave most of the options in this file alone. However, there are a few you may want to take a look at:
The host keys declarations specify where to look for global host keys. We will discuss what a host key is later.
These two items indicate the level of logging that should occur.
If you are having difficulties with SSH, increasing the amount of logging may be a good way to discover what the issue is.
These parameters specify some of the login information.
LoginGraceTime specifies how many seconds to keep the connection alive without successfully logging in.
It may be a good idea to set this time just a little bit higher than the amount of time it takes you to log in normally.
PermitRootLogin selects whether the root user is allowed to log in.
In most cases, this should be changed to no when you have created a user account that has access to elevated privileges (through su or sudo ) and can log in through ssh, in order to minimize the risk of anyone gaining root access to your server.
strictModes is a safety guard that will refuse a login attempt if the authentication files are readable by everyone.
This prevents login attempts when the configuration files are not secure.
These parameters configure an ability called X11 Forwarding. This allows you to view a remote system’s graphical user interface (GUI) on the local system.
You should thoroughly test your changes to ensure that they operate in the way you expect.
It may be a good idea to have a few terminal sessions open while you are making changes. This will allow you to revert the configuration if necessary without locking yourself out.
How To Log Into SSH with Keys
While it is helpful to be able to log in to a remote system using passwords, it is faster and more secure to set up key-based authentication.
How Does Key-based Authentication Work?
Key-based authentication works by creating a pair of keys: a private key and a public key.
The private key is located on the client machine and is secured and kept secret.
The public key can be given to anyone or placed on any server you wish to access.
When you attempt to connect using a key-pair, the server will use the public key to create a message for the client computer that can only be read with the private key.
The client computer then sends the appropriate response back to the server and the server will know that the client is legitimate.
This process is performed automatically after you configure your keys.
How To Create SSH Keys
SSH keys should be generated on the computer you wish to log in from. This is usually your local machine.
Enter the following into the command line:
You may be prompted to set a password on the key files themselves, but this is a fairly uncommon practice, and you should press enter through the prompts to accept the defaults. Your keys will be created at
Look at the permissions of the files:
As you can see, the id_rsa file is readable and writable only to the owner. This helps to keep it secret.
The id_rsa.pub file, however, can be shared and has permissions appropriate for this activity.
How To Transfer Your Public Key to the Server
If you currently have password-based access to a server, you can copy your public key to it by issuing this command:
This will start an SSH session. After you enter your password, it will copy your public key to the server’s authorized keys file, which will allow you to log in without the password next time.
Client-Side Options
There are a number of optional flags that you can provide when connecting through SSH.
Some of these may be necessary to match the settings in the remote host’s sshd configuration.
For instance, if you changed the port number in your sshd configuration, you will need to match that port on the client-side by typing:
Note: Changing your ssh port is a reasonable way of providing security through obscurity. If you are allowing ssh connections to a widely known server deployment on port 22 as normal, and you have password authentication enabled, you will likely be attacked by many automated login attempts. Exclusively using key-based authentication and running ssh on a nonstandard port is not the most complex security solution you can employ, but should reduce these to a minimum.
If you only want to execute a single command on a remote system, you can specify it after the host like so:
You will connect to the remote machine, authenticate, and the command will be executed.
As we said before, if X11 forwarding is enabled on both computers, you can access that functionality by typing:
Providing you have the appropriate tools on your computer, GUI programs that you use on the remote system will now open their window on your local system.
Disabling Password Authentication
If you have created SSH keys, you can enhance your server’s security by disabling password-only authentication. Apart from the console, the only way to log into your server will be through the private key that pairs with the public key you have installed on the server.
Warning: Before you proceed with this step, be sure you have installed a public key to your server. Otherwise, you will be locked out!
As root or user with sudo privileges, open the sshd configuration file:
After making your changes, save and close the file.
You can now reload the SSH daemon:
Password authentication should now be disabled, and your server should be accessible only through SSH key authentication.
Conclusion
Learning your way around SSH will greatly benefit any of your future cloud computing endeavours. As you use the various options, you will discover more advanced functionality that can make your life easier. SSH has remained popular because it is secure, light-weight, and useful in diverse situations.
Next, you may want to learn about working with SFTP to perform command line file transfers.
Want to learn more? Join the DigitalOcean Community!
Join our DigitalOcean community of over a million developers for free! Get help and share knowledge in our Questions & Answers section, find tutorials and tools that will help you grow as a developer and scale your project or business, and subscribe to topics of interest.
Источники информации:
- http://hostpresto.com/community/tutorials/how-to-connect-to-a-linux-server-using-secure-shell-ssh/
- http://www.lcn.com/support/articles/how-to-connect-via-ssh/
- http://phoenixnap.com/kb/ssh-to-connect-to-remote-server-linux-or-windows
- http://www.digitalocean.com/community/tutorials/how-to-use-ssh-to-connect-to-a-remote-server