How to decrypt txt
How to decrypt txt
How To Encrypt & Decrypt a Text File In Windows 10
Using built-in and third party encryption tools
The Windows Notepad is a versatile text editor included in every version of Windows. You can use it for basic tasks such as note-taking and list-making, or more advanced tasks such as creating a batch file to automate commands on your computer.
At times, you might write something important in Notepad that requires extra security. Encrypting your Notepad text file is the best option to increase your security. So, here’s how you encrypt and decrypt a text file in Windows 10.
1. Windows Encrypting File System
The Windows Encrypting File System (EFS) is an integrated file encryption tool available to all Windows 10 versions except Home. EFS is not the same as Bitlocker, which you can use for full disk encryption. Instead, EFS works on a file-by-file basis, which makes it perfect for encrypting a text file.
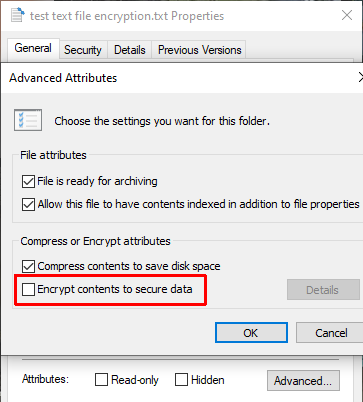
To use EFS to encrypt your file, right-click the text file and select Properties. Now, select Advanced, then check the box to Encrypt contents to secure data. Press OK, then Apply.
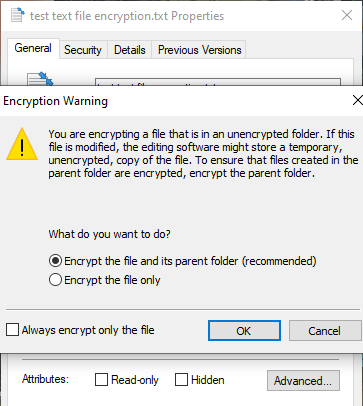
The Encryption Warning will appear, explaining that encrypting the single file can cause an issue under certain circumstances and that encrypting the entire folder offers more protection. If the file is in a frequently accessed folder, this means you’ll have to unlock the folder each time you want to access any other file. One way around this is to place your text file in a separate folder and use this as your secure folder.
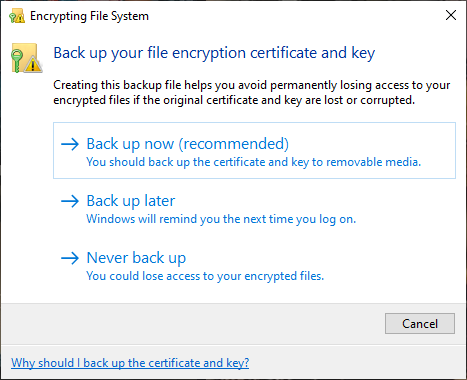
After confirming your selection, the Encrypting File System will ask you if you want to take a backup of the encryption key. You can use the encryption key backup if you forget your decryption password.
Exporting Your Encryption Key Backup
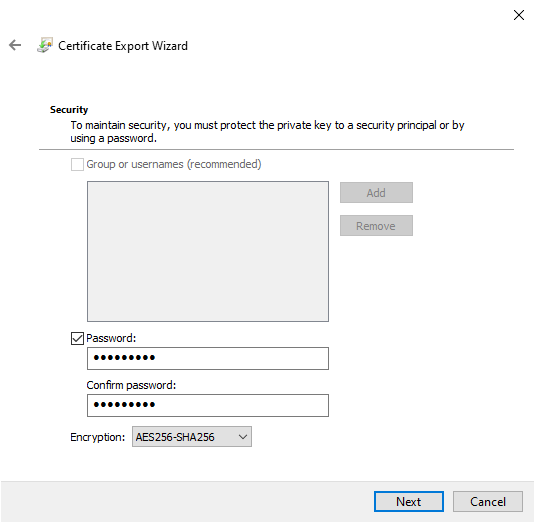
If you choose to export your encryption key backup for additional security, the Microsoft Certificate Export Wizard will run. The wizard will guide you through the creation and export of your encryption key to an external media source, such as a USB flash drive.
Select Personal Information Exchange from the first page, and check Export all extended properties. On the next page, you must input a secure and unique password to protect your text files. Switch the encryption type to AES256-SHA256 (extremely strong encryption!), then give your encryption key backup a filename. Press Finish to complete the process.
Once the process is complete, you’ll see a small lock icon on the text file icon, indicating its encryption status.
2. 7-Zip
Did you know that the archive tool, 7-Zip, also features an encryption tool? The 7-Zip option is handy for Windows 10 Home users who cannot use the Windows Encrypting File System and still want a quick way to encrypt text files.
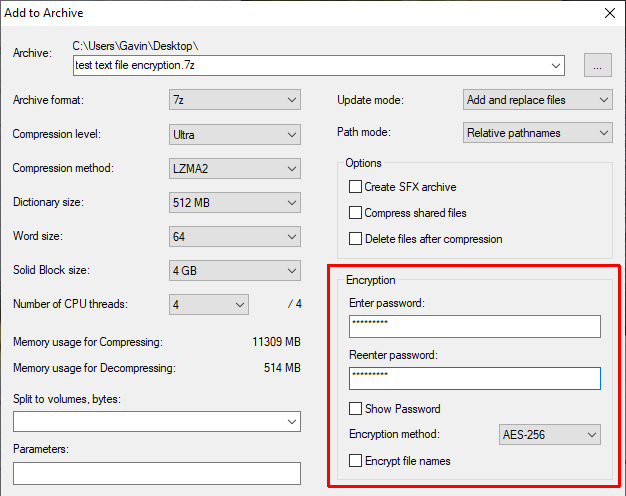
The 7-Zip encryption process is different from the EFS option. First, you must download and install the latest version of 7-Zip. Once installed, right-click the text file you want to encrypt. Select 7-Zip > Add to Archive to open the 7-Zip archive options.
Find the Encryption section on the right. Enter a strong and unique password, then press OK.
Now, when you want to access the file, you must input your password to decrypt the text file (or any other file in the archive). 7-Zip’s encryption tool is a handy way to encrypt several text files with minimal fuss.
3. AES Crypt
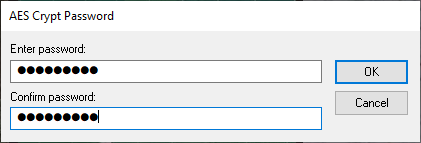
AES Crypt is a free and open-source tool you can use to encrypt text files. One of the best things about AES Crypt is the ease of use.
You install AES Crypt as normal. Once installed, right-click the text file you want to encrypt and select AES Crypt from the context menu. Enter a strong and unique password, then press OK. AES Crypt creates an encrypted copy of the text file.
The only thing to remember is to delete the original file. This is for two reasons. First, the encrypted copy is useless if someone can access the unencrypted original. Second, you won’t be able to decrypt your text file if AES Crypt detects that it still exists.
4. AxCrypt
The final single-file encryption tool for you to consider is AxCrypt, a powerful encryption tool with extensive features. However, you don’t need to worry about all of the features—just how AxCrypt will encrypt and decrypt your text file.
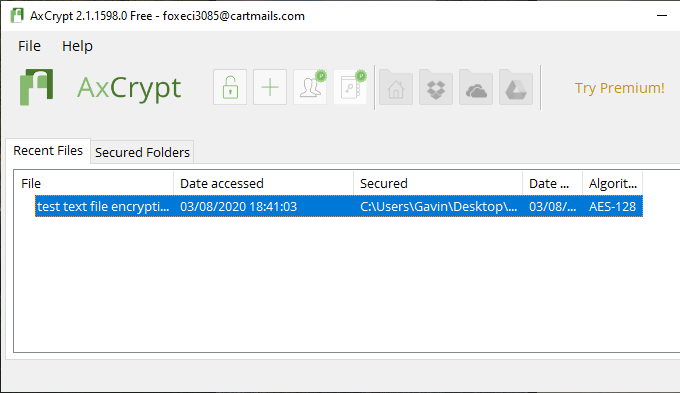
Download and install AxCrypt. The first time you launch AxCrypt, you have to run through the setup. You must provide an active email address to receive a verification code (which is essentially your free AxCrypt license), then copy and paste the code before confirming.
Next, you need to create your AxCrypt encryption password. This will encrypt and decrypt your personal text files, so make sure to create a strong and unique password. As the warning states, a password reset will let you back into your account, but it will not decrypt text files secured with the old password.
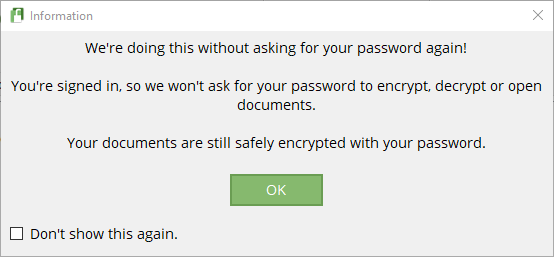
When you’re ready, drag and drop your text file into AxCrypt. AxCrypt will encrypt the file automatically. If you are logged into AxCrypt, you will not receive a password prompt to decrypt the text file. Once you close AxCrypt, you will receive a password prompt.
AxCrypt is a free encryption tool, which is why it features in our list of the best Windows freeware programs.
What’s The Best Way To Encrypt Text Files?
You have four options for encrypting your text files. The easiest option is 7-Zip, which is free, easy to use, and provides strong protection. That said, none of the other options are difficult to use—so long as you don’t forget your password!
Password creation can seem daunting. If you’re struggling, check out these easy ways to create a password you’ll always remember.
Gavin is a professional technology writer with a decade of experience covering security, gaming, cryptocurrencies, Windows, and Linux, plus some diversions into copywriting for real estate, sports, and PC hardware businesses. He graduated in 2010 with a BA (Hons) Contemporary Writing with Digital Arts and has been putting those writing skills to work ever since. Gavin lives in the depths of Cornwall with his family and enjoys hiking, board games, sea swimming, football, and tea. Read Gavin’s Full Bio
List of available regions
Main regions
Free Ransomware Decryption Tools
Hit by ransomware? Don’t pay the ransom!
Choose ransomware type
Our free ransomware decryption tools can help decrypt files encrypted by the following forms of ransomware. Just click a name to see the signs of infection and get our free fix.
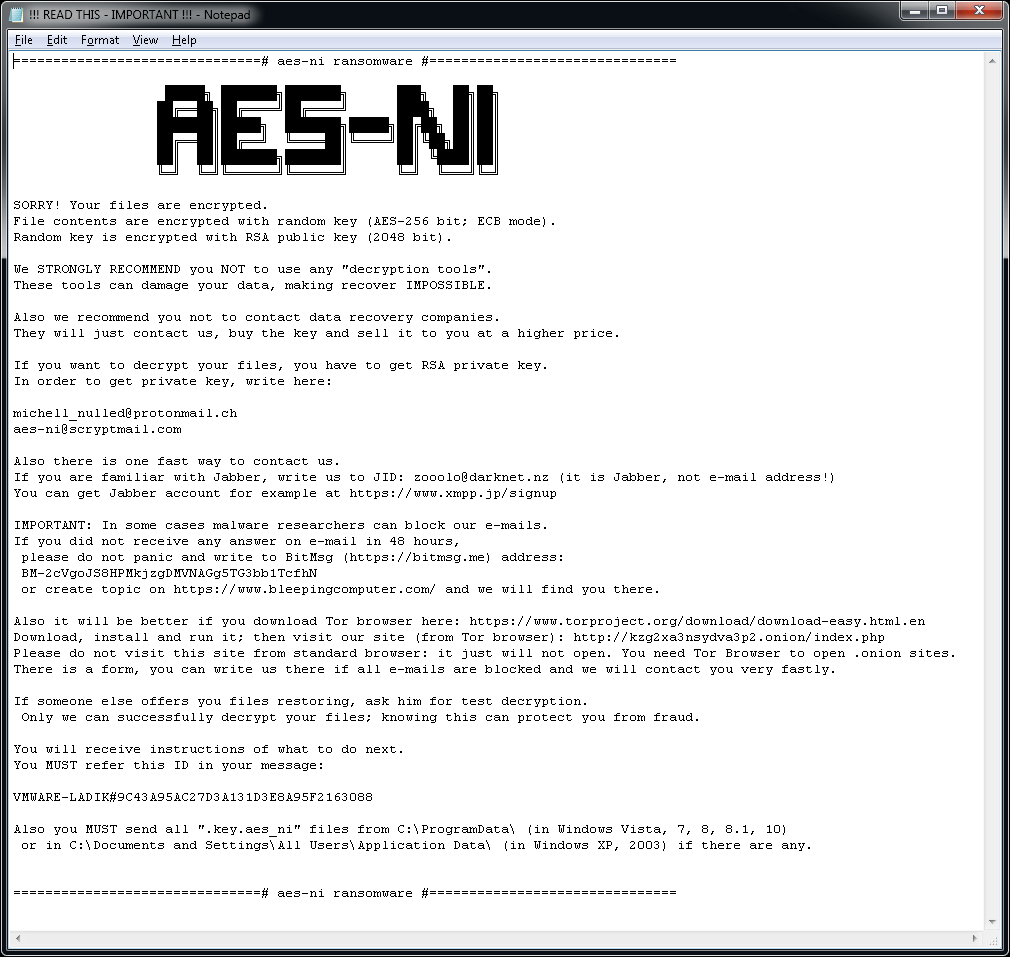
AES_NI
AES_NI is a ransomware strain that first appeared in December 2016. Since then, we’ve observed multiple variants, with different file extensions. For encrypting files, the ransomware uses AES-256 combined with RSA-2048.
The ransomware adds one of the following extensions to encrypted files:
.aes_ni
.aes256
.aes_ni_0day
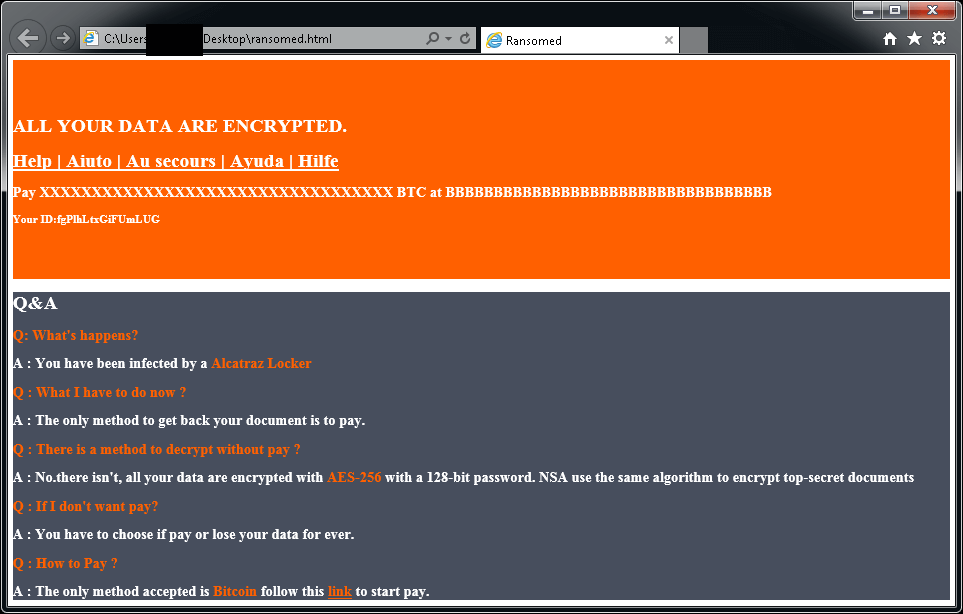
Alcatraz Locker
Alcatraz Locker is a ransomware strain that was first observed in the middle of November 2016. For encrypting user’s files, this ransomware uses AES 256 encryption combined with Base64 encoding.
Encrypted files have the «.Alcatraz» extension.
After encrypting your files, a similar message appears (it is located in a file «ransomed.html» in the user’s desktop):
If Alcatraz Locker has encrypted your files, click here to download our free fix:
Apocalypse
Apocalypse is a form of ransomware first spotted in June 2016. Here are the signs of infection:
Apocalypse adds .encrypted, .FuckYourData, .locked, .Encryptedfile, or .SecureCrypted to the end of filenames. (e.g., Thesis.doc = Thesis.doc.locked)
Opening a file with the extension .How_To_Decrypt.txt, .README.Txt, .Contact_Here_To_Recover_Your_Files.txt, .How_to_Recover_Data.txt, or .Where_my_files.txt (e.g., Thesis.doc.How_To_Decrypt.txt) will display a variant of this message:
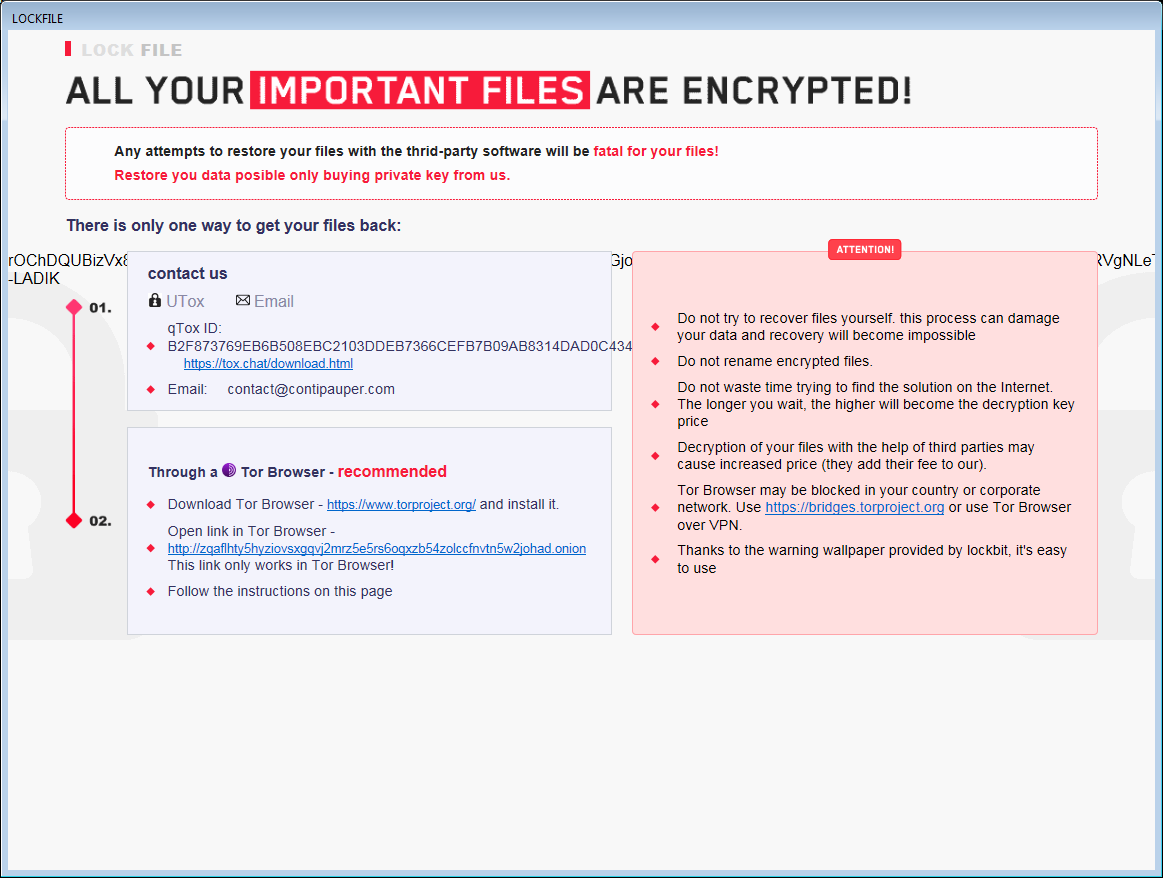
AtomSilo & LockFile
AtomSilo&LockFile are two ransomware strains analyzed by Jiří Vinopal. These two have very similar encryption schema, so this decryptor covers both variants. Victims can decrypt their files for free.
Encrypted files can be recognized by one of these extensions:
.ATOMSILO
.lockfile
Babuk
Babuk is a Russian ransomware. In September 2021, the source code leaked with some of the decryption keys. Victims can decrypt their files for free.
When encrypting file, Babuk appends one of the following extensions to the file name:
.babuk
.babyk
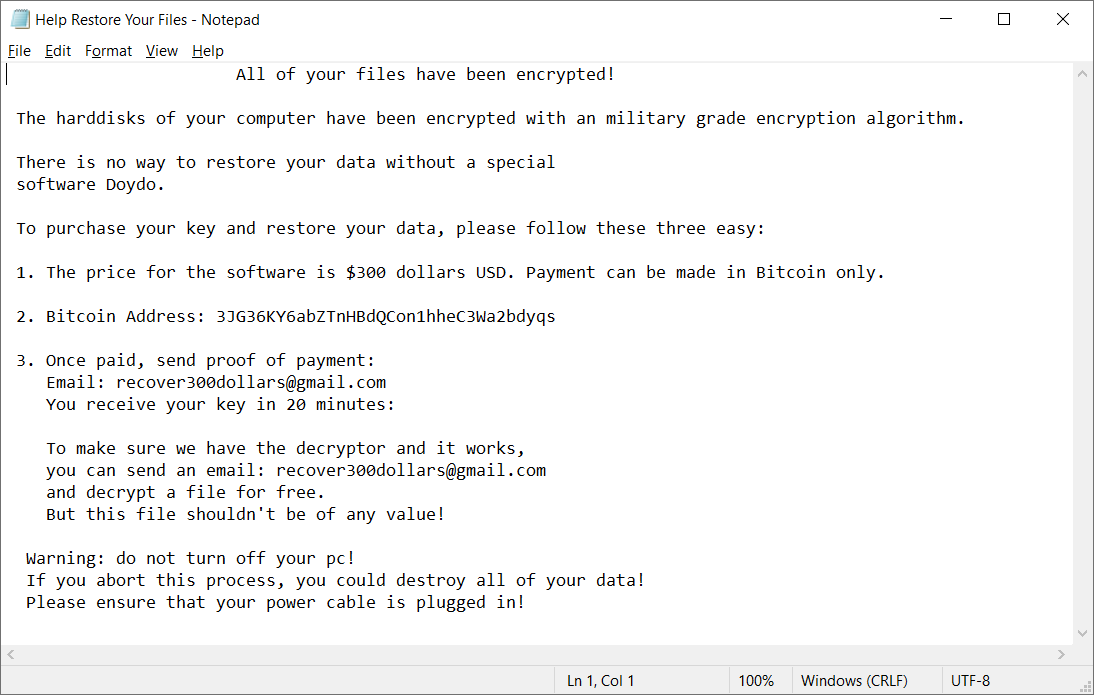
.doydo
In each folder with at least one encrypted file, the file Help Restore Your Files.txt can be found with the following content:
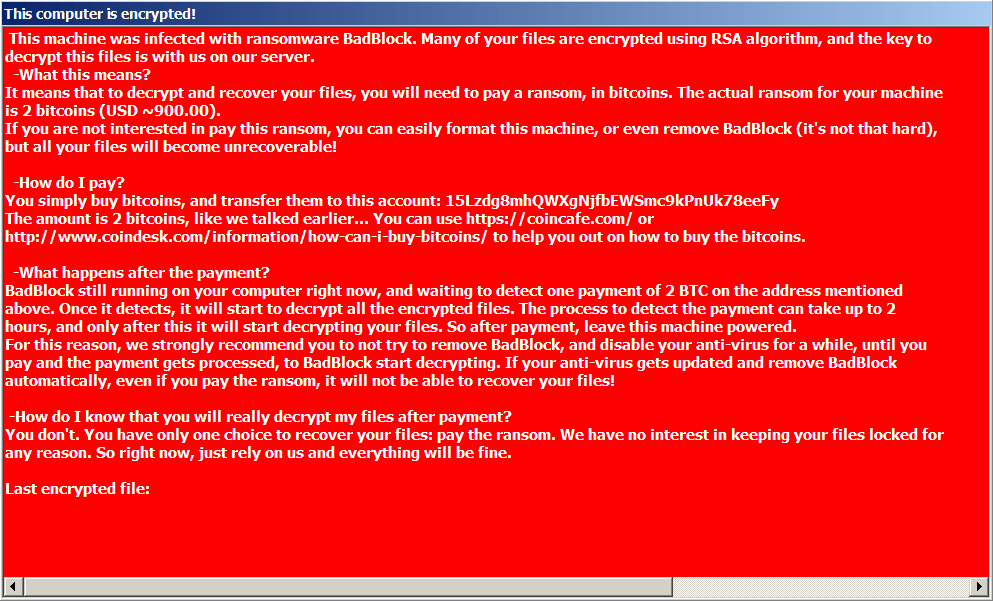
BadBlock
BadBlock is a form of ransomware first spotted in May 2016. Here are the signs of infection:
BadBlock does not rename your files.
After encrypting your files, BadBlock displays one of these messages (from a file named Help Decrypt.html):
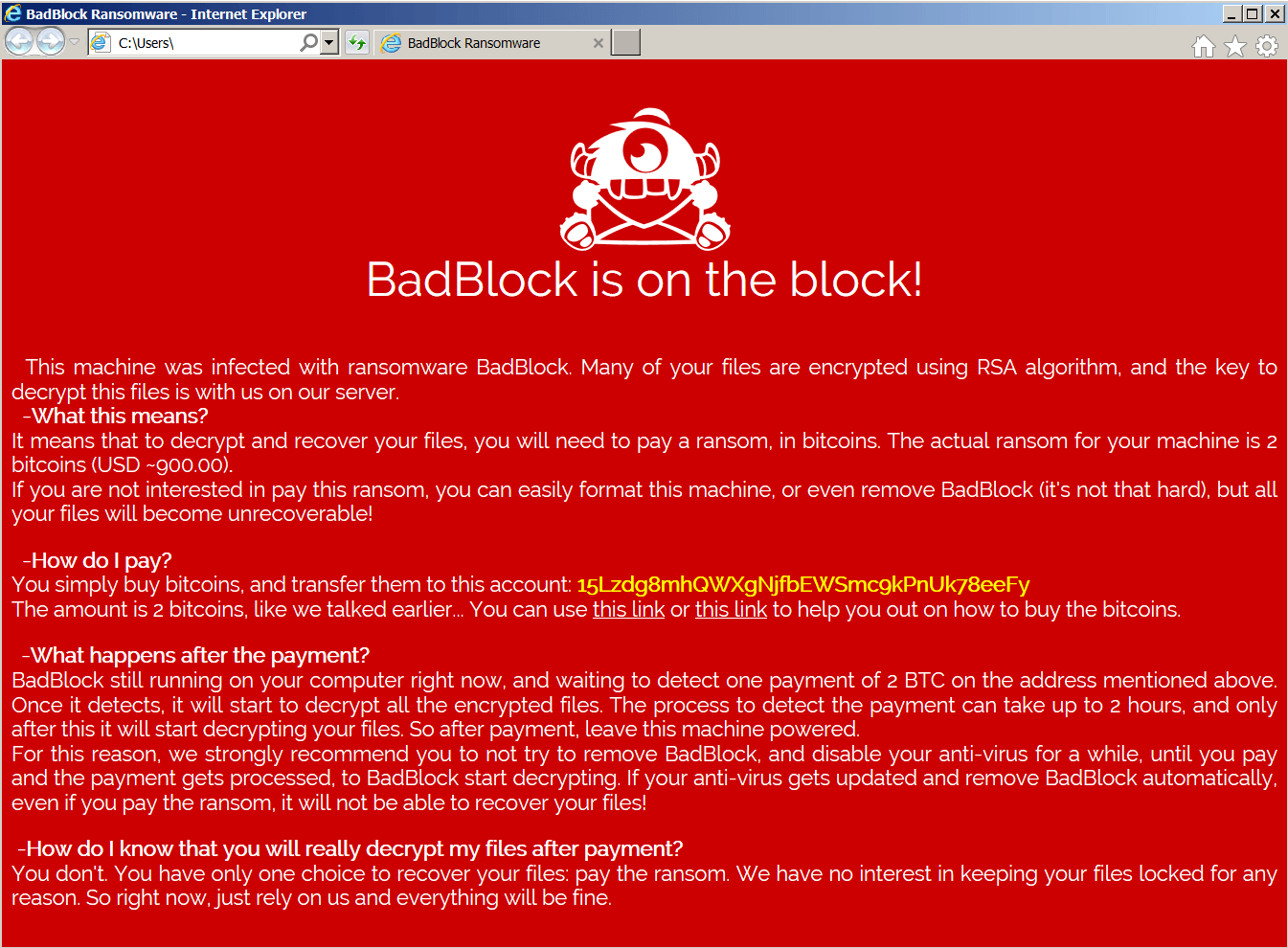
If BadBlock has encrypted your files, click here to download our free fix:
Bart is a form of ransomware first spotted at the end of June 2016. Here are the signs of infection:
Bart adds .bart.zip to the end of filenames. (e.g., Thesis.doc = Thesis.docx.bart.zip) These are encrypted ZIP archives containing the original files.
After encrypting your files, Bart changes your desktop wallpaper to an image like the one below. The text on this image can also be used to help identify Bart, and is stored on the desktop in files named recover.bmp and recover.txt.
If Bart has encrypted your files, click here to download our free fix:
Acknowledgement: We’d like to thank Peter Conrad, author of PkCrack, who granted us permission to use his library in our Bart decryption tool.
BigBobRoss
BigBobRoss encrypts user’s files using AES128 encryption. The encrypted files have new extension «.obfuscated» appended at the end of the file name.
The ransomware adds the following extension: .obfuscated
The ransomware also creates a text file named «Read Me.txt» in each folder. The content of the file is below.
BTCWare
BTCWare is a ransomware strain that first appeared in March 2017. Since then, we observed five variants, that can be distinguished by encrypted file extension. The ransomware uses two different encryption methods – RC4 and AES 192.
Encrypted file names will have the following format:
foobar.docx.[sql772@aol.com].theva
foobar.docx.[no.xop@protonmail.ch].cryptobyte
foobar.bmp.[no.btc@protonmail.ch].cryptowin
foobar.bmp.[no.btcw@protonmail.ch].btcware
foobar.docx.onyon
After encrypting your files, the desktop wallpaper is changed to the following:
You may also see one of the following ransom notes:
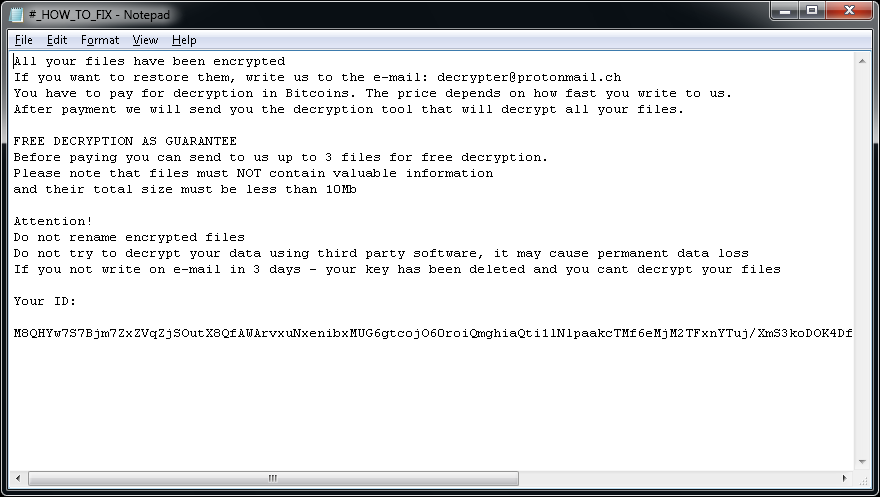
Crypt888
Crypt888 (also known as Mircop) is a form of ransomware first spotted in June 2016. Here are the signs of infection:
Crypt888 adds Lock. to the beginning of filenames. (e.g., Thesis.doc = Lock.Thesis.doc)
After encrypting your files, Crypt888 changes your desktop wallpaper to one of the following:



If Crypt888 has encrypted your files, click here to download our free fix:
CryptoMix (Offline)
CryptoMix (also known as CryptFile2 or Zeta) is a ransomware strain that was first spotted in March 2016. In early 2017, a new variant of CryptoMix, called CryptoShield emerged. Both variants encrypt files by using AES256 encryption with a unique encryption key downloaded from a remote server. However, if the server is not available or if the user is not connected to the internet, the ransomware will encrypt files with a fixed key («offline key»).
Important: The provided decryption tool only supports files encrypted using an «offline key». In cases where the offline key was not used to encrypt files, our tool will be unable to restore the files and no file modification will be done.
Update 2017-07-21: The decryptor was updated to also work with Mole variant.
Encrypted files will have one of the following extensions: .CRYPTOSHIELD, .rdmk, .lesli, .scl, .code, .rmd, .rscl or .MOLE.
The following files may be found on the PC after encrypting files:
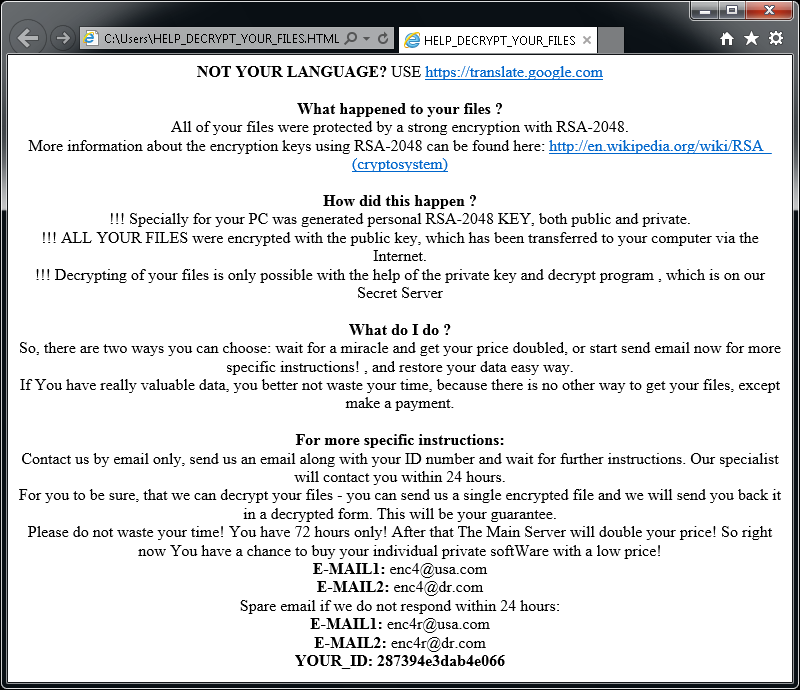
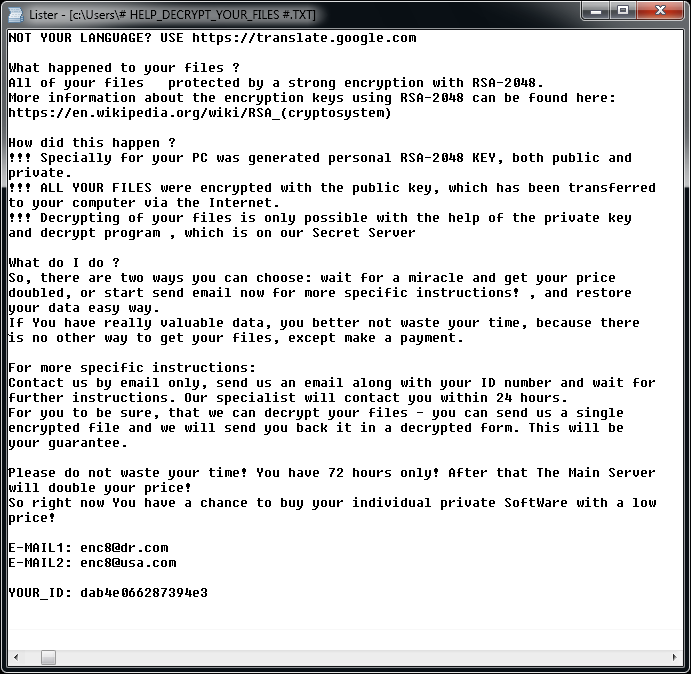
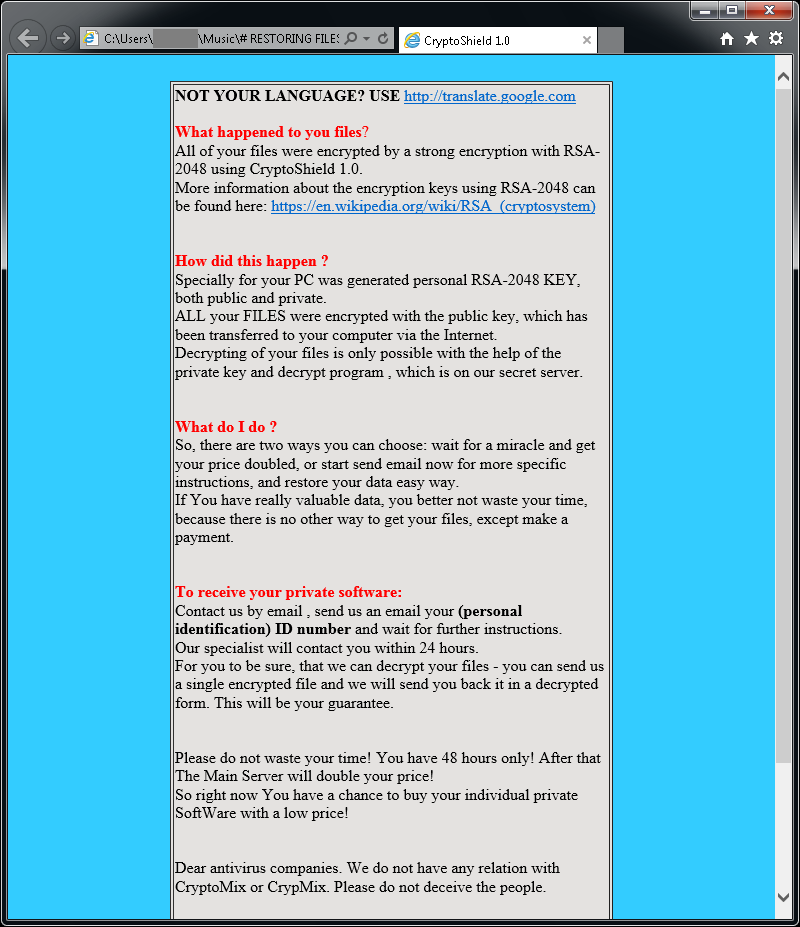
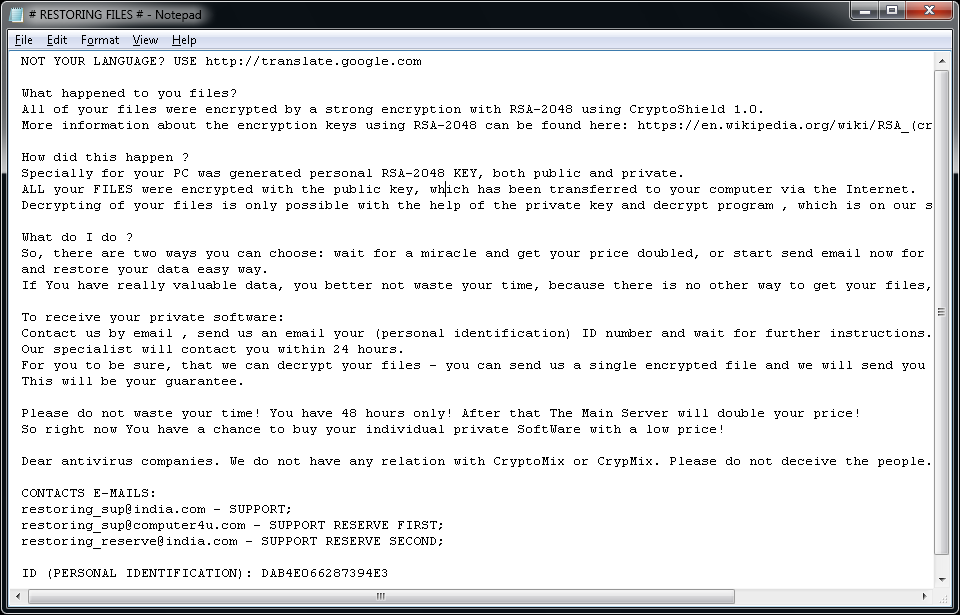
If CryptoMix has encrypted your files, click here to download our free fix:
CrySiS
CrySiS (JohnyCryptor, Virus-Encode, Aura, Dharma) is a ransomware strain that has been observed since September 2015. It uses AES-256 combined with RSA-1024 asymmetric encryption.
After encrypting your files, one of the following messages appears (see below). The message is located in «Decryption instructions.txt«, «Decryptions instructions.txt«, «README.txt«, «Readme to restore your files.txt» or «HOW TO DECRYPT YOUR DATA.txt» on the user’s desktop. Also, the desktop background is changed to one of the pictures below.

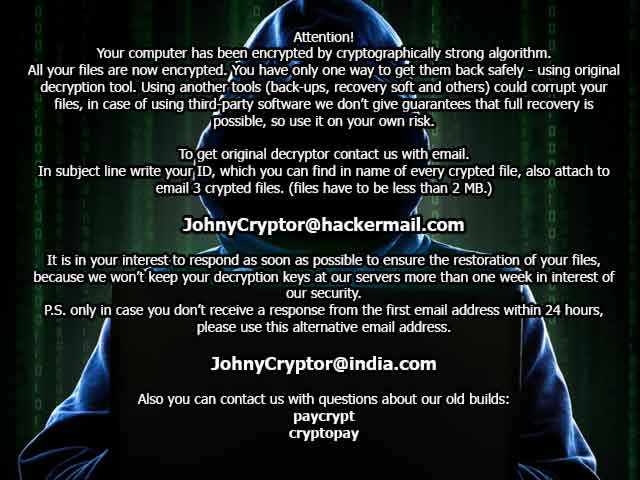



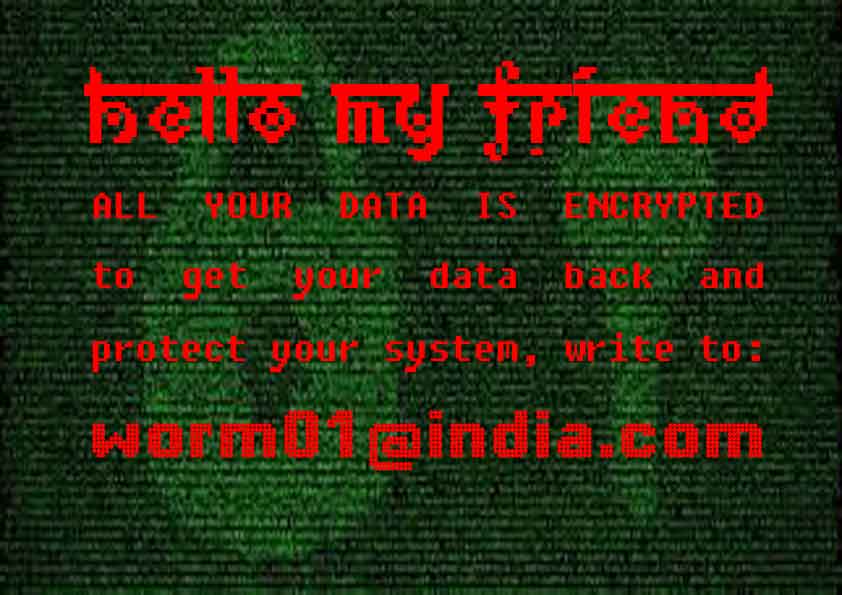

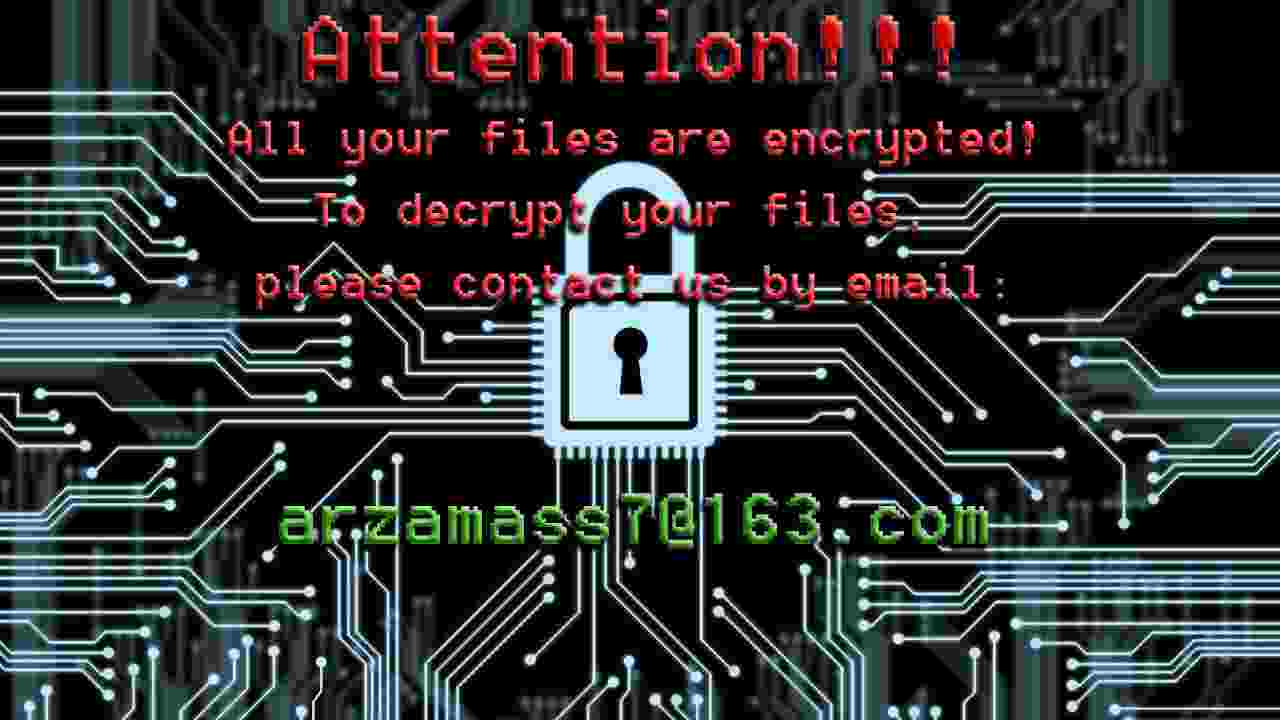

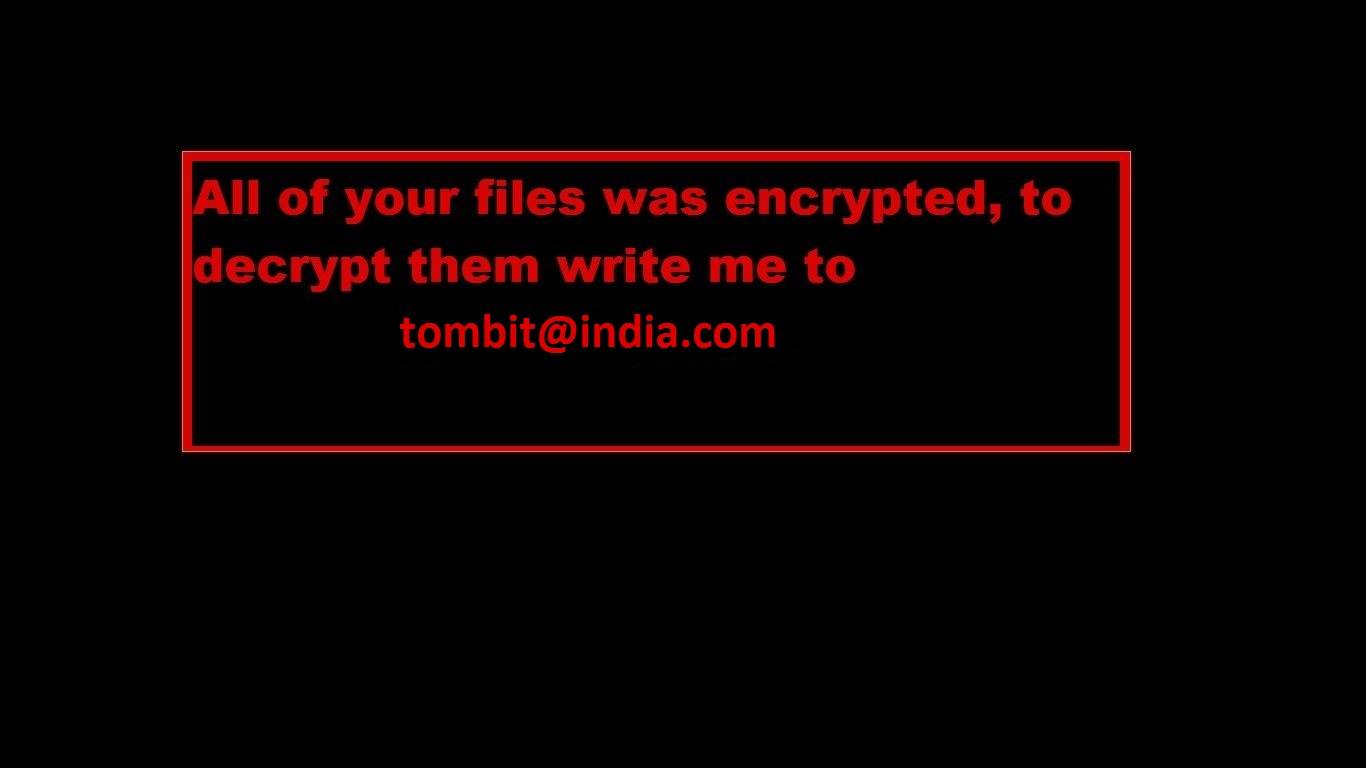
If CrySiS has encrypted your files, click here to download our free fix:
EncrypTile
EncrypTile is a ransomware that we first observed in November of 2016. After a half-year development, we caught a new, final version of this ransomware. It uses AES-128 encryption, using a key that is constant for a given PC and user.
The ransomware adds the word “encrypTile” into a file name:
The ransomware also creates four new files on user’s desktop. Names of these files are localized, here are their English versions:
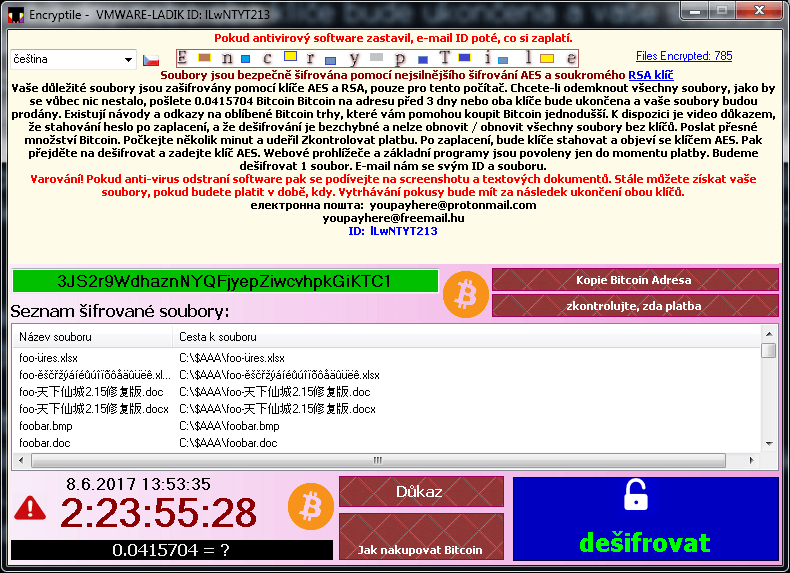
While running, the ransomware actively prevents the user from running any tools that might potentially remove it. Refer to the blog post for more detailed instructions how to run the decryptor in case the ransomware is running on your PC.
FindZip
Encrypted files will have the .crypt extension.
After encrypting your files, several files are created on the user’s desktop, with name variants of: DECRYPT.txt, HOW_TO_DECRYPT.txt, README.txt. They are all identical, containing the following text message:
Special: Because AVAST decryptors are Windows applications, it is necessary to install an emulation layer on Mac (WINE, CrossOver). For more information, please, read our blog post.
If Globe has encrypted your files, click here to download our free fix:
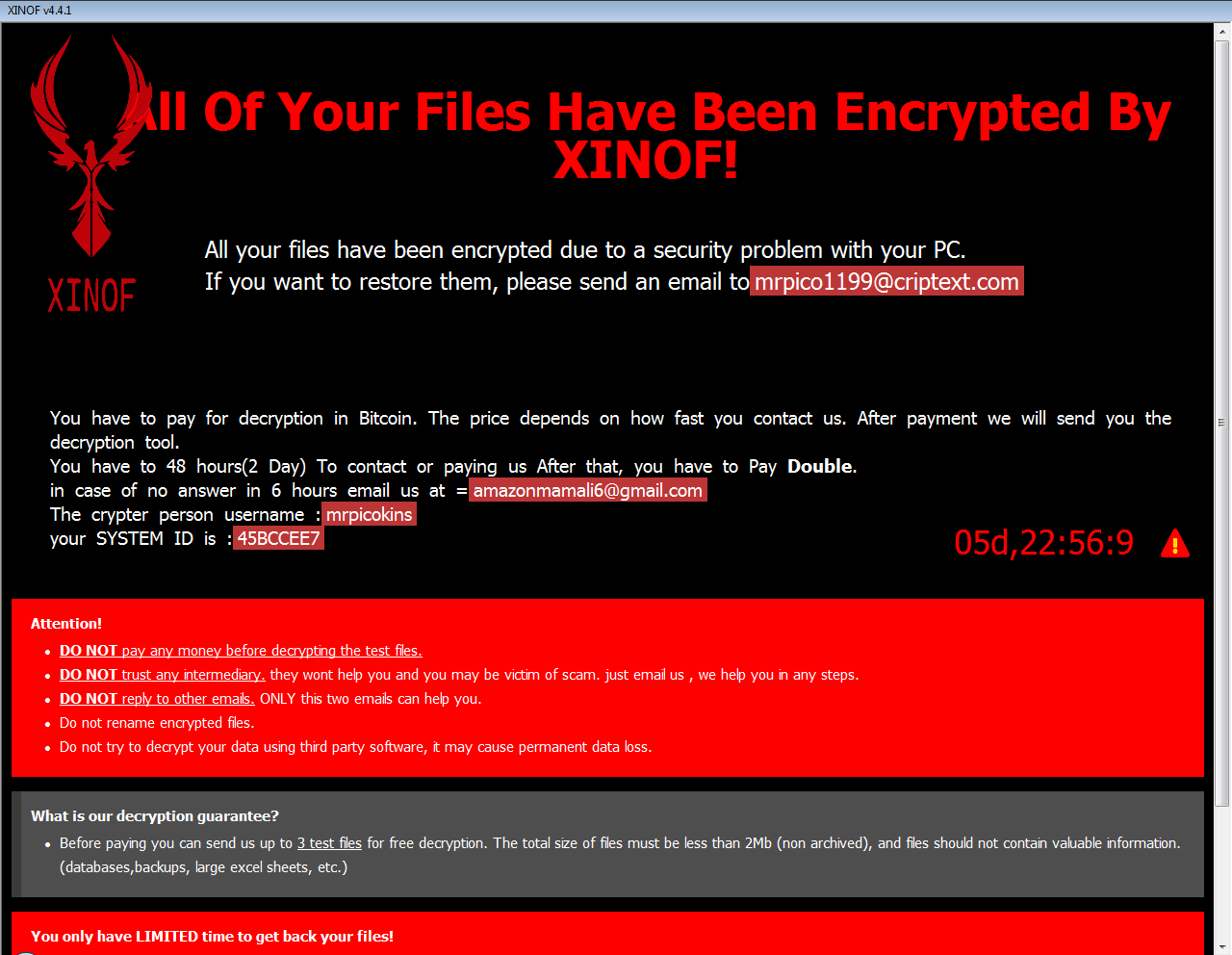
Fonix
The Fonix ransomware was active since June 2020. Written in C++, it uses three key encryption scheme (RSA-4096 master key, RSA-2048 session key, 256-bit file key for SALSA/ChaCha encryption). On February 2021, the ransomware authors shut their business down and published the master RSA key that can be used for decrypting files for free.
Encrypted files will have one of these extensions:
.FONIX,
.XINOF
After encrypting files on the victim machine, the ransomware shows the following screen:
If Fonix has encrypted your files, click here to download our free fix:
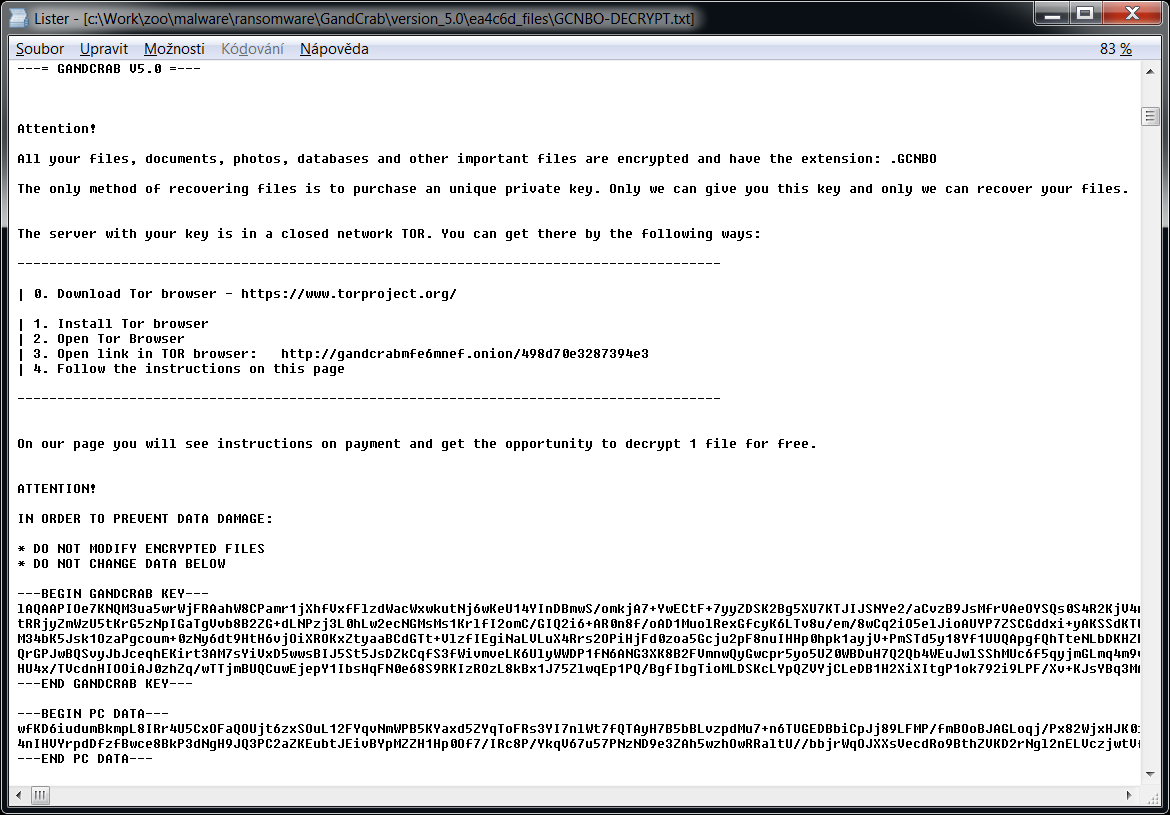
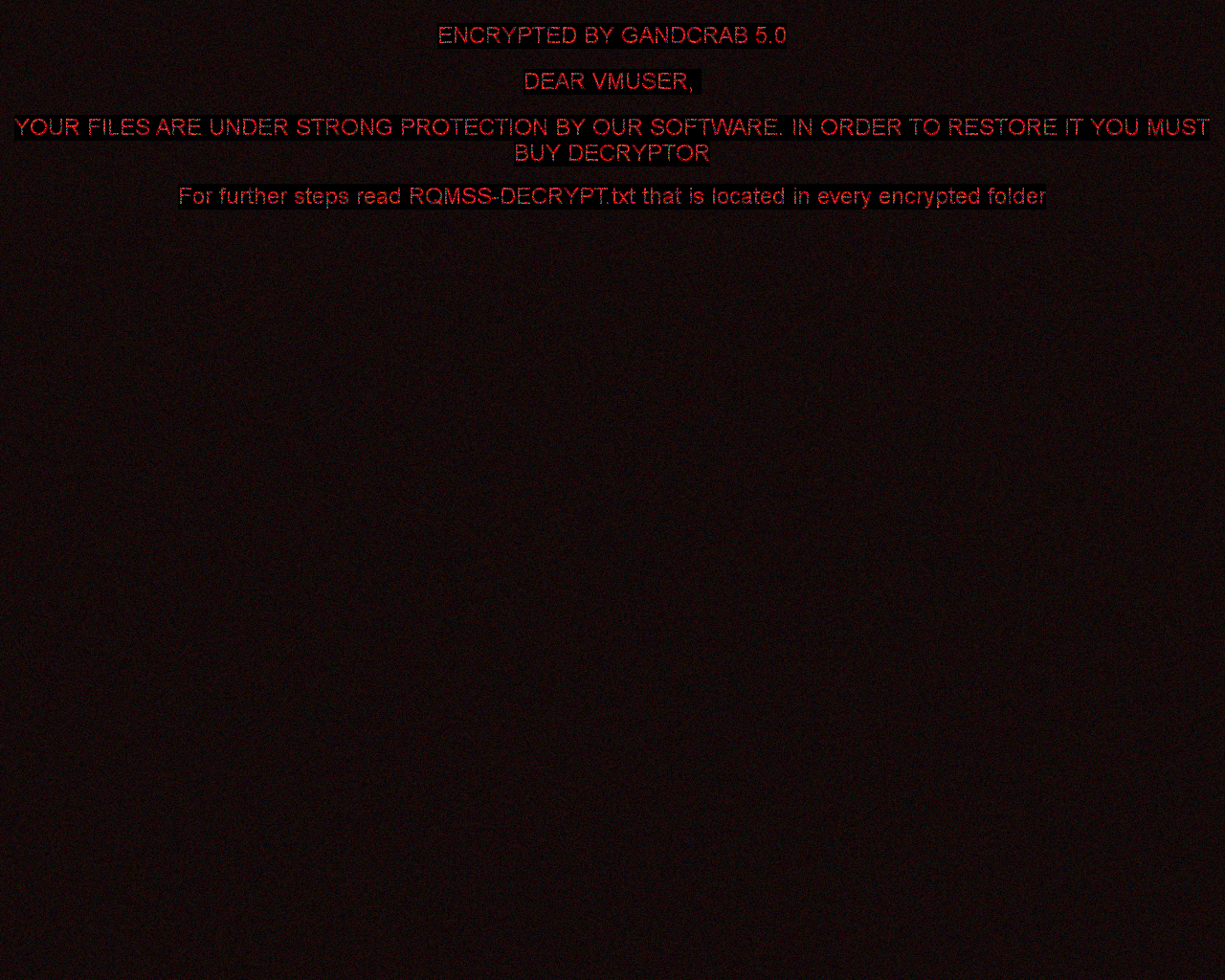
GandCrab
Gandcrab is one of the most prevalent ransomware in 2018. On 17. October 2018, Gandcrab developers released 997 keys for victims that are located in Syria. Also, in July 2018, FBI released master decryption keys for versions 4-5.2. This version of decryptor utilises all these keys and can decrypt files for free.
The ransomware also creates a text file named «GDCB-DECRYPT.txt», «CRAB-DECRYPT.txt», «KRAB_DECRYPT.txt», «%RandomLetters%-DECRYPT.txt» or «%RandomLetters%-MANUAL.txt» in each folder. The content of the file is below.
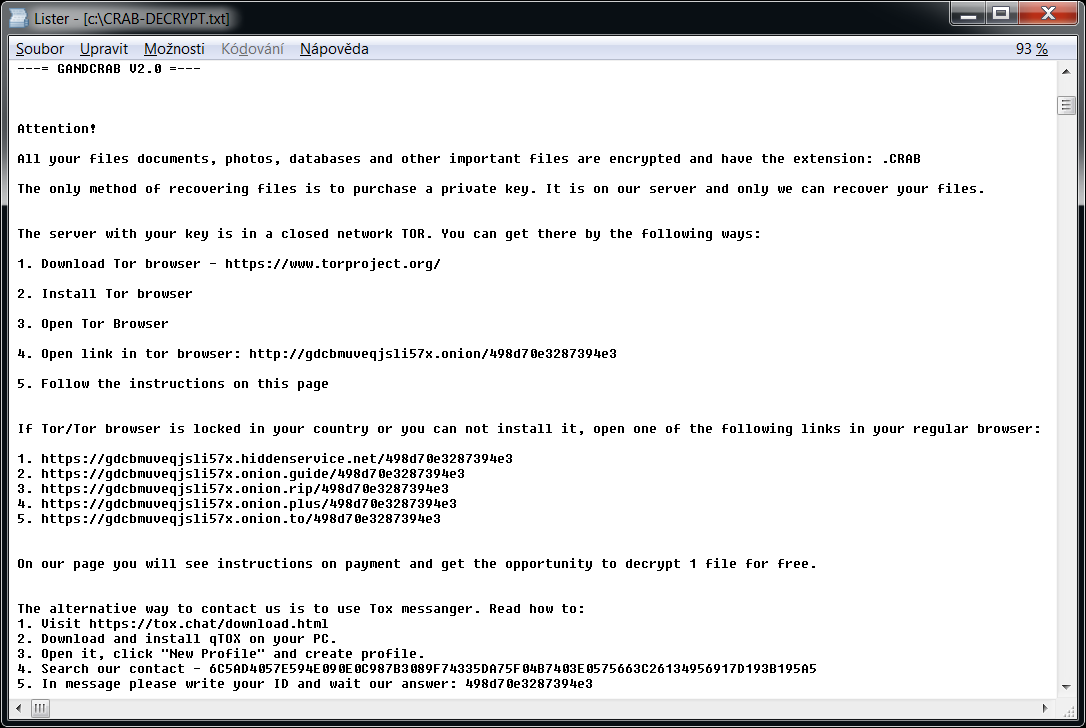
Later versions of the ransomware can also set the following image to the user’s desktop:
Globe
Globe is a ransomware strain that has been observed since August 2016. Based on variant, it uses RC4 or Blowfish encryption method. Here are signs of infection:
Globe adds one of the following extensions to the file name: «.ACRYPT«, «.GSupport4«, «.blackblock«, «.dll555«, «.duhust«, «.exploit«, «.frozen«, «.globe«, «.gsupport«, «.kyra«, «.purged«, «.raid3«, «.siri-down@india.com«, «.xtbl«, «.zendrz«, «.zendr1«, or «.hnyear«. Furthermore, some of its versions encrypt the file name as well.
After encrypting your files, a similar message appears (it is located in a file «How to restore files.hta» or «Read Me Please.hta«):
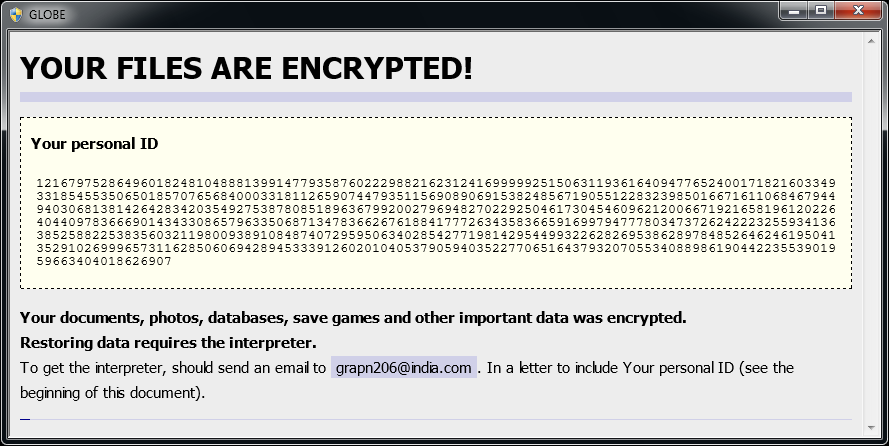
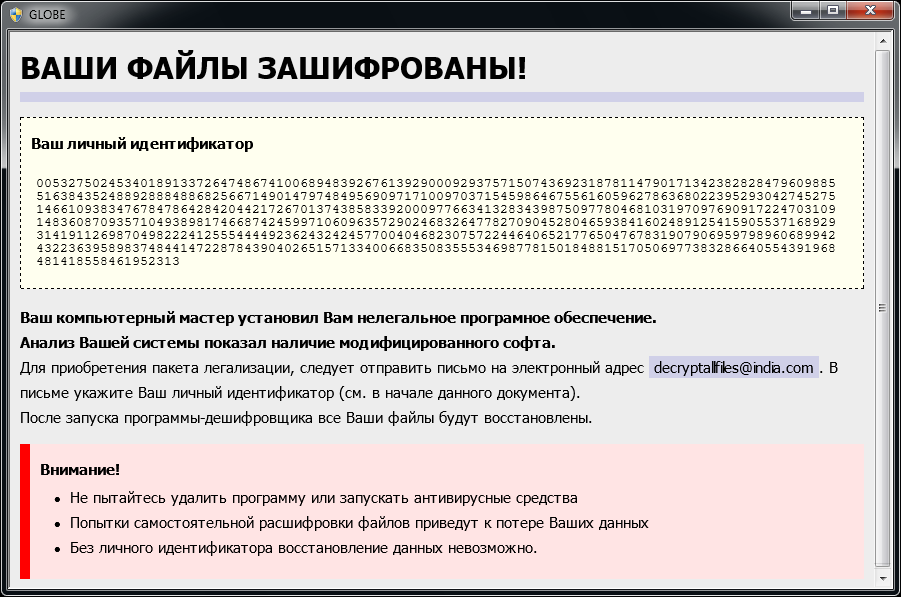
If Globe has encrypted your files, click here to download our free fix:
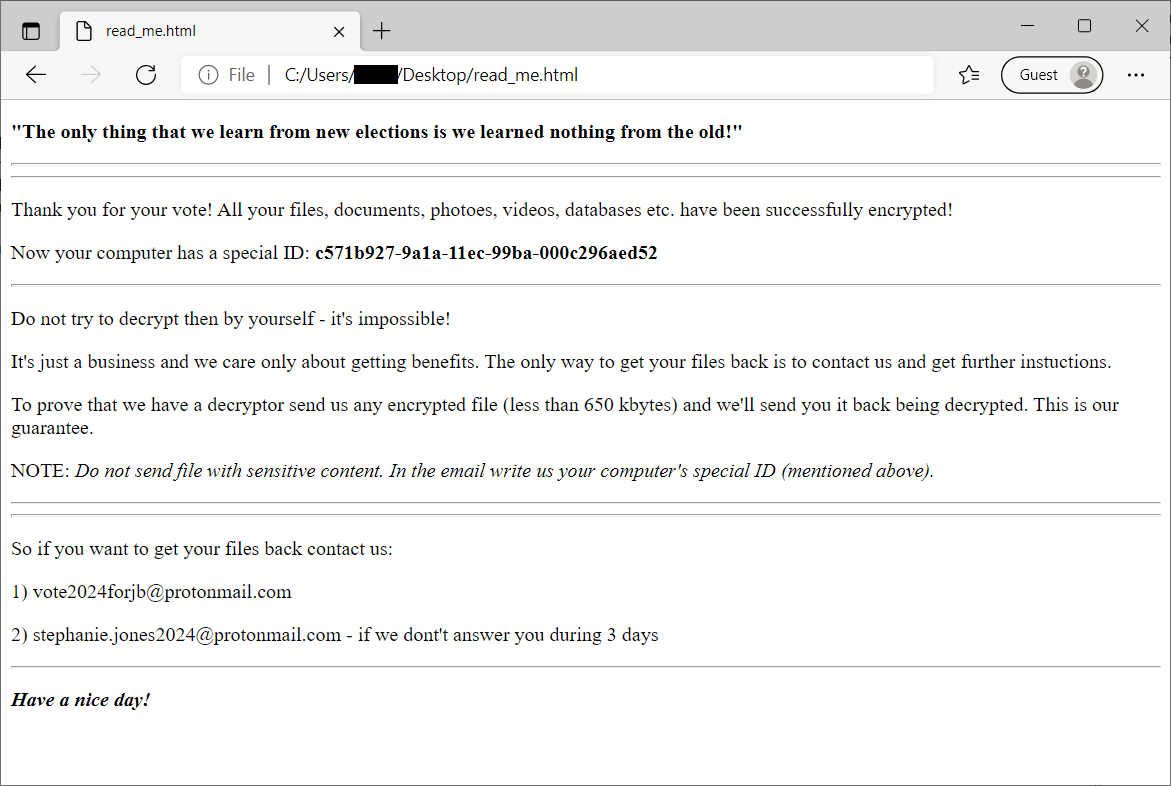
HermeticRansom
HermeticRansom is ransomware that was used at the beginning of the Russian invasion to Ukraine. It is written in Go language and encrypts files with the AES GCM symmetric cipher. Victim of this ransomware attack can decrypt their files for free.
Encrypted files can be recognized by the .[vote2024forjb@protonmail.com].encryptedJB file extension. Also, a file named read_me.html is dropped to the user’s desktop (see the image below).
HiddenTear
HiddenTear is one of the first open-sourced ransomware codes hosted on GitHub and dates back to August 2015. Since then, hundreds of HiddenTear variants have been produced by crooks using the original source code. HiddenTear uses AES encryption.
Encrypted files will have one of the following extensions (but not limited to): .locked, .34xxx, .bloccato, .BUGSECCCC, .Hollycrypt, .lock, .saeid, .unlockit, .razy, .mecpt, .monstro, .lok, .암호화됨, .8lock8, .fucked, .flyper, .kratos, .krypted, .CAZZO, .doomed.
After encrypting files, a text file (READ_IT.txt, MSG_FROM_SITULA.txt, DECRYPT_YOUR_FILES.HTML) appears on the user’s desktop. Various variants can also show a ransom message:
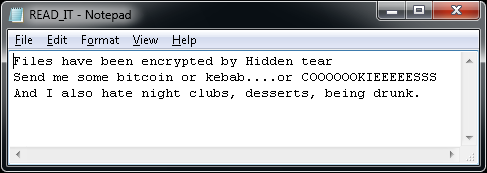


If HiddenTear has encrypted your files, click here to download our free fix:
Jigsaw
Jigsaw is a ransomware strain that has been around since March 2016. It’s named after the movie character “The Jigsaw Killer”. Several variants of this ransomware use the Jigsaw Killer’s picture in the ransom screen.
Encrypted files will have one of the following extensions: .kkk, .btc, .gws, .J, .encrypted, .porno, .payransom, .pornoransom, .epic, .xyz, .versiegelt, .encrypted, .payb, .pays, .payms, .paymds, .paymts, .paymst, .payrms, .payrmts, .paymrts, .paybtcs, .fun, .hush, .uk-dealer@sigaint.org, or .gefickt.
After encrypting your files, one of the screens below will appear:

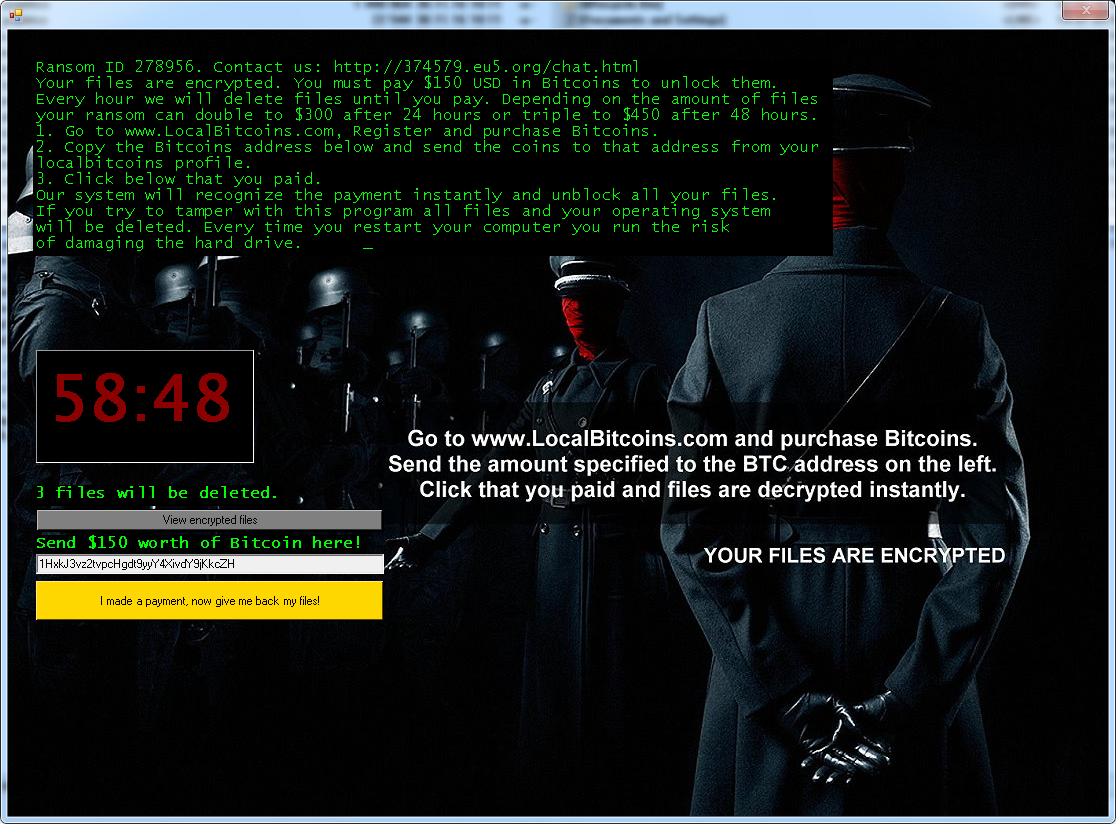

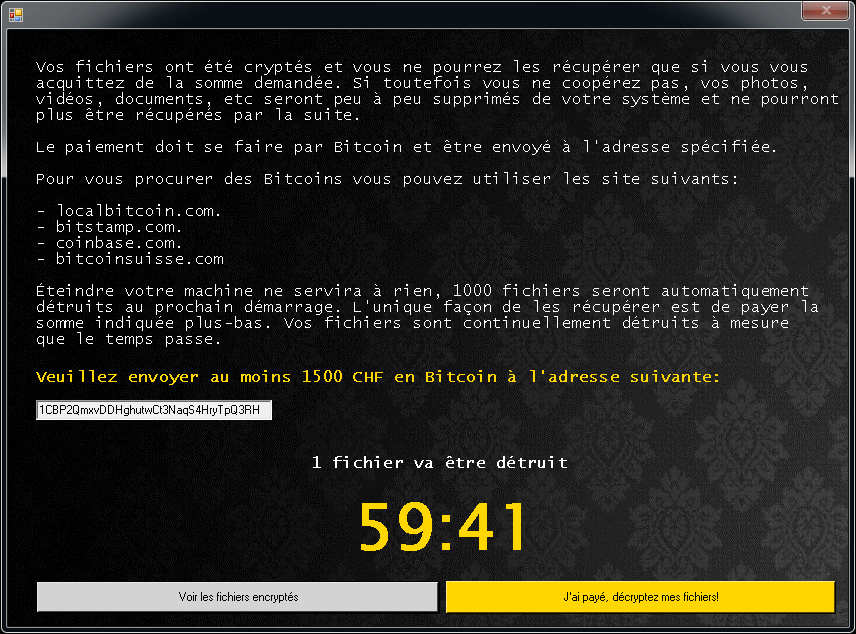
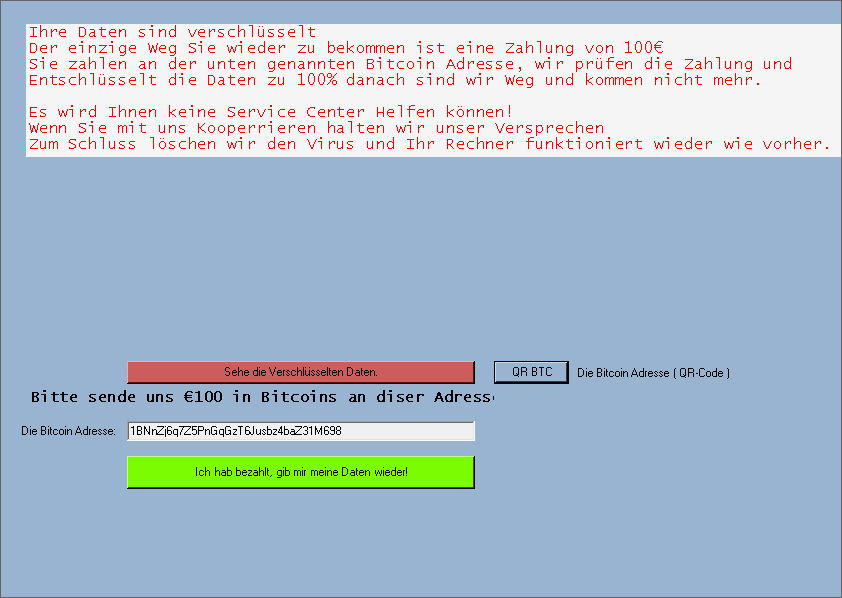
If Jigsaw has encrypted your files, click here to download our free fix:
LambdaLocker
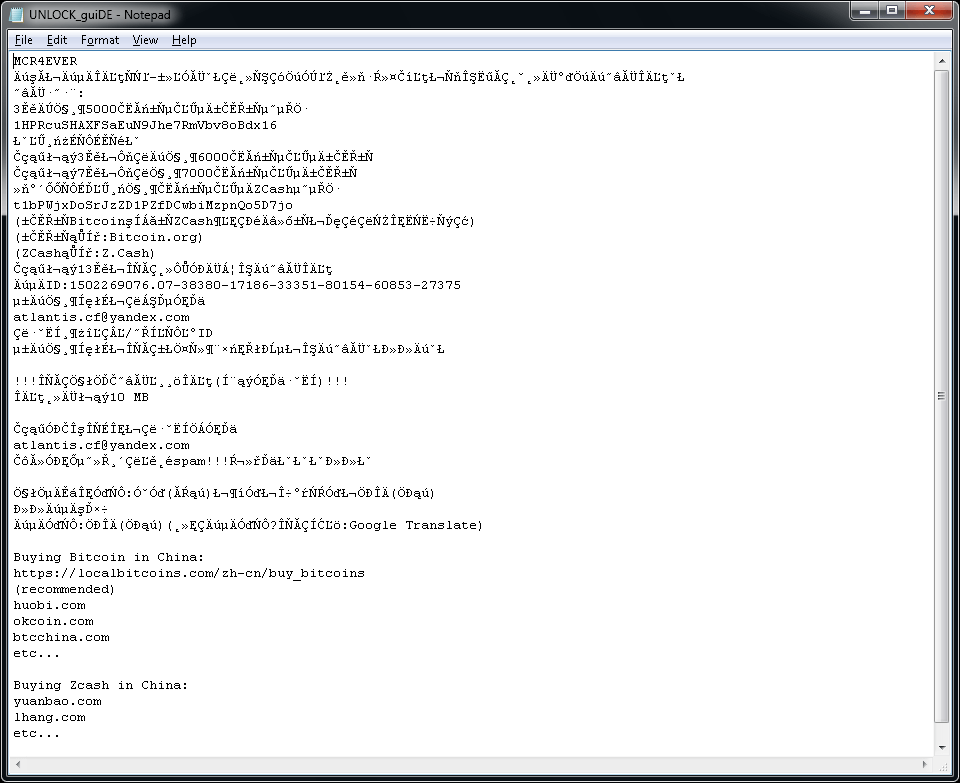
LambdaLocker is a ransomware strain that we first observed in May 2017. It is written in Python programming language and the currently prevalent variant is decryptable.
The ransomware also creates a text file named «UNLOCK_guiDE.txt» on the user’s desktop. The content of the file is below.
Legion
Legion is a form of ransomware first spotted in June 2016. Here are the signs of infection:
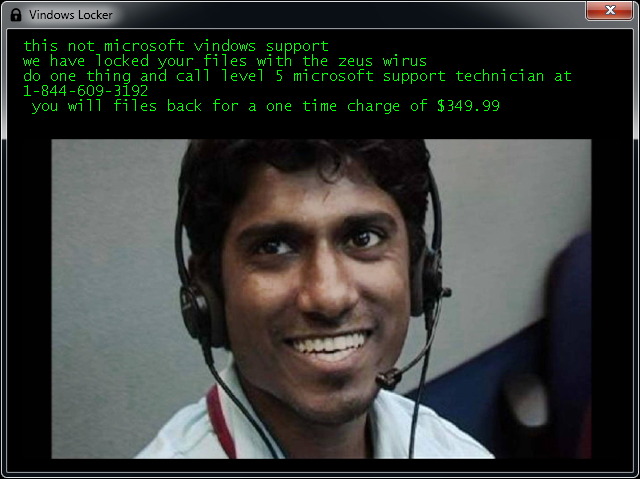
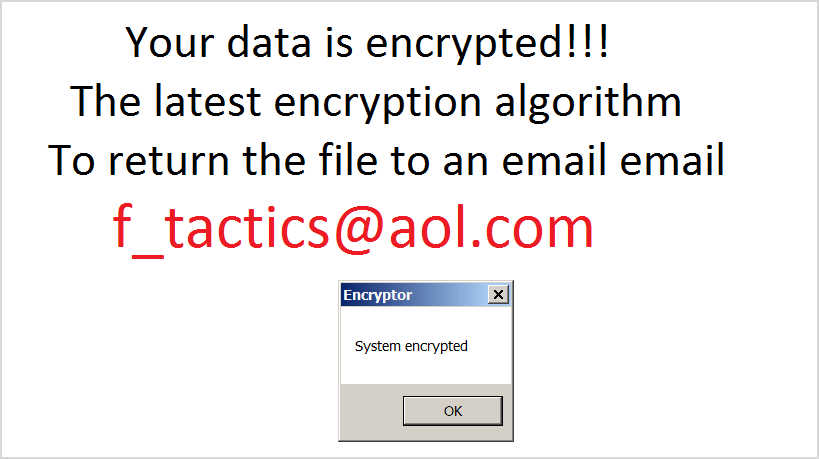
Legion adds a variant of ._23-06-2016-20-27-23_$f_tactics@aol.com$.legion or .$centurion_legion@aol.com$.cbf to the end of filenames. (e.g., Thesis.doc = Thesis.doc._23-06-2016-20-27-23_$f_tactics@aol.com$.legion)
After encrypting your files, Legion changes your desktop wallpaper and displays a popup, like this:
If Legion has encrypted your files, click here to download our free fix:
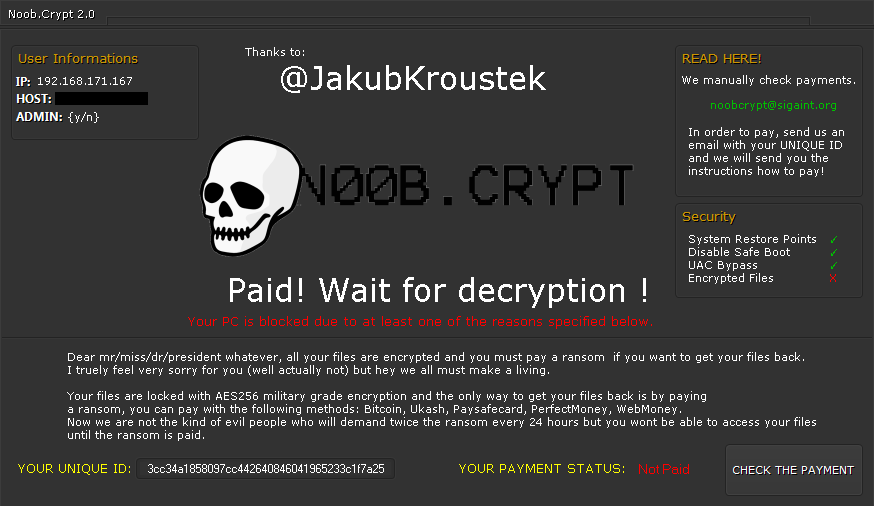
NoobCrypt
NoobCrypt is a ransomware strain that has been observed since the late July 2016. For encrypting user’s files, this ransomware uses AES 256 encryption method.
NoobCrypt doesn’t change file name. Files that are encrypted are unable to be open with their associated application, however.
After encrypting your files, a similar message appears (it is located in a file «ransomed.html» in the user’s desktop):
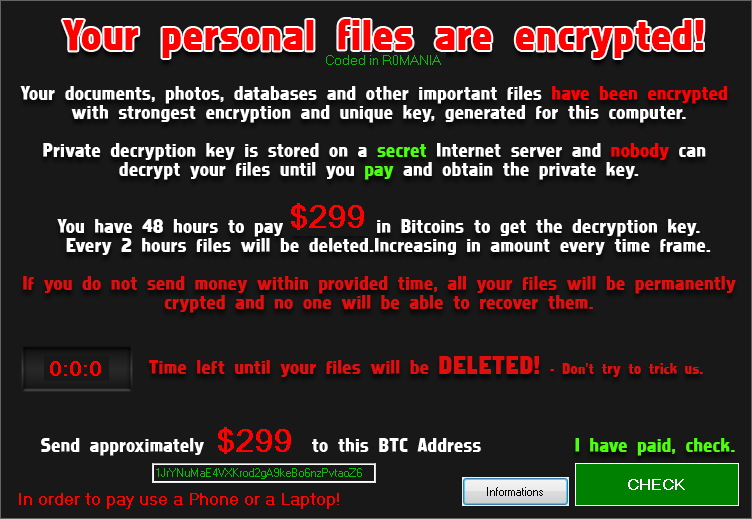
If NoobCrypt has encrypted your files, click here to download our free fix:
Prometheus
Encrypted files can be recognized by one of these file extensions:
Also, a ransom note file is dropped to the user’s desktop with one of these names:
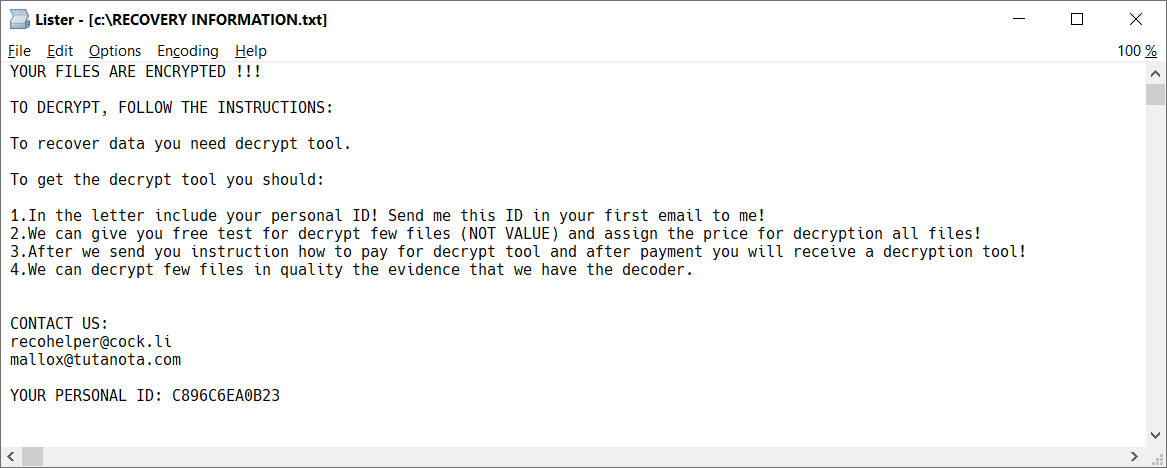
TargetCompany
TargetCompany is a ransomware that encrypts user files with Chacha20 cipher. Victim of this ransomware attack can now decrypt their files for free.
Encrypted files can be recognized by one of these extensions:
.mallox
.exploit
.architek
.brg
.carone
In each folder with at least one encrypted file, there’s also ransom note file, named RECOVERY INFORMATION.txt (see the image below).
Stampado
Stampado is a ransomware strain written using the AutoIt script tool. It has been around since August 2016. It is being sold on the dark web, and new variants keep appearing. One of its versions is also called Philadelphia.
After encryption is complete, the following screen will appear:
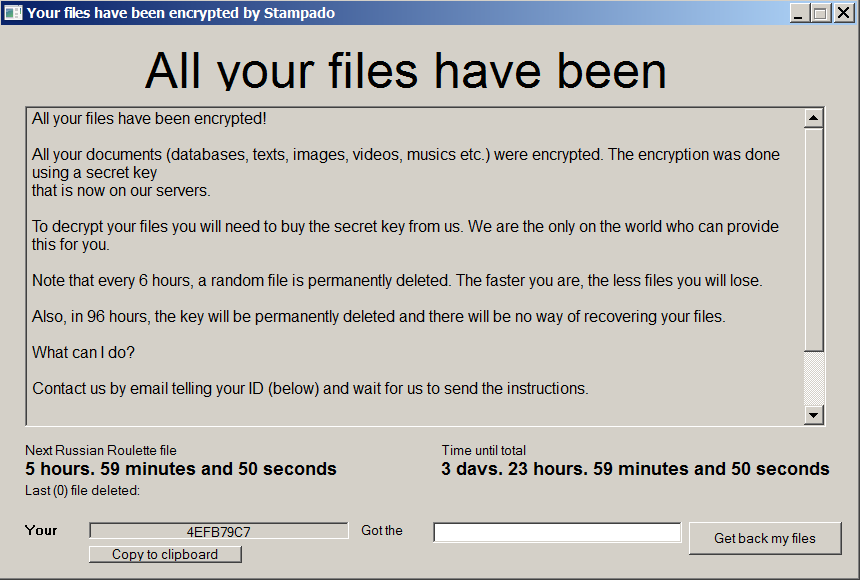
If Stampado has encrypted your files, click here to download our free fix:
SZFLocker
SZFLocker is a form of ransomware first spotted in May 2016. Here are the signs of infection:
SZFLocker adds .szf to the end of filenames. (e.g., Thesis.doc = Thesis.doc.szf)
When you try to open an encrypted file, SZFLocker displays the following message (in Polish):
If SZFLocker has encrypted your files, click here to download our free fix:
TeslaCrypt
TeslaCrypt is a form of ransomware first spotted in February 2015. Here are the signs of infection:
The latest version of TeslaCrypt does not rename your files.
After encrypting your files, TeslaCrypt displays a variant of the following message:
If TeslaCrypt has encrypted your files, click here to download our free fix:
Troldesh / Shade
Troldesh, also known as Shade or Encoder.858 is a ransomware strain that was observed since 2016. At the end of April 2020, the ransomware authors shut their business down and published decryption keys that can be used for decrypting files for free.
More information:https://www.bleepingcomputer.com/news/security/shade-ransomware-shuts-down-releases-750k-decryption-keys/
Encrypted files will have one of these extensions:
• xtbl
• ytbl
• breaking_bad
• heisenberg
• better_call_saul
• los_pollos
• da_vinci_code
• magic_software_syndicate
• windows10
• windows8
• no_more_ransom
• tyson
• crypted000007
• crypted000078
• rsa3072
• decrypt_it
• dexter
• miami_california
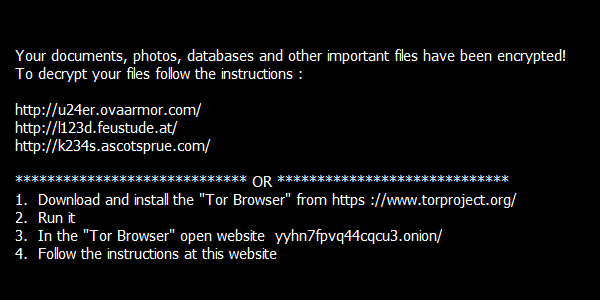
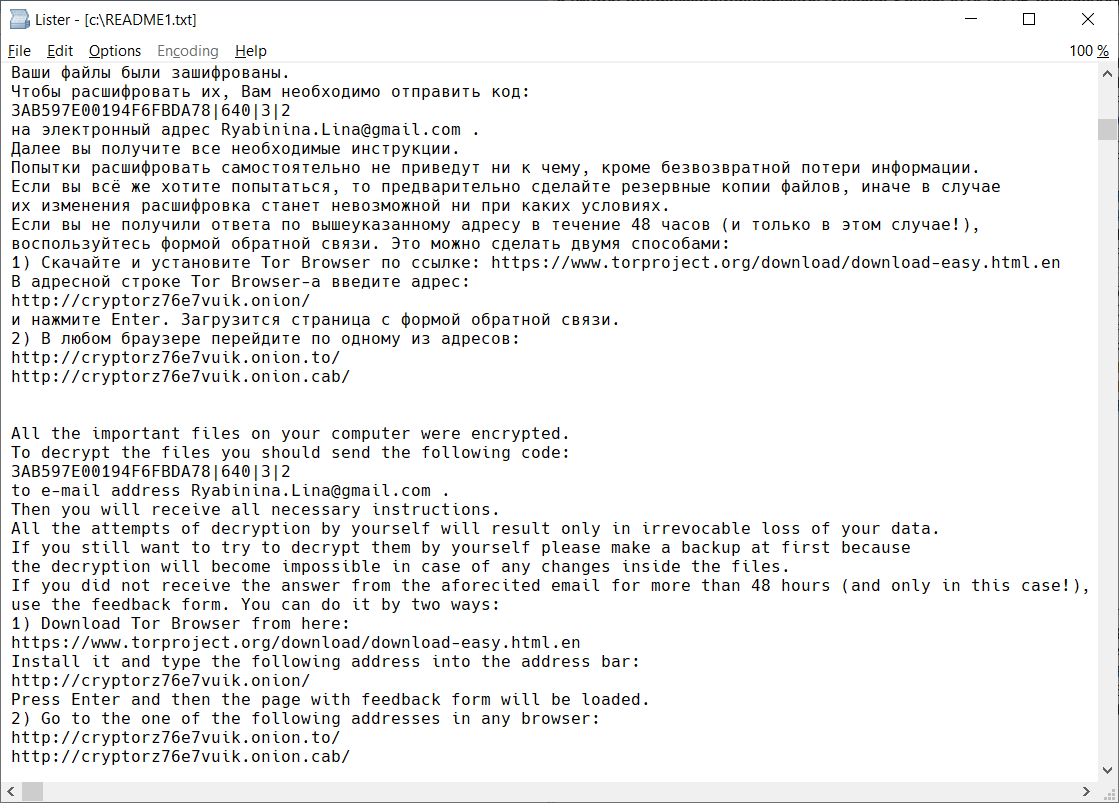
After encrypting your files, several files are created on the user’s desktop, with name of README1.txt to README10.txt. They are in different languages, containing this text:
The users’s desktop background is also changed and looks like picture below:
If Troldesh has encrypted your files, click here to download our free fix:
XData
XData is a ransomware strain that was derived from AES_NI and like WannaCry, it uses the Eternal Blue exploit to spread to other machines.
The ransomware adds the «.
» extension to the encrypted files.
In each folder with at least one encrypted file, the file «HOW_CAN_I_DECRYPT_MY_FILES.txt» can be found. Additionally, the ransomware creates a key file with name similar to:
in the following folders:
The file “HOW_CAN_I_DECRYPT_MY_FILES.txt” contains the following ransom note:
If Troldesh has encrypted your files, click here to download our free fix:
List of available regions
Main regions
Free Ransomware Decryption Tools
Hit by ransomware? Don’t pay the ransom!
Choose ransomware type
Our free ransomware decryption tools can help decrypt files encrypted by the following forms of ransomware. Just click a name to see the signs of infection and get our free fix.
AES_NI
AES_NI is a ransomware strain that first appeared in December 2016. Since then, we’ve observed multiple variants, with different file extensions. For encrypting files, the ransomware uses AES-256 combined with RSA-2048.
The ransomware adds one of the following extensions to encrypted files:
.aes_ni
.aes256
.aes_ni_0day
Alcatraz Locker
Alcatraz Locker is a ransomware strain that was first observed in the middle of November 2016. For encrypting user’s files, this ransomware uses AES 256 encryption combined with Base64 encoding.
Encrypted files have the «.Alcatraz» extension.
After encrypting your files, a similar message appears (it is located in a file «ransomed.html» in the user’s desktop):
If Alcatraz Locker has encrypted your files, click here to download our free fix:
Apocalypse
Apocalypse is a form of ransomware first spotted in June 2016. Here are the signs of infection:
Apocalypse adds .encrypted, .FuckYourData, .locked, .Encryptedfile, or .SecureCrypted to the end of filenames. (e.g., Thesis.doc = Thesis.doc.locked)
Opening a file with the extension .How_To_Decrypt.txt, .README.Txt, .Contact_Here_To_Recover_Your_Files.txt, .How_to_Recover_Data.txt, or .Where_my_files.txt (e.g., Thesis.doc.How_To_Decrypt.txt) will display a variant of this message:
AtomSilo & LockFile
AtomSilo&LockFile are two ransomware strains analyzed by Jiří Vinopal. These two have very similar encryption schema, so this decryptor covers both variants. Victims can decrypt their files for free.
Encrypted files can be recognized by one of these extensions:
.ATOMSILO
.lockfile

Babuk
Babuk is a Russian ransomware. In September 2021, the source code leaked with some of the decryption keys. Victims can decrypt their files for free.
When encrypting file, Babuk appends one of the following extensions to the file name:
.babuk
.babyk
.doydo
In each folder with at least one encrypted file, the file Help Restore Your Files.txt can be found with the following content:
BadBlock
BadBlock is a form of ransomware first spotted in May 2016. Here are the signs of infection:
BadBlock does not rename your files.
After encrypting your files, BadBlock displays one of these messages (from a file named Help Decrypt.html):

If BadBlock has encrypted your files, click here to download our free fix:
Bart is a form of ransomware first spotted at the end of June 2016. Here are the signs of infection:
Bart adds .bart.zip to the end of filenames. (e.g., Thesis.doc = Thesis.docx.bart.zip) These are encrypted ZIP archives containing the original files.
After encrypting your files, Bart changes your desktop wallpaper to an image like the one below. The text on this image can also be used to help identify Bart, and is stored on the desktop in files named recover.bmp and recover.txt.
If Bart has encrypted your files, click here to download our free fix:
Acknowledgement: We’d like to thank Peter Conrad, author of PkCrack, who granted us permission to use his library in our Bart decryption tool.
BigBobRoss
BigBobRoss encrypts user’s files using AES128 encryption. The encrypted files have new extension «.obfuscated» appended at the end of the file name.
The ransomware adds the following extension: .obfuscated
The ransomware also creates a text file named «Read Me.txt» in each folder. The content of the file is below.
BTCWare
BTCWare is a ransomware strain that first appeared in March 2017. Since then, we observed five variants, that can be distinguished by encrypted file extension. The ransomware uses two different encryption methods – RC4 and AES 192.
Encrypted file names will have the following format:
foobar.docx.[sql772@aol.com].theva
foobar.docx.[no.xop@protonmail.ch].cryptobyte
foobar.bmp.[no.btc@protonmail.ch].cryptowin
foobar.bmp.[no.btcw@protonmail.ch].btcware
foobar.docx.onyon
After encrypting your files, the desktop wallpaper is changed to the following:
You may also see one of the following ransom notes:

Crypt888
Crypt888 (also known as Mircop) is a form of ransomware first spotted in June 2016. Here are the signs of infection:
Crypt888 adds Lock. to the beginning of filenames. (e.g., Thesis.doc = Lock.Thesis.doc)
After encrypting your files, Crypt888 changes your desktop wallpaper to one of the following:






If Crypt888 has encrypted your files, click here to download our free fix:
CryptoMix (Offline)
CryptoMix (also known as CryptFile2 or Zeta) is a ransomware strain that was first spotted in March 2016. In early 2017, a new variant of CryptoMix, called CryptoShield emerged. Both variants encrypt files by using AES256 encryption with a unique encryption key downloaded from a remote server. However, if the server is not available or if the user is not connected to the internet, the ransomware will encrypt files with a fixed key («offline key»).
Important: The provided decryption tool only supports files encrypted using an «offline key». In cases where the offline key was not used to encrypt files, our tool will be unable to restore the files and no file modification will be done.
Update 2017-07-21: The decryptor was updated to also work with Mole variant.
Encrypted files will have one of the following extensions: .CRYPTOSHIELD, .rdmk, .lesli, .scl, .code, .rmd, .rscl or .MOLE.
The following files may be found on the PC after encrypting files:




If CryptoMix has encrypted your files, click here to download our free fix:
CrySiS
CrySiS (JohnyCryptor, Virus-Encode, Aura, Dharma) is a ransomware strain that has been observed since September 2015. It uses AES-256 combined with RSA-1024 asymmetric encryption.
After encrypting your files, one of the following messages appears (see below). The message is located in «Decryption instructions.txt«, «Decryptions instructions.txt«, «README.txt«, «Readme to restore your files.txt» or «HOW TO DECRYPT YOUR DATA.txt» on the user’s desktop. Also, the desktop background is changed to one of the pictures below.










If CrySiS has encrypted your files, click here to download our free fix:
EncrypTile
EncrypTile is a ransomware that we first observed in November of 2016. After a half-year development, we caught a new, final version of this ransomware. It uses AES-128 encryption, using a key that is constant for a given PC and user.
The ransomware adds the word “encrypTile” into a file name:
The ransomware also creates four new files on user’s desktop. Names of these files are localized, here are their English versions:

While running, the ransomware actively prevents the user from running any tools that might potentially remove it. Refer to the blog post for more detailed instructions how to run the decryptor in case the ransomware is running on your PC.
FindZip
Encrypted files will have the .crypt extension.
After encrypting your files, several files are created on the user’s desktop, with name variants of: DECRYPT.txt, HOW_TO_DECRYPT.txt, README.txt. They are all identical, containing the following text message:
Special: Because AVAST decryptors are Windows applications, it is necessary to install an emulation layer on Mac (WINE, CrossOver). For more information, please, read our blog post.
If Globe has encrypted your files, click here to download our free fix:
Fonix
The Fonix ransomware was active since June 2020. Written in C++, it uses three key encryption scheme (RSA-4096 master key, RSA-2048 session key, 256-bit file key for SALSA/ChaCha encryption). On February 2021, the ransomware authors shut their business down and published the master RSA key that can be used for decrypting files for free.
Encrypted files will have one of these extensions:
.FONIX,
.XINOF
After encrypting files on the victim machine, the ransomware shows the following screen:
If Fonix has encrypted your files, click here to download our free fix:
GandCrab
Gandcrab is one of the most prevalent ransomware in 2018. On 17. October 2018, Gandcrab developers released 997 keys for victims that are located in Syria. Also, in July 2018, FBI released master decryption keys for versions 4-5.2. This version of decryptor utilises all these keys and can decrypt files for free.
The ransomware also creates a text file named «GDCB-DECRYPT.txt», «CRAB-DECRYPT.txt», «KRAB_DECRYPT.txt», «%RandomLetters%-DECRYPT.txt» or «%RandomLetters%-MANUAL.txt» in each folder. The content of the file is below.

Later versions of the ransomware can also set the following image to the user’s desktop:
Globe
Globe is a ransomware strain that has been observed since August 2016. Based on variant, it uses RC4 or Blowfish encryption method. Here are signs of infection:
Globe adds one of the following extensions to the file name: «.ACRYPT«, «.GSupport7«, «.blackblock«, «.dll555«, «.duhust«, «.exploit«, «.frozen«, «.globe«, «.gsupport«, «.kyra«, «.purged«, «.raid6«, «.siri-down@india.com«, «.xtbl«, «.zendrz«, «.zendr3«, or «.hnyear«. Furthermore, some of its versions encrypt the file name as well.
After encrypting your files, a similar message appears (it is located in a file «How to restore files.hta» or «Read Me Please.hta«):


If Globe has encrypted your files, click here to download our free fix:
HermeticRansom
HermeticRansom is ransomware that was used at the beginning of the Russian invasion to Ukraine. It is written in Go language and encrypts files with the AES GCM symmetric cipher. Victim of this ransomware attack can decrypt their files for free.
Encrypted files can be recognized by the .[vote2024forjb@protonmail.com].encryptedJB file extension. Also, a file named read_me.html is dropped to the user’s desktop (see the image below).
HiddenTear
HiddenTear is one of the first open-sourced ransomware codes hosted on GitHub and dates back to August 2015. Since then, hundreds of HiddenTear variants have been produced by crooks using the original source code. HiddenTear uses AES encryption.
Encrypted files will have one of the following extensions (but not limited to): .locked, .34xxx, .bloccato, .BUGSECCCC, .Hollycrypt, .lock, .saeid, .unlockit, .razy, .mecpt, .monstro, .lok, .암호화됨, .8lock8, .fucked, .flyper, .kratos, .krypted, .CAZZO, .doomed.
After encrypting files, a text file (READ_IT.txt, MSG_FROM_SITULA.txt, DECRYPT_YOUR_FILES.HTML) appears on the user’s desktop. Various variants can also show a ransom message:



If HiddenTear has encrypted your files, click here to download our free fix:
Jigsaw
Jigsaw is a ransomware strain that has been around since March 2016. It’s named after the movie character “The Jigsaw Killer”. Several variants of this ransomware use the Jigsaw Killer’s picture in the ransom screen.
Encrypted files will have one of the following extensions: .kkk, .btc, .gws, .J, .encrypted, .porno, .payransom, .pornoransom, .epic, .xyz, .versiegelt, .encrypted, .payb, .pays, .payms, .paymds, .paymts, .paymst, .payrms, .payrmts, .paymrts, .paybtcs, .fun, .hush, .uk-dealer@sigaint.org, or .gefickt.
After encrypting your files, one of the screens below will appear:





If Jigsaw has encrypted your files, click here to download our free fix:
LambdaLocker
LambdaLocker is a ransomware strain that we first observed in May 2017. It is written in Python programming language and the currently prevalent variant is decryptable.
The ransomware also creates a text file named «UNLOCK_guiDE.txt» on the user’s desktop. The content of the file is below.
Legion
Legion is a form of ransomware first spotted in June 2016. Here are the signs of infection:
Legion adds a variant of ._23-06-2016-20-27-23_$f_tactics@aol.com$.legion or .$centurion_legion@aol.com$.cbf to the end of filenames. (e.g., Thesis.doc = Thesis.doc._23-06-2016-20-27-23_$f_tactics@aol.com$.legion)
After encrypting your files, Legion changes your desktop wallpaper and displays a popup, like this:
If Legion has encrypted your files, click here to download our free fix:
NoobCrypt
NoobCrypt is a ransomware strain that has been observed since the late July 2016. For encrypting user’s files, this ransomware uses AES 256 encryption method.
NoobCrypt doesn’t change file name. Files that are encrypted are unable to be open with their associated application, however.
After encrypting your files, a similar message appears (it is located in a file «ransomed.html» in the user’s desktop):

If NoobCrypt has encrypted your files, click here to download our free fix:
Prometheus
Encrypted files can be recognized by one of these file extensions:
Also, a ransom note file is dropped to the user’s desktop with one of these names:
TargetCompany
TargetCompany is a ransomware that encrypts user files with Chacha20 cipher. Victim of this ransomware attack can now decrypt their files for free.
Encrypted files can be recognized by one of these extensions:
.mallox
.exploit
.architek
.brg
.carone
In each folder with at least one encrypted file, there’s also ransom note file, named RECOVERY INFORMATION.txt (see the image below).
Stampado
Stampado is a ransomware strain written using the AutoIt script tool. It has been around since August 2016. It is being sold on the dark web, and new variants keep appearing. One of its versions is also called Philadelphia.
After encryption is complete, the following screen will appear:

If Stampado has encrypted your files, click here to download our free fix:
SZFLocker
SZFLocker is a form of ransomware first spotted in May 2016. Here are the signs of infection:
SZFLocker adds .szf to the end of filenames. (e.g., Thesis.doc = Thesis.doc.szf)
When you try to open an encrypted file, SZFLocker displays the following message (in Polish):
If SZFLocker has encrypted your files, click here to download our free fix:
TeslaCrypt
TeslaCrypt is a form of ransomware first spotted in February 2015. Here are the signs of infection:
The latest version of TeslaCrypt does not rename your files.
After encrypting your files, TeslaCrypt displays a variant of the following message:
If TeslaCrypt has encrypted your files, click here to download our free fix:
Troldesh / Shade
Troldesh, also known as Shade or Encoder.858 is a ransomware strain that was observed since 2016. At the end of April 2020, the ransomware authors shut their business down and published decryption keys that can be used for decrypting files for free.
More information:https://www.bleepingcomputer.com/news/security/shade-ransomware-shuts-down-releases-750k-decryption-keys/
Encrypted files will have one of these extensions:
• xtbl
• ytbl
• breaking_bad
• heisenberg
• better_call_saul
• los_pollos
• da_vinci_code
• magic_software_syndicate
• windows10
• windows8
• no_more_ransom
• tyson
• crypted000007
• crypted000078
• rsa3072
• decrypt_it
• dexter
• miami_california
After encrypting your files, several files are created on the user’s desktop, with name of README1.txt to README10.txt. They are in different languages, containing this text:
The users’s desktop background is also changed and looks like picture below:
If Troldesh has encrypted your files, click here to download our free fix:
XData
XData is a ransomware strain that was derived from AES_NI and like WannaCry, it uses the Eternal Blue exploit to spread to other machines.
The ransomware adds the «.
» extension to the encrypted files.
In each folder with at least one encrypted file, the file «HOW_CAN_I_DECRYPT_MY_FILES.txt» can be found. Additionally, the ransomware creates a key file with name similar to:
in the following folders:
The file “HOW_CAN_I_DECRYPT_MY_FILES.txt” contains the following ransom note:
If Troldesh has encrypted your files, click here to download our free fix:
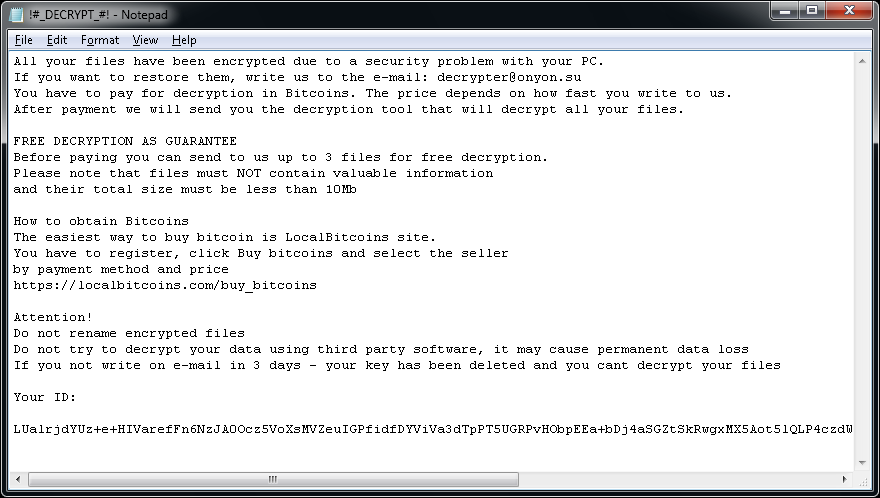
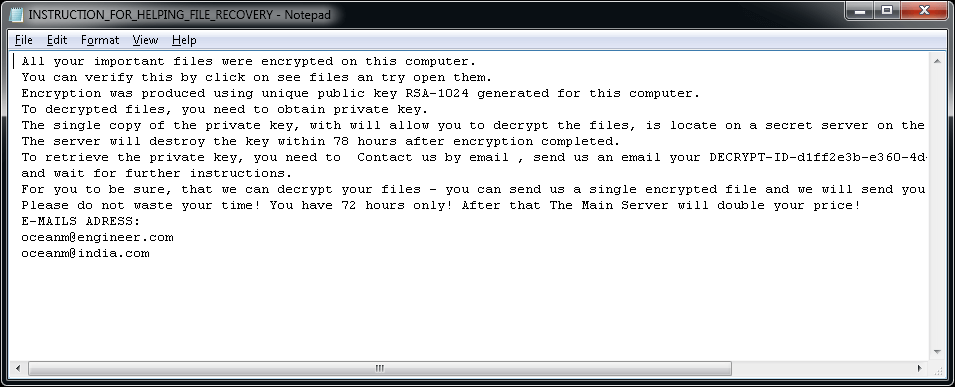
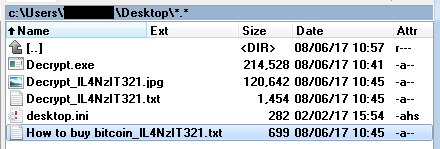
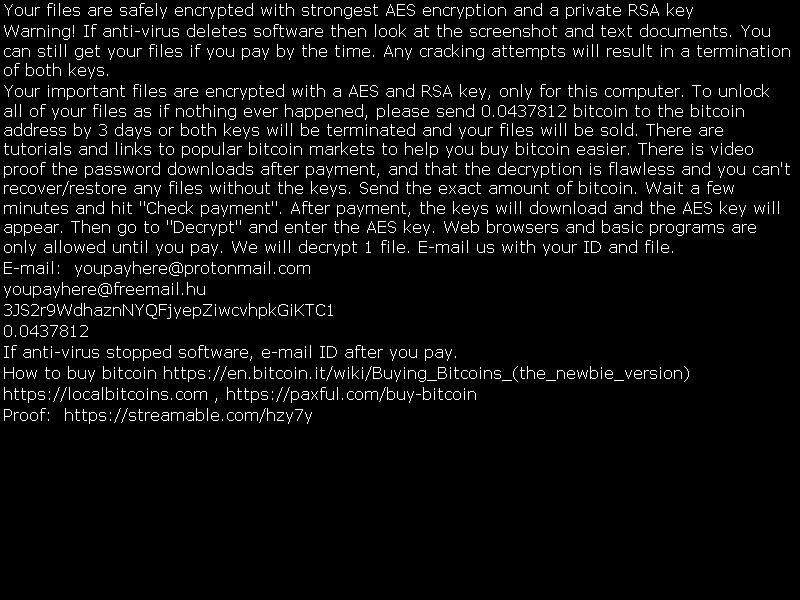
How to decrypt or get back encrypted files infected by known encrypting ransomware viruses.
In the last years, cybercriminals distribute a new type of viruses that can encrypt files on your computer (or your network) with the purpose of earning easy money from their victims. This type of viruses are called “Ransomware” and they can infect computer systems if the computer’s user doesn’t pay attention when opening attachments or links from unknown senders or sites that have been hacked by cybercriminals. According to my experience, the only safe way to keep oneself protected from this type of viruses, is to have clean backups of your files stored in a separate place from your computer. For example, in an unplugged external USB hard drive or in DVD-Rom’s.
This article contains important information of some known encrypting ransomware –crypt- viruses that were designed to encrypt critical files plus the available options & utilities in order to decrypt your encrypted files upon infection. I wrote this article in order to keep all the information for the available decrypt tools in one place and I will try to keep this article updated. Please share with us your experience and any other new information you may know in order to help each other.
How to decrypt files encrypted from Ransomware – Description & Known Decryption Tools – Methods:
Updates June 2016:
1. Trend Micro has released a Ransomware File Decryptor tool to attempt to decrypt files encrypted by the following ransomware families:
* Note: Applies to CryptXXX V3 ransomware: Due to the advanced encryption of this particular Crypto-Ransomware, only partial data decryption is currently possible on files affected by CryptXXX V3, and you have to use a thrird party repair tool to repair your files like: http://www.stellarinfo.com/file-repair/file-repair-toolkit.php
To download Trend Micro’s Ransomware File Decrypter tool (and read the instructions on how to use it), navigate to this page: Downloading and Using the Trend Micro Ransomware File Decryptor
2. Kasperky has released the following decryptor tools:
* Note: RakhniDecryptor utility is always updated to decrypt files from several ransomware families.
Rakhni
Agent.iih
Aura
Autoit
Pletor
Rotor
Lamer
Lortok
Cryptokluchen
Democry
Bitman – TeslaCrypt version 3 and 4
B. Kaspersky’s RannohDecryptor tool is designed to decrypt files affected by:
Rannoh
AutoIt
Fury
Crybola
Cryakl
CryptXXX versions 1 and 2
Cryptowalll – Virus Information & Decryption Options.
The Cryptowall (or “Cryptowall Decrypter”) virus is the new variant of Cryptodefense ransomware virus. When a computer is infected with Cryptowall ransomware, then all the critical files on the computer (including the files on mapped –network- drives if you’re logged in a network) become encrypted with strong encryption, that makes it practically impossible to decrypt them. After the Cryptowall encryption, the virus creates and sends the private key (password) to a private server in order to be used from the criminal to decrypt your files. After that, the criminals inform their victims that all their critical files are encrypted and the only way to decrypt them is to pay a ransom of 500$ (or more) in a defined time period, otherwise the ransom will be doubled or their files will be lost permanently.
How to decrypt Cryptowall infected files and get your files back:
If you want to decrypt Cryptowall encrypted files and get your files back, then you have these options:
A. The first option is to pay the ransom. If you decide to do that, then proceed with the payment at your own risk because according to our research some users get their data back and some others don’t. Keep in mind that criminals are not the most trustworthy people in the planet.
B. The second option is to clean the infected computer and then to restore your infected files from a clean backup (if you have one).
C. If you don’t have a clean backup, then the only option that remains is to restore your files in previous versions from “Shadow Copies”. Observe that this procedure works only in Windows 8, Windows 7 and Vista OS and only if the “System Restore” feature was previously enabled on your computer and was not disabled after the Cryptowall infection.
A detailed analysis of Cryptowall ransomware infection and removal can be found in this post:
CryptoDefense & How_Decrypt – Virus Information & Decryption.
Cryptodefense is another ransomware virus that can encrypt all the files on your computer regardless of their extension (file type) with strong encryption so that it makes it practically impossible to decrypt them. The virus may disable the “System Restore” feature on the infected computer and may delete all “Shadow Volume Copies” files, so you cannot restore your files to their previous versions. Upon infection Cryptodefense ransomware virus, creates two files on every infected folder (“How_Decrypt.txt” and “How_Decrypt.html”) with detailed instructions on how to pay the ransom in order to decrypt your files and sends the private key (password) to a private server in order to be used by the criminal to decrypt your files.
A detailed analysis of Cryptodefense ransomware infection and removal can be found in this post:
How to decrypt Cryptodefense encrypted files and get your files back:
In order to decrypt Cryptodefense infected files you have these options:
A. The first option is to pay the ransom. If you decide to do that, then proceed with the payment at your own risk because according to our research, some users get their data back and some others don’t. Keep in mind that criminals are not the most trustworthy people in the planet.
B. The second option is to clean the infected computer and then to restore your infected files from a clean backup (if you have one).
C. If you don’t have a clean backup then you can try to restore your files in previous versions from “Shadow Copies”. Observe that this procedure works only in Windows 8, Windows 7 and Vista OS and only if the “System Restore” feature was previous enabled on your computer and was not disabled after the Cryptodefense infection.
D. Finally, if you don’t have a clean backup and you aren’t able to restore your files from “Shadow Copies”, then you can try to decrypt Cryptodefense’s encrypted files by using the Emsisoft’s Decryptor utility. To do that:
Important Notice: This utility works only for computers infected before 1st April 2014.
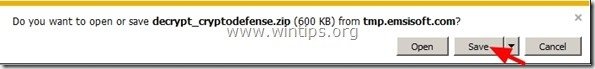
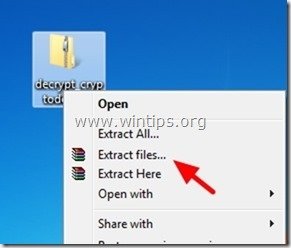
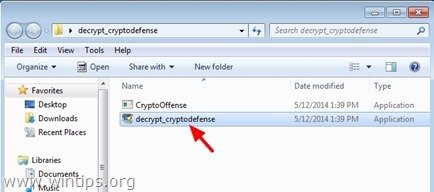
1. Download “Emsisoft Decrypter” utility to your computer (e.g. your Desktop).
2. When download is completed, navigate to your Desktop and “Extract” the “decrypt_cryptodefense.zip” file.
3. Now double-click to run the “decrypt_cryptodefense” utility.
4. Finally press the “Decrypt” button to decrypt your files.
Source – Additional information: A detailed tutorial on how to decrypt CryptoDefense encrypted files using Emsisoft’s decrypter utility can be found here: http://www.bleepingcomputer.com/virus-removal/cryptodefense-ransomware-information#emsisoft
Cryptorbit or HowDecrypt – Virus Information & Decryption.
Cryptorbit or HowDecrypt virus is an ransomware virus that can encrypt all the files on your computer. Once your computer is infected with Cryptorbit virus all your critical files are encrypted regardless of their extension (file type) with strong encryption that makes it practically impossible to decrypt them. The virus also creates two files on every infected folder on your computer (“HowDecrypt.txt” and “HowDecrypt.gif”) with detailed instructions on how you can pay the ransom and decrypt your files.
A detailed analysis of Cryptorbit ransomware infection and removal can be found in this post:
How to decrypt Cryptorbit infected files and get your files back:
In order to decrypt Cryptorbit encrypted files you have these options:
A. The first option is to pay the ransom. If you decide to do that, then proceed with the payment at your own risk because according to our research some users get their data back and some others don’t.
B. The second option is to clean the infected computer and then to restore your infected files from a clean backup (if you have one).
C. If you don’t have a clean backup, then you can try to restore your files in previous versions from “Shadow Copies”. Observe that this procedure works only in Windows 8, Windows 7 and Vista OS and only if the “System Restore” feature was previous enabled on your computer and was not disabled after the Cryptorbit infection.
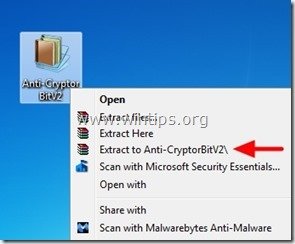
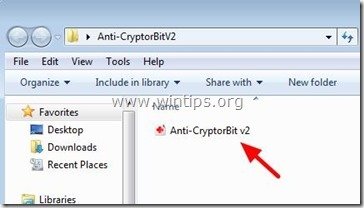
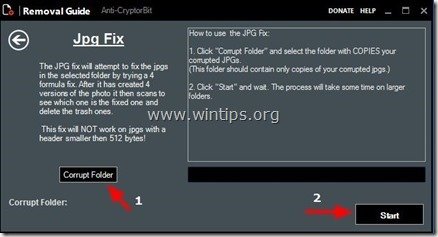
D. Finally, if you don’t have a clean backup and you aren’t able to restore your files from “Shadow Copies” then you can try to decrypt Cryptorbit’s encrypted files by using the Anti-CryptorBit utility. To do that:
1. Download “Anti-CryptorBit” utility to your computer (e.g. your Desktop)
2. When download is completed, navigate to your Desktop and “Extract” the “Anti-CryptorBitV2.zip” file.
3. Now double-click to run the Anti-CryptorBitv2 utility.
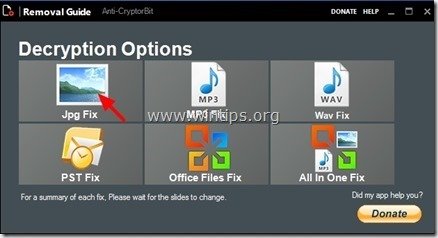
4. Choose what type of files you want to recover. (e.g. “JPG”)
5. Finally choose the folder that contains the corrupted/encrypted (JPG) files & then press the “Start” button to to fix them.
Cryptolocker – Virus Information & Decryption.
Cryptolocker (also known as “Troj/Ransom-ACP”, “Trojan.Ransomcrypt.F”) is a Ransomware nasty virus (TROJAN) and when it infects your computer, it encrypts all the files regardless of their extension (file type). The bad news with this virus is that, once it infects your computer, your critical files are encrypted with strong encryption and it is practically impossible to decrypt them. Once a computer is infected with Cryptolocker virus, then an information message appears on the victim’s computer demanding a payment (ransom) of 300$ (or more) in order to decrypt your files.
A detailed analysis of Cryptolocker ransomware infection and removal can be found in this post:
How to decrypt Cryptolocker infected files and get your files back:
In order to decrypt Cryptolocker infected files you have these options:
A. The first option is to pay the ransom. If you decide to do that, then proceed with the payment at your own risk because according to our research some users get their data back and some others don’t.
B. The second option is to clean the infected computer and then to restore your infected files from a clean backup (if you have one).
C. If you don’t have a clean backup, then you can try to restore your files in previous versions from “Shadow Copies”. Observe that this procedure works only in Windows 8, Windows 7 and Vista OS and only if the “System Restore” feature was previous enabled on your computer and was not disabled after the Cryptolocker infection.
In order to use this service you have to visit this site: ( the service has discontinued ) and upload one encrypted CryptoLocker file from the infected computer (Notice: upload a file that doesn’t contain sensitive and/or private information). After you do that, you have to specify an email address in order to receive your private key and a link to download the decryption tool. Finally run the downloaded CryptoLocker decryption tool (locally on your computer) and enter your private key to decrypt your CryptoLocker encrypted files.
The trojan CryptXXX encrypts the following types of files:
How to decrypt CryptXXX files.
If you are infected with CryptXXX Version 1 or Version 2, then use Kaspersky’s RannohDecryptor tool to decrypt your files.
If f you are infected with CryptXXX Version 3, then use Trend Micro’s Ransomware File Decryptor. *
Note: Due to the advanced encryption of CryptXXX V3 virus, only partial data decryption is currently possible and you have to use a thrird party repair tool to repair your files like: http://www.stellarinfo.com/file-repair/file-repair-toolkit.php
Locky ransomware encrypts your files using RSA-2048 and AES-128 encryption and after the infection all your files are renamed with a unique – 32 characters- file name with the extension «.locky» (e.g. «1E776633B7E6DFE7ACD1B1A5E9577BCE.locky«). Locky virus can infect local or network drives and during infection creates a file named «_HELP_instructions.html» on every infected folder, with instructions on how you can pay the ransom and decrypt your files using the TOR browser.
AutoLocky is another variant of Locky virus. The main difference between Locky and Autolocky is that Autolocky will not change the original name of the file during infection. (e.g. If a file is named «Document1.doc» before infection, the Autolocky renames it to «Document1.doc.locky«)
Trojan-Ransom.Win32.Rector – Virus Information & Decryption.
How to decrypt files infected with Trojan Rector and get your files back:
Advice: Copy all the infected files to a separate directory and close all open programs before proceeding to scan and decrypt the affected files.
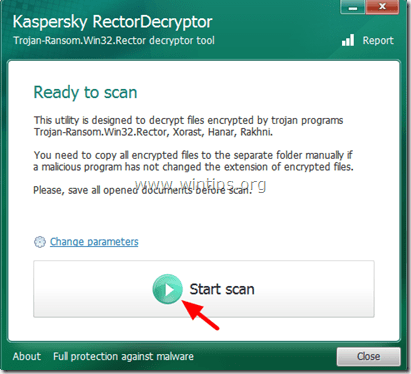
1. Download Rector Decryptor utility (from Kaspersky Labs) to your computer.
2. When the download is completed, run RectorDecryptor.exe.
3. Press the “Start Scan” button to scan your drives for the encrypted files.
* After the decryption you can find a report log of the scanning/decryption process to the root of your C:\ drive (e.g. “C:\RectorDecryptor.2.3.7.0_10.02.2011_15.31.43_log.txt”).
5. Finally continue to check and clean your system from malware programs that may exist on it.
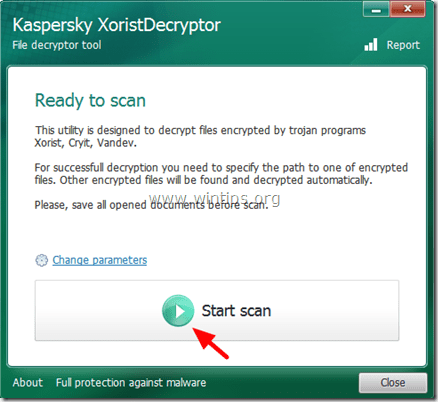
Trojan-Ransom. Win32.Xorist, Trojan-Ransom.MSIL.Vandev – Virus Information & Decryption.
The Trojan Ransom Xorist & Trojan Ransom Valdev, encrypts files with the following extensions:
doc, xls, docx, xlsx, db, mp3, waw, jpg, jpeg, txt, rtf, pdf, rar, zip, psd, msi, tif, wma, lnk, gif, bmp, ppt, pptx, docm, xlsm, pps, ppsx, ppd, tiff, eps, png, ace, djvu, xml, cdr, max, wmv, avi, wav, mp4, pdd, html, css, php, aac, ac3, amf, amr, mid, midi, mmf, mod, mp1, mpa, mpga, mpu, nrt, oga, ogg, pbf, ra, ram, raw, saf, val, wave, wow, wpk, 3g2, 3gp, 3gp2, 3mm, amx, avs, bik, bin, dir, divx, dvx, evo, flv, qtq, tch, rts, rum, rv, scn, srt, stx, svi, swf, trp, vdo, wm, wmd, wmmp, wmx, wvx, xvid, 3d, 3d4, 3df8, pbs, adi, ais, amu, arr, bmc, bmf, cag, cam, dng, ink, jif, jiff, jpc, jpf, jpw, mag, mic, mip, msp, nav, ncd, odc, odi, opf, qif, qtiq, srf, xwd, abw, act, adt, aim, ans, asc, ase, bdp, bdr, bib, boc, crd, diz, dot, dotm, dotx, dvi, dxe, mlx, err, euc, faq, fdr, fds, gthr, idx, kwd, lp2, ltr, man, mbox, msg, nfo, now, odm, oft, pwi, rng, rtx, run, ssa, text, unx, wbk, wsh, 7z, arc, ari, arj, car, cbr, cbz, gz, gzig, jgz, pak, pcv, puz, r00, r01, r02, r03, rev, sdn, sen, sfs, sfx, sh, shar, shr, sqx, tbz2, tg, tlz, vsi, wad, war, xpi, z02, z04, zap, zipx, zoo, ipa, isu, jar, js, udf, adr, ap, aro, asa, ascx, ashx, asmx, asp, aspx, asr, atom, bml, cer, cms, crt, dap, htm, moz, svr, url, wdgt, abk, bic, big, blp, bsp, cgf, chk, col, cty, dem, elf, ff, gam, grf, h3m, h4r, iwd, ldb, lgp, lvl, map, md3, mdl, mm6, mm7, mm8, nds, pbp, ppf, pwf, pxp, sad, sav, scm, scx, sdt, spr, sud, uax, umx, unr, uop, usa, usx, ut2, ut3, utc, utx, uvx, uxx, vmf, vtf, w3g, w3x, wtd, wtf, ccd, cd, cso, disk, dmg, dvd, fcd, flp, img, iso, isz, md0, md1, md2, mdf, mds, nrg, nri, vcd, vhd, snp, bkf, ade, adpb, dic, cch, ctt, dal, ddc, ddcx, dex, dif, dii, itdb, itl, kmz, lcd, lcf, mbx, mdn, odf, odp, ods, pab, pkb, pkh, pot, potx, pptm, psa, qdf, qel, rgn, rrt, rsw, rte, sdb, sdc, sds, sql, stt, t01, t03, t05, tcx, thmx, txd, txf, upoi, vmt, wks, wmdb, xl, xlc, xlr, xlsb, xltx, ltm, xlwx, mcd, cap, cc, cod, cp, cpp, cs, csi, dcp, dcu, dev, dob, dox, dpk, dpl, dpr, dsk, dsp, eql, ex, f90, fla, for, fpp, jav, java, lbi, owl, pl, plc, pli, pm, res, rnc, rsrc, so, swd, tpu, tpx, tu, tur, vc, yab, 8ba, 8bc, 8be, 8bf, 8bi8, bi8, 8bl, 8bs, 8bx, 8by, 8li, aip, amxx, ape, api, mxp, oxt, qpx, qtr, xla, xlam, xll, xlv, xpt, cfg, cwf, dbb, slt, bp2, bp3, bpl, clr, dbx, jc, potm, ppsm, prc, prt, shw, std, ver, wpl, xlm, yps, md3.
After the infection, Trojan Ransom Xorist compromises your computer’s security, makes your computer unstable and displays messages on your screen demanding a ransom in order to decrypt the infected files. The messages contain also information on how to pay the ransom in order to get the decryption utility from the cybercriminals.
How to decrypt files infected with Trojan Win32.Xorist or Trojan MSIL.Vandev:
Advice: Copy all the infected files to a separate directory and close all open programs before proceeding to scan and decrypt the affected files.
1. Download Xorist Decryptor utility (from Kaspersky Labs) to your computer.
2. When the download is completed, run XoristDecryptor.exe.
Note: If you want to delete the encrypted files when the decryption is completed, then click the “Change parameters” option and check the “Delete crypted files after decryption” check box under “Additional Options”.
3. Press the “Start Scan” button.
4. Enter the path of at least one encrypted file and then wait until the utility decrypts the encrypted files.
5. If the decryption was successful, reboot your computer and then scan and clean your system from malware programs that may exist on it.
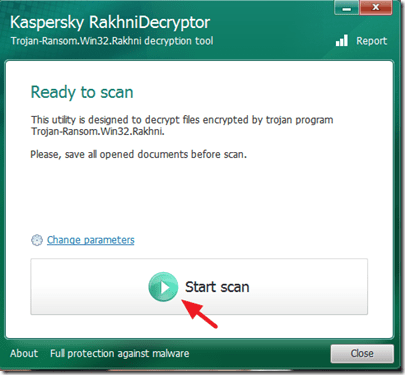
Trojan-Ransom.Win32.Rakhni – Virus Information & Decryption.
The Trojan Ransom Rakhni encrypts files by changing files extensions as follows:
After the encryption, your files are unusable and your system security is compromised. Also the Trojan-Ransom.Win32.Rakhni creates a file on your %APPDATA% folder named “exit.hhr.oshit” that contains the encrypted password for the infected files.
Warning: The Trojan-Ransom.Win32.Rakhni creates the “exit.hhr.oshit” file that contains an encrypted password to the user’s files. If this file remains on the computer, it will make decryption with the RakhniDecryptor utility faster. If the file has been removed, it can be recovered with file recovery utilities. After the file is recovered, put it into %APPDATA% and run the scan with the utility once again.
%APPDATA% folder location:
How to decrypt files infected with Trojan Rakhni and get your files back:
1. Download Rakhni Decryptor utility (from Kaspersky Labs) to your computer.
2. When the download is completed, run RakhniDecryptor.exe.
Note: If you want to delete the encrypted files when the decryption is completed, then click the “Change parameters” option and check the “Delete crypted files after decryption” check box under “Additional Options”.
3. Press the “Start Scan” button to scan your drives for encrypted files.
4. Enter the path of at least one encrypted file (e.g. “file.doc.locked”) and then wait until the utility recovers the password from the “exit.hhr.oshit” file (mind the Warning) and decrypts your files.
Trojan-Ransom.Win32.Rannoh (Trojan-Ransom.Win32.Cryakl) – Virus Information & Decryption.
The Trojan Rannoh or Trojan Cryakl encrypts all files on your computer in the following way:
How to decrypt files infected with Trojan Rannoh or Trojan Cryakl and get your files back:
Important: The Rannoh Decryptor utility decrypts files by comparing one encrypted and one decrypted file. So if you want to use the Rannoh Decryptor utility to decrypt files you must own an original copy of at least one encrypted file before the infection (e.g. from a clean backup).
1. Download Rannoh Decryptor utility to your computer.
2. When the download is completed, run RannohDecryptor.exe
Note: If you want to delete the encrypted files once the decryption is completed, then click the “Change parameters” option and check the “Delete crypted files after decryption” check box under “Additional Options”.
3. Press the “Start Scan” button.
5. After the decryption, you can find a report log of the scanning/decryption process to the root of your C:\ drive. (e.g. “C:\RannohDecryptor.1.1.0.0_02.05.2012_15.31.43_log.txt”).
How to decrypt TeslaCrypt files:
If you are infected with TeslaCrypt virus then use one of these tools to decrypt your files:
How to decrypt TeslaCrypt V3.0 files:
If you ‘re infected with TeslaCrypt 3.0 then attempt to recover your files with:
TeslaCrypt V4.0 (File name and extension are unchanged)
To decrypt TeslaCrypt V4 files, try one of the following utilities:
List of available regions
Main regions
Бесплатные дешифраторы
Стали жертвой программы-вымогателя? Не платите выкуп!
Выберите тип программы-вымогателя
Наши бесплатные дешифраторы помогут вернуть доступ к файлам, заблокированным различными видами описанного ниже ПО, требующего выкупа. Просто выберите название, чтобы просмотреть признаки заражения и получить бесплатную помощь.
AES_NI
AES_NI — это одна из программ-вымогателей, впервые появившаяся в декабре 2016 года. С тех пор было обнаружено несколько ее вариантов с разными расширениями файлов. Для шифрования файлов она использует метод AES-256 в комбинации с RSA-2048.
Эта программа-вымогатель добавляет зашифрованным файлам одно из следующих расширений:
.aes_ni
.aes256
.aes_ni_0day
Сообщение о выкупе
Alcatraz Locker
Alcatraz Locker — это одна из программ-вымогателей, впервые обнаруженная в средине ноября 2016 года. Для шифрования файлов пользователя она применяет стандарт AES 256 в сочетании с кодированием Base64.
Зашифрованные файлы получают расширение .Alcatraz.
Сообщение о выкупе
После зашифровки файлов программа отображает такое сообщение, которое находится в файле ransomed.html на рабочем столе:
Если программа Alcatraz зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
Apocalypse
Apocalypse — это вид программы-вымогателя, впервые обнаруженный в июне 2016 г. Ниже описаны признаки заражения.
Программа Apocalypse добавляет расширения .encrypted, .FuckYourData, .locked, .Encryptedfile или .SecureCrypted в конце имен файлов. (Например, вместо Thesis.doc файл будет называться Thesis.doc.locked.)
Сообщение о выкупе
При открытии файла с расширением .How_To_Decrypt.txt, .README.Txt, .Contact_Here_To_Recover_Your_Files.txt, .How_to_Recover_Data.txt или .Where_my_files.txt (например, Thesis.doc.How_To_Decrypt.txt) появится сообщение примерно следующего содержания:
AtomSilo и LockFile
AtomSilo и LockFile — это программы-вымогатели, которые были проанализированы исследователем по имени Иржи Винопал. У них похожие схемы шифрования, поэтому этот дешифратор можно использовать для обеих программ-вымогателей. Жертвы таких атак могут бесплатно расшифровать свои файлы.
Зашифрованные файлы можно узнать по одному из следующих расширений:
.ATOMSILO
.lockfile

Babuk
Babuk — российская программа-вымогатель. В сентябре 2021 года в Интернет выложили ее исходный код с несколькими ключами для расшифровки. Жертвы таких атак могут бесплатно расшифровать свои файлы.
Зашифровывая файл, Babuk добавляет к имени файла одно из следующих расширений:
.babuk;
.babyk;
.doydo.
В каждой папке, где есть хотя бы один зашифрованный файл, создается файл Help Restore Your Files.txt следующего содержания:
BadBlock
BadBlock — это вид программы-вымогателя, впервые обнаруженный в мае 2016 г. Ниже описаны признаки заражения.
Программа BadBlock не переименовывает файлы.
Сообщение о выкупе
Зашифровав ваши файлы, троянец BadBlock отображает одно из следующих сообщений (на примере файла Help Decrypt.html):

Если программа BadBlock зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
Bart — это вид программы-вымогателя, впервые обнаруженный в конце июня 2016 г. Ниже описаны признаки заражения.
Программа Bart добавляет текст .bart.zip в конце имен файлов (например, вместо Thesis.doc файл будет называться Thesis.docx.bart.zip). В этом зашифрованном ZIP-архиве содержатся исходные файлы.
Сообщение о выкупе
После зашифровки файлов программа Bart изменяет фон рабочего стола, как показано ниже. С помощью текста на этом изображении также можно распознать программу Bart. Текст хранится на рабочем столе в файлах recover.bmp и recover.txt.
Если программа Bart зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
Благодарность: благодарим Питера Конрада, автора программы PkCrack, который разрешил использовать свою библиотеку в нашем дешифраторе для троянца-вымогателя Bart.
BigBobRoss
Эта программа-вымогатель добавляет следующее расширение: .obfuscated
Сообщение о выкупе
Она также создает файл с именем Read Me.txt в каждой папке. Ниже приведено содержимое этого файла.
BTCWare
BTCWare — это одна из программ-вымогателей, впервые появившаяся в марте 2017 года. С тех пор мы обнаружили пять ее разновидностей, которые отличаются расширением зашифрованных файлов. Она использует два различных метода шифрования: RC4 и AES 192.
Имена зашифрованных файлов приобретают такой формат:
foobar.docx.[sql772@aol.com].theva
foobar.docx.[no.xop@protonmail.ch].cryptobyte
foobar.bmp.[no.btc@protonmail.ch].cryptowin
foobar.bmp.[no.btcw@protonmail.ch].btcware
foobar.docx.onyon
Сообщение о выкупе
После зашифровки файлов фон рабочего стола принимает следующий вид:
Может также отображаться одно из следующих сообщений о выкупе:

Crypt888
Crypt888 (также известна как Mircop) — это вид программы-вымогателя, впервые обнаруженный в июне 2016 г. Ниже описаны признаки заражения.
Crypt888 добавляет Lock. в начало имени файлов. Например, вместо Thesis.doc файл будет называться Lock.Thesis.doc.
Сообщение о выкупе
Зашифровав ваши файлы, программа Crypt888 меняет фон рабочего стола на один из вариантов ниже.






Если программа Crypt888 зашифровала ваши файлы, щелкните здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
CryptoMix (автономная версия)
CryptoMix (известная также как CryptFile2 и Zeta) — это одна из программ-вымогателей, впервые замеченная в марте 2016 года. В начале 2017 года появилась новая разновидность CryptoMix, получившая имя CryptoShield. Оба варианта программы шифруют файлы, применяя алгоритм AES256 с уникальным ключом шифрования, который скачивается с удаленного сервера. Если же сервер недоступен или пользователь не подключен к Интернету, программа-вымогатель шифрует файлы, используя фиксированный ключ («автономный ключ»).
Важно! Предлагаемый дешифратор способен разблокировать только файлы, зашифрованные при помощи «автономного ключа». В случаях, когда автономный ключ для шифрования файлов не использовался, наш дешифратор не сможет восстановить доступ к файлам.
Обновление от 21.07.2017: в дешифратор добавлена возможность работы с разновидностью Mole.
Зашифрованные файлы получают одно из следующих расширений: .CRYPTOSHIELD, .rdmk, .lesli, .scl, .code, .rmd, .rscl или .MOLE.
Сообщение о выкупе
После зашифровки файлов на ПК можно найти следующие файлы:




Если программа CryptoMix зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
CrySiS
CrySiS (JohnyCryptor, Virus-Encode, Aura, Dharma) — это одна из программ-вымогателей, впервые замеченная в сентябре 2015 года. В ней используется шифрование типа AES-256 в сочетании с асимметричным методом шифрования RSA-1024.
Сообщение о выкупе
Зашифровав ваши файлы, программа отображает одно из следующих сообщений. Сообщение находится в файле с именем Decryption instructions.txt, Decryptions instructions.txt, README.txt, Readme to restore your files.txt или HOW TO DECRYPT YOUR DATA.txt на рабочем столе пользователя. Кроме того, фон рабочего стола заменяется на одно из приведенных ниже изображений.










Если программа CrySiS зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
EncrypTile
EncrypTile — программа-вымогатель, впервые выявленная в ноябре 2016 года. После полугода разработки мы обнаружили ее новую, окончательную версию. В ней применяется шифрование по алгоритму AES-128 с использованием ключа, постоянного для конкретного ПК и пользователя.
Эта программа-вымогатель добавляет к имени файла слово encrypTile:
Кроме того, на рабочем столе пользователя создается четыре новых файла. Имена этих файлов локализуются, ниже приведены их английские версии:

Пока эта программа-вымогатель работает, она активно препятствует запуску любых средств, потенциально способных ее удалить. В этой публикации в блоге приведены более подробные инструкции по запуску дешифратора в случае заражения ПК этой программой.
FindZip
FindZip — это одна из программ-вымогателей, впервые обнаруженная в конце февраля 2017 года. Она распространяется на Mac OS X (10.11 и более новые версии). Принцип шифрования основан на создании ZIP-файлов: каждый зашифрованный файл представляет собой ZIP-архив, содержащий исходный документ.
Зашифрованные файлы получают расширение .crypt.
Сообщение о выкупе
После зашифровки файлов на рабочем столе пользователя создается несколько файлов, которые могут называться DECRYPT.txt, HOW_TO_DECRYPT.txt или README.txt. Они все идентичны и содержат следующее текстовое сообщение:
Особые требования: поскольку дешифраторы AVAST — это приложения для ОС Windows, на Mac необходимо установить эмулятор (WINE, CrossOver). Подробнее о том, как это сделать, читайте в нашей публикации в блоге.
Если программа Globe зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
Fonix
Программа-вымогатель Fonix активна с июня 2020 г. Она написана на языке C++ и использует три схемы шифрования ключей (RSA-4096 для основного ключа, RSA-2048 для ключа сеанса и 256-разрядный стандарт ключа файла для шифрования SALSA/ChaCha). В феврале 2021 г. создатели программы-вымогателя прекратили свою работу и опубликовали основной ключ RSA, который можно использовать для бесплатной расшифровки файлов.
Зашифрованные файлы получают одно из следующих расширений:
.FONIX
.XINOF
Сообщение о выкупе
Зашифровав файлы на устройстве жертвы, программа-вымогатель отображала следующий экран:
Если программа Fonix зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
GandCrab
GandCrab — одна из самых распространенных программ-вымогателей в 2018 году. 17 октября 2018 года разработчики Gandcrab выпустили 997 ключей для сирийских пользователей, пострадавших от этой программы. Кроме того, в июле 2018 г. ФБР выпустила основные ключи для расшифровки, подходящие для версий 4–5.2. Данная версия дешифратора использует все эти ключи и позволяет расшифровать файлы бесплатно.
Сообщение о выкупе
Она также создает текстовый файл с именем GDCB-DECRYPT.txt, CRAB-DECRYPT.txt, KRAB_DECRYPT.txt, %RandomLetters%-DECRYPT.txt или %RandomLetters%-MANUAL.txt в каждой папке. Ниже приведено содержимое этого файла.

Более поздние версии программы могут также устанавливать на рабочий стол пользователя следующее изображение:
Globe
Globe — это одна из программ-вымогателей, обнаруженная в августе 2016 года. В ней используется метод шифрования RC4 или Blowfish. Ниже описаны признаки заражения.
Программа Globe добавляет одно из следующих расширений к названию файла: .ACRYPT, .GSupport1, .blackblock, .dll555, .duhust, .exploit, .frozen, .globe, .gsupport, .kyra, .purged, .raid3, .siri-down@india.com, .xtbl, .zendrz, .zendr5 или .hnyear. Более того, некоторые версии программы зашифровывают само название файла.
Сообщение о выкупе
После зашифровки файлов программа отображает такое сообщение, которое находится в файле How to restore files.hta или Read Me Please.hta:


Если программа Globe зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
HermeticRansom
HermeticRansom — это программа-вымогатель, которая использовалась в самом начале вторжения России в Украину. Она написана на языке Go и шифрует файлы с помощью симметричного шифра AES-GCM. Пользователи, пострадавшие от ее атак, могут бесплатно расшифровать свои файлы.
Зашифрованные файлы можно распознать по расширению их имен: [vote2024forjb@protonmail.com].encryptedJB. На рабочем столе пользователя также появляется файл под названием read_me.html (см. изображение ниже).
HiddenTear
HiddenTear — одна из первых программ-вымогателей с открытым кодом, размещенная на портале GitHub и известная с августа 2015 года. С этого времени мошенниками, использующими открытый исходный код, были созданы сотни вариантов программы HiddenTear. Программа HiddenTear использует шифрование AES.
Зашифрованные файлы получают одно из следующих расширений (но могут иметь и другие): .locked, .34xxx, .bloccato, .BUGSECCCC, .Hollycrypt, .lock, .saeid, .unlockit, .razy, .mecpt, .monstro, .lok, .암호화됨, .8lock8, .fucked, .flyper, .kratos, .krypted, .CAZZO, .doomed.
Сообщение о выкупе
Когда файлы зашифрованы, на рабочем экране пользователя появляется текстовый файл (READ_IT.txt, MSG_FROM_SITULA.txt, DECRYPT_YOUR_FILES.HTML). Различные варианты могут также выводить сообщение с требованием выкупа:



Если программа HiddenTear зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
Jigsaw
Jigsaw — это одна из программ-вымогателей, существующая примерно с марта 2016 года. Она названа в честь кинозлодея по прозвищу Jigsaw Killer («Пила-убийца»). Некоторые варианты этой программы используют изображение этого персонажа на экране с требованием выкупа за разблокировку.
Зашифрованные файлы получают одно из следующих расширений: .kkk, .btc, .gws, .J, .encrypted, .porno, .payransom, .pornoransom, .epic, .xyz, .versiegelt, .encrypted, .payb, .pays, .payms, .paymds, .paymts, .paymst, .payrms, .payrmts, .paymrts, .paybtcs, .fun, .hush, .uk-dealer@sigaint.org или .gefickt.
Сообщение о выкупе
Когда файлы будут зашифрованы, отобразится один из экранов, представленных ниже:





Если программа Jigsaw зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
LambdaLocker
LambdaLocker — это одна из программ-вымогателей, впервые замеченная в мае 2017 года. Она написана на языке программирования Python. Наиболее распространенная на данный момент разновидность этой программы поддается дешифровке.
На рабочем столе пользователя также создается файл UNLOCK_guiDE.txt. Ниже приведено содержимое этого файла.
Legion
Legion — это вид программы-вымогателя, впервые обнаруженный в июне 2016 г. Ниже описаны признаки заражения.
Программа Legion добавляет нечто вроде ._23-06-2016-20-27-23_$f_tactics@aol.com$.legion или .$centurion_legion@aol.com$.cbf в конце имен файлов (Например, вместо Thesis.doc файл будет называться Thesis.doc._23-06-2016-20-27-23_$f_tactics@aol.com$.legion.)
Сообщение о выкупе
Зашифровав ваши файлы, программа Legion меняет фон рабочего стола, при этом появляется всплывающее окно, аналогичное этому:
Если программа Legion зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
NoobCrypt
NoobCrypt — это одна из программ-вымогателей, обнаруженная в конце июля 2016 года. Для шифрования файлов пользователя она применяет стандарт AES 256.
Программа NoobCrypt не меняет название файлов. Однако, зашифрованные файлы нельзя открыть программами по умолчанию.
Сообщение о выкупе
После зашифровки файлов программа отображает такое сообщение, которое находится в файле ransomed.html на рабочем столе:

Если программа NoobCrypt зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
Prometheus
Зашифрованные файлы можно узнать по одному из следующих расширений:
На рабочем столе пользователя также появляется сообщение с требованием выкупа под одним из следующих названий:
TargetCompany
TargetCompany — это программа-вымогатель, которая шифрует файлы пользователя при помощи шифра Chacha20. Пользователи, пострадавшие от ее атак, теперь могут бесплатно расшифровать свои файлы.
Зашифрованные файлы можно узнать по одному из следующих расширений:
.mallox
.exploit
.architek
.brg
.carone
В каждой папке, где есть хотя бы один зашифрованный файл, появляется также сообщение о выкупе под названием RECOVERY INFORMATION.txt (см. изображение ниже).
Stampado
Stampado — это тип программы-вымогателя, который был написан с использованием инструмента шифрования AutoIt. Эта программа существует примерно с августа 2016 года. Она была продана в сети Dark Web, новые варианты этой программы продолжают появляться. Одна из ее версий также известна под именем Philadelphia.
Сообщение о выкупе
После завершения шифрования отобразится следующий экран:

Если программа Stampado зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
SZFLocker
SZFLocker — это вид программы-вымогателя, впервые обнаруженный в мае 2016 г. Ниже описаны признаки заражения.
Программа SZFLocker добавляет .szf в конце файловых имен (например, вместо Thesis.doc файл будет называться Thesis.doc.szf).
Сообщение о выкупе
При попытке открыть зашифрованный файл программа SZFLocker отображает следующее сообщение (на польском языке):
Если программа SZFLocker зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
TeslaCrypt
TeslaCrypt — это вид программы-вымогателя, впервые обнаруженный в феврале 2015 г. Ниже описаны признаки заражения.
Последняя версия программы TeslaCrypt не переименовывает ваши файлы.
Сообщение о выкупе
Зашифровав ваши файлы, программа TeslaCrypt отображает нечто вроде следующего сообщения:
Если программа TeslaCrypt зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
Troldesh/Shade
Troldesh (известна также как Shade и Encoder.858) — это разновидность программ-вымогателей, обнаруженная в 2016 г. В конце апреля 2020 г. создатели этой вредоносной программы прекратили работу и опубликовали ключи, которые можно использовать для бесплатной дешифровки файлов.
Подробнее об этом: https://www.bleepingcomputer.com/news/security/shade-ransomware-shuts-down-releases-750k-decryption-keys/
Зашифрованные файлы получают одно из следующих расширений:
• xtbl
• ytbl
• breaking_bad
• heisenberg
• better_call_saul
• los_pollos
• da_vinci_code
• magic_software_syndicate
• windows10
• windows8
• no_more_ransom
• tyson
• crypted000007
• crypted000078
• rsa3072
• decrypt_it
• dexter
• miami_california
Сообщение о выкупе
После зашифровки файлов на рабочем столе пользователя создается несколько файлов с именем в диапазоне от README1.txt до README10.txt. В них на разных языках приведен следующий текст:
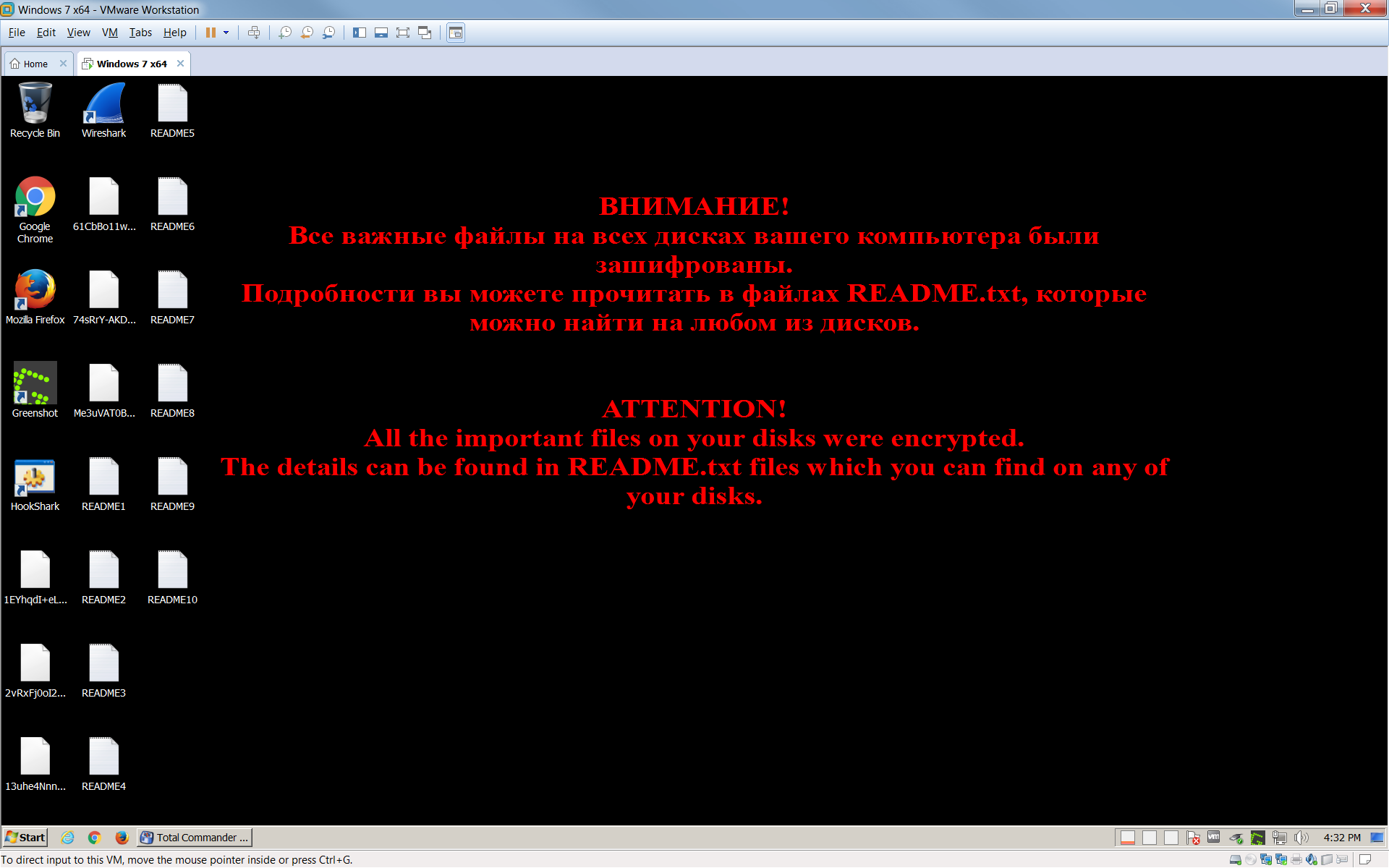
Фон рабочего стола пользователя заменяется на изображение, показанное ниже:
Если программа Troldesh зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.
XData
XData — это одна из программ-вымогателей, созданная на основе AES_NI. Как и WannaCry, она использует эксплойт Eternal Blue для распространения на другие компьютеры.
В каждой папке, где есть хотя бы один зашифрованный файл, появляется файл HOW_CAN_I_DECRYPT_MY_FILES.txt. Кроме того, программа-вымогатель создает файл ключа с именем вроде следующего:
в следующих папках:
Сообщение о выкупе
В файле HOW_CAN_I_DECRYPT_MY_FILES.txt содержится следующее сообщение о выкупе:
Если программа Troldesh зашифровала ваши файлы, нажмите здесь, чтобы скачать наш бесплатный дешифратор для разблокировки.