How to remove a computer virus
How to remove a computer virus
How to prevent and remove viruses and other malware
What is malware?
Malware is a term that is used for malicious software that is designed to do damage or unwanted actions to a computer system. Examples of malware include the following:
Rogue security software
What is a computer virus?
A computer virus is a small software program that spreads from one computer to another and interferes with computer operation. A computer virus might corrupt or delete data on a computer, use an email program to spread the virus to other computers, or even delete everything on the hard disk.
Computer viruses are frequently spread by attachments in email messages or by instant messaging messages. Therefore, you must never open an email attachment unless you know who sent the message or you are expecting the email attachment. Viruses can be disguised as attachments of funny images, greeting cards, or audio and video files. Computer viruses also spread through downloads on the Internet. They can be hidden in pirated software or in other files or programs that you might download.
Tip: For information about the symptoms of a computer virus, go to the Microsoft PC Security website.
What is a worm?
A worm is computer code that spreads without user interaction. Most worms begin as email attachments that infect a computer when they’re opened. The worm scans the infected computer for files, such as address books or temporary webpages, that contain email addresses. The worm uses the addresses to send infected email messages, and frequently mimics (or spoofs) the «From» addresses in later email messages so that those infected messages seem to be from someone you know. Worms then spread automatically through email messages, networks, or operating system vulnerabilities, frequently overwhelming those systems before the cause is known. Worms aren’t always destructive to computers, but they usually cause computer and network performance and stability problems.
What is a trojan horse?
A trojan horse is a malicious software program that hides inside other programs. It enters a computer hidden inside a legitimate program, such as a screen saver. Then it puts code into the operating system that enables a hacker to access the infected computer. Trojan horses do not usually spread by themselves. They are spread by viruses, worms, or downloaded software.
What is spyware?
Spyware can install on your computer without your knowledge. These programs can change your computer’s configuration or collect advertising data and personal information. Spyware can track Internet search habits and can also redirect your web browser to a different website than you intend to go to.
What is rogue security software?
A rogue security software program tries to make you think that your computer is infected by a virus and usually prompts you to download or buy a product that removes the virus. The names of these products frequently contain words like Antivirus, Shield, Security, Protection, or Fixer. This makes them sound legitimate. They frequently run right after you download them, or the next time that your computer starts. Rogue security software can prevent applications, such as Internet Explorer, from opening. Rogue security software might also display legitimate and important Windows files as infections. Typical error messages or pop-up messages might contain the following phrases:
Warning!
Your computer is infected!
This computer is infected by spyware and adware.
Note If you receive a message in a popup dialog box that resembles this warning, press ALT + F4 on your keyboard to close the dialog box. Do not click anything inside the dialog box. If a warning, such as the one here, keeps appearing when you try to close the dialog box, it’s a good indication that the message is malicious.
Are you sure you want to navigate from this page?
Your computer is infected! They can cause data lost and file corruption and need to be treated as soon as possible. Press CANCEL to prevent it. Return to System Security and download it to secure your PC.
Press OK to Continue or Cancel to stay on the current page.
If you see this kind of message, then don’t download or buy the software.
How to remove malware such as a virus, spyware, or rogue security software
Removing a computer virus or spyware can be difficult without the help of malicious software removal tools. Some computer viruses and other unwanted software reinstall themselves after the viruses and spyware are detected and removed. Fortunately, by updating the computer and by using malicious software removal tools, you can help permanently remove unwanted software.
To remove a computer virus and other malicious software, follow these steps in order.
1. Install the latest updates from Microsoft Update
Note A computer virus may prevent you from accessing the Microsoft Update website to install the latest updates. We recommend that you set the Automatic Updates service to run automatically so that a computer is not missing any important updates.
For more information, see Windows Update: FAQ
Click Start, and then type Windows Update in the search box.
In the results area, click Windows Update.
Click Check for Updates.
Follow the instructions to download and install the latest Windows Updates.
2. Use the free Microsoft Safety Scanner
Microsoft offers a free online tool that scans and helps remove potential threats from your computer. To perform the scan, go to the Microsoft Safety Scanner website.
3. Use the Windows Malicious Software Removal Tool
For more information about the Microsoft Malicious Software Removal Tool, see the following article in the Microsoft Knowledge Base:
4. Manually remove the rogue security software
If the rogue security software can’t be detected or removed by using Microsoft Safety Scanner or the Windows Malicious Software Removal Tool, try the following steps:
Note the name of the rogue security software. For this example, we’ll call it XP Security Agent 2010.
Restart your computer.
When you see the computer’s manufacturer’s logo, repeatedly press the F8 key.
When you are prompted, use the arrow keys to highlight Safe Mode with Networking, and then press Enter.
Click the Start button and check whether the rogue security software appears on the Start menu. If it’s not listed there, click All Programs and scroll to find the rogue security software’s name.
Right-click the name of the rogue security software program, and then click Properties.
Click the Shortcut tab.
In the Properties dialog box, check the path of the rogue security software program that is listed in Target. For example, C:\Program Files\XP Security Agent 2010.
Note The folder name frequently is a random number.
Click Open File Location.
In the Program Files window, click Program Files in the address bar.
Scroll until you find the rogue security software program folder. For example, XP Security Agent 2010.
Right-click the folder, and then click Delete.
Restart your computer.
Click the Download Now button, and then click Run.
Follow the instructions to scan your computer and help remove the rogue security software.
If you suspect that your computer is infected with rogue security software that was not detected by using Microsoft security solutions, you can submit samples by using the Microsoft Malware Protection Center submission form.
5. Run Microsoft Defender Offline
Microsoft Defender Offline is an anti-malware tool that helps remove difficult to eliminate viruses that start before Windows starts. Starting with Windows 10, Microsoft Defender Offline is built-in. To use it follow the steps in this article: Help protect my PC with Microsoft Defender Offline.
Click Download the 32 bit version or Download the 64 bit version, depending on which operating system that you are running. If you’re unsure of which operating system that you are running, see Is my PC running the 32-bit or 64-bit version of Windows.
When you are prompted, click Save As, and then save the file to a DVD, CD, or USB flash drive.
On the infected computer, insert the DVD, CD, or USB flash drive, and then restart the computer.
When you are prompted, press a key to select an option to use to start your computer, such as F12, F5, or F8, depending on the kind of computer that you are using.
Use the arrow key to scroll to the drive where you installed Microsoft Defender Offline file. Microsoft Defender Offline starts and immediately scans for malware.
How to protect your computer against malware
There are actions that you can take to help protect your computer against malware.
Turn on the firewall
Confirm that the Windows firewall is turned on. See Turn Microsoft Defender Firewall on or off for instructions on how to do that on modern versions of Windows.
Click the Start button, and then click Control Panel.
In the Search box, type firewall, and then click Windows Firewall.
In the left pane, click Turn Windows Firewall on or off (you may be prompted to enter your administrator password).
Under each network location, click Turn on Windows Firewall, and then click OK.
Keep your computer up to date
For more information about how to set Automatic Updates in Windows, see Windows Update: FAQ
Don’t be tricked into downloading malware
Here are some tips that can help protect you from downloading software that you don’t want:
Only download programs from sites that you trust. If you’re not sure whether to trust a program that you want to download, enter the name of the program into your favorite search engine to see whether anyone else has reported that it contains spyware.
Read all security warnings, license agreements, and privacy statements that are associated with any software that you download.
Never click «Agree» or «OK» to close a window that you suspect might be spyware. Instead, click the red «x» in the corner of the window or press Alt + F4 on your keyboard to close a window.
Be wary of popular «free» music and movie file-sharing programs, and make sure that you understand all the software packaged with those programs.
Use a standard user account instead of an administrator account. An administrator account can access anything on the system, and any malware run with an administrator account can use the administrator permissions to potentially infect or damage any files on the system.
For more information about how to protect a computer against viruses, see Protect my PC from viruses.
How to obtain computer virus and security-related support
For United States:
Want to chat with a live person? Our Answer Tech trained professionals are ready to help:
Security solutions for IT Professionals:
Support by country:
For locations outside North America:
For computer virus and security-related support for locations outside North America, go to the Microsoft Support website.
How to prevent and remove viruses and other malware
What is malware?
Malware is a term that is used for malicious software that is designed to do damage or unwanted actions to a computer system. Examples of malware include the following:
Rogue security software
What is a computer virus?
A computer virus is a small software program that spreads from one computer to another and interferes with computer operation. A computer virus might corrupt or delete data on a computer, use an email program to spread the virus to other computers, or even delete everything on the hard disk.
Computer viruses are frequently spread by attachments in email messages or by instant messaging messages. Therefore, you must never open an email attachment unless you know who sent the message or you are expecting the email attachment. Viruses can be disguised as attachments of funny images, greeting cards, or audio and video files. Computer viruses also spread through downloads on the Internet. They can be hidden in pirated software or in other files or programs that you might download.
Tip: For information about the symptoms of a computer virus, go to the Microsoft PC Security website.
What is a worm?
A worm is computer code that spreads without user interaction. Most worms begin as email attachments that infect a computer when they’re opened. The worm scans the infected computer for files, such as address books or temporary webpages, that contain email addresses. The worm uses the addresses to send infected email messages, and frequently mimics (or spoofs) the «From» addresses in later email messages so that those infected messages seem to be from someone you know. Worms then spread automatically through email messages, networks, or operating system vulnerabilities, frequently overwhelming those systems before the cause is known. Worms aren’t always destructive to computers, but they usually cause computer and network performance and stability problems.
What is a trojan horse?
A trojan horse is a malicious software program that hides inside other programs. It enters a computer hidden inside a legitimate program, such as a screen saver. Then it puts code into the operating system that enables a hacker to access the infected computer. Trojan horses do not usually spread by themselves. They are spread by viruses, worms, or downloaded software.
What is spyware?
Spyware can install on your computer without your knowledge. These programs can change your computer’s configuration or collect advertising data and personal information. Spyware can track Internet search habits and can also redirect your web browser to a different website than you intend to go to.
What is rogue security software?
A rogue security software program tries to make you think that your computer is infected by a virus and usually prompts you to download or buy a product that removes the virus. The names of these products frequently contain words like Antivirus, Shield, Security, Protection, or Fixer. This makes them sound legitimate. They frequently run right after you download them, or the next time that your computer starts. Rogue security software can prevent applications, such as Internet Explorer, from opening. Rogue security software might also display legitimate and important Windows files as infections. Typical error messages or pop-up messages might contain the following phrases:
Warning!
Your computer is infected!
This computer is infected by spyware and adware.
Note If you receive a message in a popup dialog box that resembles this warning, press ALT + F4 on your keyboard to close the dialog box. Do not click anything inside the dialog box. If a warning, such as the one here, keeps appearing when you try to close the dialog box, it’s a good indication that the message is malicious.
Are you sure you want to navigate from this page?
Your computer is infected! They can cause data lost and file corruption and need to be treated as soon as possible. Press CANCEL to prevent it. Return to System Security and download it to secure your PC.
Press OK to Continue or Cancel to stay on the current page.
If you see this kind of message, then don’t download or buy the software.
How to remove malware such as a virus, spyware, or rogue security software
Removing a computer virus or spyware can be difficult without the help of malicious software removal tools. Some computer viruses and other unwanted software reinstall themselves after the viruses and spyware are detected and removed. Fortunately, by updating the computer and by using malicious software removal tools, you can help permanently remove unwanted software.
To remove a computer virus and other malicious software, follow these steps in order.
1. Install the latest updates from Microsoft Update
Note A computer virus may prevent you from accessing the Microsoft Update website to install the latest updates. We recommend that you set the Automatic Updates service to run automatically so that a computer is not missing any important updates.
For more information, see Windows Update: FAQ
Click Start, and then type Windows Update in the search box.
In the results area, click Windows Update.
Click Check for Updates.
Follow the instructions to download and install the latest Windows Updates.
2. Use the free Microsoft Safety Scanner
Microsoft offers a free online tool that scans and helps remove potential threats from your computer. To perform the scan, go to the Microsoft Safety Scanner website.
3. Use the Windows Malicious Software Removal Tool
For more information about the Microsoft Malicious Software Removal Tool, see the following article in the Microsoft Knowledge Base:
4. Manually remove the rogue security software
If the rogue security software can’t be detected or removed by using Microsoft Safety Scanner or the Windows Malicious Software Removal Tool, try the following steps:
Note the name of the rogue security software. For this example, we’ll call it XP Security Agent 2010.
Restart your computer.
When you see the computer’s manufacturer’s logo, repeatedly press the F8 key.
When you are prompted, use the arrow keys to highlight Safe Mode with Networking, and then press Enter.
Click the Start button and check whether the rogue security software appears on the Start menu. If it’s not listed there, click All Programs and scroll to find the rogue security software’s name.
Right-click the name of the rogue security software program, and then click Properties.
Click the Shortcut tab.
In the Properties dialog box, check the path of the rogue security software program that is listed in Target. For example, C:\Program Files\XP Security Agent 2010.
Note The folder name frequently is a random number.
Click Open File Location.
In the Program Files window, click Program Files in the address bar.
Scroll until you find the rogue security software program folder. For example, XP Security Agent 2010.
Right-click the folder, and then click Delete.
Restart your computer.
Click the Download Now button, and then click Run.
Follow the instructions to scan your computer and help remove the rogue security software.
If you suspect that your computer is infected with rogue security software that was not detected by using Microsoft security solutions, you can submit samples by using the Microsoft Malware Protection Center submission form.
5. Run Microsoft Defender Offline
Microsoft Defender Offline is an anti-malware tool that helps remove difficult to eliminate viruses that start before Windows starts. Starting with Windows 10, Microsoft Defender Offline is built-in. To use it follow the steps in this article: Help protect my PC with Microsoft Defender Offline.
Click Download the 32 bit version or Download the 64 bit version, depending on which operating system that you are running. If you’re unsure of which operating system that you are running, see Is my PC running the 32-bit or 64-bit version of Windows.
When you are prompted, click Save As, and then save the file to a DVD, CD, or USB flash drive.
On the infected computer, insert the DVD, CD, or USB flash drive, and then restart the computer.
When you are prompted, press a key to select an option to use to start your computer, such as F12, F5, or F8, depending on the kind of computer that you are using.
Use the arrow key to scroll to the drive where you installed Microsoft Defender Offline file. Microsoft Defender Offline starts and immediately scans for malware.
How to protect your computer against malware
There are actions that you can take to help protect your computer against malware.
Turn on the firewall
Confirm that the Windows firewall is turned on. See Turn Microsoft Defender Firewall on or off for instructions on how to do that on modern versions of Windows.
Click the Start button, and then click Control Panel.
In the Search box, type firewall, and then click Windows Firewall.
In the left pane, click Turn Windows Firewall on or off (you may be prompted to enter your administrator password).
Under each network location, click Turn on Windows Firewall, and then click OK.
Keep your computer up to date
For more information about how to set Automatic Updates in Windows, see Windows Update: FAQ
Don’t be tricked into downloading malware
Here are some tips that can help protect you from downloading software that you don’t want:
Only download programs from sites that you trust. If you’re not sure whether to trust a program that you want to download, enter the name of the program into your favorite search engine to see whether anyone else has reported that it contains spyware.
Read all security warnings, license agreements, and privacy statements that are associated with any software that you download.
Never click «Agree» or «OK» to close a window that you suspect might be spyware. Instead, click the red «x» in the corner of the window or press Alt + F4 on your keyboard to close a window.
Be wary of popular «free» music and movie file-sharing programs, and make sure that you understand all the software packaged with those programs.
Use a standard user account instead of an administrator account. An administrator account can access anything on the system, and any malware run with an administrator account can use the administrator permissions to potentially infect or damage any files on the system.
For more information about how to protect a computer against viruses, see Protect my PC from viruses.
How to obtain computer virus and security-related support
For United States:
Want to chat with a live person? Our Answer Tech trained professionals are ready to help:
Security solutions for IT Professionals:
Support by country:
For locations outside North America:
For computer virus and security-related support for locations outside North America, go to the Microsoft Support website.
How to prevent and remove viruses and other malware
What is malware?
Malware is a term that is used for malicious software that is designed to do damage or unwanted actions to a computer system. Examples of malware include the following:
Rogue security software
What is a computer virus?
A computer virus is a small software program that spreads from one computer to another and interferes with computer operation. A computer virus might corrupt or delete data on a computer, use an email program to spread the virus to other computers, or even delete everything on the hard disk.
Computer viruses are frequently spread by attachments in email messages or by instant messaging messages. Therefore, you must never open an email attachment unless you know who sent the message or you are expecting the email attachment. Viruses can be disguised as attachments of funny images, greeting cards, or audio and video files. Computer viruses also spread through downloads on the Internet. They can be hidden in pirated software or in other files or programs that you might download.
Tip: For information about the symptoms of a computer virus, go to the Microsoft PC Security website.
What is a worm?
A worm is computer code that spreads without user interaction. Most worms begin as email attachments that infect a computer when they’re opened. The worm scans the infected computer for files, such as address books or temporary webpages, that contain email addresses. The worm uses the addresses to send infected email messages, and frequently mimics (or spoofs) the «From» addresses in later email messages so that those infected messages seem to be from someone you know. Worms then spread automatically through email messages, networks, or operating system vulnerabilities, frequently overwhelming those systems before the cause is known. Worms aren’t always destructive to computers, but they usually cause computer and network performance and stability problems.
What is a trojan horse?
A trojan horse is a malicious software program that hides inside other programs. It enters a computer hidden inside a legitimate program, such as a screen saver. Then it puts code into the operating system that enables a hacker to access the infected computer. Trojan horses do not usually spread by themselves. They are spread by viruses, worms, or downloaded software.
What is spyware?
Spyware can install on your computer without your knowledge. These programs can change your computer’s configuration or collect advertising data and personal information. Spyware can track Internet search habits and can also redirect your web browser to a different website than you intend to go to.
What is rogue security software?
A rogue security software program tries to make you think that your computer is infected by a virus and usually prompts you to download or buy a product that removes the virus. The names of these products frequently contain words like Antivirus, Shield, Security, Protection, or Fixer. This makes them sound legitimate. They frequently run right after you download them, or the next time that your computer starts. Rogue security software can prevent applications, such as Internet Explorer, from opening. Rogue security software might also display legitimate and important Windows files as infections. Typical error messages or pop-up messages might contain the following phrases:
Warning!
Your computer is infected!
This computer is infected by spyware and adware.
Note If you receive a message in a popup dialog box that resembles this warning, press ALT + F4 on your keyboard to close the dialog box. Do not click anything inside the dialog box. If a warning, such as the one here, keeps appearing when you try to close the dialog box, it’s a good indication that the message is malicious.
Are you sure you want to navigate from this page?
Your computer is infected! They can cause data lost and file corruption and need to be treated as soon as possible. Press CANCEL to prevent it. Return to System Security and download it to secure your PC.
Press OK to Continue or Cancel to stay on the current page.
If you see this kind of message, then don’t download or buy the software.
How to remove malware such as a virus, spyware, or rogue security software
Removing a computer virus or spyware can be difficult without the help of malicious software removal tools. Some computer viruses and other unwanted software reinstall themselves after the viruses and spyware are detected and removed. Fortunately, by updating the computer and by using malicious software removal tools, you can help permanently remove unwanted software.
To remove a computer virus and other malicious software, follow these steps in order.
1. Install the latest updates from Microsoft Update
Note A computer virus may prevent you from accessing the Microsoft Update website to install the latest updates. We recommend that you set the Automatic Updates service to run automatically so that a computer is not missing any important updates.
For more information, see Windows Update: FAQ
Click Start, and then type Windows Update in the search box.
In the results area, click Windows Update.
Click Check for Updates.
Follow the instructions to download and install the latest Windows Updates.
2. Use the free Microsoft Safety Scanner
Microsoft offers a free online tool that scans and helps remove potential threats from your computer. To perform the scan, go to the Microsoft Safety Scanner website.
3. Use the Windows Malicious Software Removal Tool
For more information about the Microsoft Malicious Software Removal Tool, see the following article in the Microsoft Knowledge Base:
4. Manually remove the rogue security software
If the rogue security software can’t be detected or removed by using Microsoft Safety Scanner or the Windows Malicious Software Removal Tool, try the following steps:
Note the name of the rogue security software. For this example, we’ll call it XP Security Agent 2010.
Restart your computer.
When you see the computer’s manufacturer’s logo, repeatedly press the F8 key.
When you are prompted, use the arrow keys to highlight Safe Mode with Networking, and then press Enter.
Click the Start button and check whether the rogue security software appears on the Start menu. If it’s not listed there, click All Programs and scroll to find the rogue security software’s name.
Right-click the name of the rogue security software program, and then click Properties.
Click the Shortcut tab.
In the Properties dialog box, check the path of the rogue security software program that is listed in Target. For example, C:\Program Files\XP Security Agent 2010.
Note The folder name frequently is a random number.
Click Open File Location.
In the Program Files window, click Program Files in the address bar.
Scroll until you find the rogue security software program folder. For example, XP Security Agent 2010.
Right-click the folder, and then click Delete.
Restart your computer.
Click the Download Now button, and then click Run.
Follow the instructions to scan your computer and help remove the rogue security software.
If you suspect that your computer is infected with rogue security software that was not detected by using Microsoft security solutions, you can submit samples by using the Microsoft Malware Protection Center submission form.
5. Run Microsoft Defender Offline
Microsoft Defender Offline is an anti-malware tool that helps remove difficult to eliminate viruses that start before Windows starts. Starting with Windows 10, Microsoft Defender Offline is built-in. To use it follow the steps in this article: Help protect my PC with Microsoft Defender Offline.
Click Download the 32 bit version or Download the 64 bit version, depending on which operating system that you are running. If you’re unsure of which operating system that you are running, see Is my PC running the 32-bit or 64-bit version of Windows.
When you are prompted, click Save As, and then save the file to a DVD, CD, or USB flash drive.
On the infected computer, insert the DVD, CD, or USB flash drive, and then restart the computer.
When you are prompted, press a key to select an option to use to start your computer, such as F12, F5, or F8, depending on the kind of computer that you are using.
Use the arrow key to scroll to the drive where you installed Microsoft Defender Offline file. Microsoft Defender Offline starts and immediately scans for malware.
How to protect your computer against malware
There are actions that you can take to help protect your computer against malware.
Turn on the firewall
Confirm that the Windows firewall is turned on. See Turn Microsoft Defender Firewall on or off for instructions on how to do that on modern versions of Windows.
Click the Start button, and then click Control Panel.
In the Search box, type firewall, and then click Windows Firewall.
In the left pane, click Turn Windows Firewall on or off (you may be prompted to enter your administrator password).
Under each network location, click Turn on Windows Firewall, and then click OK.
Keep your computer up to date
For more information about how to set Automatic Updates in Windows, see Windows Update: FAQ
Don’t be tricked into downloading malware
Here are some tips that can help protect you from downloading software that you don’t want:
Only download programs from sites that you trust. If you’re not sure whether to trust a program that you want to download, enter the name of the program into your favorite search engine to see whether anyone else has reported that it contains spyware.
Read all security warnings, license agreements, and privacy statements that are associated with any software that you download.
Never click «Agree» or «OK» to close a window that you suspect might be spyware. Instead, click the red «x» in the corner of the window or press Alt + F4 on your keyboard to close a window.
Be wary of popular «free» music and movie file-sharing programs, and make sure that you understand all the software packaged with those programs.
Use a standard user account instead of an administrator account. An administrator account can access anything on the system, and any malware run with an administrator account can use the administrator permissions to potentially infect or damage any files on the system.
For more information about how to protect a computer against viruses, see Protect my PC from viruses.
How to obtain computer virus and security-related support
For United States:
Want to chat with a live person? Our Answer Tech trained professionals are ready to help:
Security solutions for IT Professionals:
Support by country:
For locations outside North America:
For computer virus and security-related support for locations outside North America, go to the Microsoft Support website.
How to Remove a Virus or Malware from Your PC
How to Remove a Malware from Your PC
No one expects to deal with a computer infected with a malware, but even the most diligent and cyber savvy person makes mistakes. Spear phishing and other socially engineered attacks have become so sophisticated that hackers are very good at sneaking past security checkpoints. Malware can and will damage your computer, but you can minimize that damage by catching the threat and removing it from your PC in a timely manner.
Verify the Infection
You first suspect your computer is infected for a reason. Maybe it’s running slowly or experiencing an unusual number of pop-ups, for example. The bottom line is something doesn’t seem right. To verify your PC is infected, Microsoft offers various free tools for download on its Sysinternals tools webpage. The Process Explorer and Autorun tools check for unusual files that could point to malware and allow you to «kill» the executable. Microsoft also offers a Microsoft Windows Malicious Software Removal Tool.
Removing Threats
If you have malware on your PC that isn’t removed by any of the Microsoft tools, you can delete the files manually. Before beginning the process, make sure your antivirus (if applicable) and on-demand malware scanning tools are updated.
To remove a virus from your PC, disconnect from the internet and restart your computer in safe mode. (Booting into safe mode with Windows 10 is different than older versions. Follow these directions.) Working offline prevents the malware from doing more damage and eliminates the risk of downloading more problems. Once in safe mode, delete temporary files using the Disk Cleanup tool. This should speed up the scans you need to do and may even delete malware hidden in these files.
After cleaning up the hard drive, run the on-demand scan. Because you aren’t connected to the internet, the scan only covers malware recognized by the most recent update, which is why your operating system and all software needs to be current. Otherwise, the scan may not detect the virus.
The type of scan you perform is up to you. The quick scan for general threats may be enough to find malware lurking in your system, but if you want to be very thorough and you have more time, a full or custom scan digs deeper. If the on-demand scanning tool finds a problem, it should delete or quarantine the associated file before clearing you to reboot your computer into normal mode. However, if time permits, it’s a good idea to run a second scan with the on-demand scanner or with antivirus software to make sure nothing else is lingering in the background.
If your PC continues to show signs of malware, you may have to save your most important data to an external hard drive or cloud server and re-install Windows.
Post-Malware Care
Removing malware as soon as possible keeps your information safe from prolonged attacks, but it won’t protect you from damage that may have already occurred. The malware may have leaked usernames, passwords and other sensitive information before you caught it.
Once you are certain the PC is clear of the virus, the hard work begins. You should change all your passwords, starting with banking and financial accounts. Again, before doing so, make sure all your software, your browser and your operating system are fully updated to plug potential vulnerabilities. Additionally, check your browser settings to make sure all the strongest security measures are turned on.
Finally, install highly rated security solution and use good security practices, such as verifying attachments, visiting only secure websites and never clicking on unknown links online or in email. Otherwise, you could find yourself removing another virus from your PC.
How do computer viruses work?
Are you concerned that your computer may have a virus? If your computer is infected, learning how to get rid of a computer virus is vital.
This article teaches you all there is to know about how computer viruses work and computer virus removal.
Read on as we discuss:
How to get rid of a computer virus
In this section, we explore how to get rid of a computer virus from a PC and from a Mac.
Removing a computer virus from a PC
Computer viruses are almost always invisible. Without anti-virus protection, you may not know you have one. This is why it is vital to install anti-virus protection on all your devices.
If your PC has a virus, following these ten simple steps will help you to get rid of it:
Step 1: Download and install a virus scanner
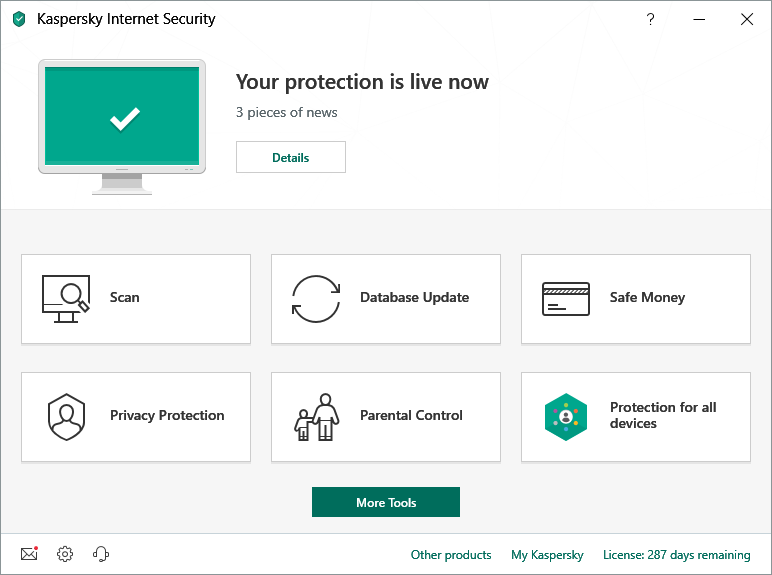
Download a virus scanner or complete internet security solution. We recommend Kaspersky Internet Security. The video below will guide you through the installation process:
Step 2: Disconnect from internet
When you are removing a virus from your PC, it is a good idea to disconnect from the internet to prevent further damage: some computer viruses use the internet connection to spread.
Step 3: Reboot your computer into safe mode
To protect your computer while you remove the virus, reboot it in ‘Safe Mode’. Are you unsure of how to do this?
Here is a simple guide:
Step 4: Delete any temporary files
Next, you need to delete any temporary files using ‘Disk Clean Up’.
Here’s how to do this:
Some viruses are programmed to initiate when your computer boots up. Deleting temporary files may delete the virus. However, it is not safe to rely on this. To ensure you rid your computer of viruses, it is wise to complete the following steps.
Step 5: Run a virus scan
Now it is time to run a virus scan using your chosen anti-virus or internet security software. If you are using Kaspersky Internet Security, select and run ‘Scan’.
Step 6: Delete or quarantine the virus
If a virus is found, it may affect multiple files. Select ‘Delete’ or ‘Quarantine’ to remove the file(s) and get rid of the virus. Rescan your computer to check there’s no further threats. If threats are found, quarantine or delete the files.
Step 7: Reboot your computer
Now that the virus is removed, you can reboot your computer. Simply turn it on as you would normally. It no longer needs to be in ‘Safe Mode’.
Step 8: Change all your passwords
To protect your computer from further attack, change all your passwords in case they were compromised. This is only strictly necessary if you have reason to believe your passwords have been captured by malware, but it is better to be safe than sorry.
You can always check the virus’s functionality on your anti-virus vendor’s website or with their technical support team if unsure.
Step 9: Update your software, browser and operating system
Updating your software, browser and operating system will reduce the risk of flaws in old code being exploited by criminals to install malware on your computer.
Removing a computer virus from a Mac
If you use a Mac, you may be under the impression that your computer cannot get a virus. Unfortunately, this is a misconception. There are fewer viruses that target Macs compared with the many that target PCs, but Mac viruses do exist.
Some Mac viruses are designed to trick users into thinking they are anti-virus products. If you accidentally download one of these, your computer may be infected. Three examples of Mac viruses of this type are ‘MacDefender’, ‘MacProtector’, and ‘MacSecurity’.
If you think your Mac has a virus, here are six steps to follow to remove it:
To ensure nothing is missed and to keep your Mac protected, consider installing a running an anti-virus solution if you do not already have one. We recommend comprehensive internet security solution like Kaspersky Total Security.
What is a computer virus?
A computer virus is a type of malware (malicious software) designed to make self-replicate, i.e. to make copies of itself on any drive connected to your computer.
Computer viruses are so-called because, like real viruses, they can self-replicate. Once your computer is infected with a virus, this is how it spreads. When a computer virus infects your computer, it may slow it down and stops it working properly.
There are three main ways that your computer may have become infected with a computer virus.
The first way your computer could become infected from removable media, like a USB stick. If you insert a USB stick or disk into your computer from an unknown source, it may contain a virus.
Sometimes hackers leave infected USB sticks or disks in people’s workplaces, or public places like cafes to spread computer viruses. People sharing USBs may also transfer files from an infected computer to one that isn’t infected.
Another way your computer become infected with a virus is through a download from the internet.
If you are downloading software or apps to your computer, ensure you do so from a trusted source. For example, the Google Play Store or Apple’s App Store. Avoid downloading anything via a pop-up or a website you do not know.
The third way your computer could become infected with a virus is if you open an attachment, or click on a link, in a spam email.
Whenever you receive mail from a sender you do not know or trust, avoid opening it. If you do open it, do not open any attachments or click on any links.
How to tell if your computer has a virus
There are numerous signs to look out for that indicate your computer may have a virus.
Firstly, is your computer slowing down? If everything is taking longer than usual, your computer may have become infected.
Secondly, look out for apps or programs that you do not recognize. If you see an app or a program appear on your computer that you do not remember downloading, exercise caution.
It is a good idea to uninstall any software you do not recognize and then to run a virus scan using anti-virus or internet security software to check for threats. Pop-ups that appear when your browser is closed are a tell tail sign of a virus. If you see these, take immediate action to remove the virus, by following the steps outlined above.
Another sign that your computer may have a virus is if apps or programs on your computer start behaving strangely. If they start crashing for no apparent reason, your computer may have a virus.
Finally, a virus may cause your computer to start overheating. If this happens, investigate whether you have a virus using anti-virus or internet security software.
Can your computer become infected with a virus via email?
Your computer can become infected with a virus via email, but only if you open attachments within a spam email or click on the links contained in them.
Simply receiving a spam email will not infect your computer. Just mark these as spam or junk and ensure they are deleted. Most email providers will automate this (Gmail for example) but if any slip through the net, just mark them as spam yourself and don’t open them.
How to protect your computer from viruses
Here are some key ways that you can protect your computer from viruses:
Kaspersky Internet Security received two AV-TEST awards for the best performance & protection for an internet security product in 2021. In all tests Kaspersky Internet Security showed outstanding performance and protection against cyberthreats.
How do computer viruses work?
Has your computer got a virus? Learn how to get rid of a computer virus, how to find out if your computer has one and if you can get a computer virus via email.
Источники информации:
- http://support.microsoft.com/en-gb/topic/how-to-prevent-and-remove-viruses-and-other-malware-53dc9904-0baf-5150-6e9a-e6a8d6fa0cb5
- http://support.microsoft.com/en-us/topic/how-to-prevent-and-remove-viruses-and-other-malware-53dc9904-0baf-5150-6e9a-e6a8d6fa0cb5
- http://www.kaspersky.com/resource-center/preemptive-safety/how-to-remove-a-virus-or-malware-from-your-pc
- http://www.kaspersky.co.in/resource-center/threats/how-to-get-rid-of-a-computer-virus