Snmp how to use
Snmp how to use
Snmp how to use
SNMP stands for Simple Network Monitoring Protocol. It is a protocol for management information transfer in networks, for use in LANs especially, depending on the chosen version.
Its usefulness in network administration comes from the fact that it allows information about network-connected devices to be collected in a standardized way across a large variety of hardware and software types.
Hardly any network admin renounces SNMP. Rather, most of them confidently rely on it because nearly all kinds of devices from many different manufacturers support SNMP, which helps them achieve comprehensive monitoring thanks to the SNMP technology.
Versions
Currently, there are three major versions of SNMP. The first version was developed rather quickly in the late ´80s when network administration lacked suitable network administration tools that were not dependent on hardware manufacturers.
SNMP v1 was defined in 1988 and was based on SGMP ( RFC 1028 ). Then, it was broadly accepted and used. It is still used today, almost 30 years later, which is nearly an eternity in IT. SNMP v1 provides the basic functionalities for data polling and is relatively easy to use. It doesn’t create much overhead because it doesn’t include any encryption algorithms. So, for security reasons, use SNMP v1 in LANs only. Its biggest limitation is its 32-bit counter architecture, which is not enough for today’s gigabyte networks or larger.
If users want to manage networks in a WAN, the CMISE/CMIP protocol is the right protocol to go for.
SNMP v2 supports 64-bit counters but still sends critical data as clear text, so it does not really enhance security. And if users come across SNMP v2, it is mostly «SNMP v2c» that manufacturers or networkers are talking about, with the «c» standing for «community». Two other SNMP v2 versions exist, SNMP v2p and SNMP v2u, but they are only implemented in rare cases.
Credentials for SNMP devices
Defined in 2002, SNMP v3 includes the advantages of SNMP v2c and adds security solutions like user accounts, authentication, and optional encryption of data packages. This enhances security and makes SNMP v3 the recommended SNMP version when it comes to security. However, it also makes configuration more difficult, specifically user management. Therefore, much more processing power is needed, especially with short monitoring intervals that create a great number of SNMP messages.
SNMP v3 has three different security levels:
How does SNMP work?
A network normally has at least one computer or server running monitoring software. It is the managing entity. A network will also most probably have a few, or many, or even really many, other devices: switches, routers, workstations, server racks, printers, coffee machines, or anything else that needs to be monitored. They are the managed devices.
SNMP messages are sent and received between so-called managers and agents. Usually, the SNMP manager in the network is installed on the managing entity and the SNMP agents are installed on the managed devices.
Basically, the transfer of SNMP messages can be compared to the typical communication between a client and a server, offering both pull and push technologies. The pull (or poll) technology is the most common communication type where a client, like the network management software on the managing entity, sends out a request to solicit a response from a server, or managed device. Its counterpart, the push technology, allows the managed device to “speak” and send out an SNMP message upon an event.
In SNMP terminology, for example, a GET request from an SNMP manager (client) follows the pull model, whereas an SNMP trap is «pushed out» by an SNMP agent (server) without any previous request.
SNMP message types
There are different types of SNMP messages that can be used to set up network monitoring via SNMP:
SNMP message transfer
SNMP uses the User Datagram Protocol (UDP) to transfer messages. It is necessary that UDP packets can make it from the agent to the manager for monitoring to be successful. This typically works by default on a local network but additional router configuration is needed to allow such packets to traverse wider networks.
SNMP agents receive UDP requests on port 161. Requests sent from an SNMP manager may be sent from any port. Usually, it’s 161. Agents send traps via port 162. The SNMP manager also receives traps on port 162.
What are OIDs and MIBs?
OID stands for Object Identifier. OIDs uniquely identify managed objects that are defined in MIB files.
Example:
On a printer, the typical objects to monitor are the different cartridge states and maybe the number of printed files. On a switch, the typical objects of interest are the incoming and outgoing traffic as well as the rate of package loss or the number of packets addressed to a broadcast address.
The object (OID) hierarchy is generally depicted as a tree with different levels from the root to the single leaves. Each OID has an address that follows the levels of the OID tree.
Sample:
Here is a sample structure of an OID:
Top level and general MIB object IDs are asssigned by different standard organizations like ISO. Vendors define OIDs for their own products in p rivate branches of the OID tree.
There are two types of objects: scalar and tabular ones. Scalar objects define a single object instance whereas tabular objects define multiple related object instances grouped in MIB tables.
Why OIDs and MIBs are needed
Every piece of management information that can be obtained via SNMP – be it the memory usage of a server, the traffic on a switch, or the queued files on a printer – is individually addressed by its OID. This property is the reason why OIDs are needed. They help admins to identify and monitor the objects that they have in their network and thus make monitoring meaningful.
For the managing entity and a managed device in networks to communicate successfully, both of them need to know which OIDs are available.
This is the reason why MIBs exist and why system admins need them. Every object that has to be monitored on a device has to be provided by the device’s MIB(s). Therefore, admins have to make sure that all necessary MIBs are stored on SNMP agent devices as well as on the managing entity system. An MIB file can be easily recognized via the extensions .my or .mib.
Device manufacturers normally deliver the necessary MIBs along with their SNMP-supporting products. Depending on the monitoring solution used, one might have to convert MIBs to product specific MIB versions.
Why SNMP is so universal: SMI
There are various factors that make SNMP so universal. Structure of Management Information (SMI) provides a commonly understood and standardized structure for the data types and for the transfer of them. Please also consider this link to get to the bottom of why SMI is also inextricably tied to OIDs and MIBs. More about SMI here.
Value added by SNMP
Being well organized
It can be an adventure to keep track of the vast quantity of network devices that modern networks comprise. Ideally, monitoring solutions support admins by offering a suitable way to structure and group devices and by presenting a clear overview that allows to go into detail whenever needed to ensure overall system health.
Alerting & notifying
Thanks to monitoring tools, sysadmins know exactly where to take action when a problem arises, and sometimes they even know before it occurs. Being informed on time is absolutely critical, so monitoring solutions should offer enough ways to notify the admin – like email, push notifications, SMS text messages (to be on the safe side when there’s no internet, for example), execution of a program, or even alerts on a smartwatch.
Reporting & statistics
Network monitoring will result in a lot of data in monitoring database. Let the numbers speak for themselves and use them to create reports and statistics. Analysis will not only provide insight into networks, but also help justify IT needs to the accounting or managing board. Visual dashboards will also help to be more successful.
Planning ahead
Data analysis will show the trends for individual networks and allow to plan ahead. The results: reliability, speed, and efficiency.
Comfortable setup
Setting up monitoring for large networks can be very tedious and time-consuming. Monitoring tools will automate and speed that up for the users and provide, for example, flexible network auto-discoveries or default templates for widely used network infrastructure products. And who would have thought? These technologies most probably use SNMP, too!
Network Basics: What Is SNMP and How Does It Work?
What is Simple Network Management Protocol (SNMP)?
Simple Network Management Protocol (SNMP) is a way for different devices on a network to share information with one another. It allows devices to communicate even if the devices are different hardware and run different software. And despite any rumors you may hear, it’s not going anywhere anytime soon.
Without a protocol like SNMP, there would be no way for network management tools to identify devices, monitor network performance, keep track of changes to the network or determine the status of network devices in real-time.
That’s how Paul Querna summed up the Simple Network Management Protocol, or SNMP, back in 2003. He was writing about how the protocol can be used to collect lots of network information easily, but can also seem convoluted.
Querna’s phrase sums up SNMP quite effectively. The protocol certainly has its shortcomings, just like any other technology. And those drawbacks are more pronounced in some SNMP versions than in others.
At the same time, though, SNMP is a vital tool for effective network management. It’s not perfect, but it’s one of the best solutions available for monitoring and managing devices on the network.
Below, I discuss SNMP’s role in network management, identify the various SNMP versions available, and explain how to use SNMP effectively and securely on your network.
SNMP architecture
SNMP has a simple architecture based on a client-server model.
Some devices may have multiple device components. For example, a laptop typically contains a wired as well as a wireless network interface.
SNMP data hierarchy
While the SNMP architecture is simple, the data hierarchy the protocol uses can seem complicated if you’re not familiar with it. Fortunately, it’s relatively simple once you understand the philosophy behind it.
To provide flexibility and extensibility, SNMP doesn’t require network devices to exchange data in a rigid format of fixed size. Instead, it uses a tree-like format, under which data is always available for managers to collect.
The data tree consists of multiple tables (or branches, if you want to stick with the tree metaphor), which are called Management Information Bases, or MIBs. MIBs group together particular types of devices or device components. Each MIB has a unique identifying number, as well as an identifying string. Numbers and strings can be used interchangeably (just like IP addresses and hostnames).
Each MIB consists of one or more nodes, which represent individual devices or device components on the network. In turn, each node has a unique Object Identifier, or OID. The OID for a given node is determined by the identifier of the MIB on which it exists combined with the node’s identifier within its MIB.
Written with strings, that OID would translate to:
iso.org.dod.internet.private.transition.products.chassis.card.slotCps.
cpsSlotSummary.cpsModuleTable.cpsModuleEntry.cpsModuleModel.3562.3.
Using the OID, a manager can query an agent to find information about a device on the network. For example, if the manager wants to know whether an interface is up, it would first query the interface MIB (called the IF-MIB), then check the OID value that reflects operational status to determine whether the interface is up.
Why use OIDs?
The MIB and OID data hierarchy may seem confusing, but there are several important advantages to a system like this. One is that information can be pulled by the manager without having to send an explicit request for the agent to collect it. That reduces overhead and ensures information about the network’s status is always readily available.
The system also provides an easy, flexible way to organize many devices across a network. It works no matter how large or small the network is, or what kind of devices are on it.
SNMP also makes it possible to collect large amounts of information quickly without clogging the network with traffic. Because information about device status is always available in a simple format and is updated in real-time, managers can pull it without waiting for the data to be collected or requiring large data transfers.
Last but not least, it’s worth noting that some OID values are vendor-specific, which makes it easy to gain some information about a device based simply on its OID (Auvik now includes extended OID monitor history!). For example, if an OID starts with 1.3.6.1.4.1.9, it applies to a Cisco device. Other vendors have their own OID specifications. (Wireshark, the open-source network scanner, offers a handy OID lookup tool.) The standard OID prefix, which can be used for almost any device that supports SNMP, is 1.3.6.1.2.
SNMP versions
The final important thing to understand about SNMP is that the features available in different versions of the protocol vary widely, especially when it comes to security.
Photo Briana Cole on Flickr
SNMPv1
The first version of SNMP—SNMPv1—offers weak security features. Under SNMPv1, managers can authenticate to agents without encryption when requesting information. That means anyone with access to the network could run “sniffing” software to intercept information about the network. It also means an unauthorized device can easily pretend to be a legitimate manager when controlling the network.
As well, SNMPv1 uses certain default credentials, which admins don’t always update, making it easy for unauthorized parties to gain access to sensitive information about the network. Unfortunately, SNMPv1 is still used on a relatively wide basis today because some networks haven’t yet been updated.
SNMPv2
SNMPv2, which appeared in 1993, offered some security enhancements, but it was supplanted in 1998 by SNMPv3, which remains the most recent version of the protocol and the most secure.
SNMPv3
SNMPv3 makes data encryption possible. It also allows admins to specify different authentication requirements on a granular basis for managers and agents. This prevents unauthorized authentication and can optionally be used to require encryption for data transfers.
The bottom line is that, while the security issues in SNMPv1 earned SNMP a bad name in some circles, SNMPv2 and especially SNMPv3 solved those problems. The newer versions of SNMP provide an up-to-date, secure way to monitor the network.
Enabling SNMP
If the poor security in SNMPv1 has you worried, fret not. SNMP is not normally enabled by default on devices. That means that, in most cases, admins have to log in and turn it on in order to make SNMP data available. This requirement reduces the risk of running an insecure SNMP version without realizing it.
Back that up!
And once you’ve enabled and taken the time to properly configure SNMP, don’t forget to back it up! Backups are a routine part of any network maintenance checklist, and should never be missed. Automation of backups can not only add peace of mind, but will ensure you’ve always got multiple restore points to choose from.
About Dana Oros
Dana is the technical training director at Auvik. She also has a kayak and a history degree.
SNMP Basics: What is SNMP & How Do I Use It?
You’ve decided you want to get a better handle on your network. Maybe you’re looking at setting up some monitoring. But then you discover you need to configure this thing called SNMP, and that’s when the problems start. There are things to configure that you’ve never heard of: OIDs, MIBs, traps, informs, polling, and versions. What the heck is all this stuff anyway, and do you need to know it all?
In this first part of a series on SNMP you’ll learn the basics, and see how it can help you make your network more reliable and easier to manage.
What the Heck is SNMP Anyway?
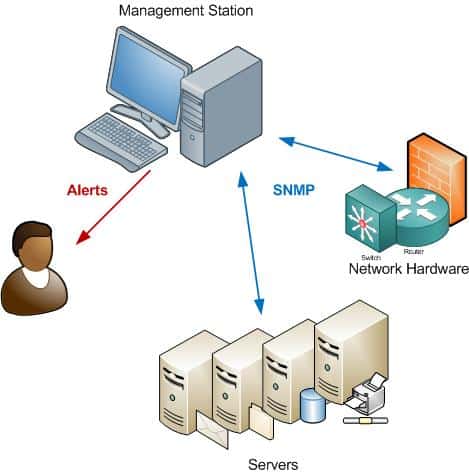
SNMP stands for Simple Network Management Protocol. It is a standard way of monitoring hardware and software from nearly any manufacturer, from Juniper, to Cisco, to Microsoft, Unix, and everything in between. SNMP requires only a couple of basic components to work: a management station, and an agent.
First, a management station is required. The management station is simply software that collects information from your network. Most management stations will poll your network for information regularly. Management stations range from the very simple to highly complex.
Simple software is usually very feature-limited, but can be freely available and easy to configure. For example, the free SolarWinds Network Device Manager that was recently released.
On the other hand, complex systems can manage your entire network. They will also do things like generate reports, perform inventory, and send email or SMS text alerts when systems fail. Networkmanagementsoftware.com recently reviewed SolarWinds Network Performance Monitor, – an excellent management solution.
Second, the hardware or software that you want to monitor must have an agent running. The agent collects information, and then sends it to the monitoring station when polled. Agents can also send notification to the management station without being polled, for example if an error is detected.
Agents are usually built-in to your network hardware and software – they simply need to be enabled and configured.
What Can It Do?
SNMP is very simple, yet powerful. It has the ability to help you manage your network by:
Versions and Security (or Lack Thereof)
Several versions of SNMP are supported, v1, v2c, and v3. Nearly all monitoring stations support all three versions. So why not simply use the newest version all the time?
Version 1 is the simplest and most basic of the versions, and there may be times where it’s required to support older hardware. But version 2c adds several enhancements to the protocol, such as support for “Informs”. Because of this v2c has become most widely used.
However, a major weakness of v1 and v2c is security. Community strings – the equivalent of passwords – are transmitted in clear text and there is no support for authentication. This creates risk that your community strings could become compromised. This is not good, especially considering the power SNMP has to change device configuration.
SNMP v3 adds a security features that overcome the weaknesses in v1 and v2c, and it should generally be used if possible – especially if you plan to transmit information across unsecured links. However, the extra security makes it much more complex to configure.
Ports and Firewalls
SNMP uses UDP as the transport protocol. If management traffic will traverse firewalls, make sure that the following default ports are open:
MIBs, OIDs and Traps, Oh My!
The basics of SNMP are simple, but terminology is one of the needlessly complicated parts of SNMP. However, it’s easily understood. In the next article we’ll help clear the confusion around things like “strings”, and “MIBs”.
After that, we’ll look at a few tools you can use to explore SNMP in greater detail, and start using it to automate critical monitoring tasks. In the meantime, check out our Downloads page for links and reviews of many popular monitoring systems and tools.
Snmp how to use
SNMP stands for «Simple Network Management Protocol.» It’s an application layer protocol included in the internet protocol suite, a set of the most commonly used communication protocols online.
SNMP originated in the 1980s at the time when organizational networks were growing in both size and complexity. Today, it’s one of the most widely accepted protocols for network monitoring. Here’s a look at how SNMP works and why it matters to network professionals.
SNMP is used to collect data related to network changes or to determine the status of network-connected devices. Collecting this data can help IT professionals keep their finger on the pulse of all their managed devices and applications. Every device within the network can be queried in real time with SNMP, TCP, and other types of probes for their performance metrics. When thresholds for certain values are exceeded, software can alert system administrators of the issue, allowing them to drill into the data and troubleshoot a solution.
How SNMP Works
All day, traffic is ebbing and flowing across your network as users conduct transfers, browse, perform downloads, and more. SNMP talks to your network to find out information related to this network device activity. For example, it tracks bytes, packets, and errors transmitted and received on a router, connection speed between devices, or the number of hits a web server receives.
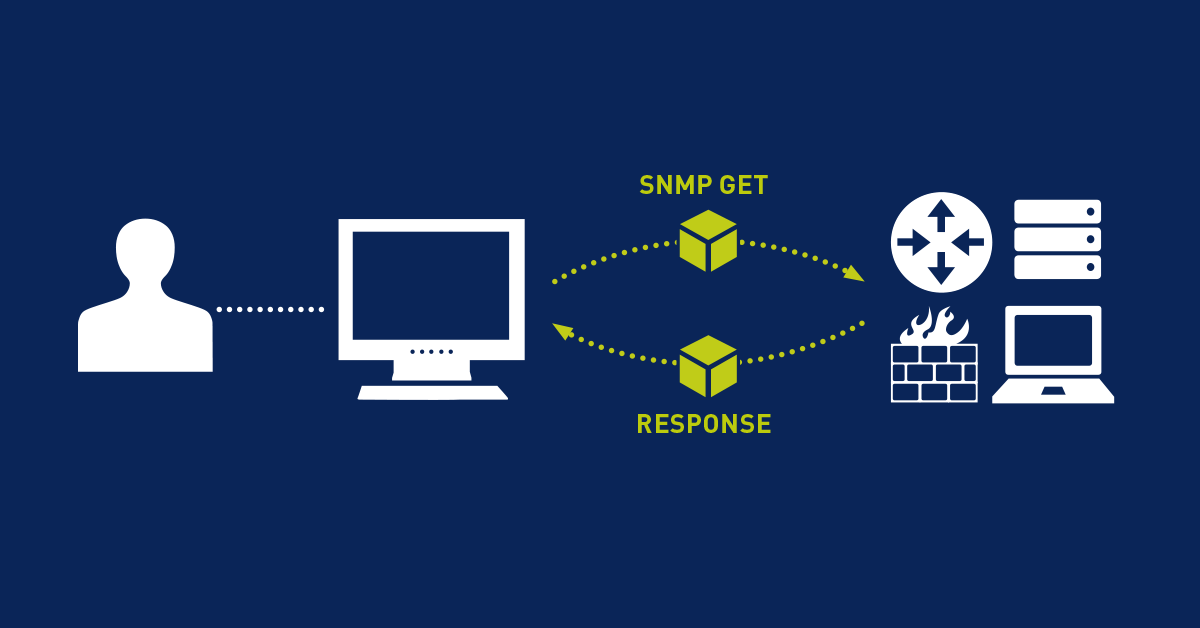
SNMP works by sending messages, called protocol data units (PDUs), to devices within your network that “speak” SNMP. These messages are called SNMP Get-Requests. Using these requests, network administrators can track virtually any data values they specify. All of the information SNMP tracks can be provided to a product that asks for it. That product can either display or store the data, depending on an administrator’s preferences.
The Five Basic SNMP Commands
SNMP uses five basic messages to allow the SNMP manager and SNMP agent to communicate:
The SNMPTRAP command is a common way for devices to send alerts. These are asynchronous messages sent to the manager by an agent when something needs to be reported. A storage appliance, for example, might send a trap to the manager when it loses access to a drive. Other examples include a power-up situation or high-traffic notification that should be evaluated.
But SNMP managers don’t have to sit around waiting for agents to send a message. They may prefer to ask for data proactively. This ensures devices are still active and functioning properly. Without a proactive check you may not know if a quiet device is offline or simply doesn’t have anything to report.
The SNMPGET command retrieves one or more values from the MIB (management information base).
GET NEXT
The GETNEXT command retrieves the next corresponding value of the OID (object identifier) in the MIB tree.
GET RESPONSE
The GETRESPONSE command is used by the agent to send back the values of actions requested by the SNMP manager.
If a manager wants to ask an agent for data with a get message, the agent will send back a get-response. The manager might only need that one piece of data, or it can then send a get-next message (and then another, and another) to request a full status update.
The SNMPSET command is used by the SNMP manager to tell an agent to take action. Some agents control relay outputs that can be toggled. Others have beacon lights, backup systems, thermostats, and other settings that can be changed with a set command.
SNMP Components & Architecture
In order to effectively monitor network activity, SNMP relies on an architecture consisting of the following:
Together, these components gather information to bring back to the network requester.
Two Types of SNMP Configurations
SNMP uses read and read-write community strings to share information. Both can be configured to allow public access or set to prevent unauthorized changes.
SNMP Protocol Versions
SNMP & Network Monitoring Tools
For IT departments looking to harness the power of SNMP, it’s imperative to have a network monitoring tool that’s up for the task. SNMP monitoring tools can run automatic discovery on the network and interrogate devices to extract exposed data, which facilitates monitoring comprehensively across all devices.
Intermapper uses SNMP probes to query network devices for their management information base (MIB) variables. SNMP needs access to MIBs and their associated object identifiers (OIDs) in order to interrogate devices and read data. As a leading network monitoring software choice, Intermapper has hundreds of built-in network probes to give you a wide variety of data about your network performance. And it works with the latest protocol version, SNMPv3. Users also have the ability to create their own custom probes. This enables SNMP-speaking devices to deliver device status updates in a way that enhances the overall quality of network monitoring and management.
Continue Learning:
The Network Professional’s Survival Guide
We asked network professionals like you to share the tips and tools that help them survive and succeed. This guide compiles advice on how to survive your daily network responsibilities.
Explore Network Monitoring Software
Learn how Intermapper monitors and maps everything with an IP address to give you a look at your entire environment.
An Introduction to SNMP (Simple Network Management Protocol)
Introduction
A large part of being a system administrator is collecting accurate information about your servers and infrastructure. There are a number of tools and options for gathering and processing this type of information. Many of them are built upon a technology called SNMP.
SNMP stands for simple network management protocol. It is a way that servers can share information about their current state, and also a channel through which an administer can modify pre-defined values. While the protocol itself is very simple, the structure of programs that implement SNMP can be very complex.
In this guide, we will introduce you to the basics of the SNMP protocol. We will go over its uses, the way that the protocol is typically used in a network, the differences in its protocol versions, and more.
Basic Concepts
SNMP is a protocol that is implemented on the application layer of the networking stack (click here to learn about networking layers). The protocol was created as a way of gathering information from very different systems in a consistent manner. Although it can be used in connection to a diverse array of systems, the method of querying information and the paths to the relevant information are standardized.
There are multiple versions of the SNMP protocol, and many networked hardware devices implement some form of SNMP access. The most widely used version is SNMPv1, but it is in many ways insecure. Its popularity largely stems from its ubiquity and long time in the wild. Unless you have a strong reason not to, we recommend you use SNMPv3, which provides more advanced security features.
In general, a network being profiled by SNMP will mainly consist of devices containing SNMP agents. An agent is a program that can gather information about a piece of hardware, organize it into predefined entries, and respond to queries using the SNMP protocol.
The component of this model that queries agents for information is called an SNMP manager. These machines generally have data about all of the SNMP-enabled devices in their network and can issue requests to gather information and set certain properties.
SNMP Managers
An SNMP manager is a computer that is configured to poll SNMP agent for information. The management component, when only discussing its core functionality, is actually a lot less complex than the client configuration, because the management component simply requests data.
The manager can be any machine that can send query requests to SNMP agents with the correct credentials. Sometimes, this is implemented as part of a monitoring suite, while other times this is an administrator using some simple utilities to craft a quick request.
SNMP Agents
SNMP agents do the bulk of the work. They are responsible for gathering information about the local system and storing them in a format that can be queried.updating a database called the “management information base”, or MIB.
The MIB is a hierarchical, pre-defined structure that stores information that can be queried or set. This is available to well-formed SNMP requests originating from a host that has authenticated with the correct credentials (an SNMP manager).
The agent computer configures which managers should have access to its information. It can also act as an intermediary to report information on devices it can connect to that are not configured for SNMP traffic. This provides a lot of flexibility in getting your components online and SNMP accessible.
Understanding the Management Information Base
The most difficult part of the SNMP system to understand is probably the MIB, or management information base. The MIB is a database that follows a standard that the manager and agents adhere to. It is a hierarchical structure that, in many areas, is globally standardized, but also flexible enough to allow vendor-specific additions.
The MIB structure is best understood as a top-down hierarchical tree. Each branch that forks off is labeled with both an identifying number (starting with 1) and an identifying string that are unique for that level of the hierarchy. You can use the strings and numbers interchangeably.
To refer to a specific node of the tree, you must trace the path from the unnamed root of the tree to the node in question. The lineage of its parent IDs (numbers or strings) are strung together, starting with the most general, to form an address. Each junction in the hierarchy is represented by a dot in this notation, so that the address ends up being a series of ID strings or numbers separated by dots. This entire address is known as an object identifier, or OID.
Hardware vendors that embed SNMP agents in their devices sometimes implement custom branches with their own fields and data points. However, there are standard MIB branches that are well defined and can be used by any device.
The standard branches we will be discussing will all be under the same parent branch structure. This branch defines information that adheres to the MIB-2 specification, which is a revised standard for compliant devices.
The base path to this branch is:
This can also be represented in strings like:
The section 1.3.6.1 or iso.org.dod.internet is the OID that defines internet resources. The 2 or mgmt that follows in our base path is for a management subcategory. The 1 or mib-2 under that defines the MIB-2 specification.
This is a great resource for familiarizing yourself with the MIB tree. This particular page represents the connecting nodes at the junction we have been talking about. You can check what is further up and down the tree by checking out the “superior” and “subsidiary” references respectively.
Another similar tool is a SNMP Object Navigator provided by Cisco. This can be used to drill down into the hierarchy to find information you need. A similar tree is provided by SolarWinds.
SNMP Protocol Commands
One of the reasons that SNMP has seen such heavy adoption is the simplicity of the commands available. There are very few operations to implement or remember, but they are flexible enough to address the utility requirements of the protocol.
The following PDUs, or protocol data units, describe the exact messaging types that are allowed by the protocol:
With these seven data unit types, SNMP is capable of querying for and sending information about your networked devices.
Protocol Versions
The SNMP protocol has gone through many changes since it was first introduced. The initial spec was formulated with RFC 1065, 1066, and 1067 in 1988. By the simple fact that it has been around so long, this version is still widely supported. However, there are many security issues with the protocol, including authenticating in plain text, so its use is highly discouraged, especially when used on unprotected networks.
Work on version 2 of the protocol was initiated in 1993 and offers some substantial improvements on the earlier standard. Included in this version was a new “party-based” security model meant to address the security issues inherent with the prior revision. However, the new model was not very popular because it was difficult to understand and implement.
Because of this, a few “spin-offs” of version 2 were created, each of which kept the bulk of the version 2 improvements, but swapped out the security model. In SNMPv2c, community-based authentication, the same model used in v1, was reintroduced. This was the most popular version of the v2 protocol. Another implementation, called SNMPv2u, uses user-based security, although this was never very popular. This allowed for per-user authentication settings.
In 1998, the third (and current) version of the SNMP protocol entered as a spec proposal. From a user’s perspective, the most relevant change was the adoption of a user-based security system. It allows you to set a user’s authentication requirements as one of these models:
In addition to authentication, an access control mechanism was implemented to provide granular control over which branches a user can access. Version 3 also has the ability to leverage the security provided by the transport protocols, such as SSH or TLS.
Conclusion
Now that you have a good idea about how the protocol operates, you have the foundation needed to implement SNMP in your own infrastructure.
In the next guide, we’ll discuss how to install and configure the components necessary to leverage SNMP on your systems.
Want to learn more? Join the DigitalOcean Community!
Join our DigitalOcean community of over a million developers for free! Get help and share knowledge in our Questions & Answers section, find tutorials and tools that will help you grow as a developer and scale your project or business, and subscribe to topics of interest.
Tutorial Series: Monitoring and Managing your Network with SNMP
SNMP, or simple network management protocol, is a well-established way of monitoring and managing diverse sets of networked systems. In this series, we will introduce you to the basics of the protocol, teach you how to install the agent and manager components on several hosts, and demonstrate how to use the net-snmp suite of utilities to gather information and modify the configuration of remote hosts.
Источники информации:
- http://www.auvik.com/franklyit/blog/network-basics-what-is-snmp/
- http://www.networkmanagementsoftware.com/snmp-tutorial/
- http://www.helpsystems.com/resources/articles/snmp-basics-what-it-and-how-it-works
- http://www.digitalocean.com/community/tutorials/an-introduction-to-snmp-simple-network-management-protocol