How to get trading sign gpo
How to get trading sign gpo
Get-GPOReport
Generates a report either in XML or HTML format for a specified GPO or for all GPOs in a domain.
Syntax
Description
The Get-GPOReport cmdlet generates a report in either XML or HTML format that describes properties and policy settings for a specified Group Policy Object (GPO) or for all GPOs in a domain. The information that is reported for each GPO includes: details, links, security filtering, Windows Management Instrumentation (WMI) filtering, delegation, and computer and user configurations.
You can specify the All parameter to generate a report for every GPO in the domain, or you can specify either the Name or Guid parameter to generate a report for a single GPO. You can also pipe GPO objects into this cmdlet. If you specify a file through the Path parameter, the report is written to a file; otherwise, it is printed to the display.
Examples
Example 1: Generate an HTML report for the specified GPO
This command generates a report in HTML format for the GPO TestGPO1 and writes it to the file C:\GPOReports\GPOReport1.html
Example 2: Generate an XML report for each GPO in the specified domain
This command generates a report in XML format for each GPO in the sales.contoso.com domain and writes it to the file C:\GPOReports\GPOReportsAll.xml. The DC1.sales.contoso.com domain controller is contacted to complete the operation.
If the domain of the user account (or, for startup and shutdown scripts, the computer account) is different from sales.contoso2.com, a trust must exist between the two domains.
Example 3: Generate an XML report for a GPO with the specified GUID
This command generates a report in XML format for the GPO with the specified GUID. Because no Path parameter is supplied, the report is written to the display.
Parameters
Indicates that the cmdlet generates a report for all GPOs in the domain.
| Type: | SwitchParameter |
| Position: | 5 |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Specifies the domain for this cmdlet. You must specify the fully qualified domain name (FQDN) of the domain.
For the Get-GPOReport cmdlet:
If a single GPO is specified, it must exist in this domain.
If the All parameter is specified, a report is generated for each GPO in this domain.
If you do not specify the Domain parameter, the domain of the user that is running the current session is used. If the cmdlet is being run from a computer startup or shutdown script, the domain of the computer is used. For more information, see the Notes section in the full Help.
If you specify a domain that is different from the domain of the user that is running the current session or, (for a startup or shutdown script, the computer), a trust must exist between that domain and the domain of the user or the computer.
You can also refer to Domain by its built-in alias, domainname. For more information, see about_Aliases.
| Type: | String |
| Aliases: | DomainName |
| Position: | 3 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
Specifies the GPO for which to generate the report by its globally unique identifier (GUID). The GUID uniquely identifies the GPO.
You can also refer to the Guid parameter by its built-in alias, id. For more information, see about_Aliases.
| Type: | Guid |
| Aliases: | Id |
| Position: | 0 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
Specifies the GPO for which to generate the report by its display name.
The display name is not guaranteed to be unique in the domain. If another GPO with the same display name exists in the domain an error occurs. You can use the Guid parameter to uniquely identify a GPO.
You can also refer to the Name parameter by its built-in alias, displayname. For more information, see about_Aliases.
| Type: | String |
| Aliases: | DisplayName |
| Position: | 0 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
Specifies the path to the report file; for instance, c:\Reports\GpoReport.xml. If no path is specified, the report is printed to the display.
| Type: | String |
| Position: | 2 |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Specifies the format of the report. You must specify either Html (for HTML format) or Xml (for XML format). These values are not case sensitive.
The following values are permitted for this object type.
| Type: | ReportType |
| Accepted values: | Xml, Html |
| Position: | 1 |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Specifies the name of the domain controller that this cmdlet contacts to complete the operation. You can specify either the fully qualified domain name (FQDN) or the host name.
If you do not specify the name by using the Server parameter, the primary domain controller (PDC) emulator is contacted.
You can refer to this parameter by its built-in alias, dc. For more information, see about_Aliases.
| Type: | String |
| Aliases: | DC |
| Position: | 4 |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Inputs
Microsoft.GroupPolicy.Gpo
An object that represents a GPO. Collections that contain GPOs from different domains are not supported.
Outputs
None
This cmdlet does not generate any output.
Notes
You can use the Domain parameter to explicitly specify the domain for this cmdlet.
If you do not explicitly specify the domain, the cmdlet uses a default domain. The default domain is the domain that is used to access network resources by the security context under which the current session is running. This domain is typically the domain of the user that is running the session. For instance, the domain of the user who started the session by opening Windows PowerShell from the Program Files menu, or the domain of a user that is specified in a runas command. However, computer startup and shutdown scripts run under the context of the LocalSystem account. The LocalSystem account is a built-in local account, and it accesses network resources under the context of the computer account. Therefore, when this cmdlet is run from a startup or shutdown script, the default domain is the domain to which the computer is joined.
Get-GPO
Gets one GPO or all the GPOs in a domain.
Syntax
Description
The Get-GPO cmdlet gets one Group Policy Object (GPO) or all the GPOs in a domain. You can specify a GPO by its display name or by its globally unique identifier (GUID) to get a single GPO, or you can get all the GPOs in the domain through the All parameter.
This cmdlet returns one or more objects that represent the requested GPOs. By default, properties of the requested GPOs are printed to the display; however, you can also pipe the output of the Get-GPO cmdlet to other Group Policy cmdlets.
Examples
Example 1: Get a single GPO from a domain
This command gets the GPO named Group Policy Test. The GPO must exist in the domain of the user that is running the session (or, for startup and shutdown scripts, the computer). The command gets the GPO information by contacting the primary domain controller (PDC).
Example 2: Get a single GPO by GUID
This command gets the GPO that has the ID (GUID) 331a09564-cd4a-4520-98fa-446a2af23b4b in the sales.contoso.com domain. If the domain of the user that is running the session (or, for startup and shutdown scripts, the computer) is different that sales.contoso.com, a trust must exist between the two domains. The command retrieves the GPO information by contacting the PDC (in the sales.contoso.com domain).
Example 3: Get all GPOs from a domain
This command get all the GPOs in the sales.contoso.com domain.
Parameters
Indicates that the cmdlet gets all the GPOs in the domain.
| Type: | SwitchParameter |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Specifies the domain for this cmdlet. You must specify the fully qualified domain name (FQDN) of the domain.
For the Get-GPO cmdlet, the GPO (or GPOs) to that this cmdlet gets must exist in this domain.
If you do not specify the Domain parameter, the domain of the user that is running the current session is used. If the cmdlet is being run from a computer startup or shutdown script, the domain of the computer is used. For more information, see the Notes section in the full Help.
If you specify a domain that is different from the domain of the user that is running the current session (or, for a startup or shutdown script, the computer), a trust must exist between that domain and the domain of the user or the computer.
You can also refer to the Domain parameter by its built-in alias, domainname. For more information, see about_Aliases.
| Type: | String |
| Aliases: | DomainName |
| Position: | 1 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
Specifies the GPO to retrieve by its globally unique identifier (GUID). The GUID uniquely identifies the GPO.
You can also refer to the Guid parameter by its built-in alias, id.
| Type: | Guid |
| Aliases: | Id |
| Position: | 0 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
Specifies the GPO to retrieve by its display name.
The display name is not guaranteed to be unique in the domain. If another GPO with the same display name exists in the domain an error occurs. You can use the Guid parameter to uniquely identify a GPO.
You can also refer to the Name parameter by its built-in alias, displayname.
| Type: | String |
| Aliases: | DisplayName |
| Position: | 0 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
Specifies the name of the domain controller that this cmdlet contacts to complete the operation. You can specify either the fully qualified domain name (FQDN) or the host name.
If you do not specify the name by using the Server parameter, the primary domain controller (PDC) emulator is contacted.
You can also refer to the Server parameter by its built-in alias, dc.
| Type: | String |
| Aliases: | DC |
| Position: | 2 |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Inputs
Microsoft.GroupPolicy.Gpo
You can pipe a GPO for which to get information to this cmdlet. You can pipe GPO objects into this cmdlet to display information about the GPOs. Collections that contain GPOs from different domains are not supported.
Outputs
Microsoft.GroupPolicy.Gpo
This cmdlet returns an object that represents the requested GPO.
Notes
You can use the Domain parameter to explicitly specify the domain for this cmdlet.
If you do not explicitly specify the domain, the cmdlet uses a default domain. The default domain is the domain that is used to access network resources by the security context under which the current session is running. This domain is typically the domain of the user that is running the session. For example, the domain of the user who started the session by opening Windows PowerShell from the Program Files menu, or the domain of a user that is specified in a runas command. However, computer startup and shutdown scripts run under the context of the LocalSystem account. The LocalSystem account is a built-in local account, and it accesses network resources under the context of the computer account. Therefore, when this cmdlet is run from a startup or shutdown script, the default domain is the domain to which the computer is joined.
Строим отчеты и анализируем групповые политики с помощью PowerShell

Используем PowerShell в связке с групповыми политиками: что для этого нужно?
Последовательность наших действий:
Строим отчеты по групповым политикам
Проблема №1. Необходимо получить информацию о том, что в настоящий момент происходит в групповых политиках
В данном случае вместо JeremyGPO выступает отображаемое имя (DisplayName) объекта групповых политик. Выводится такая табличка
Решение проблемы: создаем отчеты.
Проблема №2. Слишком много GPO, которые не используются.
Задача: найти пустые GPOs
Проблема №3.
Кто обращался к объекту групповой политики?
Имеются ли GPO, в которых половина политики деактивирована (“Are there any GPOs with ‘half’ the policy disabled?”)
Имеются ли GPO, в которых все политики деактивированы (“Are there any GPOs with ‘all’ the policy disabled?”)
Применяем фильтр по статусу GPO (GPOStatus). Каждому из трех вопросов выше соответствуют три команды:
Анализируем объекты групповых политик
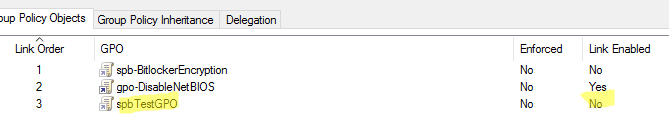
Проблема №4. Обнаруживаем GPO без связей
Проблема 5. Объекты групповых политик с излишними настройками в реестре (“Extra Registry Settings”)
Находим излишние настройки в реестре
Еще раз обозначим, что мы привели в посте лишь сухой остаток того, что было продемонстрировано в докладе. Сам доклад можно посмотреть здесь.
Также для построения отчетов по групповым политикам вы можете воспользоваться нашей программой NetWrix Group Policy Change Reporter.
How to get trading sign gpo
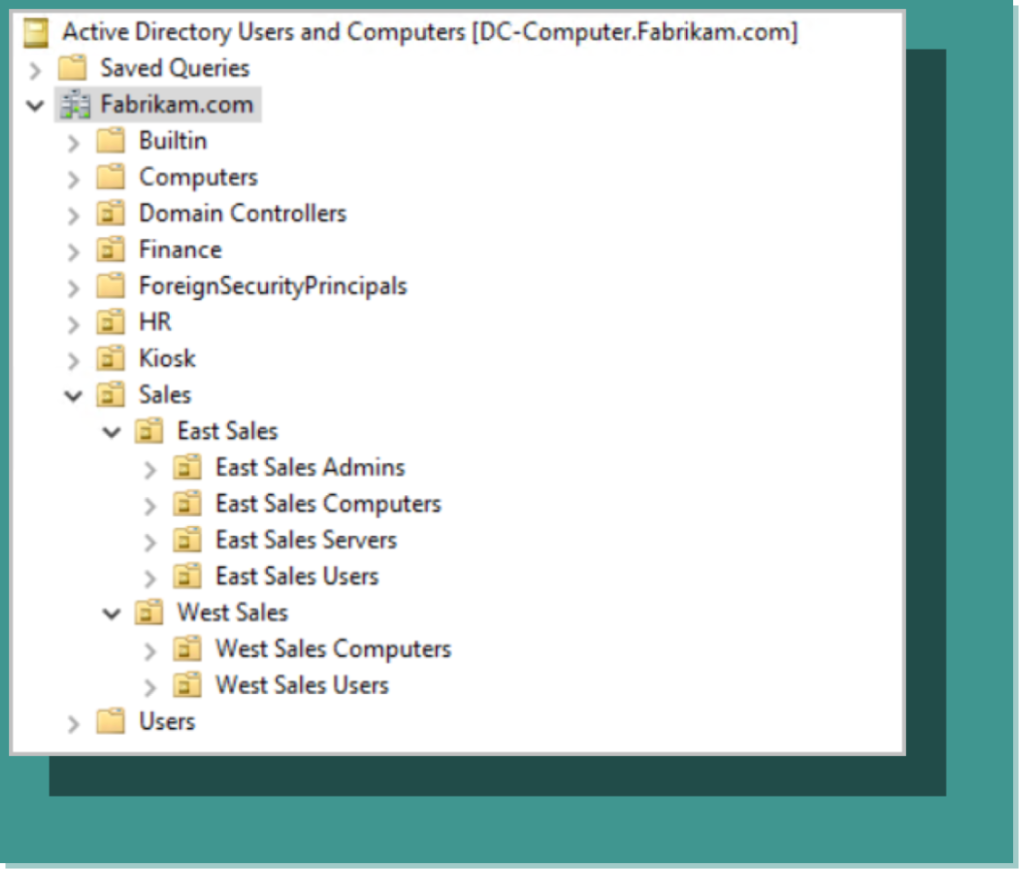
GPO Item Level Targeting is one of the most powerful tools you can use as a Group Policy admin. First of all, You know how important it is to segregate your domain into applicable OUs for different user and computer AD accounts (see Figure 1).
Figure 1: Example OUs for an active directory.
While this approach by itself may have been completely sufficient at one time, in today’s complicated networks you need more granular control over GPO delegation, for instance, at times when you want to apply a GPO to members of a designated security group only or when a user is on a particular IP address range.
BLOG: How to Apply Item Level Targeting
Item-Level Targeting lets you define how Group Policy settings apply to Active Directory users or computers by setting conditions. You perform the process by first selecting conditional logic statements like AND, OR, and NOT. These best practices will help you get more out of Item-level targeting.
There are few other ways you can target GPOs (or what they do) to users:
We’ll briefly explore the first two options, and then dive into ILT and why it can help you out immensely.
GPO Item Level Targeting by Group
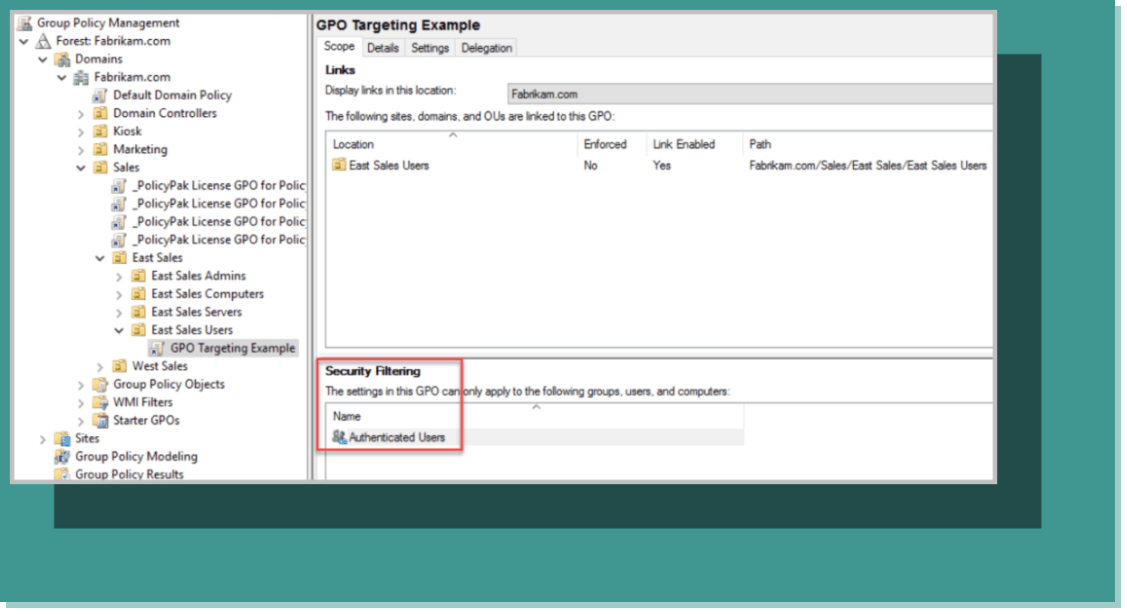
A basic way to target GPOs is to use security filtering so that the GPO only applies to a designated group or groups. By default, a GPO applies to all authenticated users within the container that the GPO is linked to, such as an OU. In the example in Figure 2 below, the GPO is being applied to all authenticated users within the “East Sales Users” OU.
Figure 2: Applying a GPO to the OU “East Sales Users.”
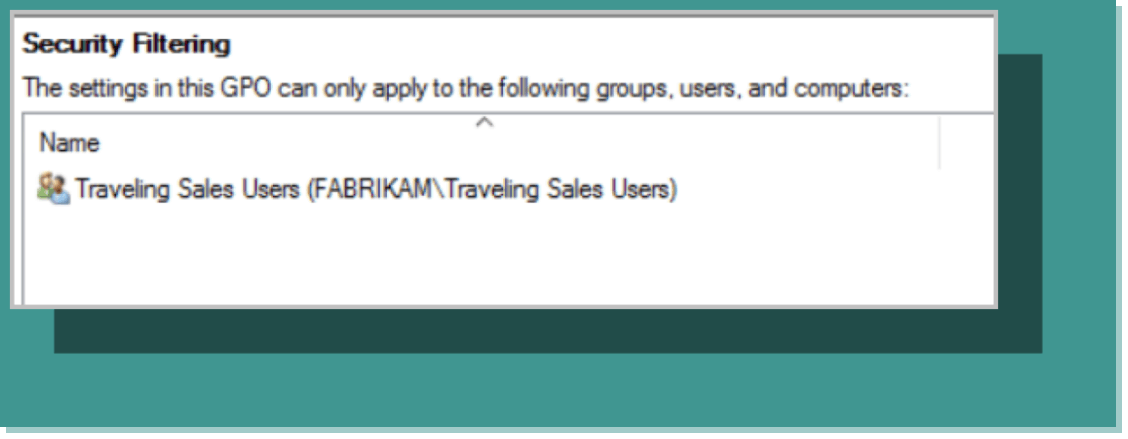
Using the Security Filtering settings, you can delete the Authenticated Users group and select one or more designated groups. In Figure 3, the GPO is being targeted to the Traveling Sales Users group.
Figure 3: Using security filtering to target a specific group.
GPO Item Level Targeting by WMI
Another option for targeting GPOs is WMI filtering. This is applicable for certain circumstances such as targeting a specific operating system. If you wanted to target only machines running Windows 10, you could create the following WMI query:
select * from Win32_OperatingSystem where Version like “10.%” and ProductType=”1″
You would then create a WMI filter within Group Policy Management and a query statement, as shown in Figure 4 below.
Figure 4: Creating a WMI filter and query statement.
While WMI does do the job in some cases, it has a number of shortcomings.
BLOG: WMI Filtering Tips and Tricks
Why is WMI important when it comes to Group Policy? WMI provides a way for you to filter Group Policy Objects based on the result of a WMI query. Where might this come in handy? It can help you custom target your GPOs so the right GPOs apply within just the right conditions.
GPO Item Level Targeting with Everything Else
If OU design and targeting by group are just ok and WMI is not great, what’s other choice do you have for targeting GPOs? Let’s talk about Item Level Targeting.
Item Level Targeting gives you a whole gamut of things to target such as:
You also don’t need to know how to write a query statement because it is all point and click. Although it sounds good so far, there are a couple of shortcomings.
In other words, if want to create a GPO using Administrative Templates or create a policy for non-domain-joined computers, you are out of luck.
Item-Level Targeting and Group Policy Preferences
Let’s work through an example of a situation where all admins can use ILT, like with a Registry Item change. Microsoft Group Policy Preferences gives you a number of granular control functions including ILT. ILT allows you to change the scope of individual preference items, so they apply only to selected users or computers.
The screenshot in Figure 5 shows a Group Policy Preferences policy that creates a registry key. Once the registry configuration is complete, you can then access its properties and click the common tab where you can select “Item-level targeting” as is shown in the screenshot below. Note that ILT is available for any GPP setting.
Figure 5: Selecting “Item-level targeting” for a Group Policy Preferences policy.
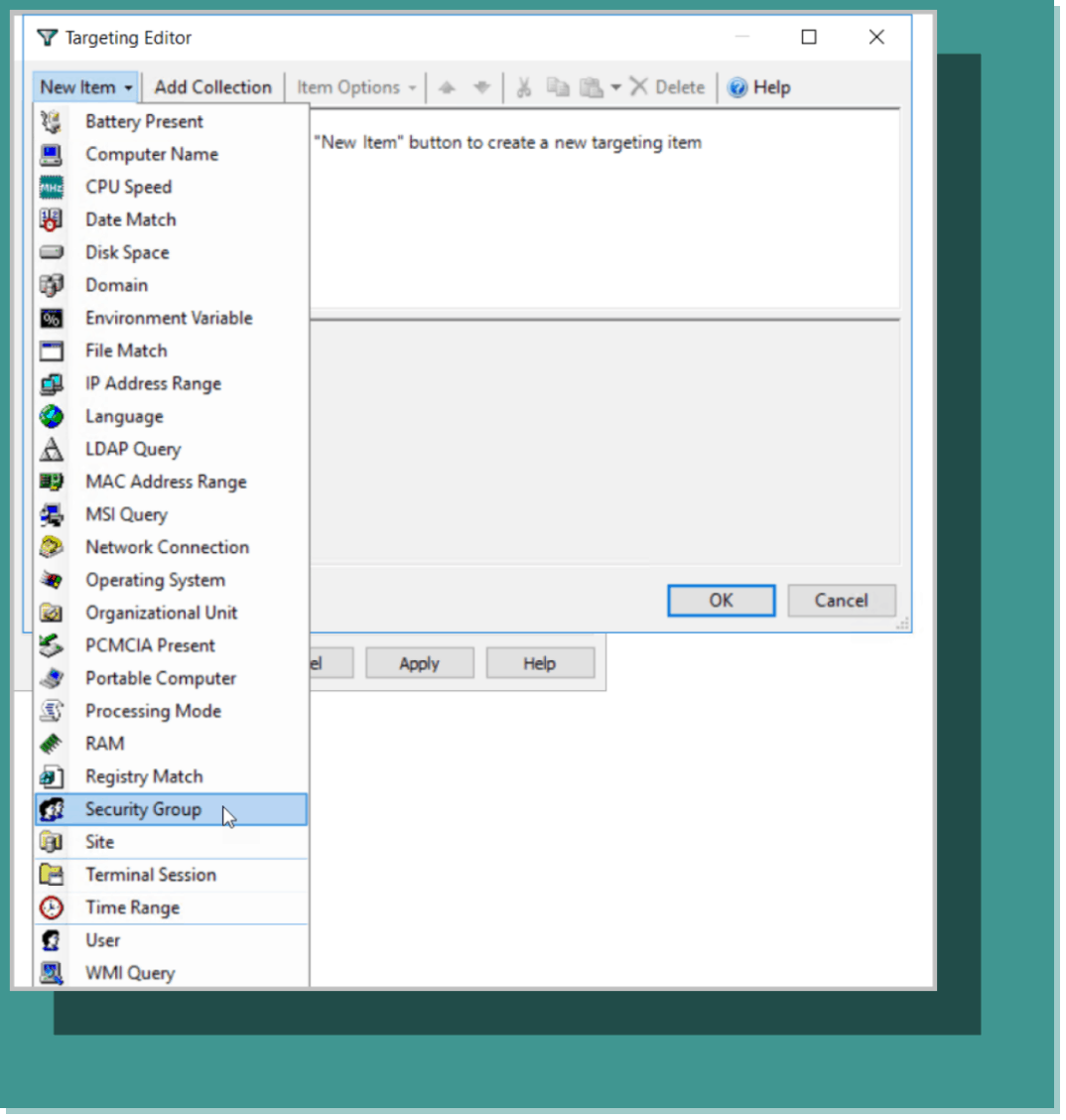
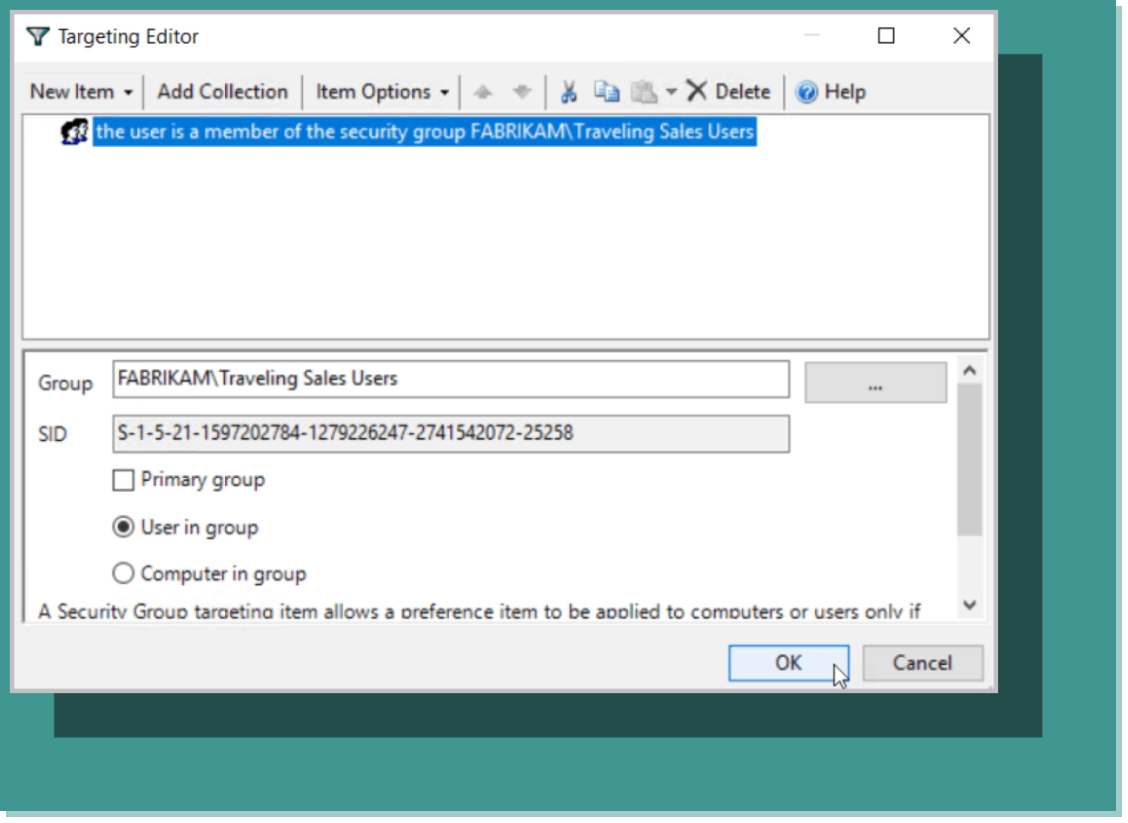
You can then select an item to target. In this case we are going to choose “Security Group,” as shown in Figure 6.
Figure 6: Targeting security groups in the Targeting Editor.
We want to start out by targeting a domain security group. In the screenshot below in Figure 7, we have chosen the Traveling Sales Users group as we did earlier.
Figure 7: Targeting the Traveling Sales Users group.
Now the registry item will be updated for all group members in the linked OU as well as all nested OUs, unless blocked for inheritance.
FREE TRIAL: GPO Reduction and Transitions Pak
Reduce and consolidate Group Policy Objects and Settings for a more modernized and efficient Windows infrastructure. The PolicyPak GPO Reduction and Transitions Pak manages complex environments in a way that eliminates sprawl and simplifies administration.
While having the ability to target security groups is cool, ILT provides far more granularity. For example, what if the registry key were only applicable for machines that run Windows 10 Professional edition? In this case, you can add a condition that members of the security group must also be running that particular OS, as shown below in Figure 8. Of course, if the combined value of all targeting items for a preference item is false, then the settings in the GPPrefs item are not applied to the user or computer.
Figure 8: Restricting the application of the GPO to users with Windows 10 Professional.
Let’s dive even deeper with ILT. You can use varying logical operators (“And,” “Or,” “Is,” and “Is Not”) to delegate a GPO to members of one group or another. You can also incorporate the use of collections. In the example below in Figure 9, the GPO is assigned to members of either the Traveling Sales Users group or East Sales Managers who also meet the conditions of a collection consisting of two settings. In this case, users of either group must be logged on a portable computer and running Windows 10 Professional edition. Notice the use of logical operators as well.
Figure 9: Targeting groups using logical operators and collections.
Using PolicyPak to Overcome Limitations of GPO Item Level Targeting
All of these options make ILT seem like a good solution, but the problem is that it is not natively available for the more than 4,000 Administrative Templates settings that you use every day. In addition, there are other items in Group Policy that don’t have ILT where it would be really useful (like with 3rd party add-ons).
Is there some magical workaround for this? Actually, yes. Simply use PolicyPak.
PolicyPak is a modern desktop management solution that maximizes the management tools you already have. PolicyPak allows you to configure, deploy, and manage policies for your Windows environments using Microsoft Group Policy Editor, SCCM, or other systems management systems. Its solution suite gives you super admin powers to do things such as use ILT with Administrative Templates settings. As you can see from the screenshot below in Figure 10, the policy creation process mimics that of traditional group policy.
Figure 10: The policy creation process with PolicyPak.
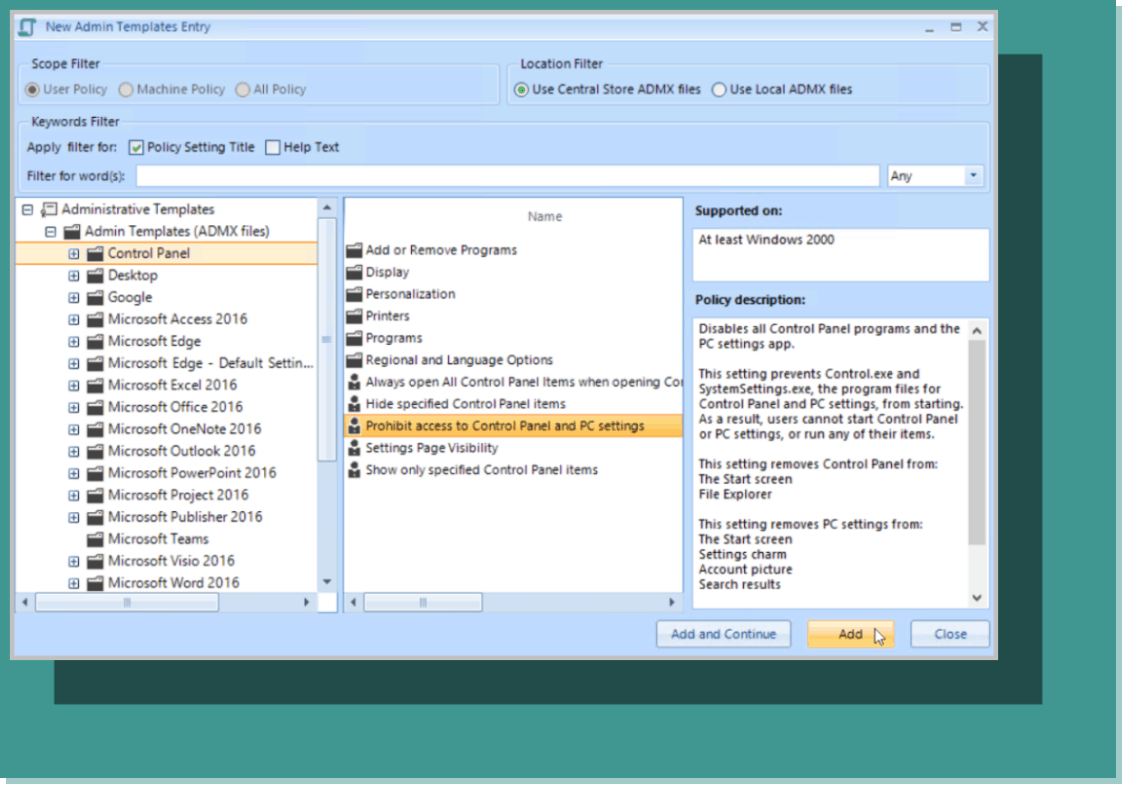
PolicyPak Admin Templates Manager includes all of the same administrative templates settings you are familiar with, including third party templates you may be using as well. You can enable or disable the setting of your choice. In the example below in Figure 11, we want to prohibit access to Control Panel and PC settings.
Figure 11: Creating a new Admin Templates entry.
Notice the Item Level Targeting button is available within the properties page (see Figure 12), thus giving you identical access to the ILT feature as shown below.
Figure 12: Using the Item-Level Targeting feature of PolicyPak Admin Templates Manager.
By utilizing ILT for all of your GPOs, you can consolidate your GPOs into a much smaller and more manageable number or even a single GPO. You can watch a video to see how to use PolicyPak ILT to simplify your GPO environment. You can also get more information on how PolicyPak can apply ILT to MDM-enrolled and non-domain-joined machines.
Summary
Item Level Targeting is a great feature to maximize your Group Policy Preferences environments even with its shortcomings; however, you don’t have to accept its limitations. With PolicyPak, you can meet the demands of today’s mobile and remote work strategies by deploying any traditional GPO to any Windows machine you want using ILT.
Управление групповыми политиками (GPO) в Active Directory с помощью PowerShell
Основной классический инструмент для управления групповыми политиками (GPO) в домене Active Directory — графическая консоль Group Policy Management Console (gpmc.msc). Однако для автоматизации и повышения эффективности некоторых задач управления GPO в Active Directory, вы можно использовать PowerShell, который предоставляет широкие возможности по администрированию групповых политик.
Установка PowerShell модуля управления групповыми политиками
Для управления доменными групповыми политиками на вашем компьютере должен быть установлен модуль GroupPolicy. Данный модуль доступен в Windows Server после установки компонента Group Policy Management. Данную опцию можно установить из консоли Server Manager или с помощью PowerShell:
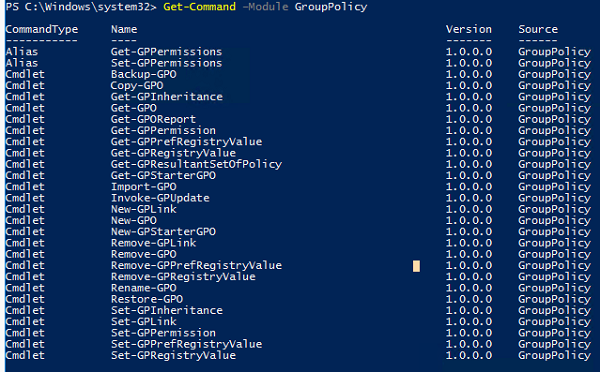
Полный список PowerShell командлетов в модуле GroupPolicy можно вывести с помощью команды:
Get-Command –Module GroupPolicy
С помощью PowerShell модуля GroupPolicy вы можете:
Управление GPO с помощью PowerShell
Рассмотрим несколько типовых задач администратора, в которых можно использовать PowerShell для управления групповыми политиками.
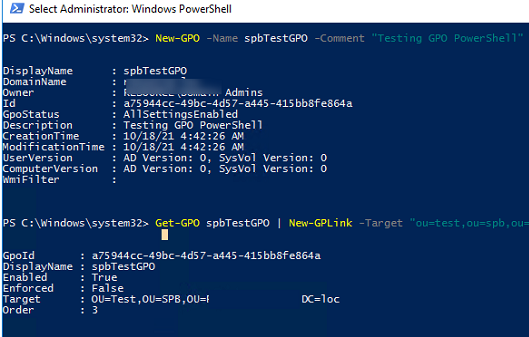
Чтобы создать новую пустую политику, воспользуйтесь командой:
Если у вас в домене созданы стартовые групповые политики (Starter GPO), вы можете создать новую политику на основе такого шаблона (например, с определенными настройками Security Baseline):
Чтобы назначить политику на определенную OU, используйте командлет New-GPLink:
Чтобы отлинковать GPO от OU:
Если нужно отключить применение GPO, но не удалять связь, используется командлет Set-GPLink:
GPO перестала применяться к OU, но осталась слинкованной.
Следующая однострочная команда PowerShell создаст новую GPO, которая меняет настройки одного параметра реестра (отключает автообновление драйверов), ограничит применение политики определенной группой безопасности, и прилинкует к определенному OU:
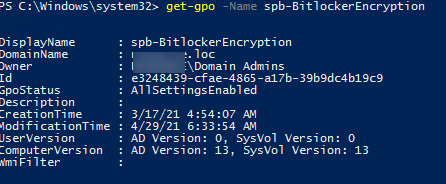
С помощью командлета Get-GPO можно вывести информацию о конкретном объекте GPO или о всех политиках в домене. Данный командлет возвращает GUID политики (часто нужен при диагностике применения GPO на компьютерах или решения проблем с репликацией объектов политик при проверке состояния AD), время создания, модификации политики, примененные WMI фильтры GPO.
Можно вывести настройки WMI фильтра, привязанного к GPO (но изменить настройки фильтра не получится):(Get-GPO spbWin10Settings).WmiFilter
PowerShell: применение GPO, результирующие политики
Для обновления групповых политик на удаленных компьютерах используется командлет Invoke-GPUpdate. Можно обновить настройки GPO на конкретном компьютере:
Или на всех компьютерах в указанной OU:
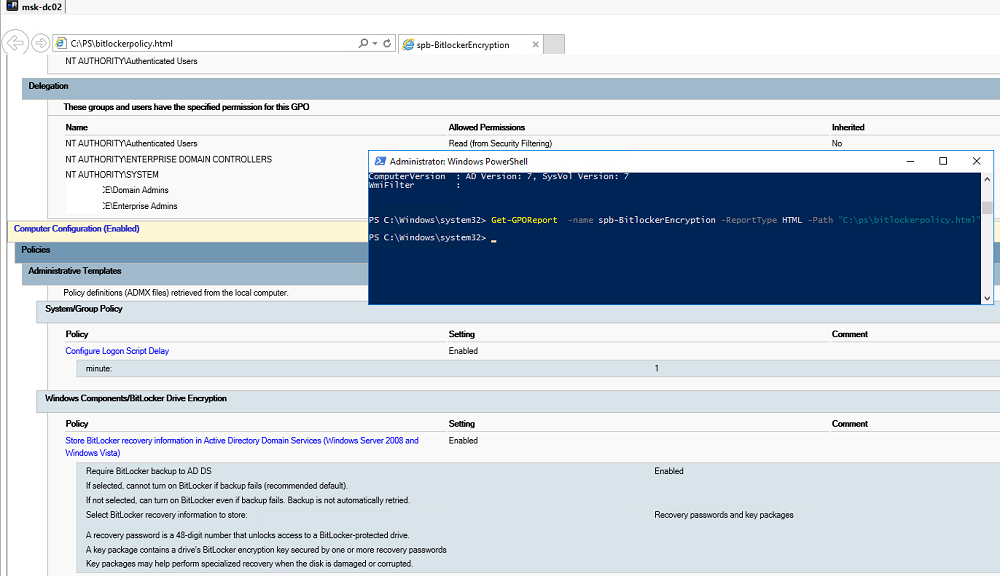
Командлет Get-GPOReport используется для построения HTML/XML отчетов с настройками указанной политики:
Резервное копирование и восстановление GPO
С помощью PowerShell вы можете создавать резервные копии объектов групповых политик в домене и восстанавливать их.
Можно создать резервную копию всех GPO:
Для восстановления GPO используется:
Вы можете хранить несколько версий резервных копий GPO в одной папке. Чтобы восстановить определенную версию GPO, нужно указать ее ID резервной копии (32 разрядный идентификатор):